


|
||
|
||
A whopping 600 million cyberattacks every single day—that’s what organizations face nowadays, according to the Microsoft Digital Defense Report. The sheer volume of threats—coupled with the expanding attack surfaces resulting from digital transformation, scaling, and other factors—has made attack surface monitoring a must even for organizations that were previously happy with a more traditional vulnerability management approach.
While the market offers a plethora of attack surface monitoring tools, choosing the best fit for your organization’s specific needs and existing infrastructure can be daunting. To help with this decision, we compared some of the top tools organizations use for attack surface monitoring. We examined their pricing structures and key ASM capabilities—asset discovery, vulnerability scanning, risk prioritization, and continuous monitoring.
Different organizations have different needs, however, there are some basics that every attack surface monitoring tool needs to cover:
A good attack surface monitoring tool should be able to help security teams discover both known and unknown internet-facing assets to build a reliable asset inventory. The most important part here is coverage—how many assets (and asset types) a tool can find. Good attack surface monitoring tools use a mix of reconnaissance methods. Also, what sets a good tool apart is the ease of adding root assets and the speed at which it can discover related assets—this process should be easy and shouldn’t take more than a few hours.
An organization’s attack surface consists of its exposed assets and their vulnerabilities. So, these tools should scan newly discovered and existing assets for vulnerabilities and track changes over time.
The effectiveness depends on the scanner’s detection capabilities, the quality of its vulnerability databases, and how well it handles false positives—some use payload-based scanning to reduce unnecessary alerts and some employ multiple scanners. The stronger the scanning engine and data sources, the more accurate the risk picture.
Good attack surface monitoring tools let teams prioritize vulnerabilities based on risk, rather than severity. So, advanced tools combine risk scores like CVSS or EPSS, exploitation data, and sometimes the business impact of affected assets.
Some tools go as far as to offer automated remediation, but it’s a double-edged sword. On the one hand, it’s very nice to automatically close a certain port on all systems without the need to set up a thousand tasks for IT engineers. It saves a lot of time and effort. On the other hand, that usually requires extremely complex setups. The tools that are capable of this cost a fortune, and the time spent making it work could be roughly the same as time saved by automating some of the tasks.
Attack surface mapping could be a one-time exercise when it comes to offensive security, but for defensive purposes, it should be continuous—and becomes attack surface monitoring.
The meaning of “continuous” varies by tool—some scan weekly, while others trigger scans based on real-time updates like new vulnerabilities. A few allow custom scan frequencies per asset, but only a handful run non-stop without delays—and only these can provide true real-time visibility.
