


|
||
|
||
Koi Security has been monitoring a threat group they have dubbed “DarkSpectre” for more than a year now. The group was behind at least three major malware campaigns leveraging Zoom Stealer, ShadyPanda, and GhostPoster that have affected more than 8.8 million users over the course of their seven-year-long operation.
The researchers uncovered another DarkSpectre campaign that affected 2.2 million users so far. The group reportedly used a new GhostPoster-linked Opera browser extension that has been installed nearly 1 million times as of December 2025.
Koi Security identified 20 IoCs in their report comprising three subdomains, 12 domains, one IP address, and four email addresses.
We extracted unique domains from the subdomains, bringing the total number of domains to 15. We then excluded legitimate domains from our IoC list with the help of Jake AI. The results showed that eight were legitimate domains, leaving us with seven for further analysis. That said, we further investigated 15 IoCs in all comprising three subdomains, seven domains, one IP address, and four email addresses. Our analysis led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We took a closer look at the three subdomains identified as IoCs aided by Jake AI. We discovered that while two of them were part of legitimate web infrastructures but could have been compromised for attacks, one—policies[.]extfans[.]com—was illegitimate and currently inactive.
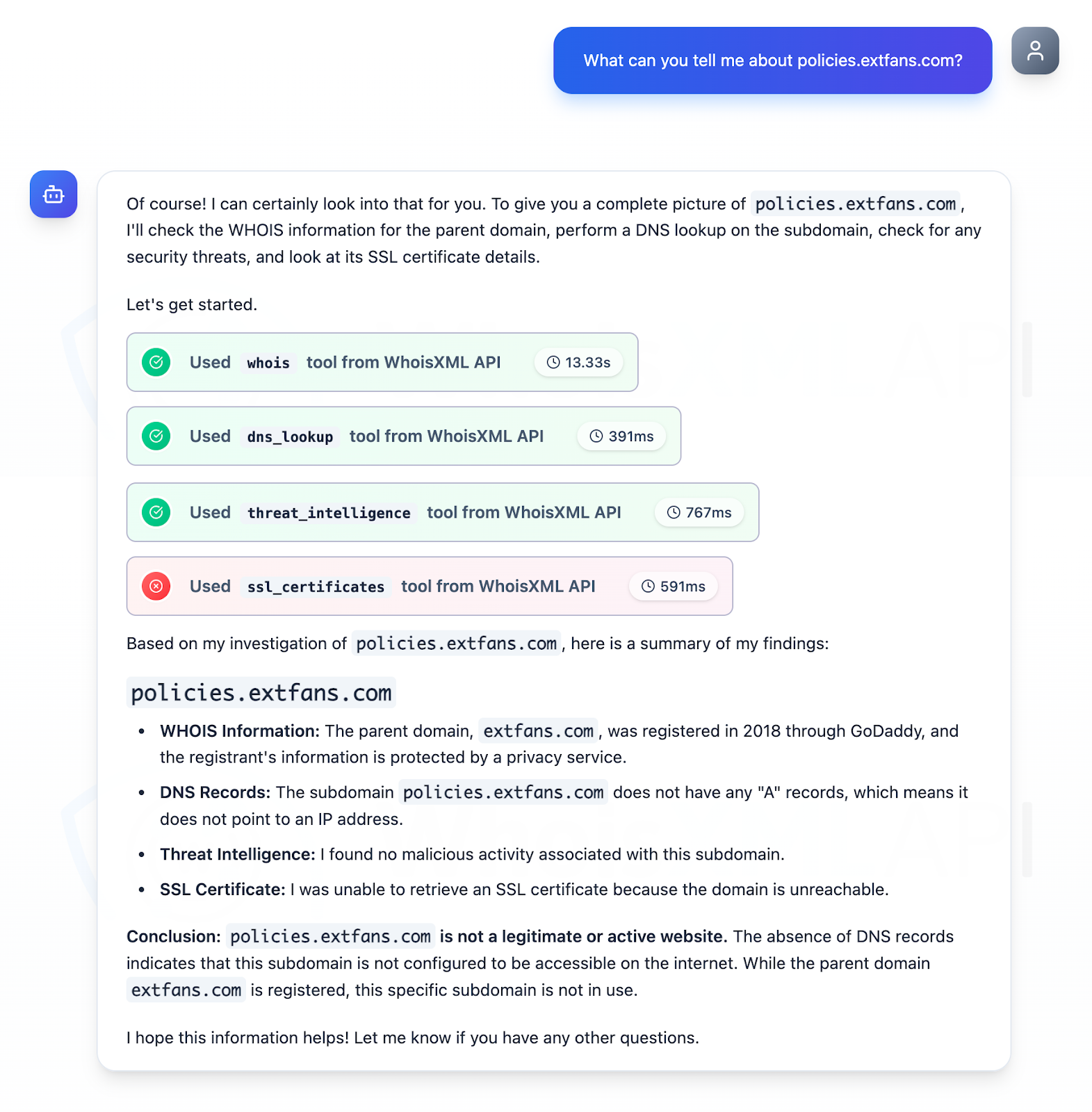
Next, we investigated the four email addresses identified as IoCs using Jake AI. While three of them were deemed legitimate, one was tagged as invalid.
