


|
||
|
||
Proofpoint tracked several state-sponsored and financially motivated threat clusters that used SquarePhish2 and Graphish, among other phishing tools, to trick users into granting the actors access to their Microsoft 365 accounts by bypassing the OAuth device code authorization process. Successfully compromising the victims’ accounts reportedly led to account takeover, data exfiltration, and other serious consequences. The researchers identified at least 44 IoCs associated with the attacks in their report.
Note that four of the 21 subdomains identified as IoCs can have multiple variations, which could mean a substantially bigger volume. Any number of target organization names can be appended to the subdomain onlinedocuments-[OrganisationName][.]vxhwuulcnfzlfmh[.]live, for example.
After extracting unique domains from the subdomains identified as IoCs, we collated 52 IoCs. Next, we weeded out legitimate domains from the 28 identified as IoCs using Jake AI. Our queries revealed that six of them were legitimate, reducing the number of domains for further analysis to 22. In the end, we analyzed 46 IoCs comprising 21 subdomains (including four with multiple variations), 22 domains, one IP address, and two email addresses.
Using our homegrown tools to investigate the threat, we uncovered these findings:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Our quest to unearth more information about the threat began with Jake AI queries for 17 of the 21 subdomains (excluding the four with multiple variations). We discovered that four of them are worth avoiding as they could well be on their way to becoming phishing pages. One such case is illustrated below.

