


|
||
|
||
CloudSEK recently named 15 of the top threats to watch out for in 2026. We managed to cover most of them in the past year or so, including LockBit, BlackCat, Cl0p, RedLine Stealer, Agent Tesla, Mirai, Dridex, Lumma, and Bumblebee. That said, we zoomed in on QakBot this time.
According to the report above, QakBot is one of the most notorious access Trojans and loaders to date. Often distributed via phishing emails, it has been known for harvesting credentials, maintaining C&C access, and delivering various payloads. It is also well-known for rapid lateral movement useful for targeted attacks and serving ransomware. Its usual victims? Enterprises that heavily rely on email.
To conduct our in-depth investigation, we looked for a list of IoCs and found this from Trellix. We extracted 929 unique domains from the extensive list of URLs they published. Aided by the WhoisXML API MCP Server, we weeded out the legitimate domains, which may have been compromised for various attacks, from the domain list. We ended up with 492 domains. We focused on 125 domains to better manage the analysis.
We also extracted 19 unique subdomains from the Trellix IoC list. Adding that to the 125 domains, we studied a total of 144 IoCs. Our investigation led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We first looked into the 19 subdomains identified as IoCs using Jake AI. While 18 of them were benign and associated with legitimate domains, one—books[.]ttc[.]edu[.]sg—was flagged for malware distribution. Specifically, while its main domain—ttc[.]edu[.]sg is registered to Trinity Theological College in Singapore and has been active since 1996, the subdomain points to the malicious IP address—200[.]69[.]23[.]93.
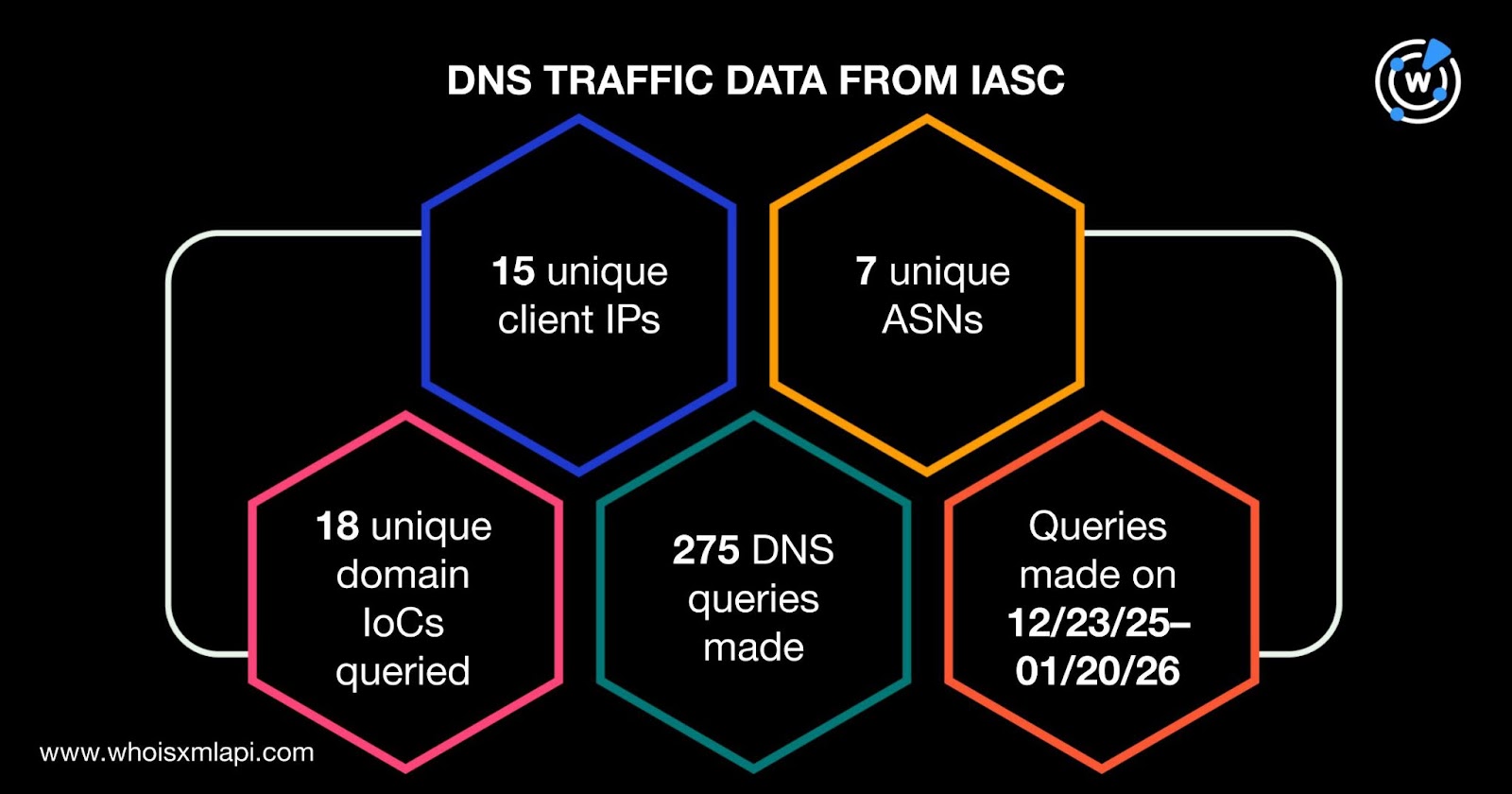
We then moved on to our analysis of the 125 domains identified as IoCs. First off, we looked at sample network traffic data from the IASC. We learned that 15 unique client IP addresses under seven distinct ASNs communicated with 18 unique domains identified as IoCs via 275 DNS queries made between 23 December 2025 and 20 January 2026.
