


|
||
|
||
The OilRig cyber espionage group that goes by many names, including APT34, Crambus, Lyceum, and Siamesekitten, launched a long-term intrusion against a Middle Eastern government agency that ran from February to September 2023. Security experts believed the attackers enabled remote access on compromised computers, deployed keyloggers and backdoors, and stole passwords and other sensitive data over the eight-month period.
The group has been operating similar long-running campaigns since 2014 and is considered an ongoing threat. Threat Intelligence Platform (TIP) researchers thus launched a DNS investigation into OilRig’s known indicators of compromise (IoCs). We gathered 16 domains and six IP addresses tagged as IoCs related to OilRig campaigns over the past two years. 1, 2, 3, 4, 5, 6
Pivoting off them enabled us to uncover 667 unique artifacts broken down into:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
A closer look at 16 domains tagged in various OilRig campaigns revealed that:
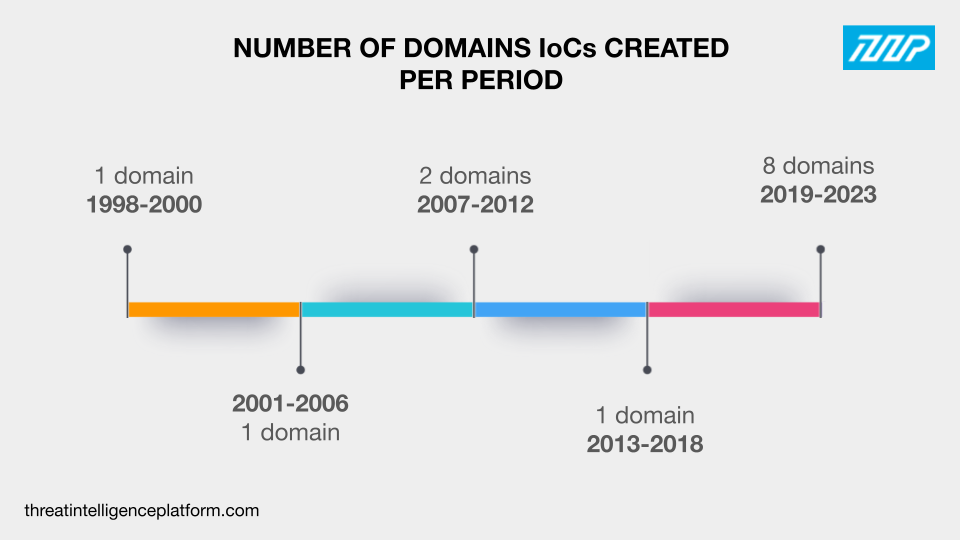
Such variations in domain age can provide insights into some of the APT group’s tactics regarding domain usage. For instance, the presence of older domains supports findings that some IoCs were likely legitimate domains the attackers compromised.
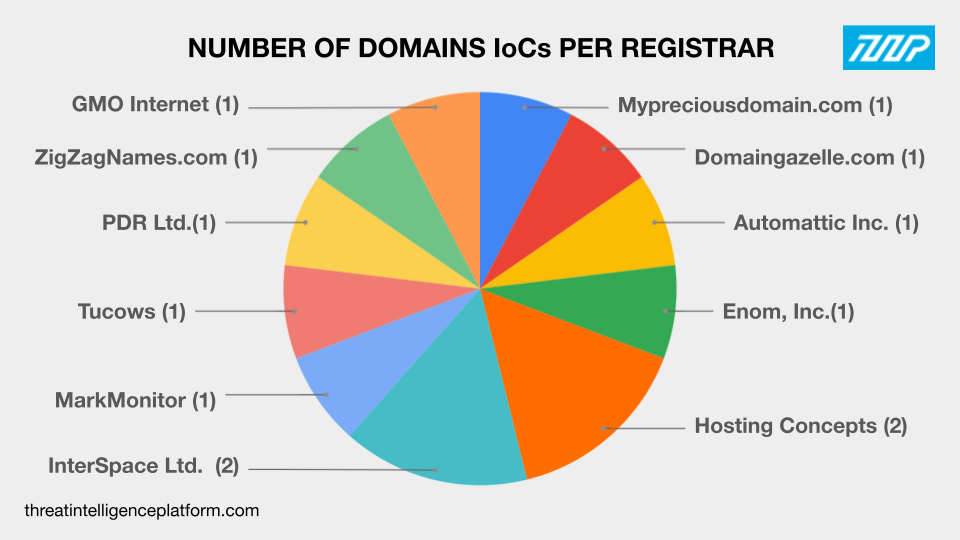
They used 11 different registrars—Mypreciousdomain.com, Automattic, Inc., Domaingazelle.com, Enom, Inc., MarkMonitor, Tucows, PDR Ltd., ZigZagNames.com, and GMO Internet managed one domain each while Hosting Concepts and InterSpace Ltd. handled two domain IoCs each. Three IoCs did not have current registrar data.