We looked closer into the two email addresses identified as IoCs next via Jake AI as well. One of them could be dangerous to interact with due to its association with a phishing campaign.
First off, we queried the 22 domains identified as IoCs on the First Watch Malicious Domains Data Feed and found out that five of them were deemed likely to turn malicious 65—93 days before they were reported as such on 18 December 2025.
| DOMAIN IoC | FIRST WATCH DATE | NUMBER OF DAYS BEFORE REPORT DATE |
|---|---|---|
| blitzcapital[.]net | 09/16/25 | 93 |
| bluecubecapital[.]com | 09/17/25 | 92 |
| vxhwuulcnfzlfmh[.]live | 10/06/25 | 73 |
WHOIS API queries for the 22 domains identified as IoCs revealed that:
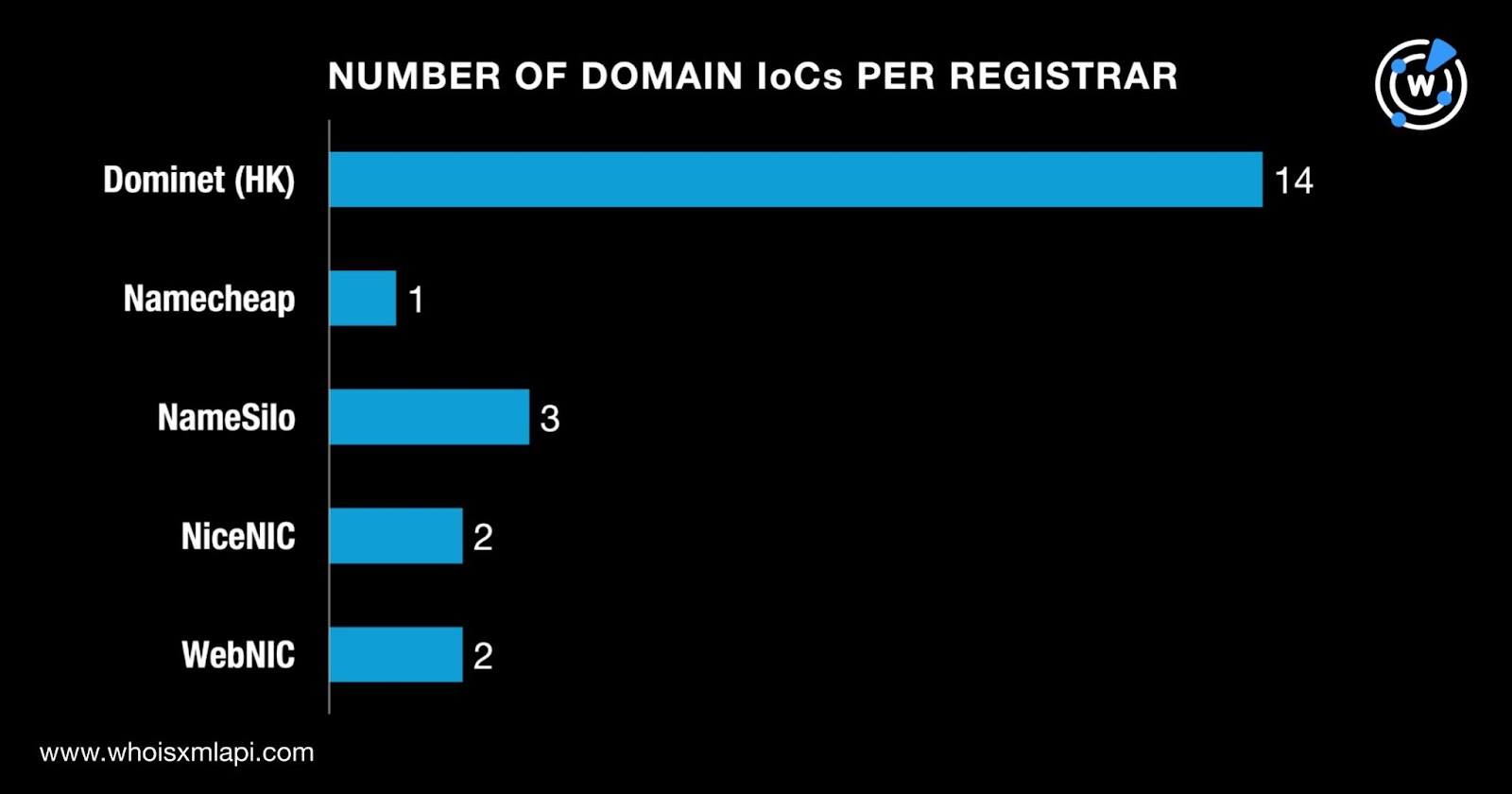
While two of them did not have registrant countries on record, the remaining 20 were registered in four countries—16 in Malaysia, two in Thailand, and one each in Iceland and the U.S.
DNS Chronicle API queries for the 22 domains identified as IoCs showed that 21 of them had historical domain-to-IP resolutions. All in all, the 21 domains posted 823 resolutions over time. The domain bluecubecapital[.]com recorded the oldest first resolution date—5 February 2017.
| DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| bluecubecapital[.]com | 261 | 02/05/17 | 12/25/25 |
| blitzcapital[.]net | 172 | 04/28/17 | 06/02/25 |
| magnavite[.]com | 101 | 06/03/17 | 08/09/19 |
| virtoshare[.]com | 56 | 11/10/17 | 10/10/25 |
| vaultally[.]com | 136 | 11/15/19 | 01/03/21 |
An IP Geolocation API query for the sole IP address identified as an IoC showed that while it did not have an ISP on record, it was geolocated in the Netherlands.
After obtaining more information about the IoCs connected to SquarePhish2 and Graphish, we searched for other possibly connected artifacts. We started our hunt with WHOIS History API queries for the 22 domains identified as IoCs. We learned that nine of them had 35 unique email addresses in their historical WHOIS records. Further scrutiny revealed that three of them were public email addresses.
Next, we queried the three public email addresses on Reverse WHOIS API and discovered that while none of them appeared in current WHOIS records, all of them were present in historical WHOIS records. Our search, in fact, turned up 91 unique email-connected domains after those already identified as IoCs were filtered out.
We then queried the 22 domains identified as IoCs on DNS Lookup API and found out that 14 of them actively resolved to 23 unique IP addresses after the sole IoC was filtered out.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byRadix

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byCSC
