


|
||
|
||
Phishing campaigns almost always require a massive volume of domains in order to succeed. Phishers, after all, need to have readily weaponizable vectors at their disposal in case the ones they’re currently employing get detected and consequently blocked.
The Threat Intelligence Platform (TIP) research team recently uncovered an email address that belonged to the operator of an ongoing phishing operation that has seemingly been amassing an arsenal of .com domains. Using this address as a jump-off point, we sought to uncover all other potentially connected artifacts strewn all over the DNS. Our in-depth investigation into the threat found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our DNS deep dive by looking for domains that were registered using the email address identified as an IoC in the past 10 years or so. That led to the discovery of 507 email-connected domains. A TIP bulk malware check for them revealed that 60 of them were found malicious.
The WHOIS records of the 507 email-connected domains revealed these findings:
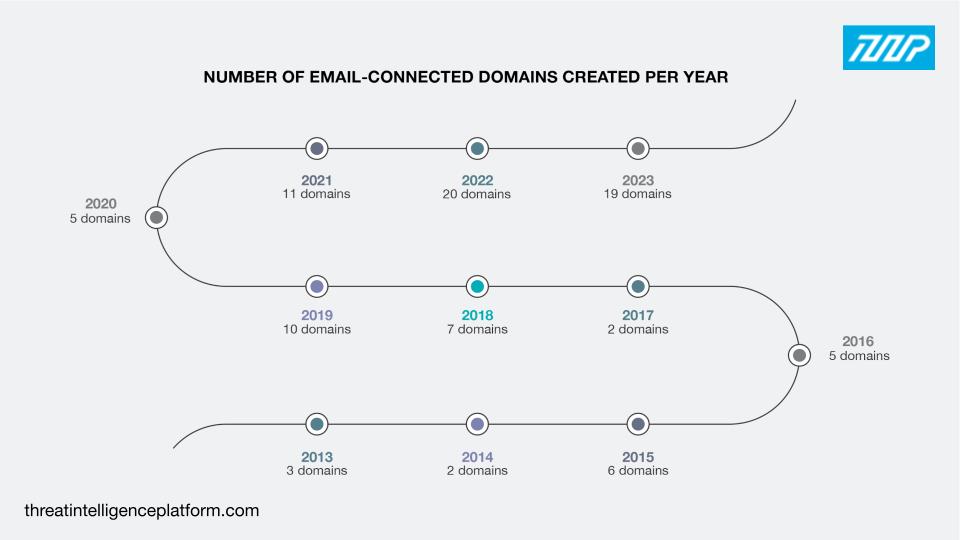
Creation dates: The 90 email-connected domains with current WHOIS records were created between 2013 and 2023. The highest number, 20 domains to be exact, were created in 2022.
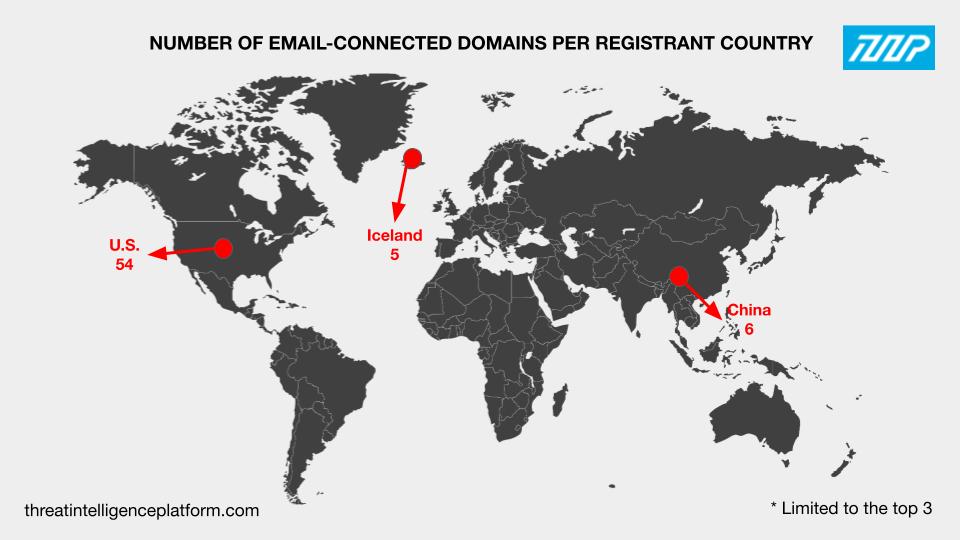
Registrant countries: Only 81 of the 90 email-connected domains had the registrant country field filled, with the top 3 registrant countries being the U.S. (54 domains), China (6 domains), and Iceland (5 domains). The remaining 16 domains were registered in nine other countries.