These are the four staples of attack surface monitoring that every tool should be able to cover. Now, let’s get to our tool selection.
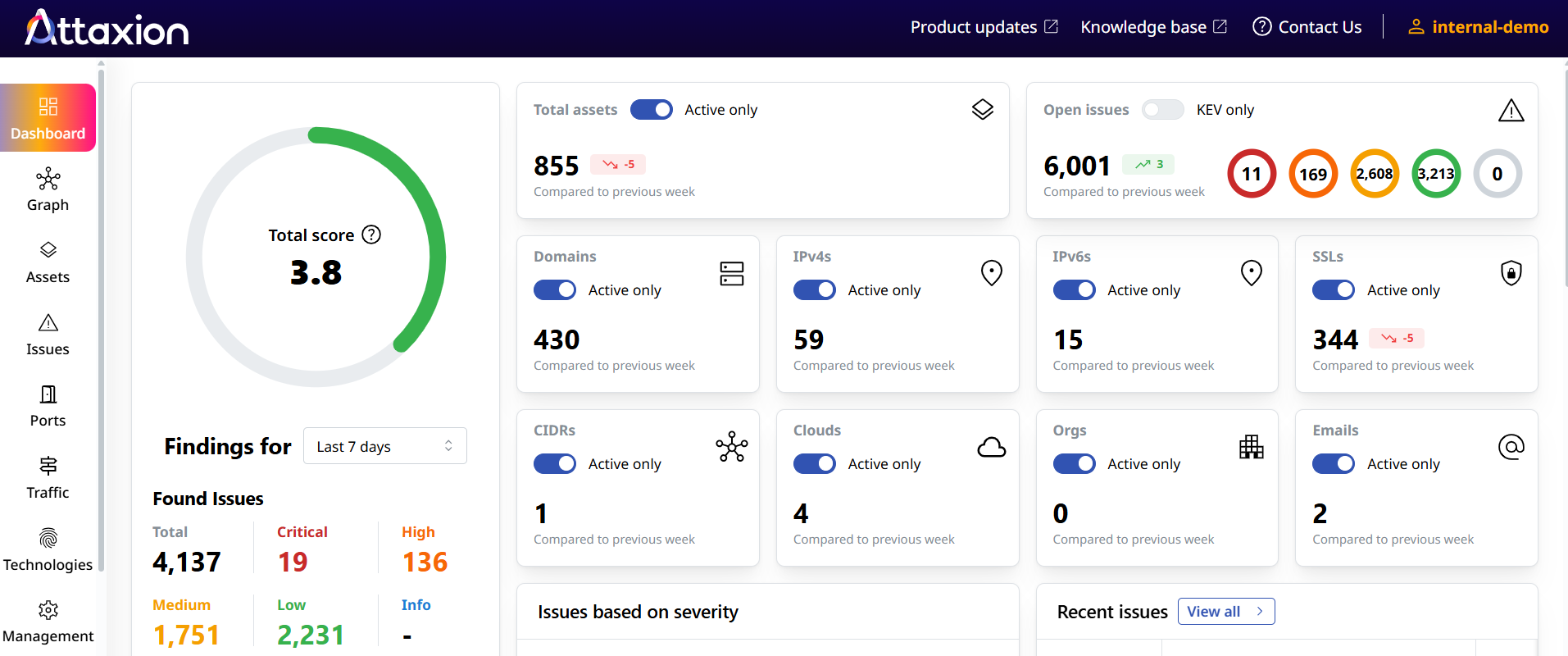
Attaxion is an advanced cybersecurity platform designed to support external attack surface management and other cybersecurity processes. It focuses on automatically discovering internet-facing assets and continuously scanning them for vulnerabilities and other security issues with a penetration testing automation tool, among other things.
One of Attaxion’s most notable differentiators is its extensive coverage of external assets. The platform’s modern reconnaissance techniques enable it to identify and validate a wide range of digital assets, including web applications, domains, IP addresses, cloud resources, and even exposed email addresses.
Among Attaxion’s main features are:
Pricing
Attaxion offers four pricing plans, with its Starter plan priced at $129 per month for up to 40 assets. Its Plus plan costs $349 per month for up to 120 assets, while its Business plan costs $949 per month for up to 360 assets. Users can get two months free if they pay annually.
For organizations that need to scan more than 360 assets, Attaxion offers an Enterprise plan, with pricing dependent on the size of the attack surface. Attaxion also has a 30-day free trial.
Strengths
Weaknesses
ProjectDiscovery is an organization known for its open-source tools, including the vulnerability scanner Nuclei and the passive subdomain discovery tool Subfinder. Its commercial offering, ProjectDiscovery Cloud, is a vulnerability management platform that integrates with the Crunchbase API to identify an organization’s subsidiaries and their associated assets. It supports further asset discovery through its other open-source tools that pull asset lists from public cloud platforms, scan open ports, and crawl web pages.
ProjectDiscovery’s asset discovery engine runs continuously, keeping the asset inventory up to date by discovering internet-exposed and cloud assets. On the Enterprise plan, it continuously scans for vulnerabilities and misconfigurations, while the free plan provides only one monthly scan. The platform automatically retests open vulnerabilities to track their status.
Pricing
ProjectDiscovery’s pricing is currently not publicly available. Not so long ago (and the internet still remembers), they offered a plan called “Growth,” which was priced at $3,500 annually and covered up to 100 assets. This plan is no longer on their pricing page anymore.
ProjectDiscovery doesn’t offer a free trial period, but has a free tier with asset discovery limited to 10 new domains per month linked to the business email used during sign-up. The free plan is very limited in its functionality and performs a once-a-month vulnerability scan.
Strengths
Weaknesses
Inconsistent vulnerability scanning results (users have reported both false positives and false negatives).
A free trial would be more useful than a free plan that is too limited.
