


|
||
|
||
Among the latest to suffer from zero-day exploitation is Ivanti, a software company providing endpoint management and remote access solutions to various organizations, including U.S. federal agencies. High-impact zero-day vulnerabilities affecting Ivanti Connect Secure VPN and Policy Secure were recently reported, which could allow threat actors to execute arbitrary code with high-level access.
Mandiant already reported zero-day exploitations using these vulnerabilities by UNC5221, a suspected China-based espionage threat group. Other unknown threat groups may have also exploited the vulnerabilities. Mandiant published an in-depth investigation of the exploitation, including a list of indicators of compromise (IoCs) comprising 10 domains, two subdomains, and eight IP addresses.
In an effort to find more information and possibly connected artifacts, the WhoisXML API research team expanded the IoC list, leading to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download on our website.
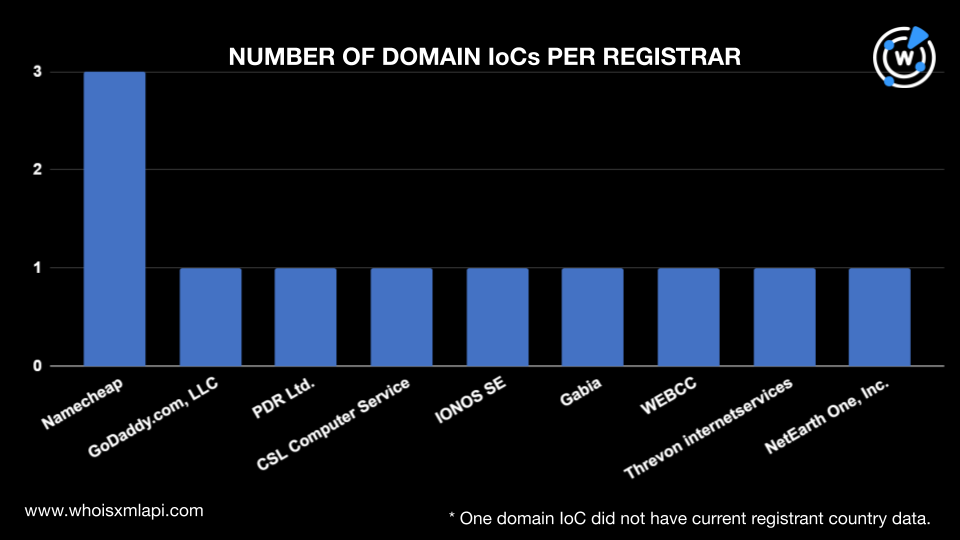
As our usual first step in analyzing IoCs, we performed a bulk WHOIS lookup for 12 domains (10 domain IoCs and two domains extracted from the subdomains tagged as IoCs) and found that:
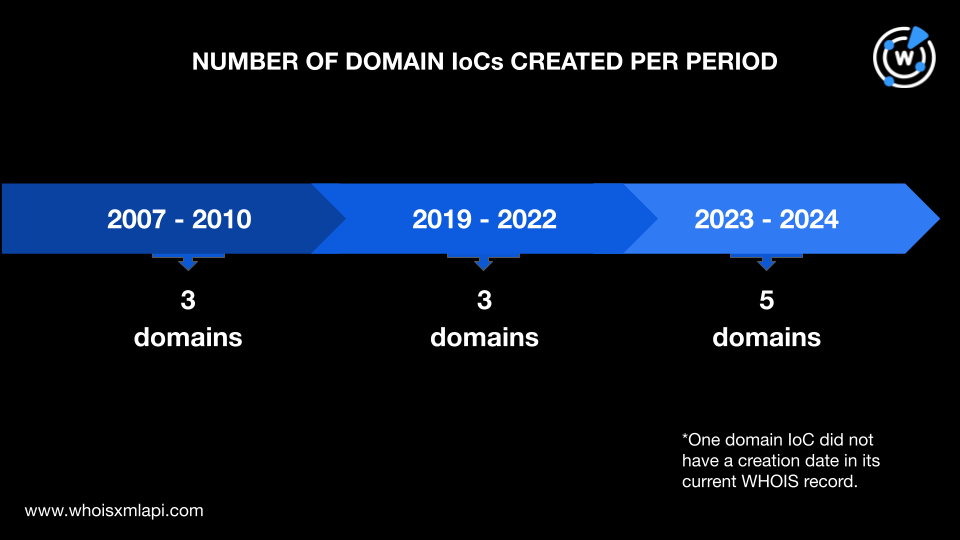
Three domains were created in 2024, two in 2023, one in 2022, one in 2021, one in 2019, two in 2010, and the oldest in 2007. The remaining domain had no creation date in its current WHOIS record.
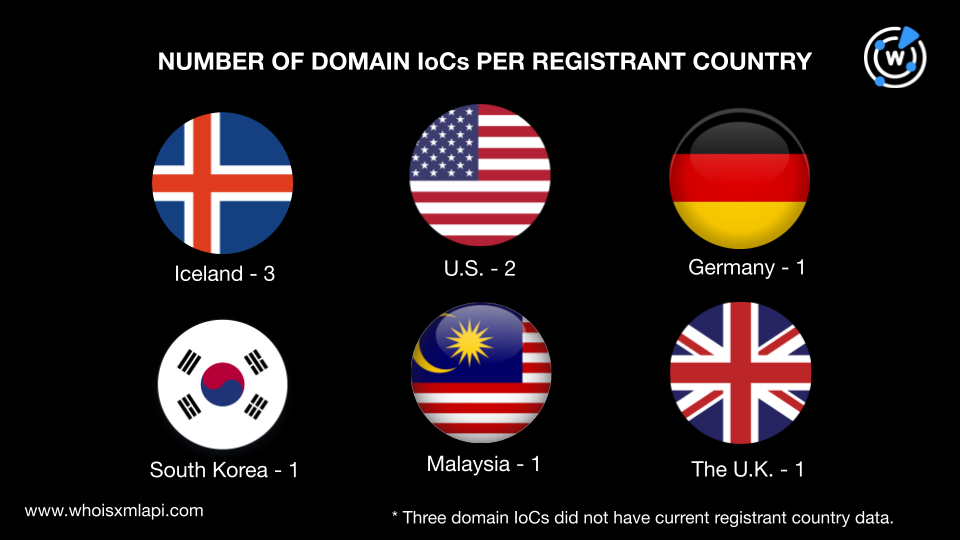
They were spread across six registrant countries. Three were registered in Iceland, two in the U.S., and one each in Germany, South Korea, Malaysia, and the U.K. Three domains did not have a current registrant country data.
We also subjected the domain IoCs to a screenshot analysis, which revealed that some continued to host live content, including the websites below.

