


|
||
|
||
Wearing a disguise has often worked when it comes to infiltrating well-protected targets. So long as threat actors stay in character, they could succeed with their ruse. And that is how Chinese APT group SilverFox managed to trick victims into thinking they were Russian. The actors used Cyrillic characters in their SEO poisoning campaign lures that deployed ValleyRAT.
Silver Fox abused Microsoft Teams to target Chinese organizations. They used ValleyRAT to conduct state-sponsored espionage for sensitive intelligence and engage in financial fraud and theft to fund their operations.
ReliaQuest originally identified 41 IoCs comprising six domains, 17 subdomains, and 18 IP addresses after analyzing the cyber attack in great depth. We investigated the Silver Fox infrastructure further and unearthed these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We started out by looking more closely at the 17 subdomains identified as IoCs using Jake AI. We learned that while none of them were inherently malicious, 16 were either uncategorized or inactive. We also found out that 15 of them, specifically those that started with the text string teams., shared the same IP address.
ReliaQuest originally identified six domains and 17 subdomains as IoCs as mentioned earlier. We extracted 17 unique domains from the 17 subdomains. Adding those to the six domains and ensuring none of them were duplicates brought the total number of unique domains to 23. We then checked if any of the 23 domains were owned by legitimate entities using the WhoisXML API MCP Server and took out three, which brought our final total number of domains for further analysis down to 20.
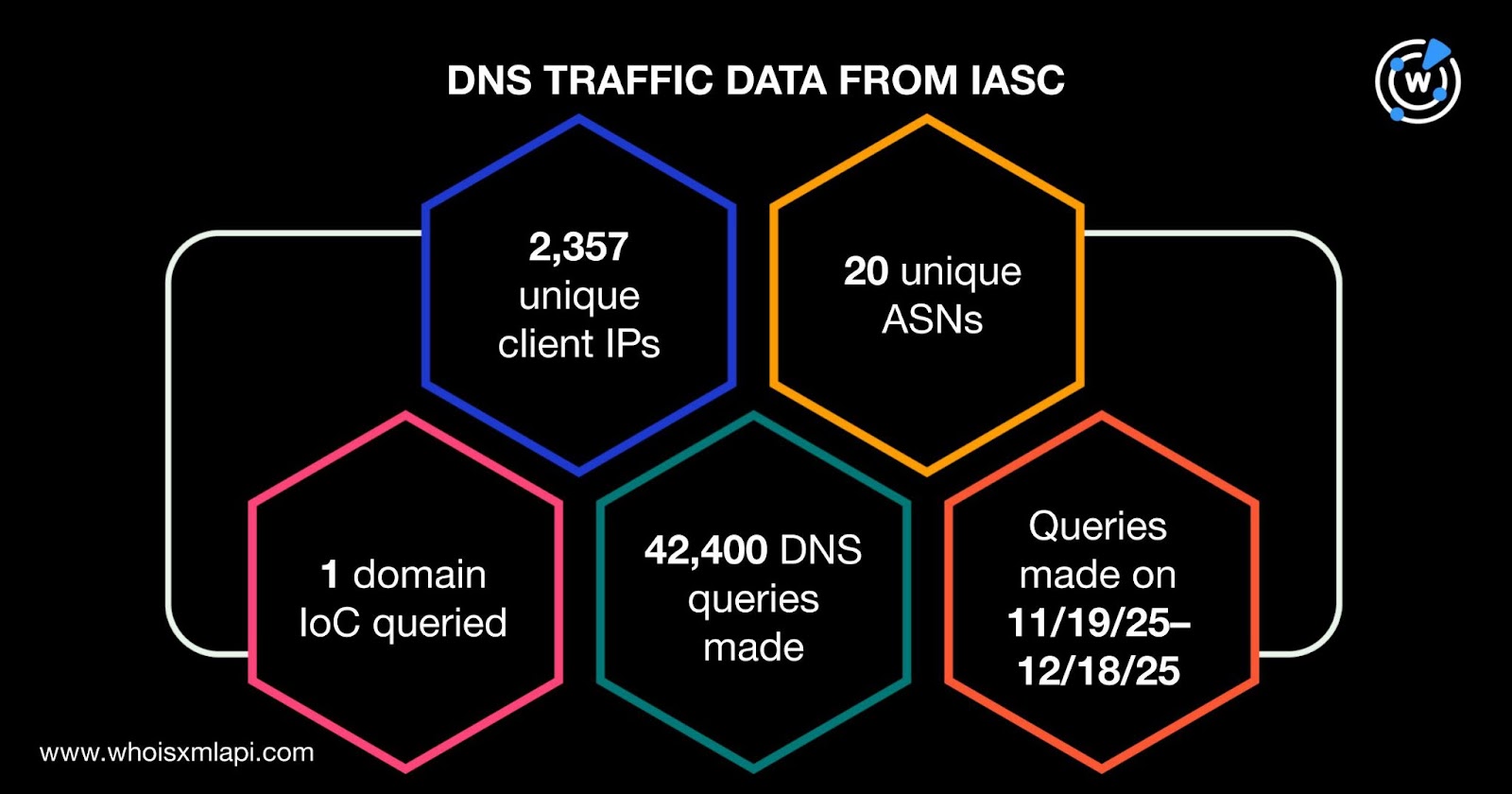
Sample network traffic data from the IASC revealed that 2,357 unique client IP addresses under 20 distinct ASNs communicated with one domain identified as an IoC via 42,400 DNS queries made between 19 November and 18 December 2025.
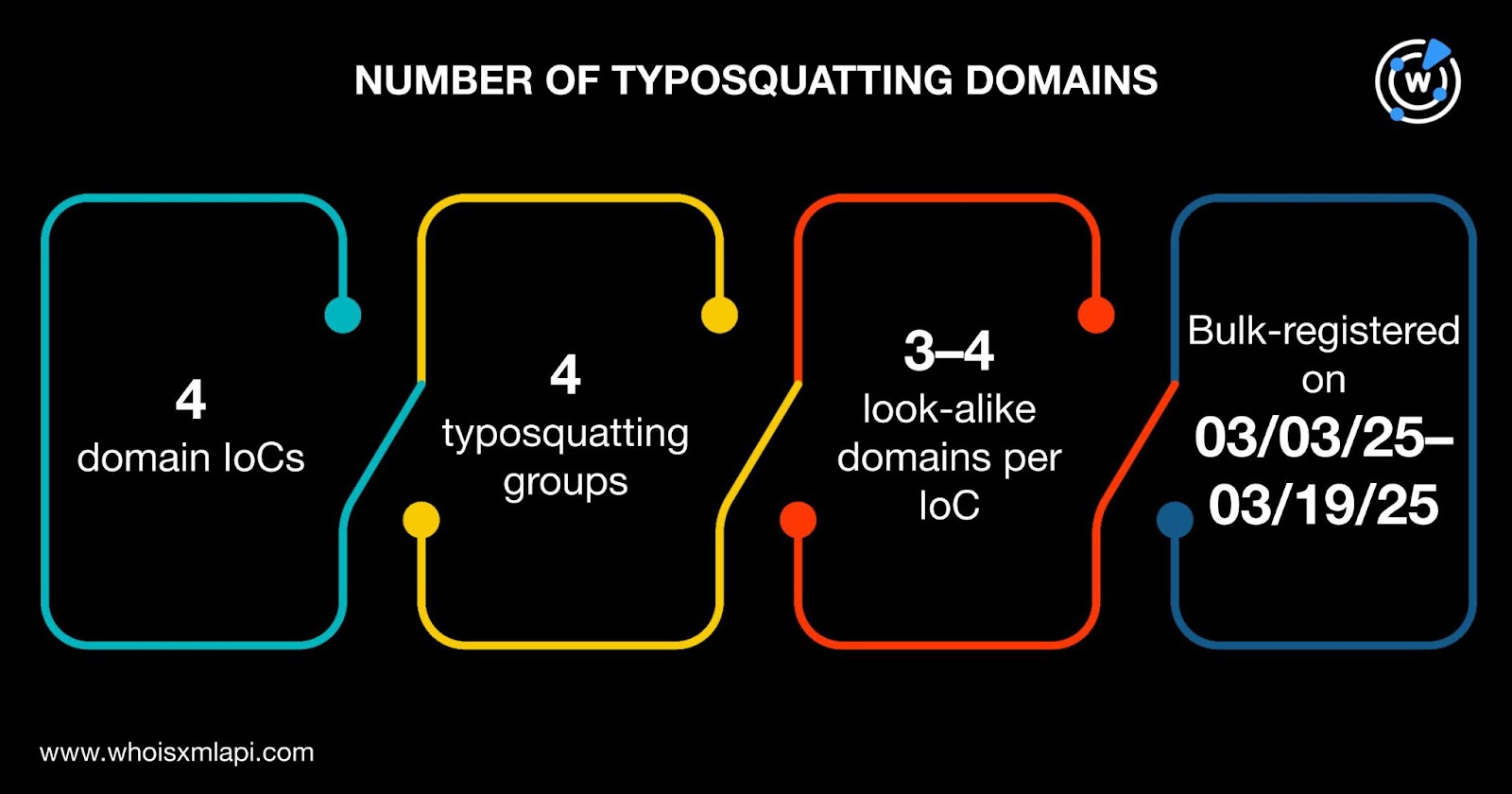
Data from the Typosquatting Data Feed, meanwhile, showed that four domains identified as IoCs were bulk-registered with 3—4 look-alikes each between 3 and 19 March 2025. A total of four typosquatting groups were found.
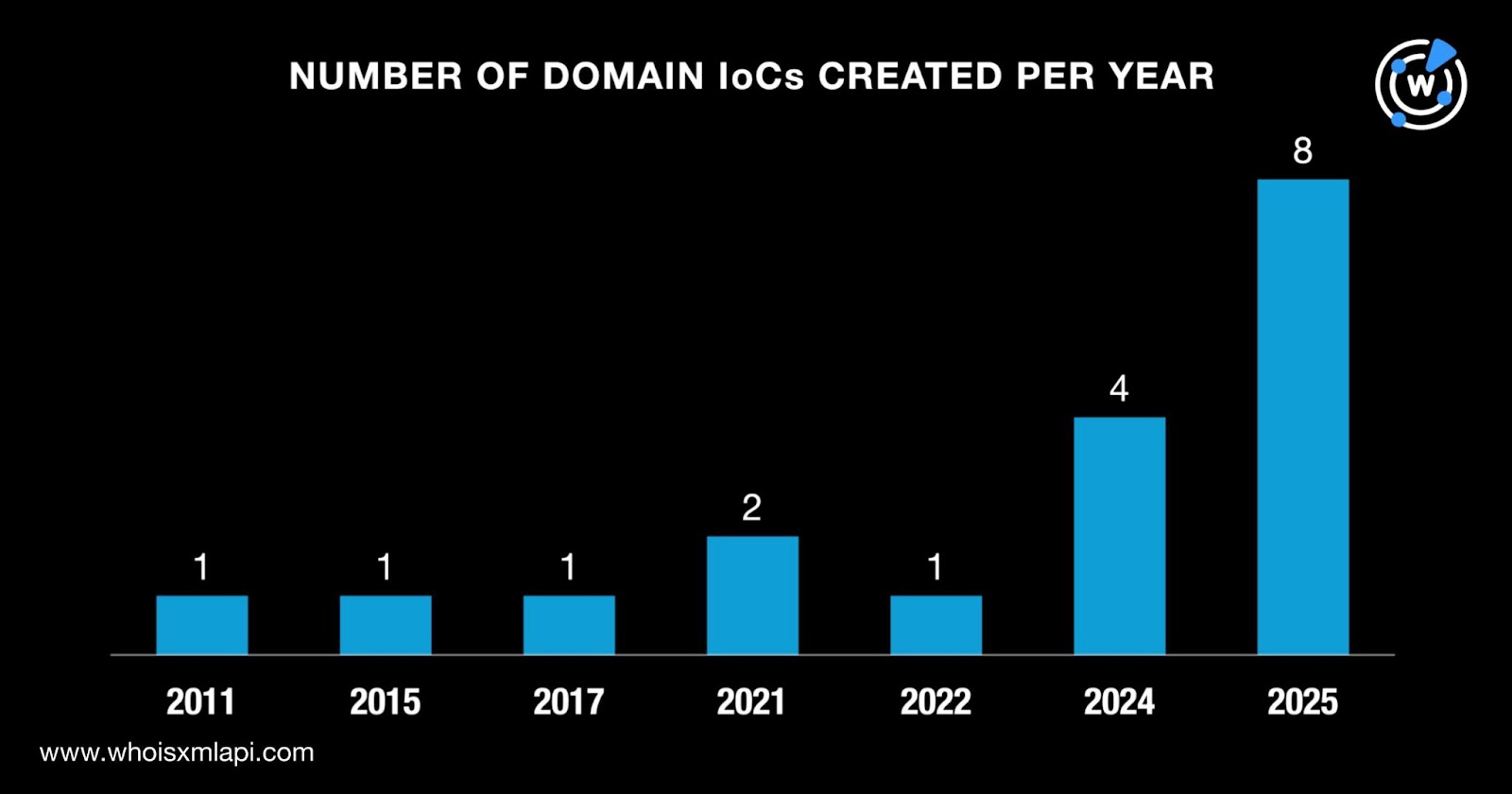
