


|
||
|
||
Palo Alto Networks’ Unit 42 tracked and monitored the most recent Ashen Lepus aka WIRTE APT campaign that leveraged a new malware suite they have dubbed “AshTag.” The group conducted espionage activities against Arabic-speaking government entities. This time, however, the researchers witnessed a tangible evolution in the group’s operational security and TTPs. The actors specifically enhanced their custom payload encryption, infrastructure obfuscation by using legitimate subdomains, and in-memory malware execution to minimize forensic artifacts.
That said, were we able to uncover more potentially connected artifacts using the 12 subdomains Unit 42 has identified as IoCs.
We extracted 10 unique domains from the 12 subdomains identified as IoCs, bringing our total number of IoCs to analyze to 22. Our in-depth analysis of the AshTag IoCs led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Queries for the 12 subdomains identified as IoCs on Jake AI showed that all of them have been flagged for malware distribution between 13 and 16 December 2025. While 11 of them could not be categorized, one—auth[.]onlinefieldtech[.]com—fell under several categories, including Technology & Computing, Internet, and Business & Finance, along with an unrelated category Style & Fashion.
We began our investigation by querying the 10 domains identified as IoCs on the WhoisXML API MCP Server, which revealed that none of them were owned by legitimate entities.
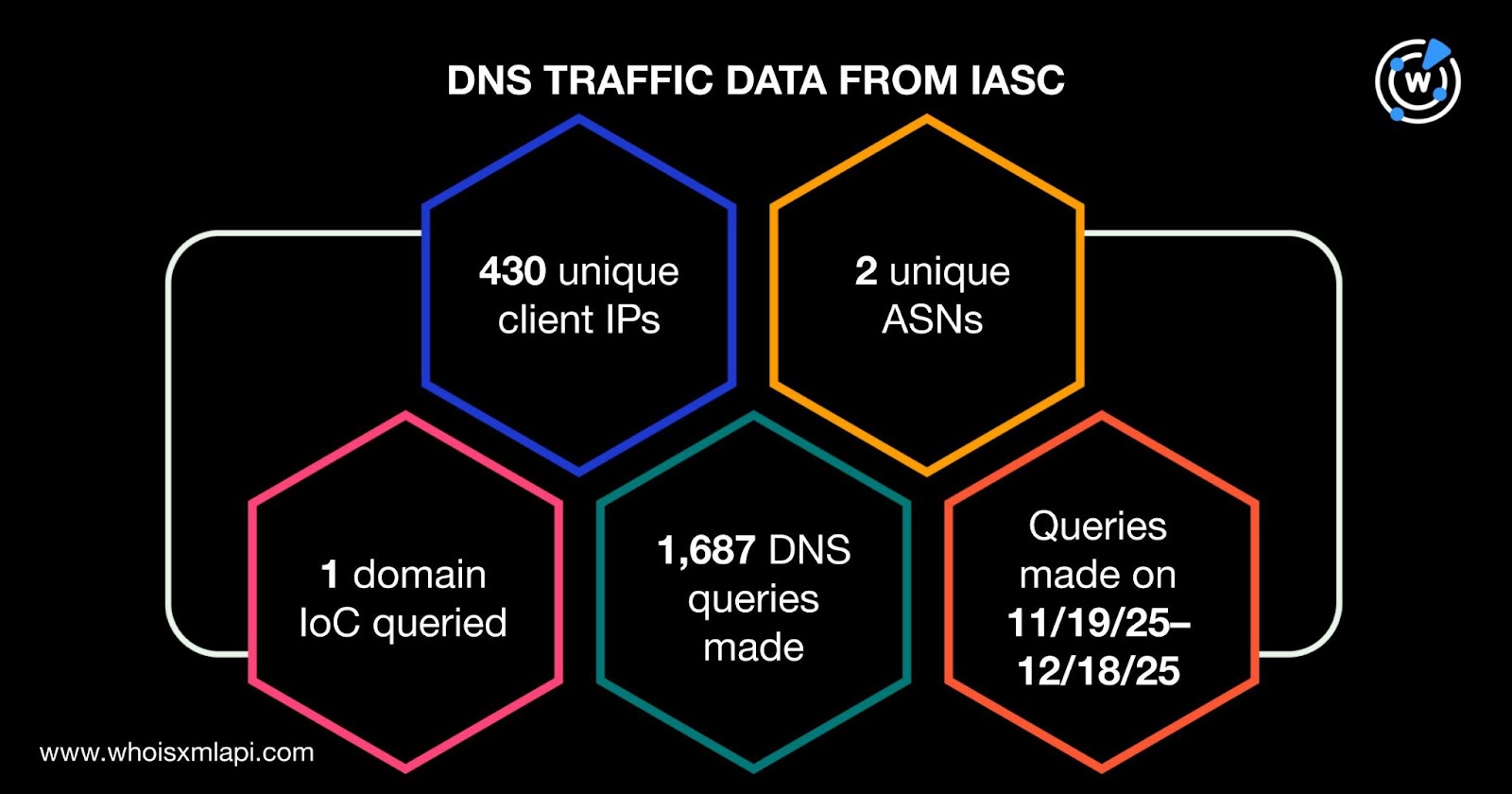
Sample IASC network traffic data for the 10 domains identified as IoCs showed that 430 unique client IP addresses under two distinct ASNs communicated with the domain IoC api[.]softmatictech[.]com via 1,687 DNS queries between 19 November and 18 December 2025.
In addition, the results of our First Watch Malicious Domains Data Feed queries showed that two domains identified as IoCs were deemed likely to turn malicious 75—752 days before being dubbed as such on 11 December 2025.
| DOMAIN IoC | FIRST WATCH DATE | NUMBER OF DAYS BEFORE REPORT DATE |