To uncover other potential threat vectors that may have already been used in or could be weaponized for attacks, we then scoured the DNS records of the email-connected domains for more information.
A closer look at the domains’ DNS records revealed that only 144 of the domains resolve to IP addresses as of this writing. Take a look at our findings below.
| Malicious IP Address | Number of Times Reported on AbuseIPDB |
|---|---|
| 18[.]119[.]154[.]66 | 26 |
| 3[.]140[.]13[.]188 | 34 |
| 3[.]94[.]41[.]167 | 27 |
| 52[.]86[.]6[.]113 | 26 |
| 52[.]71[.]57[.]184 | 42 |
| 3[.]19[.]116[.]195 | 27 |
| 3[.]130[.]253[.]23 | 33 |
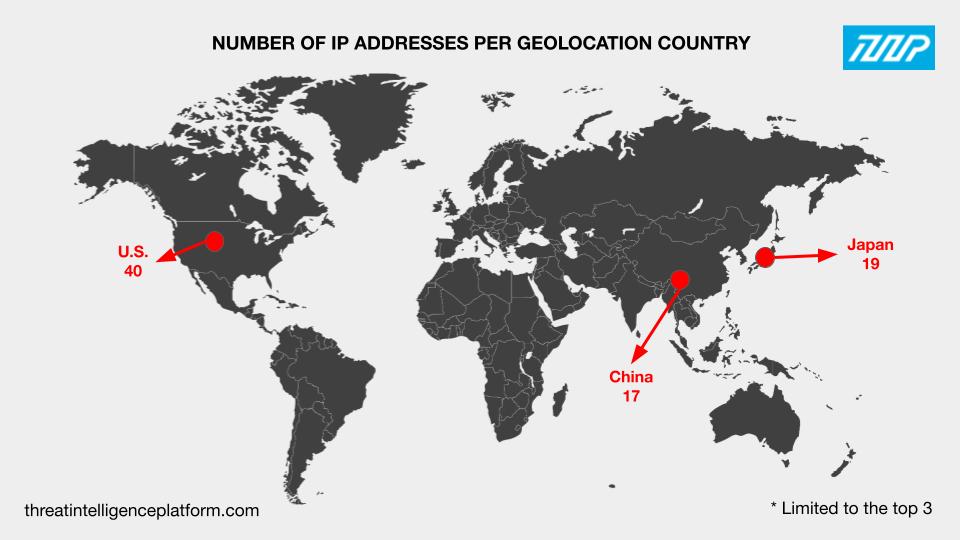
The top 3 countries where the IP addresses pointed to were the U.S. (40 IP addresses), Japan (19 IP addresses), and China (17 IP addresses). The 23 remaining IP addresses were geolocated in eight other countries.
The 98 IP addresses with available Internet service provider (ISP) information were distributed among 35 ISPs led by Amazon (19 IP addresses), RackIP Consultancy (17 IP addresses), and Microsoft (8 IP addresses).