The results of our First Watch Malicious Domains Data Feed queries also revealed that seven domains identified as IoCs were deemed likely to turn malicious 239—339 before they were reported as such on 4 December 2025.
| DOMAIN IoC | FIRST WATCH DATE | NUMBER OF DAYS BEFORE THE REPORT DATE |
|---|---|---|
| kkkgenieyesl[.]cn | 12/30/24 | 339 |
| teamszv[.]com | 03/02/25 | 277 |
| fjzwb[.]com | 03/18/25 | 261 |
| telegramgwxz[.]com | 03/18/25 | 261 |
| telegramtgxz[.]com | 03/18/25 | 261 |
Next, we queried the 20 domains identified as IoCs on WHOIS API and discovered that only 18 had current WHOIS records. We limited our analysis for this section to the 18 domains with current WHOIS records. That said, we learned that:
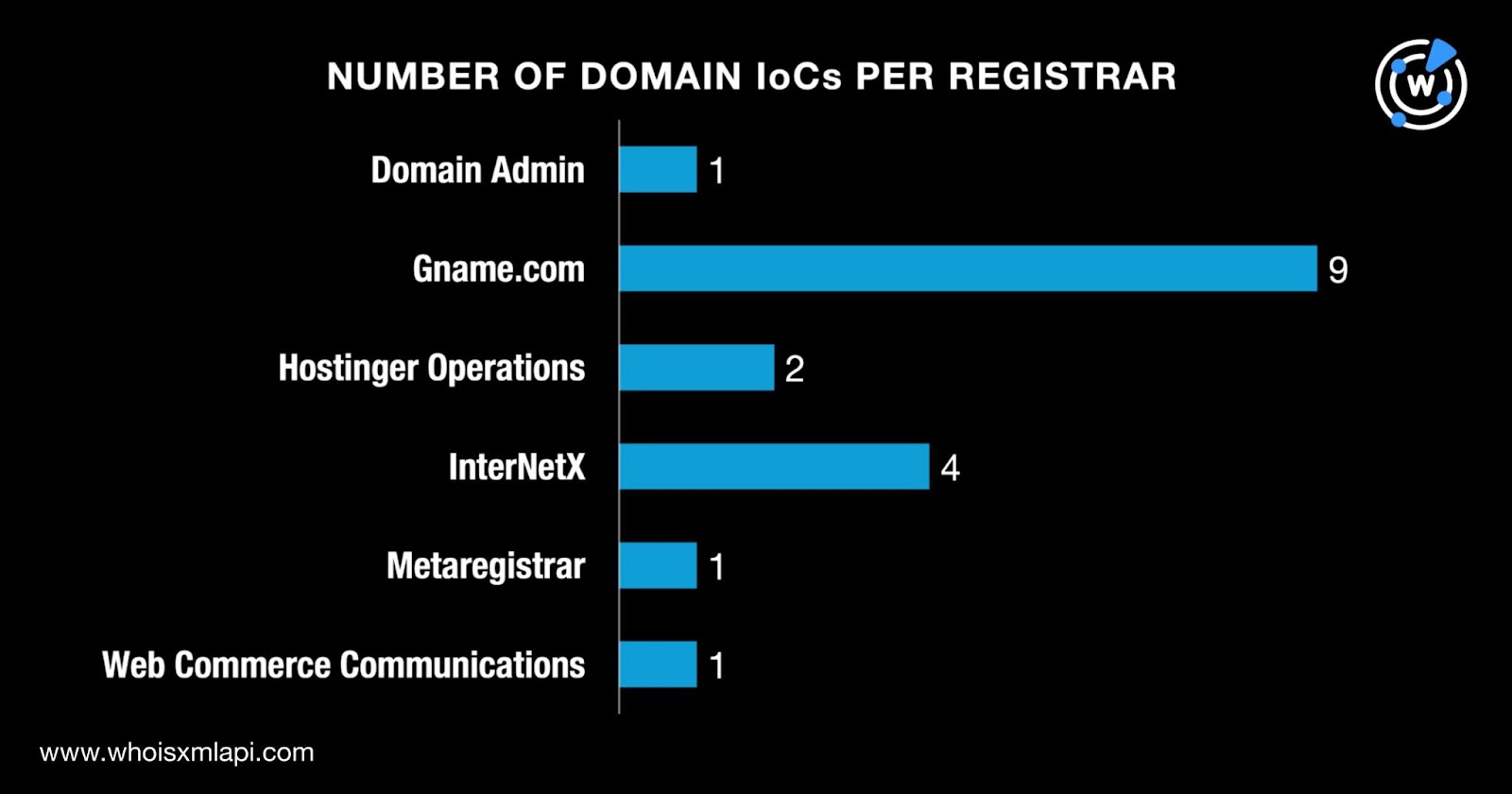