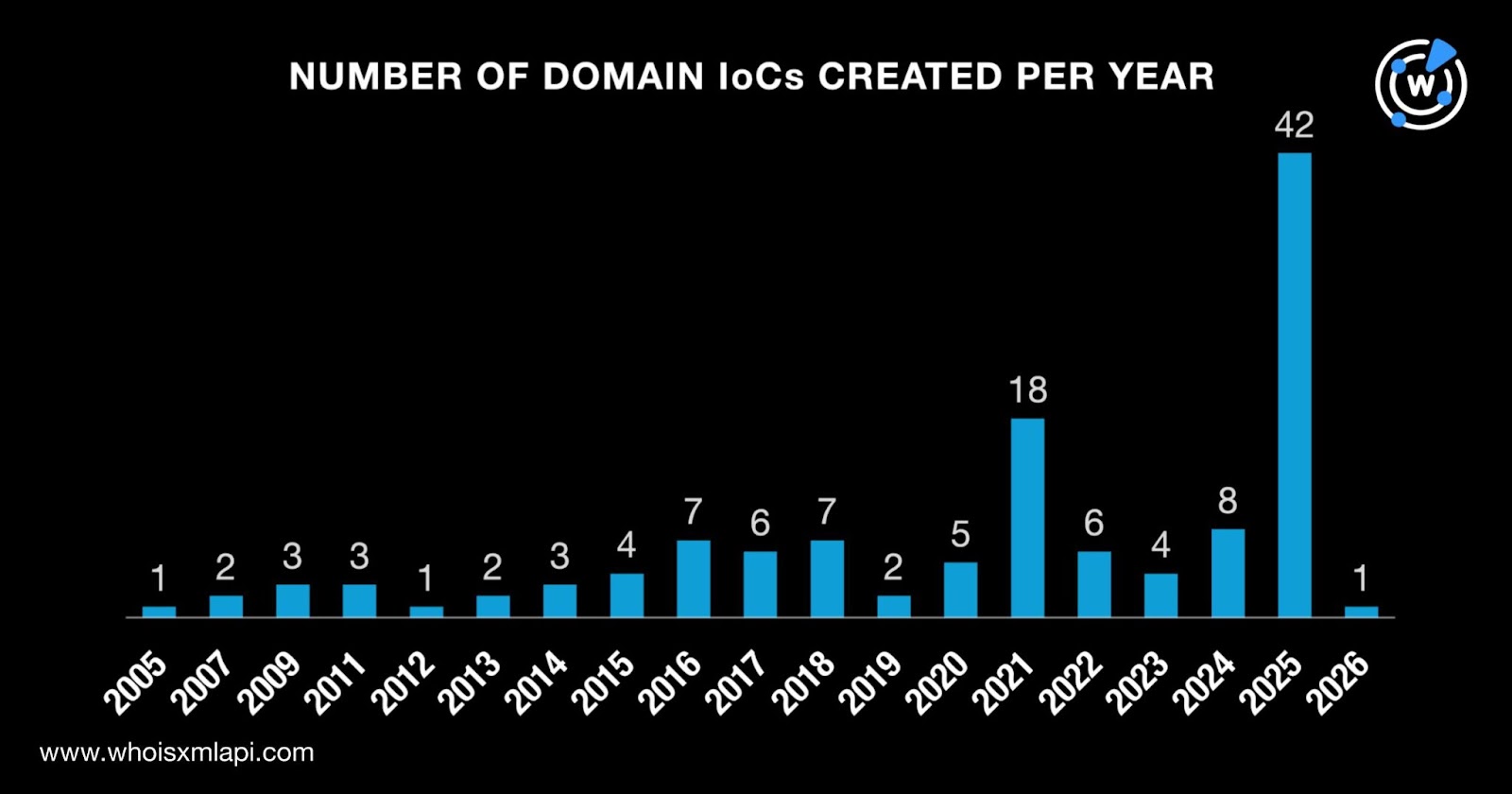
According to our First Watch Malicious Domains Data Feed query results, eight of the domains identified as IoCs were registered with malicious intent from the get-go.
Next, we queried the 125 domains identified as IoCs on WHOIS API and found out that:
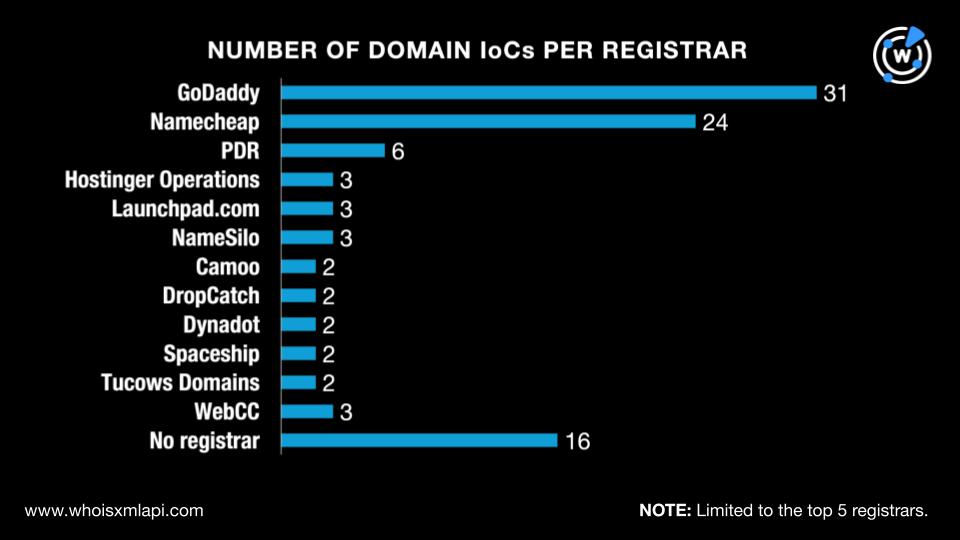
While 16 did not have registrars on record, the remaining domains were administered by 38 different registrars. Note that apart from the top 5 featured in the image below, one domain each was managed by Atak Domain Bilgi Teknolojileri, Bluehost, Cloudflare, Cosmotown, CV Jogjacamp, Domain Science Kutatasi Szolgaltato Korlatolt Felelossegu Tarsasag, DomainSpot, Dominet (HK), Dreamhost, eNom, Ernet, GMO Internet Group, Gname.com, Ionos, Klaatudomains.com, Metaregistrar, Name.com, Nominalia Internet, P.A. Viet Nam Company, Porkbun, REG-MEP, Skykomishdomains.com, Telekom Srbija, THNIC, TurnCommerce, and West263 International.