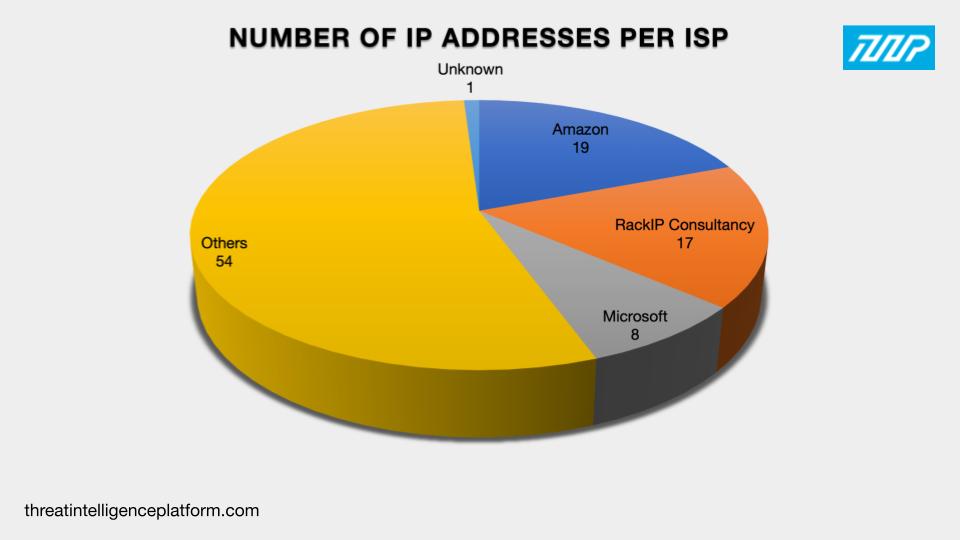
Further scrutiny of the IP records allowed us to determine that while nine didn’t have connected domains, 40 of the IP addresses were possibly dedicated, playing host to a total of 1,721 domains, 19 of which turned out to be malicious based on a bulk TIP malware check.
Further scrutiny of the 79 malicious domains (60 email- and 19 IP-connected domains) led to the following findings:
A total of 34 email- and IP-connected malicious domains remained accessible as of this writing—22 led to live