


|
||
|
||

Cyberattacks are accelerating, and CSC’s latest report exposes how domain vulnerabilities—outside corporate firewalls—remain a critical blind spot for enterprise security strategies.
In the sixth annual edition of its Domain Security Report, CSC delivers a sobering assessment of domain security across the Forbes Global 2000 and the world’s top 100 unicorns. While technical capabilities in the cybersecurity space continue to advance, domain security—the foundation of digital brand presence and infrastructure—remains inconsistently adopted and dangerously under-prioritized.
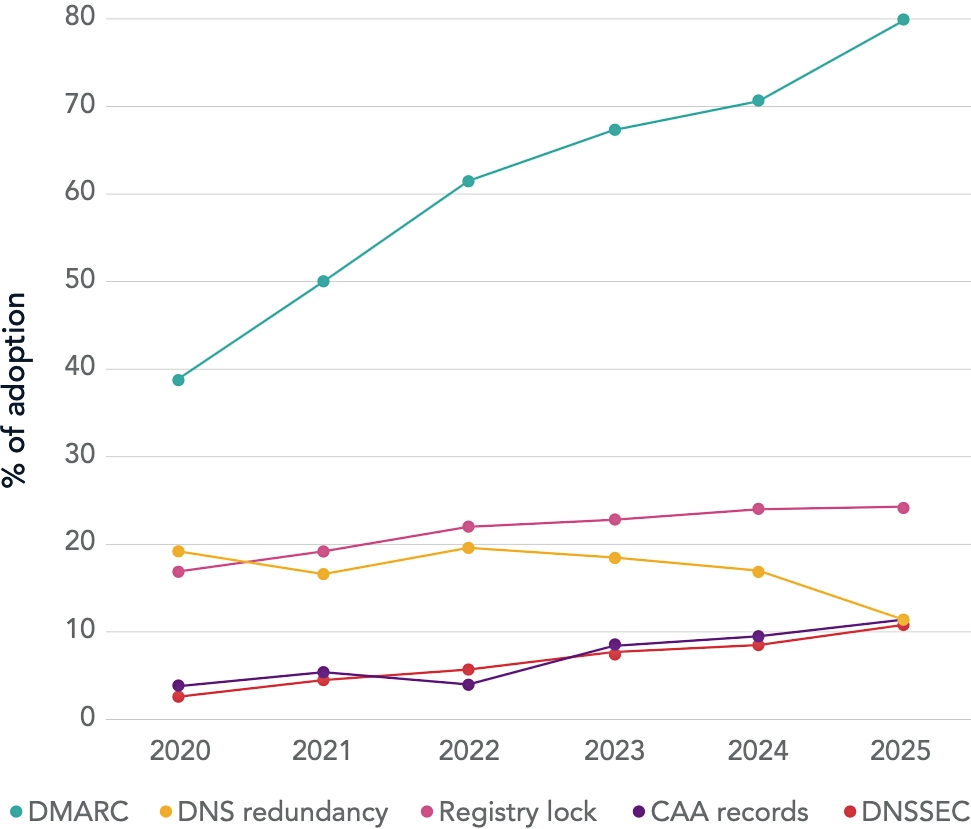
The report highlights that 67% of Global 2000 companies have implemented fewer than half of eight key domain security controls, including DMARC, DNS redundancy, registry lock, and DNSSEC. These gaps are not theoretical; they are actively exploited. CSC’s analysis found that malicious actors are registering lookalike or dormant domains at scale, with 88% of homoglyph domains—fake domains using visually similar characters—owned by third parties. Many of these domains contain active email (MX) records, making them potent tools for phishing, impersonation, and fraud.
The DNS layer is a growing focus of threat actors. From hijacked subdomains and dangling DNS to weaponized dormant assets, attackers are exploiting low-cost and often overlooked entry points. CSC’s findings underscore that the domain ecosystem—email, websites, APIs, and authentication infrastructure—is the gateway to nearly every form of modern attack, from ransomware to brand abuse and AI stack manipulation.
Encouragingly, adoption of DMARC continues to rise, driven partly by regulatory tailwinds such as the EU’s NIS2 Directive. DMARC implementation among the Global 2000 jumped from 39% in 2020 to 80% in 2025. Yet regional disparities persist: 85% of non-adopters are based in APAC, where uptake continues to lag. Similarly, DNSSEC adoption has quadrupled in six years but still only reaches 11% of companies—a worrying statistic given its role in authenticating DNS responses and preventing traffic redirection.
CSC draws attention to the clear advantages of enterprise-class registrars, whose clients demonstrate markedly stronger adoption of critical controls. Registry lock usage, for example, is 6x higher among Global 2000 firms using enterprise registrars versus consumer-grade alternatives. This single measure helps prevent unauthorized changes to DNS settings, especially in cases where registrar accounts are compromised.
Unicorns—particularly those in AI and fintech—show a split profile. They lead in lightweight DNS record-based measures like SPF and DMARC but fall behind in infrastructure-heavy practices such as DNS redundancy and registry lock. This reflects their agility and technical savviness, but also exposes them to growing risks as they scale.
The broader implication is clear: as the external attack surface expands and AI-powered threats grow more sophisticated, domain security must become an integral part of enterprise-wide cyber risk governance. The cost of inertia is not just downtime or regulatory non-compliance—it is systemic vulnerability across digital operations, customer trust, and supply chain resilience. The window for proactive hardening is closing.
Sponsored byVerisign

Sponsored byRadix

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byDNIB.com