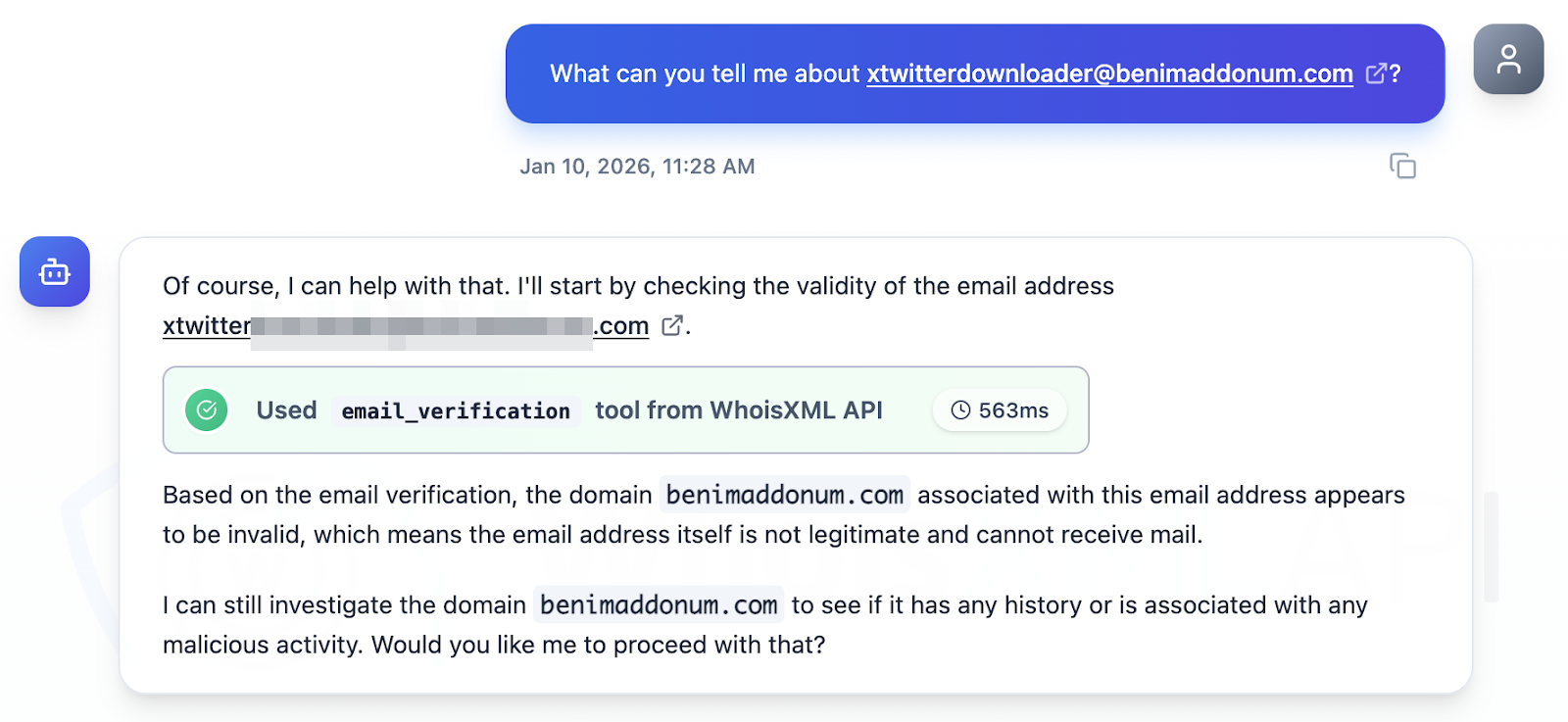
It is also worth noting that one other email address from the four identified as IoCs was used to register domains. We will thus include it in our search for new artifacts later.
We looked more closely at the seven domains identified as IoCs next.