|---|---|---|
| healthylifefeed[.]com | 20 November 2023 | 752 |
| systemsync[.]info | 27 September 2025 | 75 |
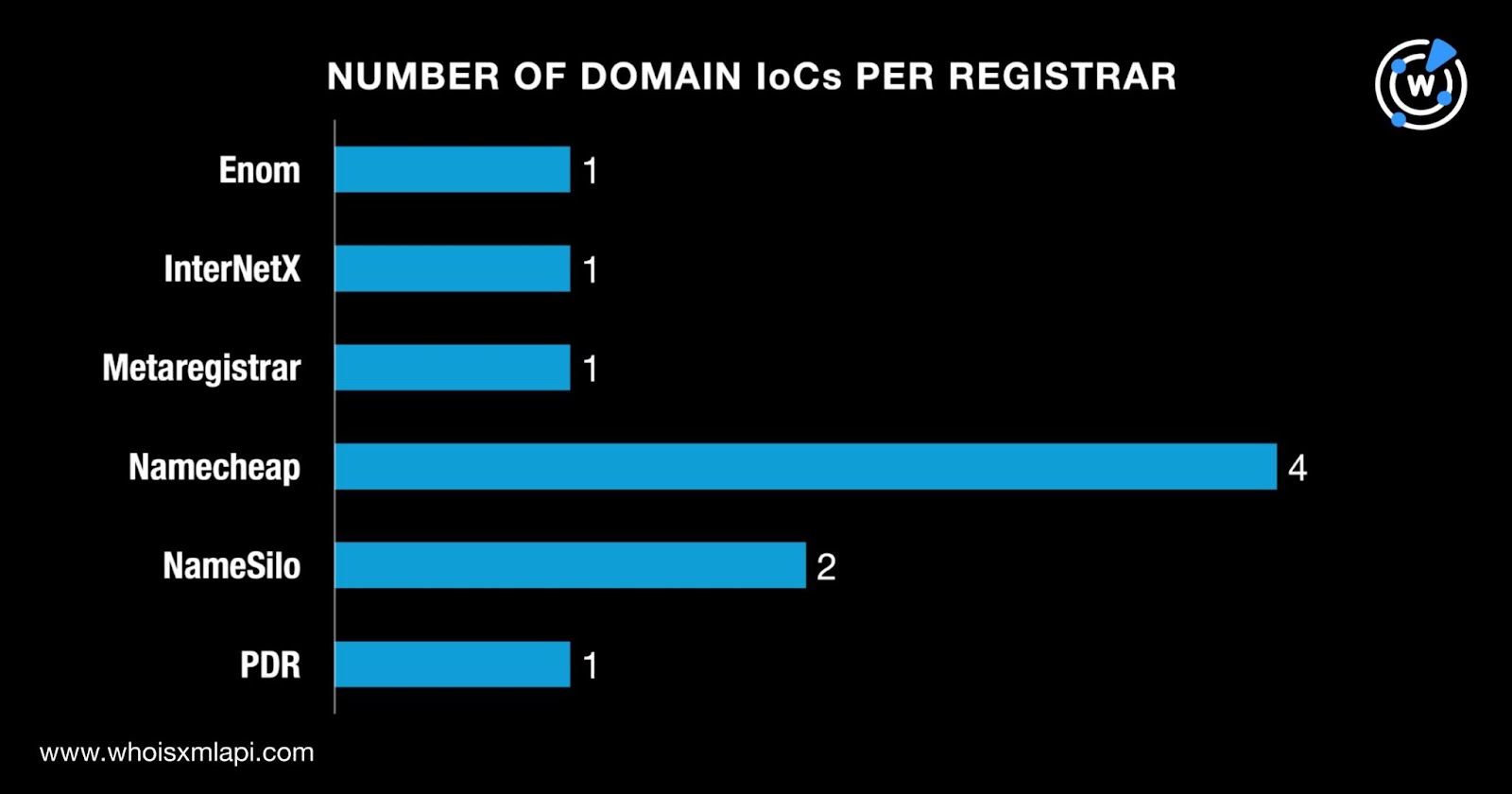
We then queried the 10 domains identified as IoCs on WHOIS API and discovered that:
Namecheap was the top registrar, accounting for four of the domains. NameSilo accounted for two domains while Enom, InterNetX, Metaregistrar, and PDR administered one domain each.
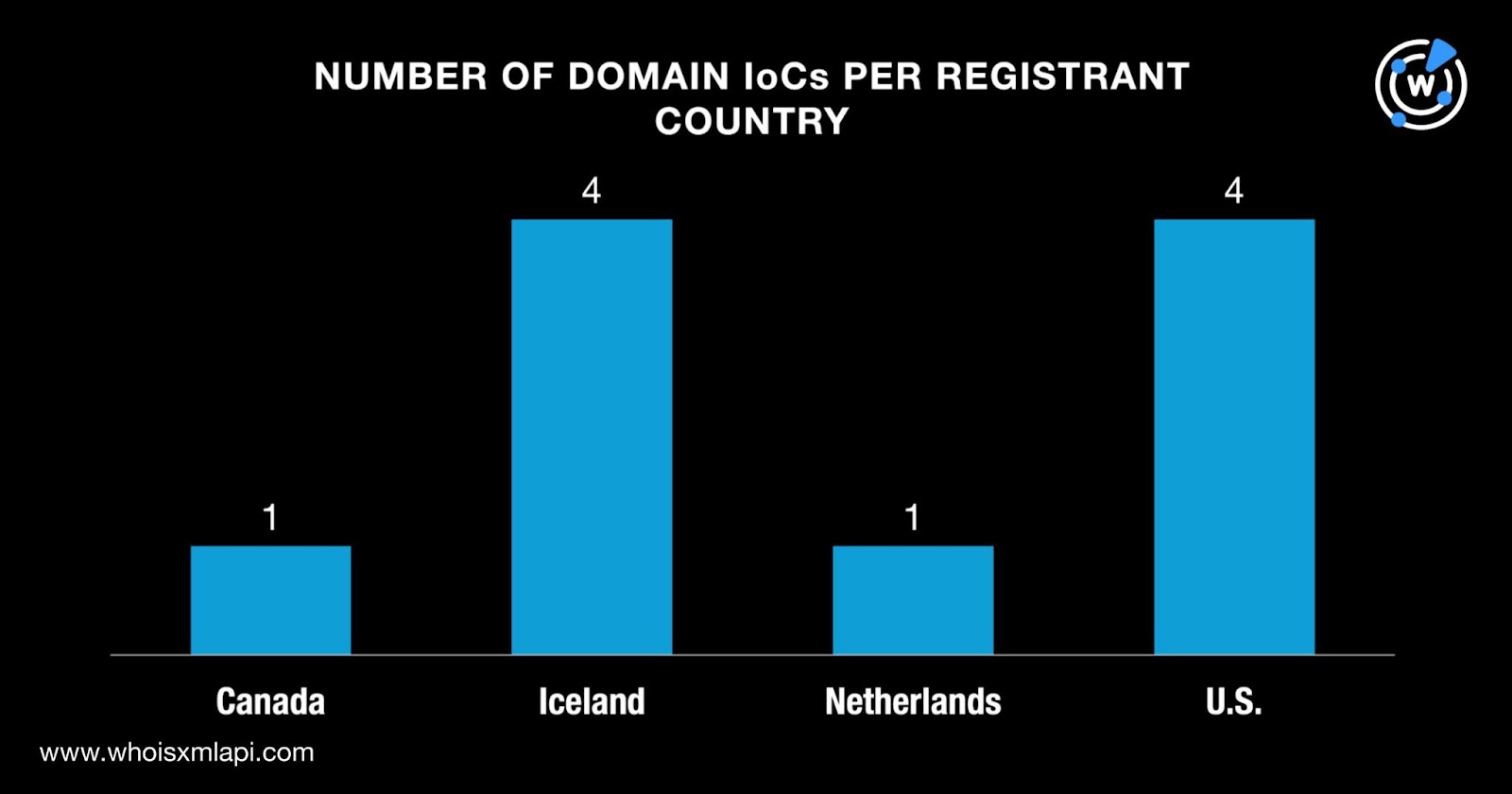
Finally, four domains each were registered in Iceland and the U.S. while one each was registered in Canada and the Netherlands.
A DNS Chronicle API query for the 10 domains identified as IoCs, meanwhile, showed that they recorded 1,425 domain-to-IP resolutions over time. The domain technology-system[.]com posted the oldest resolution on 7 February 2017.
| DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| technology-system[.]com | 77 | 02/07/17 | 08/30/25 |
| healthylifefeed[.]com | 225 | 04/28/17 | 11/04/17 |
| techtg[.]com | 294 | 04/29/17 | 05/30/25 |
| widetechno[.]info | 556 | 04/29/17 | 08/14/25 |
| techupinfo[.]com | 95 | 07/09/18 | 08/30/24 |
Next, we began our search for new artifacts by querying the 10 domains identified as IoCs on WHOIS History API and found out that six of them had email addresses in their historical WHOIS records. We uncovered 36 unique email addresses in all. Upon further scrutiny, we determined that nine were public email addresses.
According to the results of our Reverse WHOIS API queries for the nine public email addresses, none of them were present in any other domain’s current WHOIS records. All of them, meanwhile, appeared in the historical WHOIS records of 29 unique email-connected domains after those already identified as IoCs were filtered out.
Next, we queried the 10 domains identified as IoCs on DNS Lookup API, which showed that only one—techupinfo[.]com—actively resolved to a single IP address.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byRadix

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byWhoisXML API