They were administered by six registrars led by Gname.com, which accounted for nine domains. InterNetX administered four domains; Hostinger Operations managed two; and Domain Admin, Metaregistrar, and Web Commerce Communications managed one each.
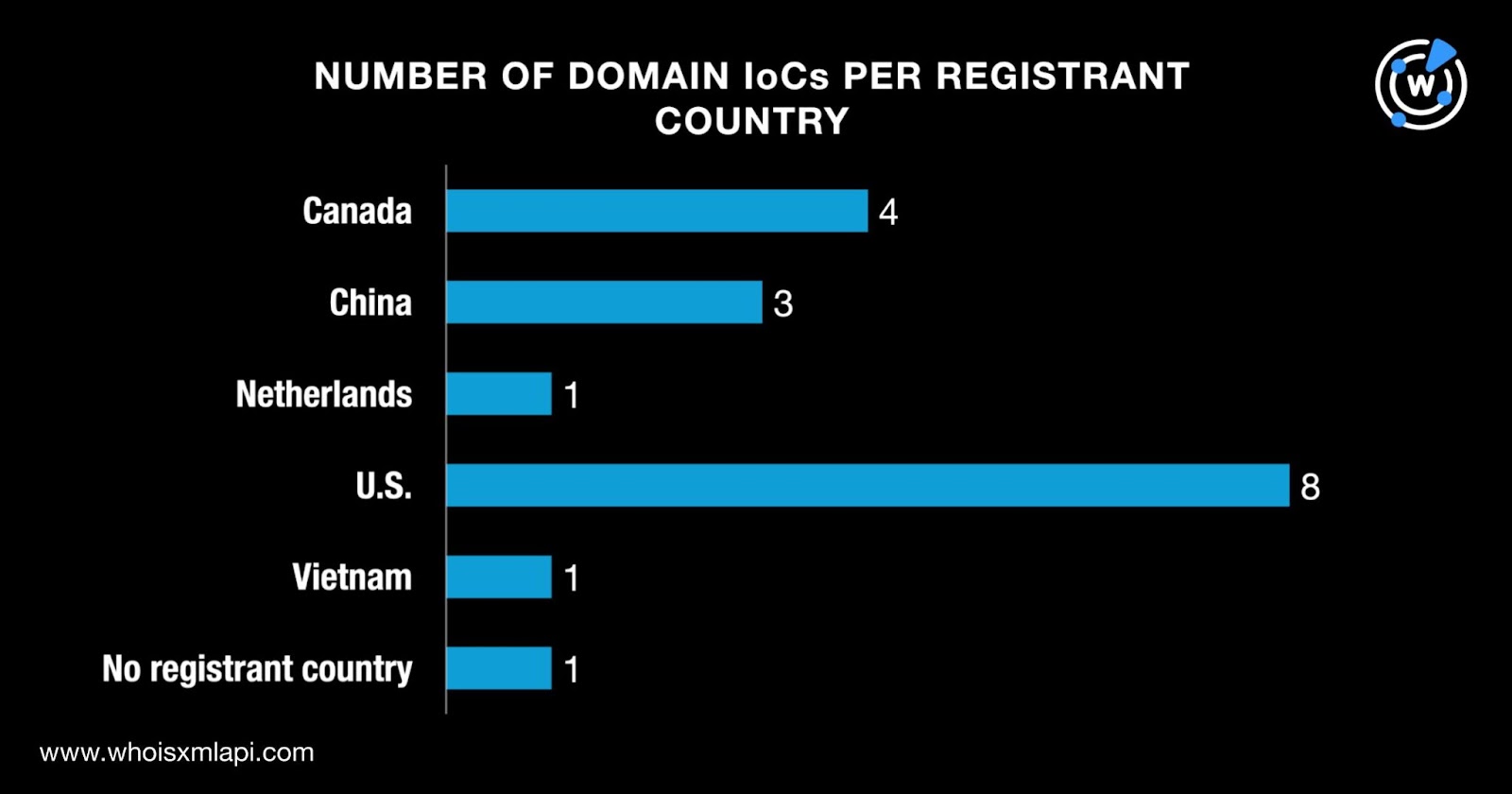
While one domain did not have a registrant country on record, the remaining 17 were registered in five countries topped by the U.S., which accounted for eight domains. Four domains were registered in Canada; three in China; and one each in the Netherlands and Vietnam.
A DNS Chronicle API query for the 20 domains identified as IoCs revealed that only 18 had historical domain-to-IP resolutions. They posted a total of 2,729 resolutions over time. The domains baoyingkeji[.]com, fin-tastikantioch[.]com, and hardepc[.]com posted the oldest resolutions on 5 February 2017. Note that five other domains—chetanagarbatti[.]com, cpeakem[.]com, jqsnzp[.]com, kensun4a[.]com, and xclyd[.]com—posted resolutions in a matter of days after the first three did. This similarity could point to ownership by the same entity or, in this case, being part of the same attack infrastructure.
| DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| baoyingkeji[.]com | 260 | 02/05/17 | 02/10/25 |
| fin-tastikantioch[.]com | 492 | 02/05/17 | 01/09/24 |
| hardepc[.]com | 135 | 02/05/17 | 02/02/25 |
| chetanagarbatti[.]com | 297 | 02/07/17 | 12/15/25 |
| cpeakem[.]com | 349 | 02/12/17 | 02/22/25 |
Jake AI queries for the 18 IP addresses identified as IoCs revealed that 17 could be dedicated hosts.