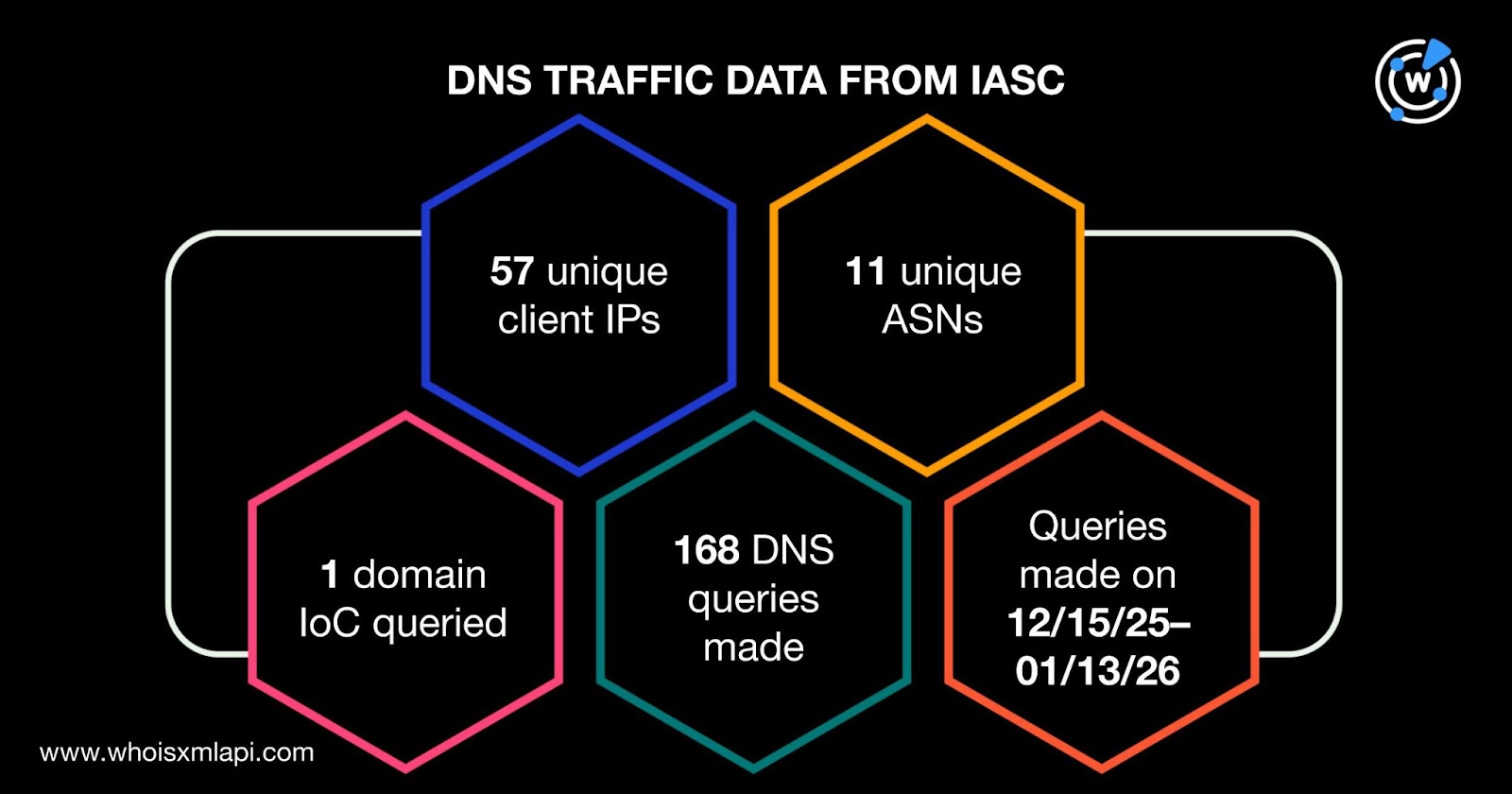
Sample network traffic data from the IASC revealed that 57 unique client IP addresses under 11 distinct ASNs communicated with one domain identified as an IoC via 168 DNS queries made between 15 December 2025 and 13 January 2026.
We also queried the seven domains identified as IoCs on WHOIS API and found out that only six had current WHOIS records.