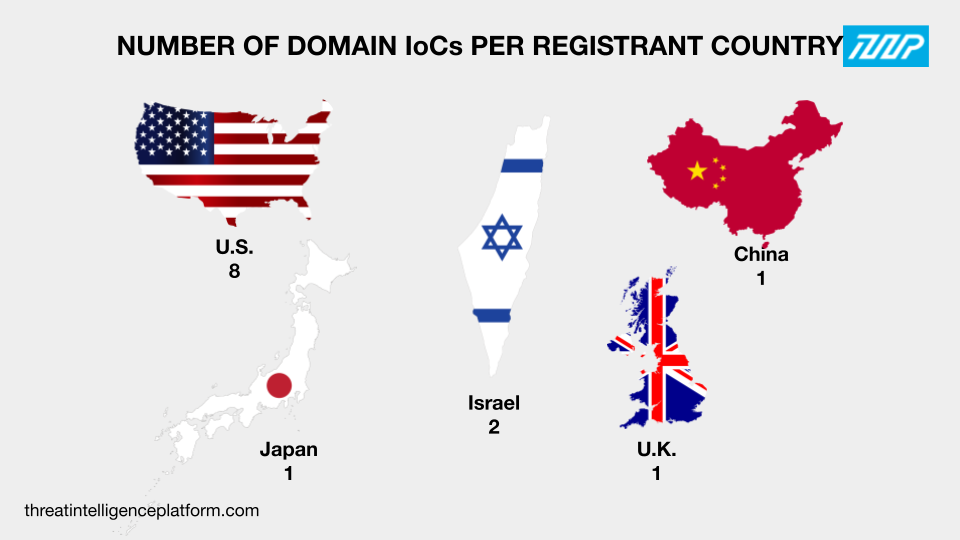
Next, we determined the registrant countries of the domain IoCs. Although OilRig is believed to be Iran-based, most of the domains appeared to be registered in the U.S. The rest were registered in the U.K., Israel, China, and Japan while some did not have registrant country data in their current WHOIS records.
Looking into the historical WHOIS records of the 16 OilRig domain IoCs enabled us to discover 45 email addresses, five of which were public.
We then dove into the DNS to look for domains that contained the email addresses in their current WHOIS records, which led us to 86 connected domains after filtering out duplicates and the IoCs.
TIP query results for all the domain IoCs uncovered their IP resolutions. From here, we found that only five of the 16 domains had active IP resolutions. This led us to 22 additional IP addresses that served as host to the domain IoCs. TIP also detected that five of the additional IP addresses were malicious.
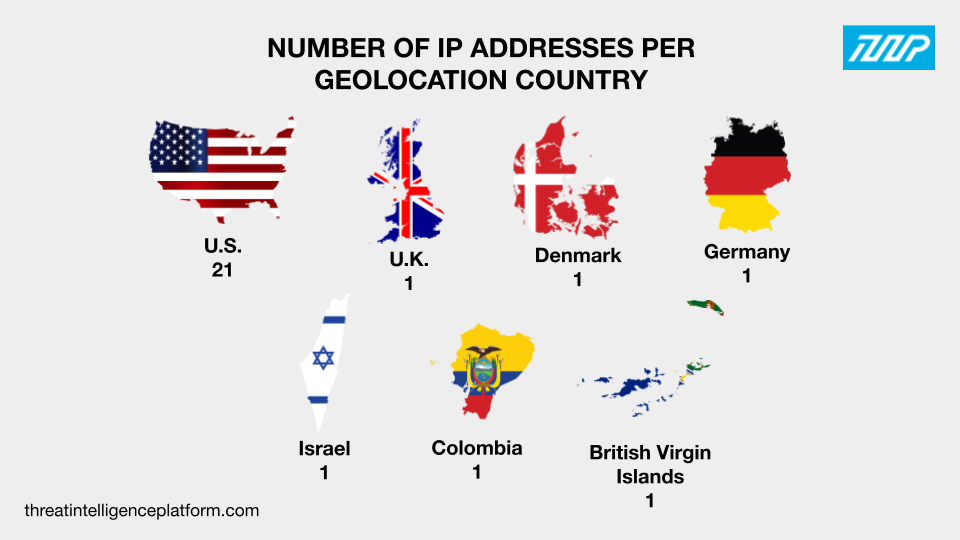
The 22 additional IP addresses and six originally tagged as IoCs were then subjected to TIP queries, which revealed they were geolocated across seven countries—U.S. had the most number of IP addresses at 21 while the U.K., Denmark, Germany, Israel, Colombia, and the British Virgin Islands had one IP address each. One IP address did not have geolocation data.
In addition, we found that 18 of the IP addresses were most likely dedicated while the rest did not have resolving domains. After removing duplicates, the IoCs, and email-connected domains, we found 171 unique domains resolving to the IP addresses.
We also looked at the IoCs’ text string usage. While only the string cdn appeared in several, some domains caught our interest because they seemed to be mimicking the web properties of popular companies like Uber, WorldRemit, and Expedia. Since they had different registrars and WHOIS record details, however, they could not be directly attributed to the imitated brands and could be cybersquatting.
The text strings we observed among the IoCs include:
These exact text strings appeared at the beginning of 33 domains sporting TLD extensions that differed from those of the IoCs. For example, we found .ws and .ph versions of asiaworldremit, joexpediagroup, and uber-asia.
Expanding this investigation to include domains using a combination of the IoC text strings led us to 346 additional domains. The search parameters and strings we used were:
TIP further detected that eight of the string-connected domains were also tagged as IoCs for other campaigns, most notably associated with malware distribution. All of them were first seen in the first and second quarters of 2023. Interestingly, seven of the malicious string-connected domains were last detected on 16 January 2024, only a day before this report was written. One domain was last seen on 5 November 2023.
Our extensive analysis and expansion of the 22 OilRig IoCs led to the discovery of 667 potentially connected web resources comprising nine public email addresses, 86 email-connected domains, 22 additional IP addresses, 171 IP-connected domains, and 379 sting-connected domains. Some of these artifacts also figured in other malicious campaigns.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byRadix