Has various bugs and glitches. 3. Censys ASM
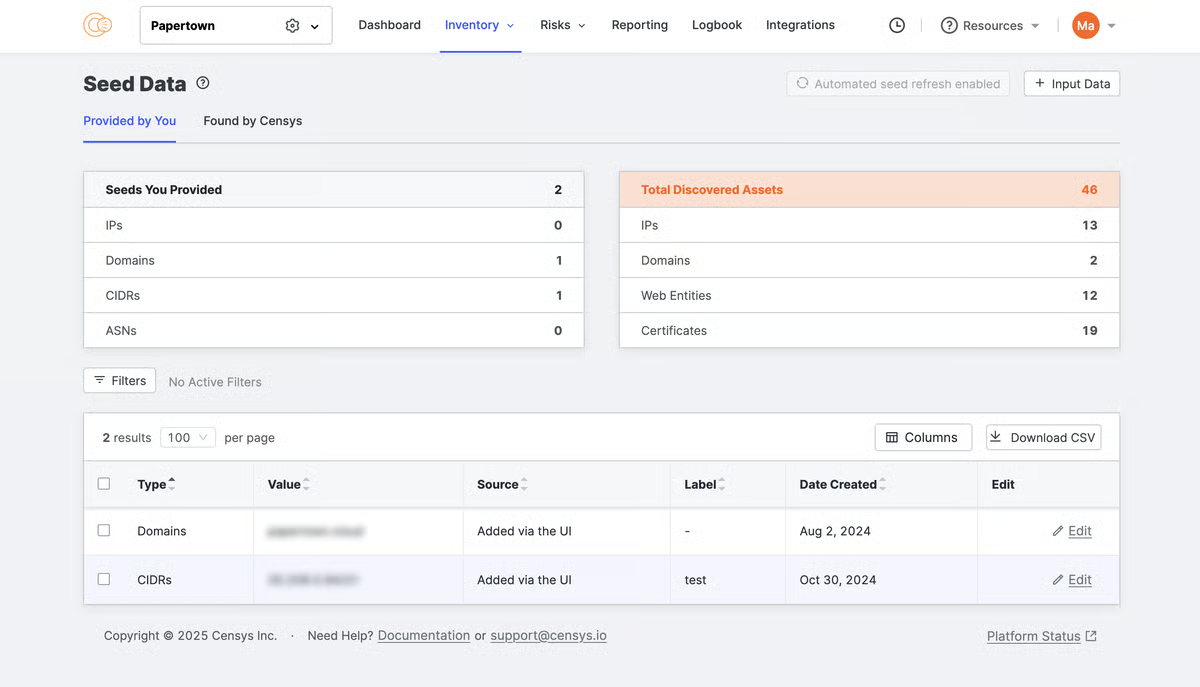
Censys is a company primarily known for Censys Search, a search engine for internet-facing assets. It also offers the Censys ASM platform—an external attack surface management (EASM) platform that relies on Censys Search for asset discovery. To start using Censys, users provide seed assets, which then undergo a verification process.
Once the seed assets are verified, Censys ASM discovers related assets (e.g., domains, subdomains, IPv4 and IPv6 addresses, cloud buckets, CIDRs, ASNs, and SSL certificates).
Censys ASM presents scan results on the “Risk Instances” tab, allowing users to filter by asset type, environment, risk type, and severity. The platform offers remediation suggestions and integrations with Jira and ServiceNow for ticketing. It also connects with security tools like Microsoft Sentinel, Qualys VMDR, Tenable VM, and Splunk for event tracking and vulnerability management.
Pricing
Censys’ pricing for its ASM solution is not published on its website, but it was previously listed on Amazon at $93,000 per year (it was delisted as of August 2025).