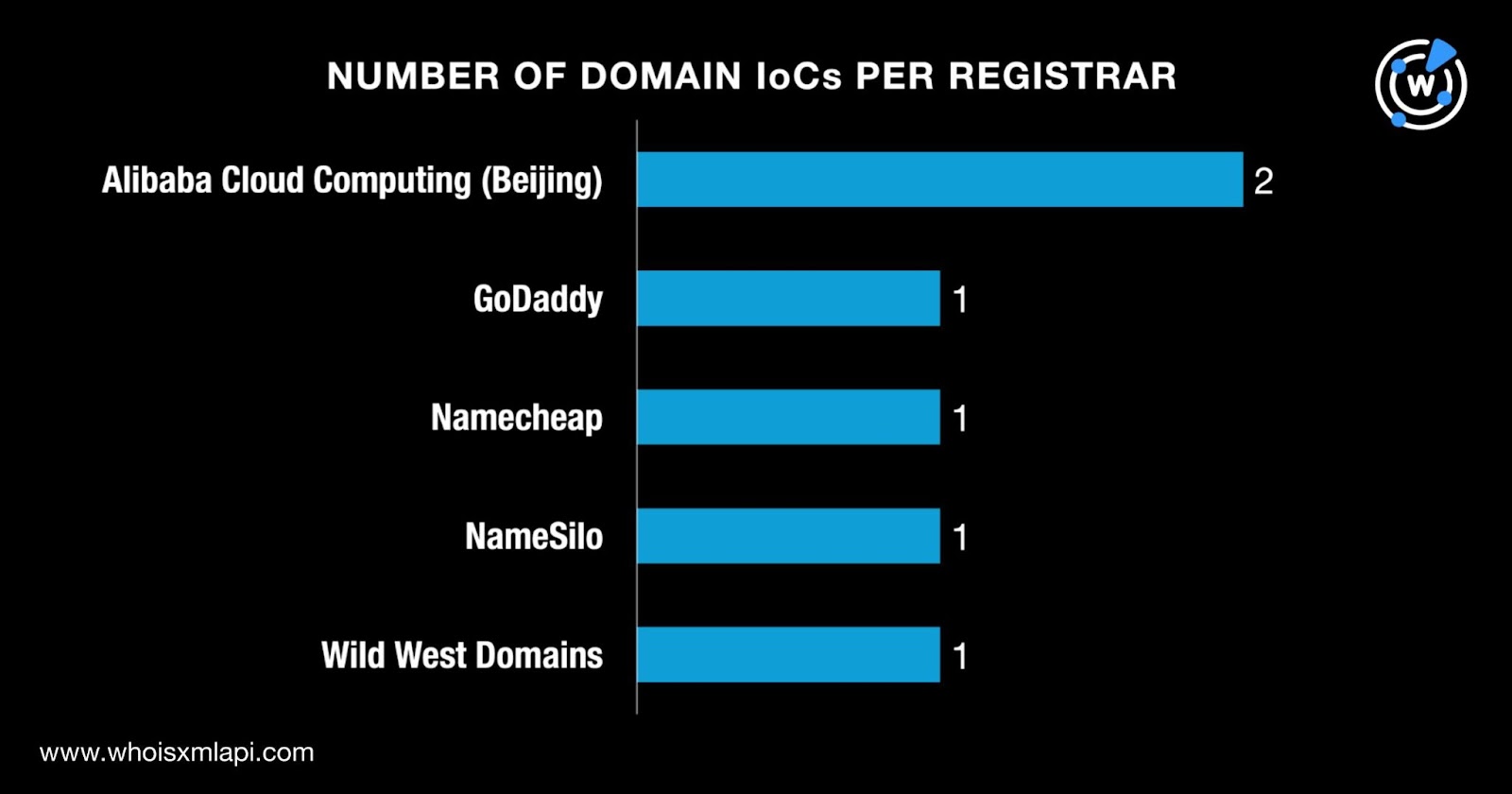
They were administered by five different registrars—two by Alibaba Cloud Computing (Beijing) and one each by GoDaddy, Namecheap, NameSilo, and Wild West Domains.