pages, eight were parked, and four led to error or warning pages. Many of those with live content looked like gambling sites, a few examples of which are shown below.
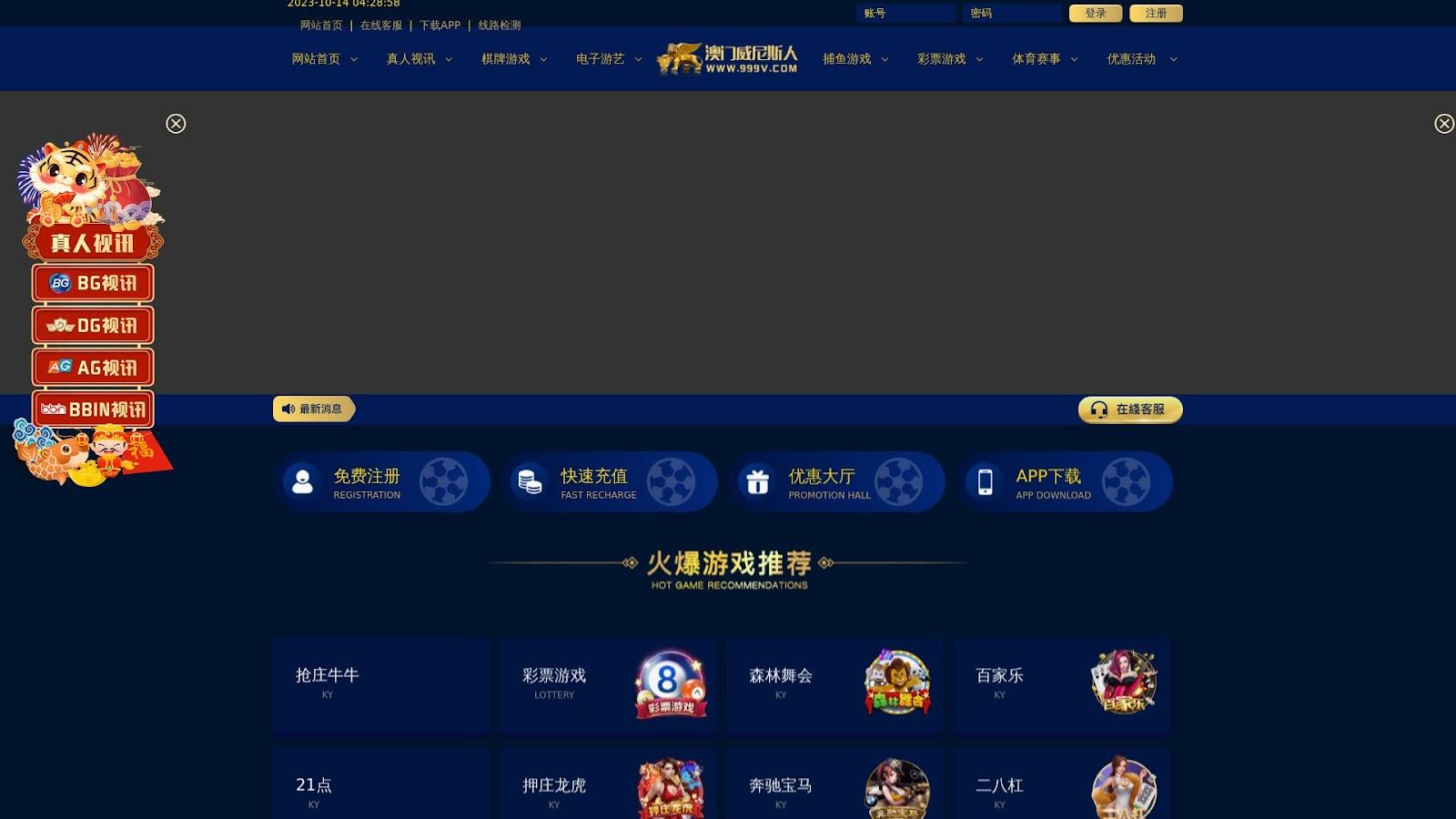
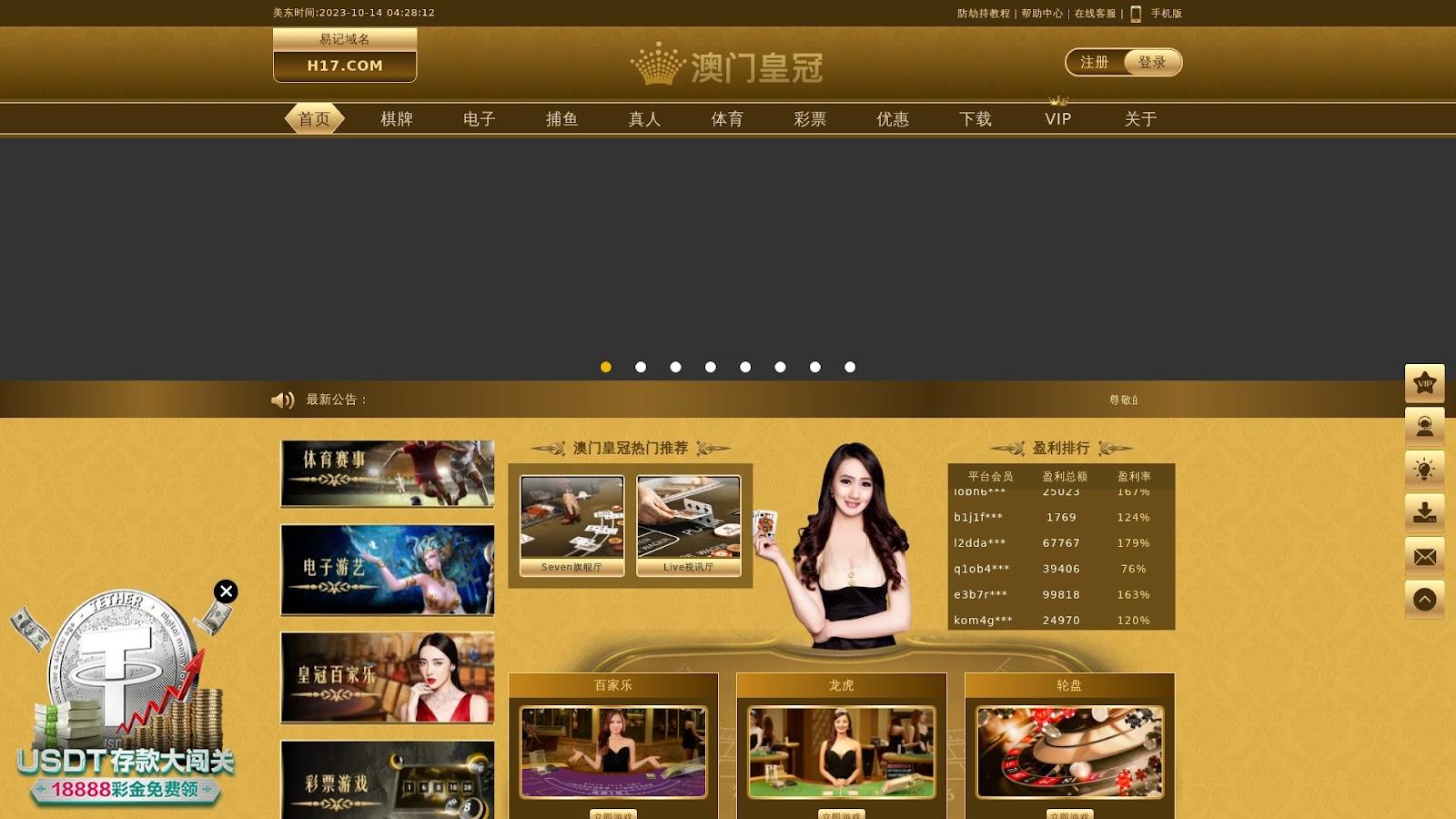
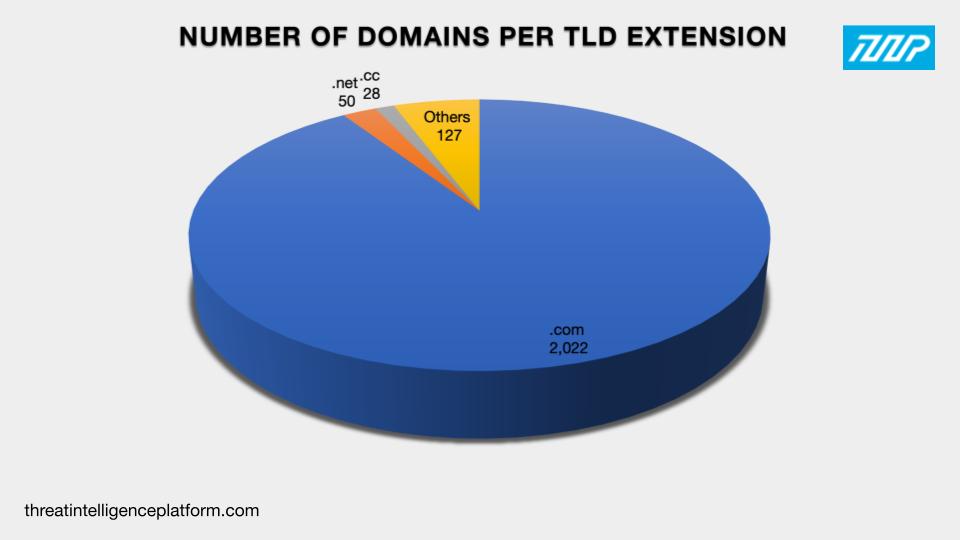
Earlier, we posited that the operators of this particular phishing campaign could be amassing a portfolio largely made up of .com domains. Our analysis of 2,228 domains in total (email- and IP-connected) revealed that a majority, 2,022 or 91%, did indeed sport .com as top-level domain (TLD) extension. The remaining 205 domains sported 35 other TLD extensions.
Our in-depth investigation of the phishing operation allowed us to find 2,327 potentially connected domains and IP addresses from a single email address identified as an IoC. And, as we originally posited, this particular threat group had an arsenal of at least 2,022 .com domains at their disposal.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byVerisign

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byCSC