Next, we did a bulk IP geolocation lookup for the eight IP addresses listed as IoCs, which revealed that:
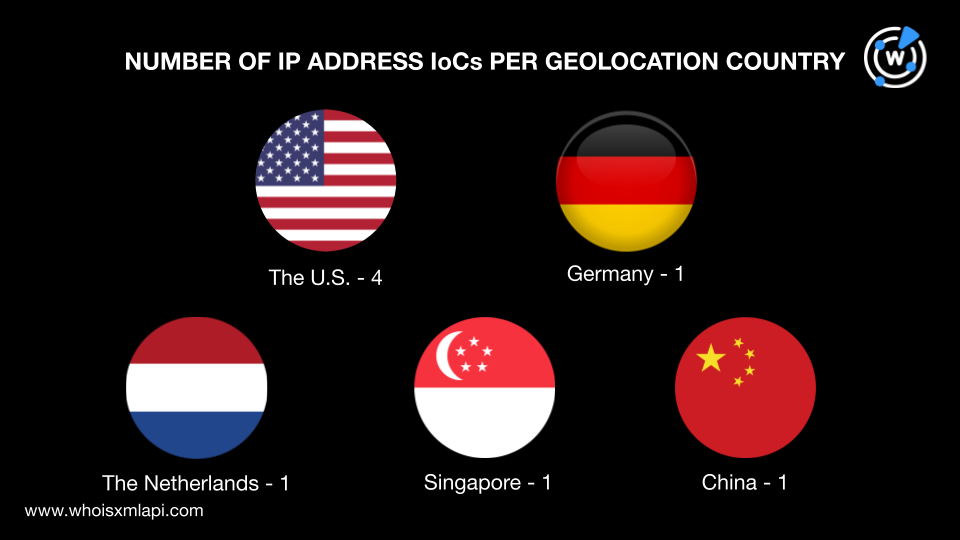
Our next step was to scour the DNS for more traces of the malicious resources used in the vulnerability exploitation.
WHOIS History API searches for the domain IoCs enabled us to discover 14 email addresses in their historical WHOIS records, three of which were public. Subjecting the three unredacted email addresses to Reverse WHOIS API searches revealed that they appeared in the current WHOIS records of 33 domains after duplicates and IoCs were removed.
Next, we performed DNS lookups for the 12 domain IoCs (including two from the subdomains tagged as IoCs), which led us to 13 unique IP addresses, excluding those already tagged as IoCs.
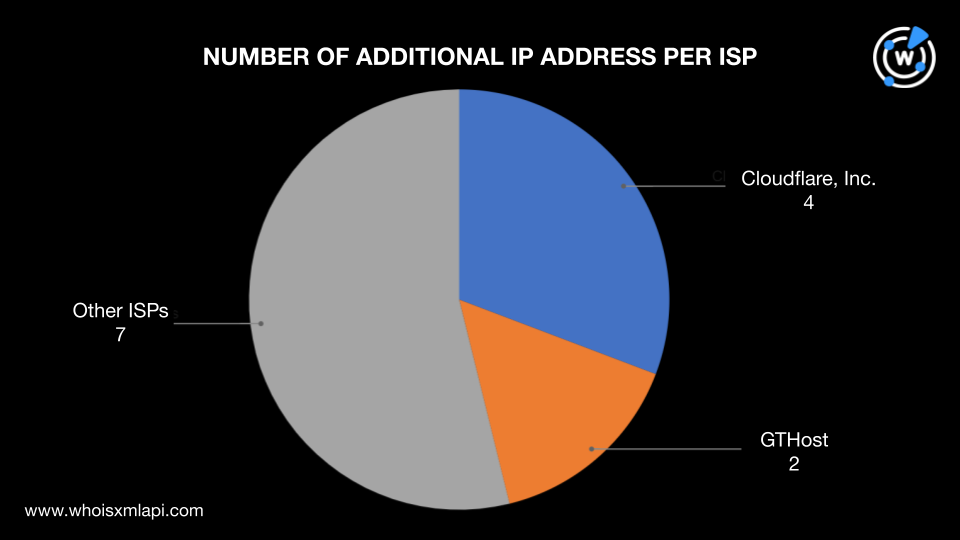
The 13 additional IP addresses were then subjected to IP geolocation lookups, which revealed that:
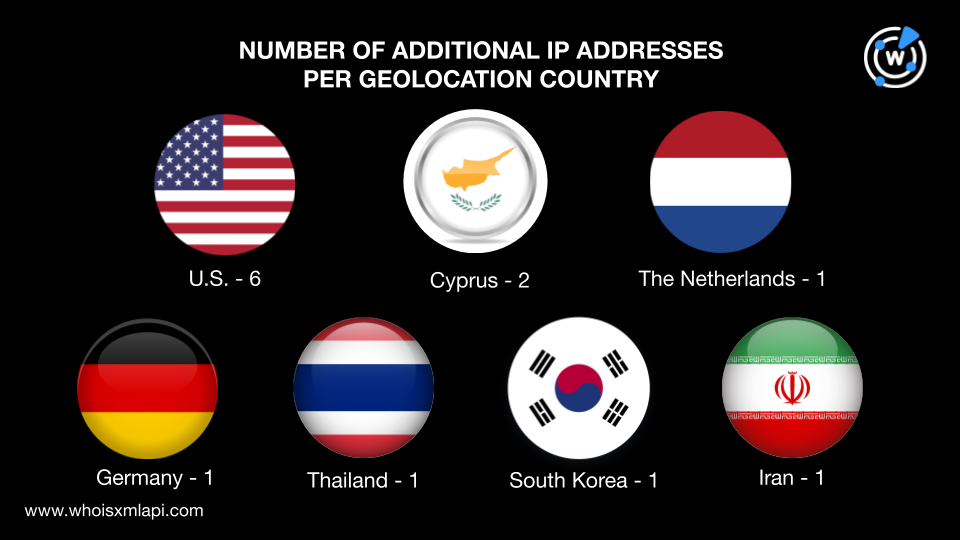
They were managed by nine ISPs—Cloudflare with four IP addresses, GTHost with two, and Signet BV, IONOS SE, Siamdata Communication Co. Ltd., Korea Telecom, QuadraNet Enterprises LLC, SoftLayer, and Pars Parva System LLC with one IP address each.
Threat Intelligence API also revealed that all 13 IP addresses were associated with various threats. A few examples are shown in the table below.
| IP ADDRESSES | ASSOCIATED THREAT TYPES |
|---|---|
| 104[.]21[.]61[.]132 | Phishing Malware Generic |
| 217[.]160[.]0[.]177 | Phishing Malware |
| 5[.]8[.]18[.]6 | Malware Generic |
| 172[.]67[.]209[.]167 | Phishing Malware Generic |