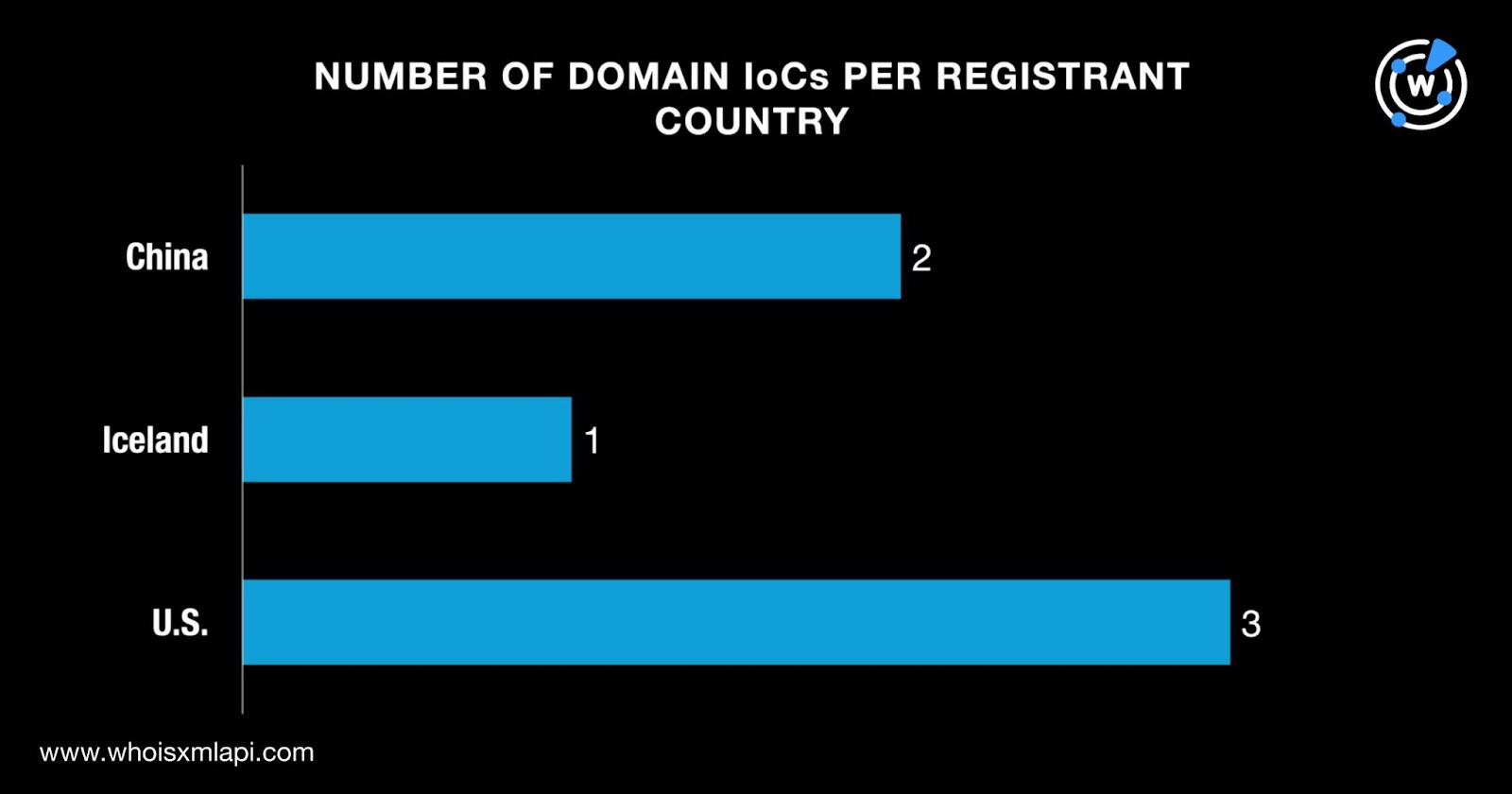
They were registered in three different countries—three in the U.S., two in China, and one in Iceland.
DNS Chronicle API queries for the seven domains identified as IoCs showed that only six had historical domain-to-IP resolutions. Altogether, they recorded 1,283 resolutions over time. The domain gmzdaily[.]com posted the oldest resolution on 5 February 2017.
| DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| gmzdaily[.]com | 393 | 02/05/17 | 12/17/25 |
| infinitynewtab[.]com | 261 | 02/06/17 | 11/16/22 |
| extfans[.]com | 205 | 06/11/18 | 4/28/23 |
An IP Geolocation API query for the sole IP address identified as an IoC revealed that it was geolocated in China under the administration of China Unicom.
Interestingly, though, the IP address is currently not in use nor has not recorded historical IP-to-domain resolutions over time.
After obtaining more information about the IoCs, we went on to search for new DarkSpectre-connected artifacts.
First, we queried the seven domains identified as IoCs on WHOIS History API and discovered that five of them had email addresses in their historical WHOIS records. We amassed nine email addresses in all and found out that seven were public email addresses. We now had eight public email addresses—seven from our searches and one tagged as an IoC (i.e., from the “An Examination of the Email IoCs” section)—for further analysis.
Reverse WHOIS API queries for the eight email addresses showed that one could belong to a domainer so we excluded the domains connected to it for the next step. The results for the remaining seven email addresses led to the discovery of 8,579 unique email-connected domains after those already identified as IoCs were filtered out.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byCSC

Sponsored byVerisign

Sponsored byVerisign

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byIPv4.Global