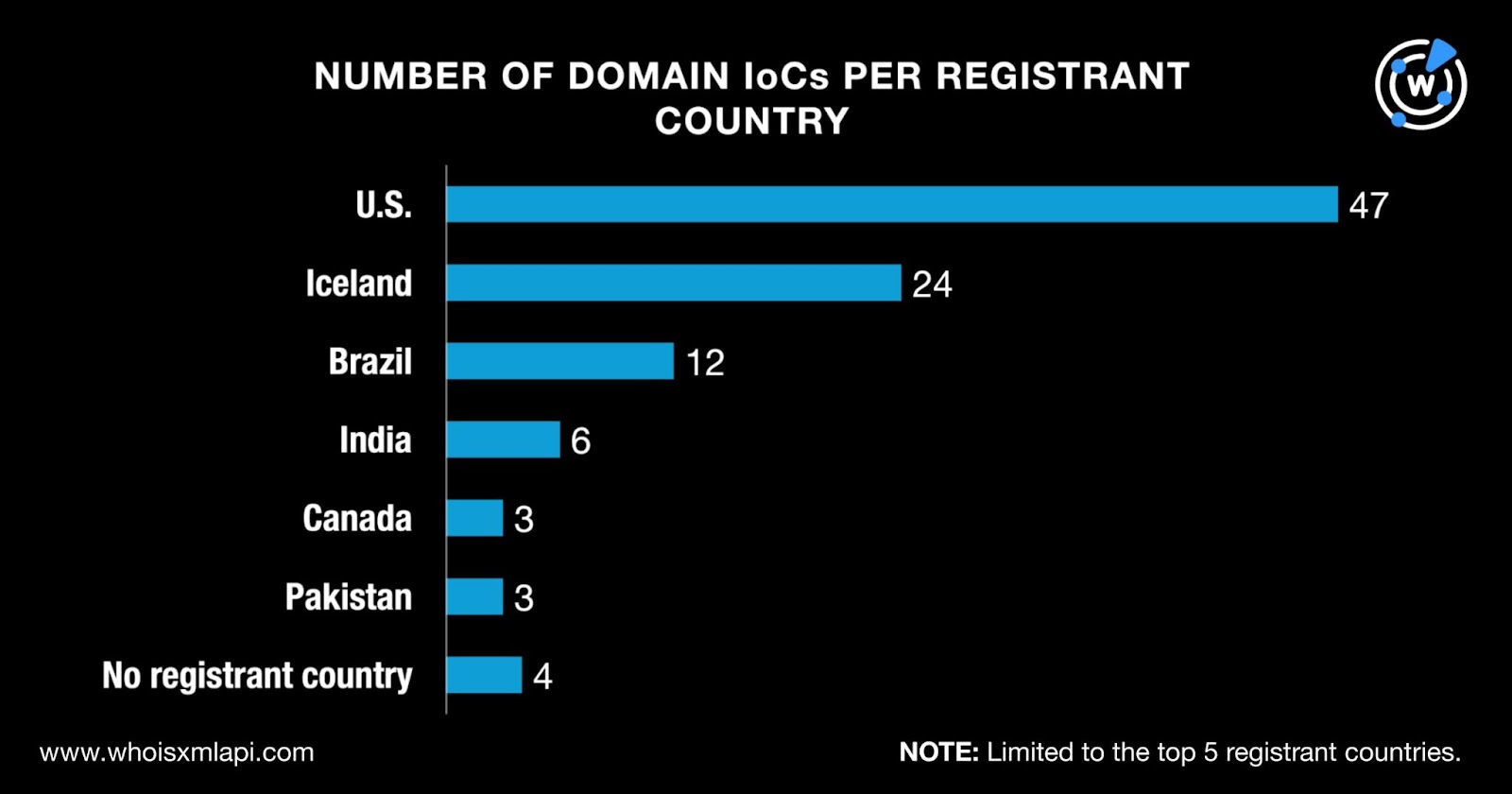
While four did not have registrant countries on record, the remaining domains were registered in 20 different countries. Note that apart from the top 5 featured in the image below, two domains each were registered in Cameroon, China, Lithuania, Malaysia, Thailand, and the U.K. while one each was registered in Australia, Bangladesh, Egypt, France, Indonesia, Kenya, Mexico, the Netherlands, Nigeria, Portugal, South Korea, Spain, Tanzania, and Vietnam.
DNS Chronicle API queries for the 125 domains identified as IoCs revealed that they had 25,867 historical domain-to-IP resolutions since 5 February 2017. A total of 13 posted their first resolutions on that date.
| DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| ankitashrivastava[.]com | 255 | 02/05/17 | 12/19/25 |
| ansaf[.]or[.]tz | 356 | 02/05/17 | 01/19/26 |
| aurogroup[.]net | 357 | 02/05/17 | 02/26/17 |
| bellstowingandrecovery[.]com | 182 | 02/05/17 | 08/30/24 |
| bitakhoshnood[.]com | 197 | 02/05/17 | 12/16/25 |
Further scrutiny of the historical domain-to-IP resolutions revealed half-year peaks over time. Many of the domains that started resolving within each specific period could have been weaponized for the same attack.
| YEAR | NUMBER OF DOMAIN IoCs | MONTH WITH HIGHEST NUMBER OF IoCs REGISTERED |
|---|---|---|
| 2017 | 54 | February |
| 2018 | 17 | June |
| 2019 | 10 | March |
| 2020 | 8 | January and December |