Strengths
Weaknesses
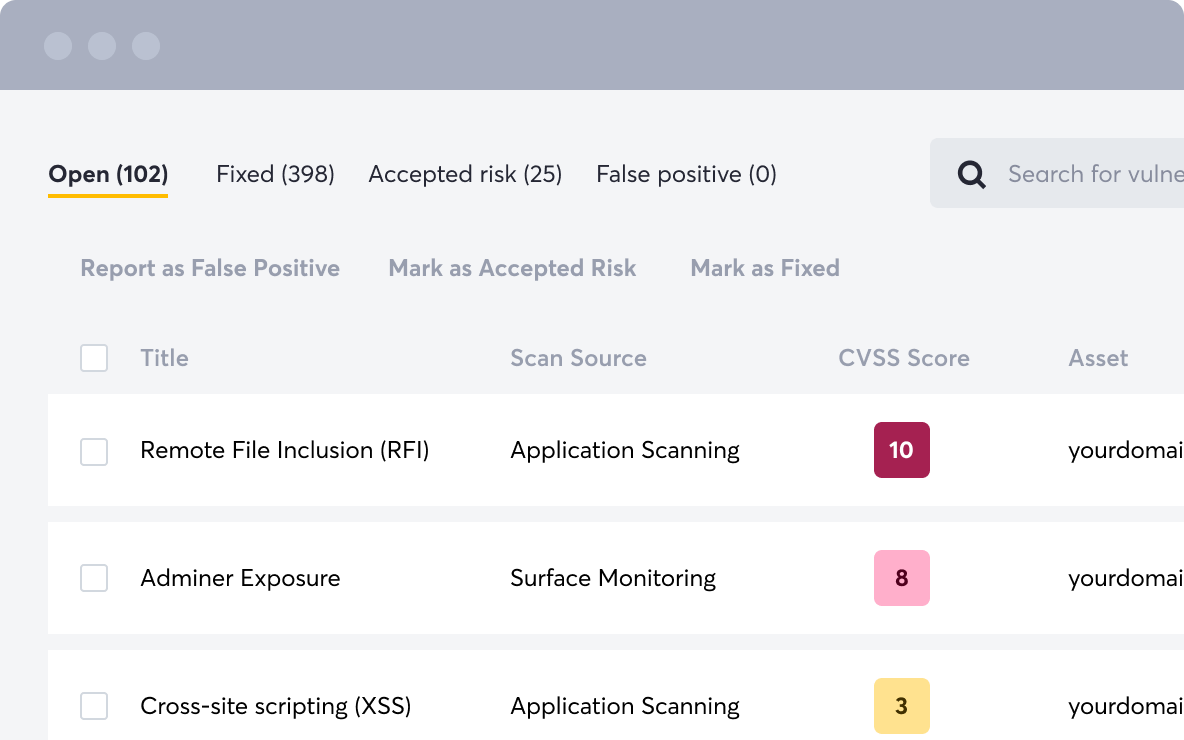
Detectify is an EASM platform that also performs dynamic application security testing. It has automatic asset discovery methods (scraping, brute forcing, DNS zone transfer, SSL monitoring, application scanning, etc.) for subdomains, IP addresses, and cloud instances, but users can also manually add subdomains by importing them or integrating with AWS, Azure, Cloudflare, GCP, GoDaddy, and other providers.
Detectify uses proprietary scanners and draws from an ethical hacker community to identify issues early, employing payload-based scanning for high certainty. For remediation purposes, the platform provides descriptions, vulnerable asset lists, and sometimes code snippets or screenshots. It continuously monitors the attack surface for new assets, technologies, and vulnerabilities, and integrates with various apps like Slack, Jira, Trello, and Splunk via Workato.
Pricing
Detectify’s pricing starts at approximately $430/month, or $3,690/year, covering up to 25 subdomains. It also offers a 14-day free trial.
Strengths
Weaknesses
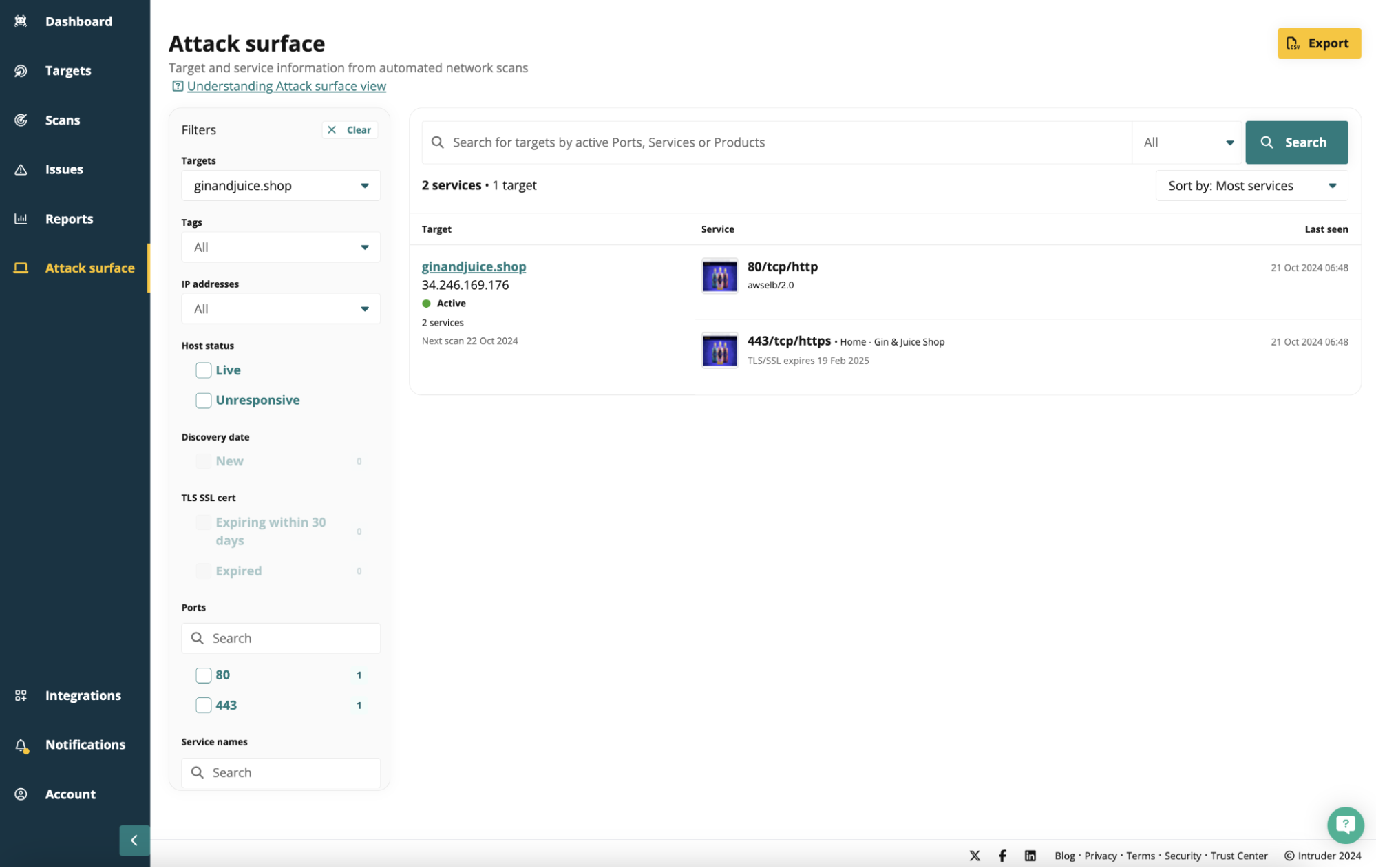
Intruder.io is a cloud-based platform that specializes in vulnerability management and ASM, designed to help organizations secure their attack surface and meet compliance requirements, such as PCI DSS.
Its key features revolve around its diverse set of vulnerability scanners, which vary by plan: the Essential plan uses OpenVAS; the Cloud plan combines OpenVAS with Nuclei; the Pro plan utilizes Tenable Nessus; and Enterprise plans blend Nessus with Nuclei. For web applications, it relies on OWASP ZAP.
Intruder supports scheduled network scans (weekly, monthly, quarterly, and daily on custom plans) and manual initiation. It offers “Emerging Threat” scans on Cloud plans and above and “Rapid Response” scans on the Enterprise plan for actively exploited threats. It also supports authenticated web application scanning and API schema testing.
Pricing
Intruder’s pricing is tiered, depending on the chosen plan and number of targets or web applications. The Essential plan starts at $99/month, the Cloud plan at $180/month, and the Pro plan at $240/month, all for five infrastructure licenses (excluding VAT). Pricing for the Enterprise tier is available upon request by contacting sales. There is also a 14-day free trial period available.
