

|
||
Today X-Force, IBM’s security research and development arm, released its 2008 Midyear Trend Statistics report that indicates cyber-criminals are adopting new automation techniques and strategies that allow them to exploit vulnerabilities much faster than ever before. The new tools are being implemented on the Internet by organized criminal elements, and at the same time public exploit code published by researchers are putting more systems, databases and ultimately, people at risk of compromise.
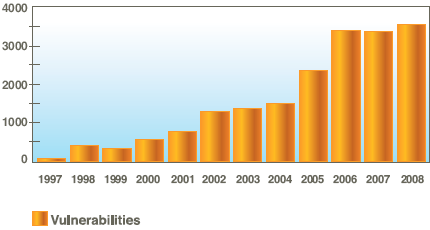
According to the X-Force report, 94 percent of all browser-related online exploits occurred within 24 hours of official vulnerability disclosure. These attacks, known-as “zero-day” exploits, are on the Internet before people even know they have a vulnerability that needs to be patched in their systems.
This phenomenon is being driven by sophisticated cyber-criminals’ adoption and evolution of automated tools for creating and delivering exploit tools, as well as the lack of a set protocol for disclosing vulnerabilities in the research industry. The practice of disclosing exploit code along with a security advisory has been the accepted practice for many security researchers. However, according to the X-Force report, vulnerabilities disclosed by independent researchers are twice as likely to have zero-day exploit code published, calling into question how researchers practice vulnerability disclosure and signifying the need for a new standard in the industry.
“The two major themes in the first half of 2008 were acceleration and proliferation,” said X-Force Operations Manager Kris Lamb. “We see a considerable acceleration in the time a vulnerability is disclosed to when it is exploited, with an accompanying proliferation of vulnerabilities overall. Without a unified process for disclosing vulnerabilities, the research industry runs the risk of actually fueling online criminal activity. There’s a reason why X-Force doesn’t publish exploit code for the vulnerabilities we have found, and perhaps it is time for others in our field to reconsider this practice.”
Key findings from the X-Force report include:
To access the X-Force 2008 Mid-Year Trend Statistics Report click here.
Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byCSC

Sponsored byVerisign

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byWhoisXML API