| 104[.]21[.]69[.]158 | Phishing Malware Generic |
To find more connected domains, we subjected the 13 additional IP addresses and eight IP address IoCs to reverse IP lookups, which showed that nine were potentially dedicated. They led to 211 IP-connected domains after filtering out duplicates, the IoCs, and email-connected domains.
Screenshot analyses for the IP-connected domains revealed that one domain—tedtankal[.]xyz—hosted content similar to one of the domain IoCs, areekaweb[.]com. While the two domains had redacted WHOIS records, they were both registered with GoDaddy.

As a final step, we looked for string-connected domains using Domains & Subdomains Discovery using the Starts with search parameter. They led to the discovery of 145 domains that began with these strings that appeared among the domain IoCs:
Meanwhile, a wildcard search on Threat Intelligence API using the string clicko (i.e., clicko*) revealed eight domains associated with phishing, malware, and other threats. One of the malicious domains continued to host live content.
Our investigation started out with 10 domains, two subdomains, and eight IP addresses tagged as IoCs in the zero-day exploitation of Ivanti vulnerabilities. It then led to the discovery of three public email addresses, 33 email-connected domains, 13 additional IP addresses, 211 IP-connected domains, and 153 string-connected domains. We also found that all 13 additional IP addresses and eight string-connected domains already figured in various cyber threats.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign

Sponsored byRadix

Sponsored byCSC

Sponsored byWhoisXML API
