


|
||
|
||
This past week we have been seeing some heavy CNN spam—that is, spam in the form of breaking news stories from CNN.com.
Below is a sample:
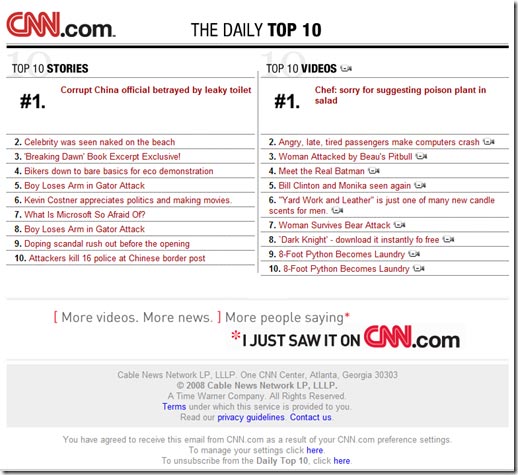
These all look like legitimate news stories, and indeed, they probably are taken straight from an actual CNN news bulletin (I don’t subscribe so I wouldn’t know). Indeed, the unsubscribe information and Terms of Use actually link to actual CNN unsubscribe pages. However, if you mouse-over all of the news links, they go to a spam web page wherein the payload is either a spam advertisement or you click on another link to download a file and flip your computer into a botnet.
This technique is known as spoofing and it has been used by spamemrs for a long time. It is a social engineering technique where they will masquerade as a legitimate source in order to trick the end-user into taking some sort of action. In phishing emails, they are attempting to recover sensitive personal user information to gain access to financial records. With this spam run, the spammers are attempting to deceive the end-user into clicking on the links to download a virus and flip them into their botnet. Because many people trust CNN and the messages look like an actual email bulletin, they can be fooled into thinking this is a legitimate email notification.
The spam outbreak “from” CNN however, quickly morphed into a new breed a couple of days later:
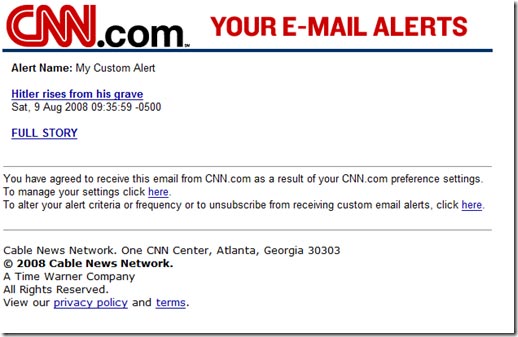
It appears that the spammers had learned from previous mistakes because this one is a little slicker. In the body contents, just like the old one it contains links to valid messages and a single payoff (the link to Full Story which contains a payload to a virus or spam). However, the message source is where we see how the spammers have evolved. They started making the source of the messages more representative of an actual CNN message. The previous spam campaign contained some textbook errors which I won’t go into in this post. However, they are still using the spoofing technique in order to get their payload delivered.
Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byRadix