Strengths
Weaknesses
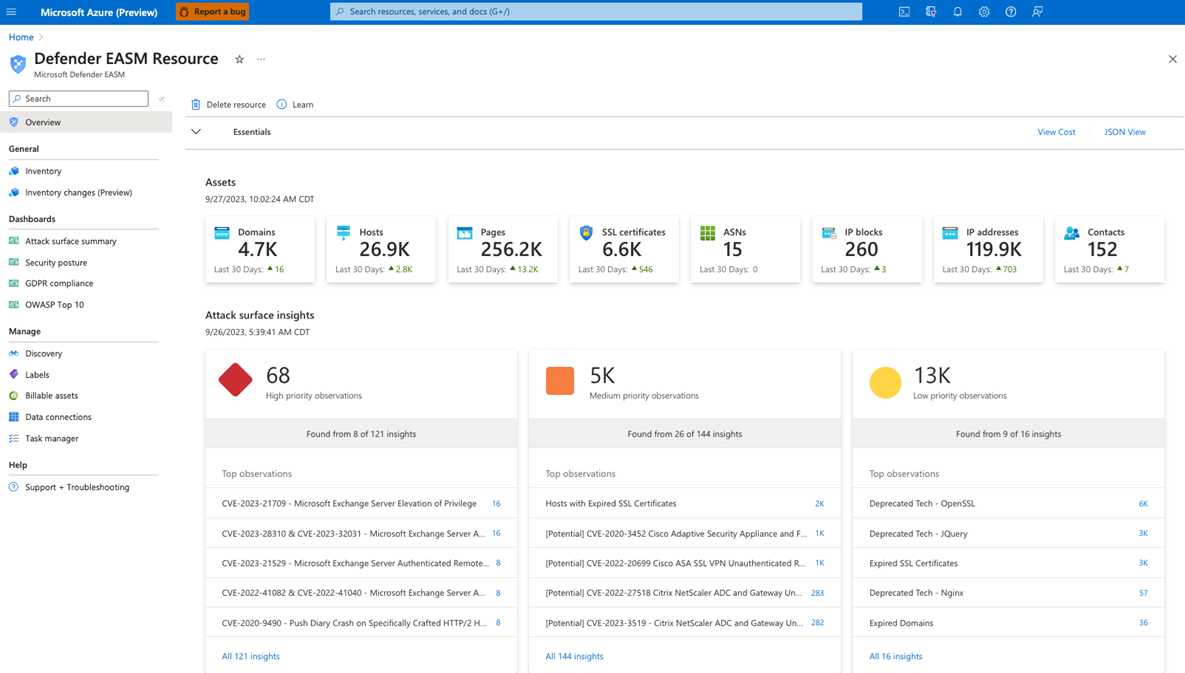
Microsoft Defender EASM is Microsoft’s dedicated solution for continuously discovering and mapping an organization’s digital attack surface. It is part of the broader Microsoft Defender for Cloud product line.
A key differentiator is its deep integration with Azure (it requires an Azure account), and its policy engine automation, which allows security teams to set up rules for automatic asset status adjustments, helping with prioritization and filtering.
Pricing
Microsoft offers a 30-day free trial period. Its pricing is set at $0.011 per asset per day, although the definition of an “asset” can be ambiguous, as website pages are reportedly counted as assets, which differs from typical EASM platforms.
Strengths
Weaknesses
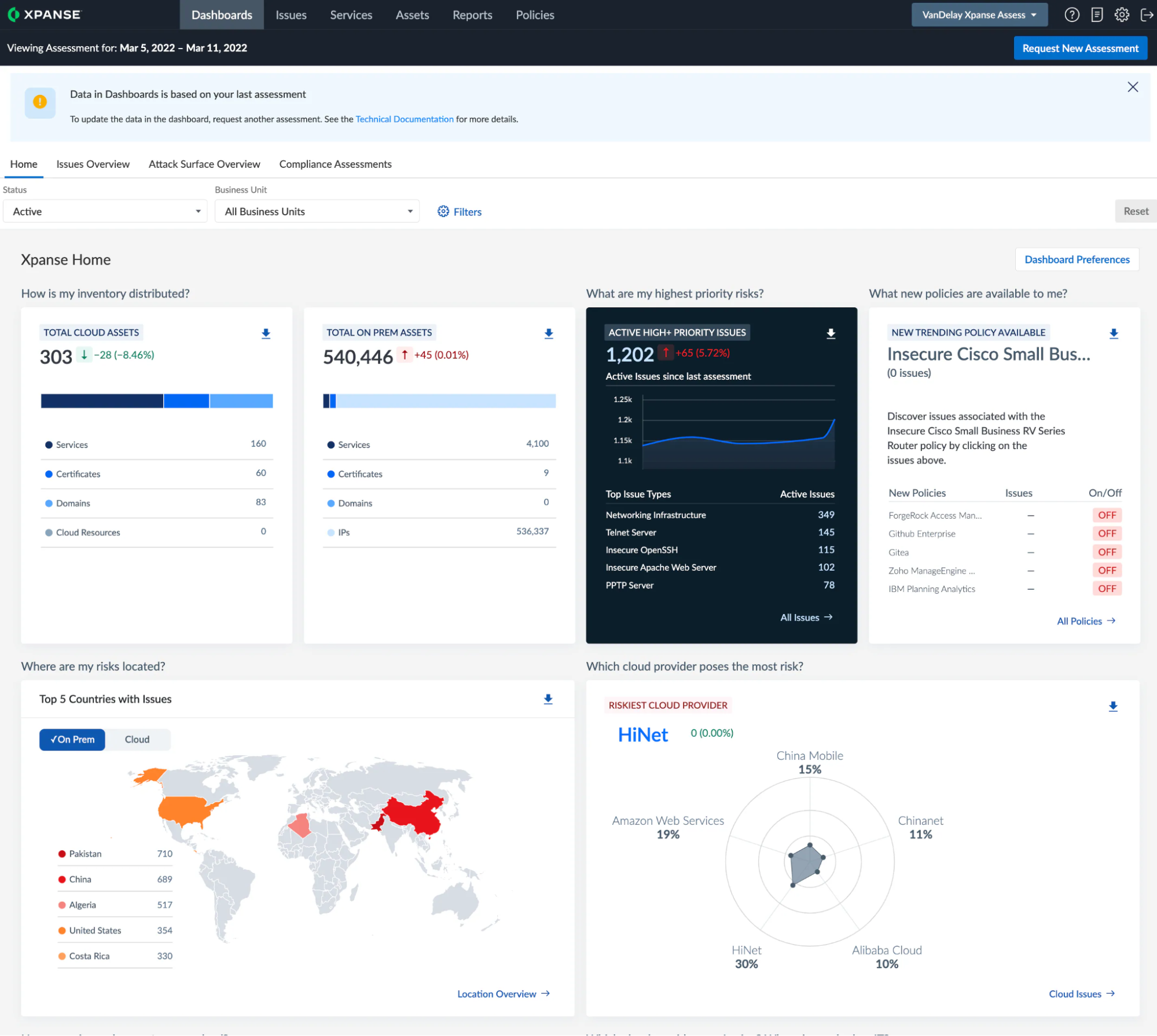
Palo Alto Cortex Xpanse is a popular ASM solution that offers extensive flexibility and customization for cybersecurity teams. Its asset discovery involves the use of various reconnaissance methods and open-source intelligence. It also uses a proprietary, payload-based scanner to find vulnerabilities and confirm their exploitability, and incorporates advanced prioritization metrics like CVSS, EPSS, exploit maturity, and in-the-wild exploitation data, with options for custom scoring.
Cortex Xpanse’s continuous monitoring involves frequent global IPv4 space scans and daily scans of customer-attributed assets, with customizable dashboards, reports, and alerts via email or messengers.
Pricing
Palo Alto Cortex Xpanse’s pricing is not publicly disclosed, but online sources suggest an approximate cost of $100,000 per year per unit, with additional costs for a resident engineer (around $443,000 per year) and initial deployment services for setup.