| 2021 | 20 | December |
| 2022 | 13 | September |
| 2023 | 3 | March |
We started our search for connected artifacts by querying the 125 domains identified as IoCs on WHOIS History API. We discovered that 123 had email addresses in their historical WHOIS records. They had 360 unique email addresses in all. Further scrutiny showed that 105 were public email addresses.
Based on the results of our Reverse WHOIS API queries for the 105 public email addresses, none of them were present in current WHOIS records. While 104 appeared in historical WHOIS records, two could belong to domainers, leaving us with 102 for further analysis. They led to the discovery of 11,325 unique email-connected domains after those already identified as IoCs were filtered out.
Threat Intelligence API queries for the 11,325 email-connected domains showed that nine have already been weaponized for various attacks.
| MALICIOUS EMAIL-CONNECTED DOMAIN | ASSOCIATED THREAT | DATE FIRST SEEN | DATE LAST SEEN |
|---|---|---|---|
| garagedoorrepairchicopeema[.]com | PhishingGeneric threat | 11/20/2511/22/25 | 01/22/2612/20/25 |
| alltopposts[.]com | Malware distribution | 03/09/23 | 01/16/26 |
| boogadelic[.]com | Phishing | 06/30/25 | 12/31/25 |
| cialisfirst[.]com | Suspicious activity | 04/06/23 | 01/13/26 |
| extremetowingservice[.]com | Phishing | 07/27/25 | 01/22/26 |
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byRadix

Sponsored byVerisign

Sponsored byVerisign
