


|
||
|
||
Advanced persistent threat (APT) groups are more dangerous than your run-of-the-mill cybercriminals. They, after all, trail their sights not only on financial gain but loftier targets such as wreaking havoc on entire nations.
The WhoisXML API research team expanded lists of indicators of compromise (IoCs) related to six Asia-Pacific (APAC)-based or -targeting APT groups that launched attacks in 2023, as shown in the table below.
| APT GROUP | DESCRIPTION |
|---|---|
| APT29 | Believed to be based in Russia and operating since 2008, the group has launched attacks against organizations in the U.S. |
| APT32 | Believed to be based in Vietnam, they have been targeting Southeast Asian countries since 2014. |
| Earth Lusca | Believed to be based in China, the group has targeted organizations in Australia and been operating since 2019. |
| Higaisa | Believed to be based in South Korea, they have targeted organizations in North Korea since 2009. |
| Sandworm Team | Believed to be based in Russia and operating since 2009, the group has trailed its sights on organizations in Ukraine in the past. |
| Turla | Believed to be based in Russia, they have been operating since 2004 and launched attacks targeting organizations in 45 countries to date. |
Download the white paper now to explore our insights into the inner workings of the six APT groups.
Our analysis began with compiling a list of 34 APT groups from the MITRE ATT&CK Groups and Mandiant APTs pages. We then filtered for groups that launched attacks in 2023, were based in or targeted APAC countries, and had published domains identified as IoCs.
We were left with six APT groups—APT29, APT32, Earth Lusca, Higaisa, Sandworm Team, and Higaisa. Next, we scoured security research blogs 1 and collated 44 domains identified as IoCs in total.
Our in-depth study of the six APT groups led to:

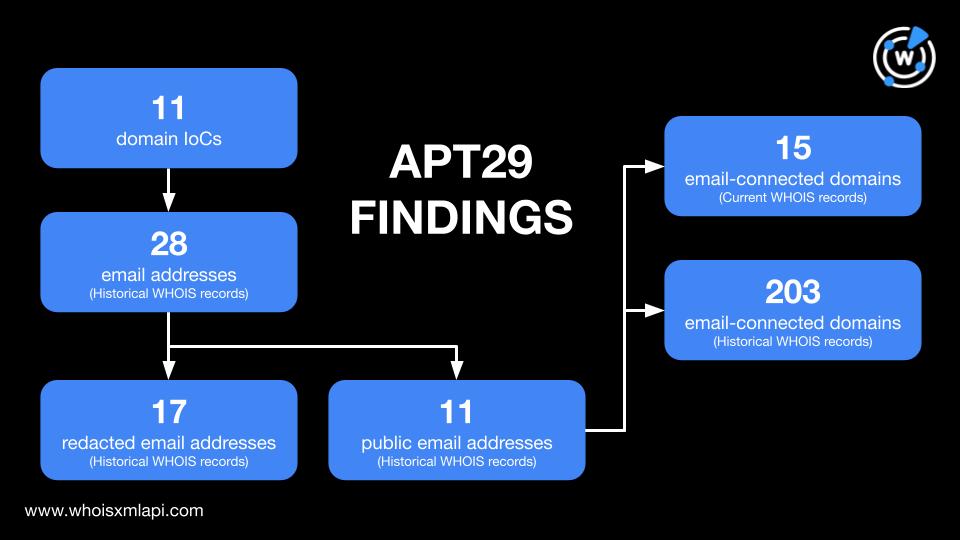
APT29, a Russia-based cyber espionage group said to have ties to the nation’s Foreign Intelligence Service (SVR) active since 2008, has trailed its sights on government networks across Europe and other North Atlantic Treaty Organization (NATO) member countries in the past. The group also reportedly attacked research institutes and think-tanks prior to its most recent target in the first half of 2023—Ukrainian organizations.
Our researchers expanded a public list of 11 domains identified as APT29 IoCs as part of the white paper, which led to the discovery of:
APT groups are bound to remain elusive since they are often backed by powerful and resourceful entities. Our research shows that several cyber intelligence sources can help provide more insights into APT-related activities.
Want to know more about the six APT groups? Download our complete white paper “2023 IoC List Expansion for APAC-Based/Targeting APT Groups: Leveraging Current and Historical WHOIS Data” now.
Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byVerisign

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byRadix