Strengths
Weaknesses
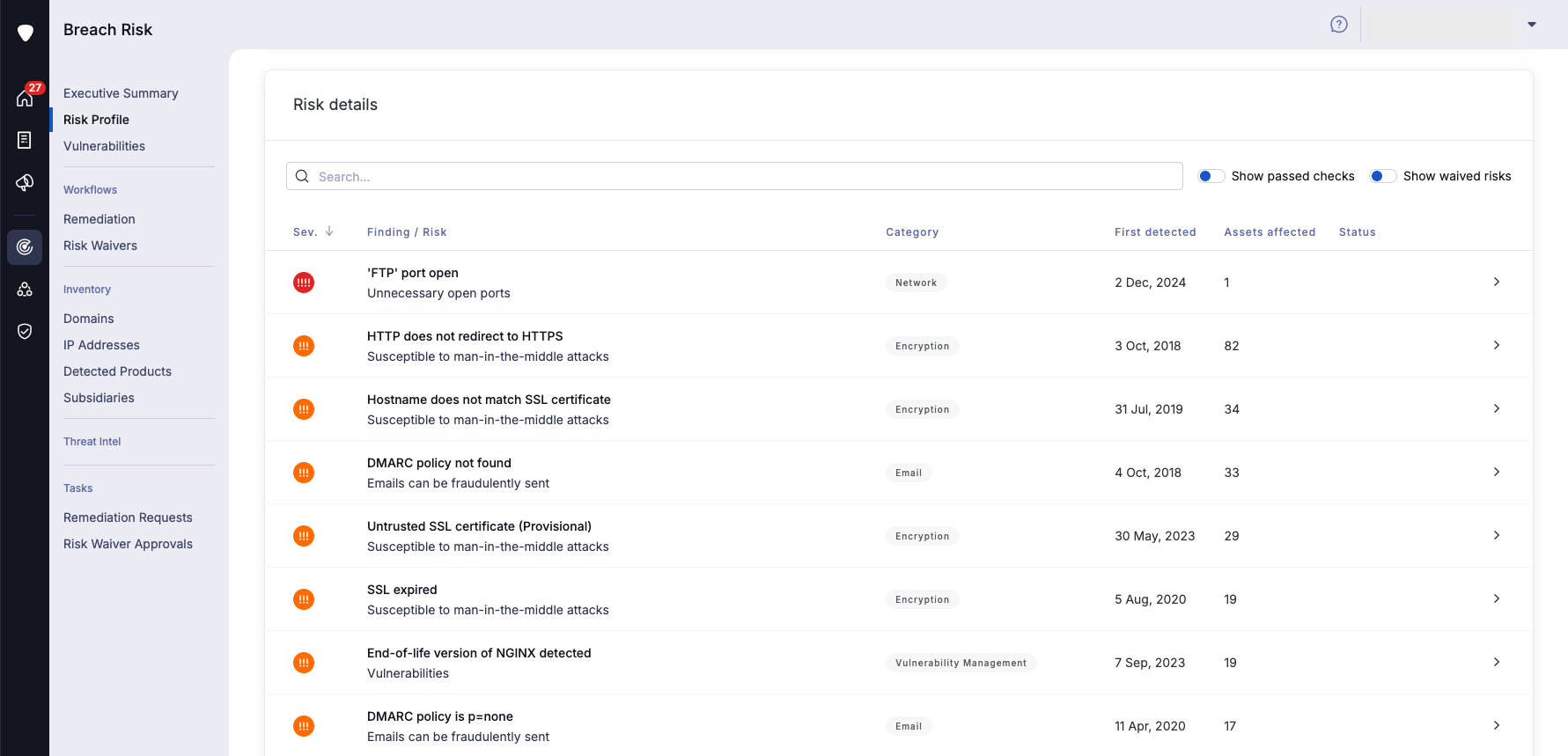
UpGuard is a well-established vendor in the third-party risk management (TPRM) space, offering products like UpGuard Vendor Risk (TPRM), UpGuard Breach Risk (EASM), and UpGuard Trust Exchange (security information sharing). Its Breach Risk product focuses on EASM, providing daily asset scanning, risk prioritization, and remediation workflows with email notifications and integrations with Jira and Asana.
The platform detects vulnerabilities by analyzing associated products, security headers, IP/domain reputation, SSL implementation, network layer security, and email implementation. It uses a non-intrusive scanner, classifies vulnerabilities as “verified” or “unverified,” and offers CVSS, EPSS, and CISA KEV status for CVEs. UpGuard Breach Risk also continuously monitors websites and potential typosquatting.
Pricing
UpGuard Breach Risk starts at $3,000 per year. You can also combine it with Vendor Risk, at $79 per month for each vendor. A Starter plan combining Breach Risk and Vendor Risk (for up to 50 vendors) is available for $19,188 per year. While there’s a free plan for Vendor Risk, it’s not available for Breach Risk, though a 14-day free trial is offered for all products.
Strengths
Weaknesses
The optimal choice depends on your organization’s specific needs, budget, and desired depth of features. For enterprises with large budgets and complex infrastructures, Palo Alto Cortex Xpanse is a great choice for attack surface monitoring, with its frequent global and daily asset scans, validation for everything, and automated remediation.
However, organizations with smaller budgets may find Attaxion a more suitable fit as it is the most affordable platform with comprehensive asset discovery coverage and continuous monitoring capabilities. Attaxion continuously scans the organization’s attack surface for new assets and vulnerabilities, offering a low false positive rate and rich context for the discovered issues.
Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byDNIB.com