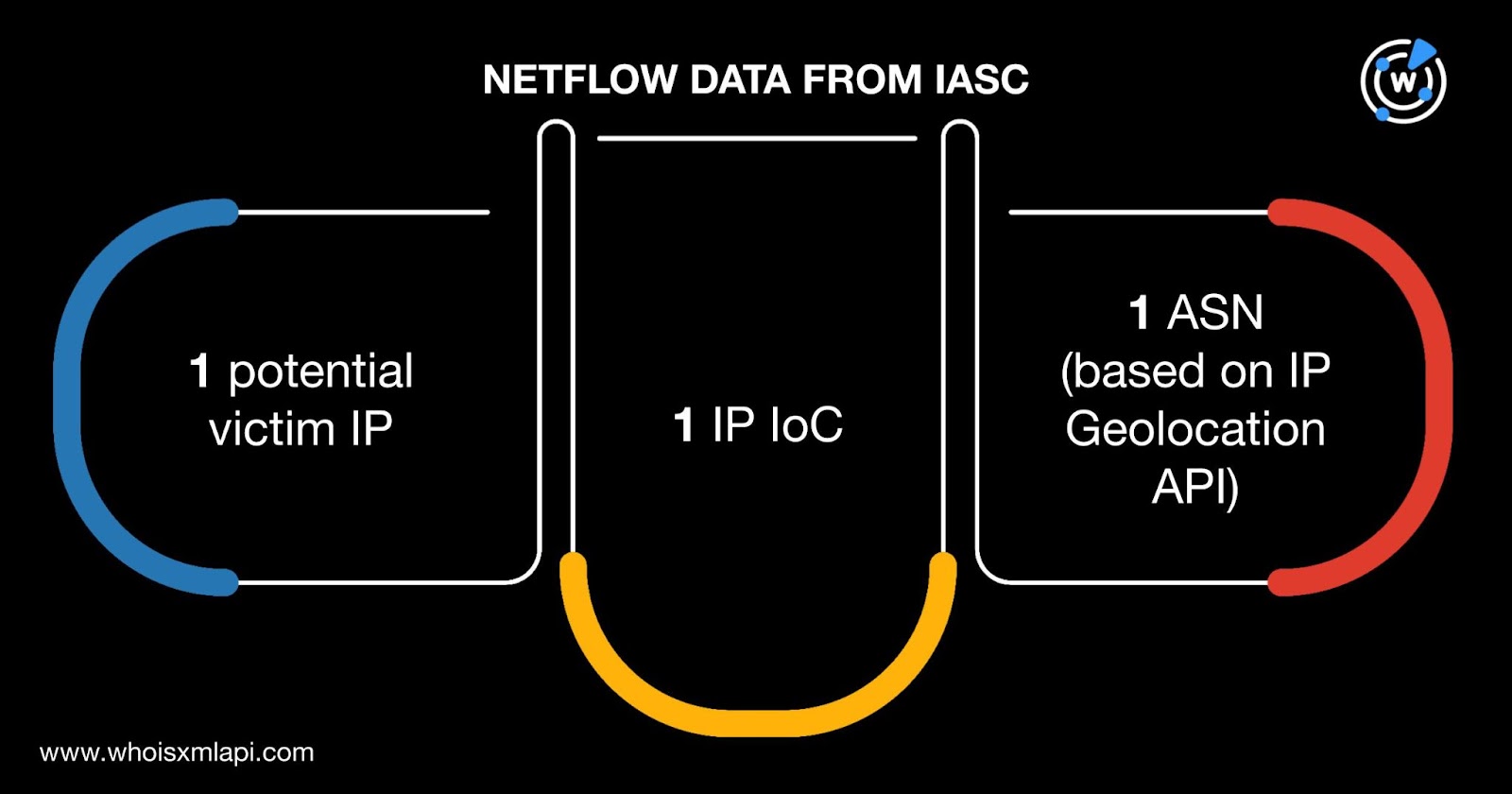
Sample IASC network traffic data for the 17 possibly dedicated IP addresses revealed an interesting finding. We learned that one potential victim IP address communicated with one IP address identified as an IoC on 9 December 2025.
Next, we queried the 18 IP addresses identified as IoCs on Bulk IP Geolocation Lookup and found out that:
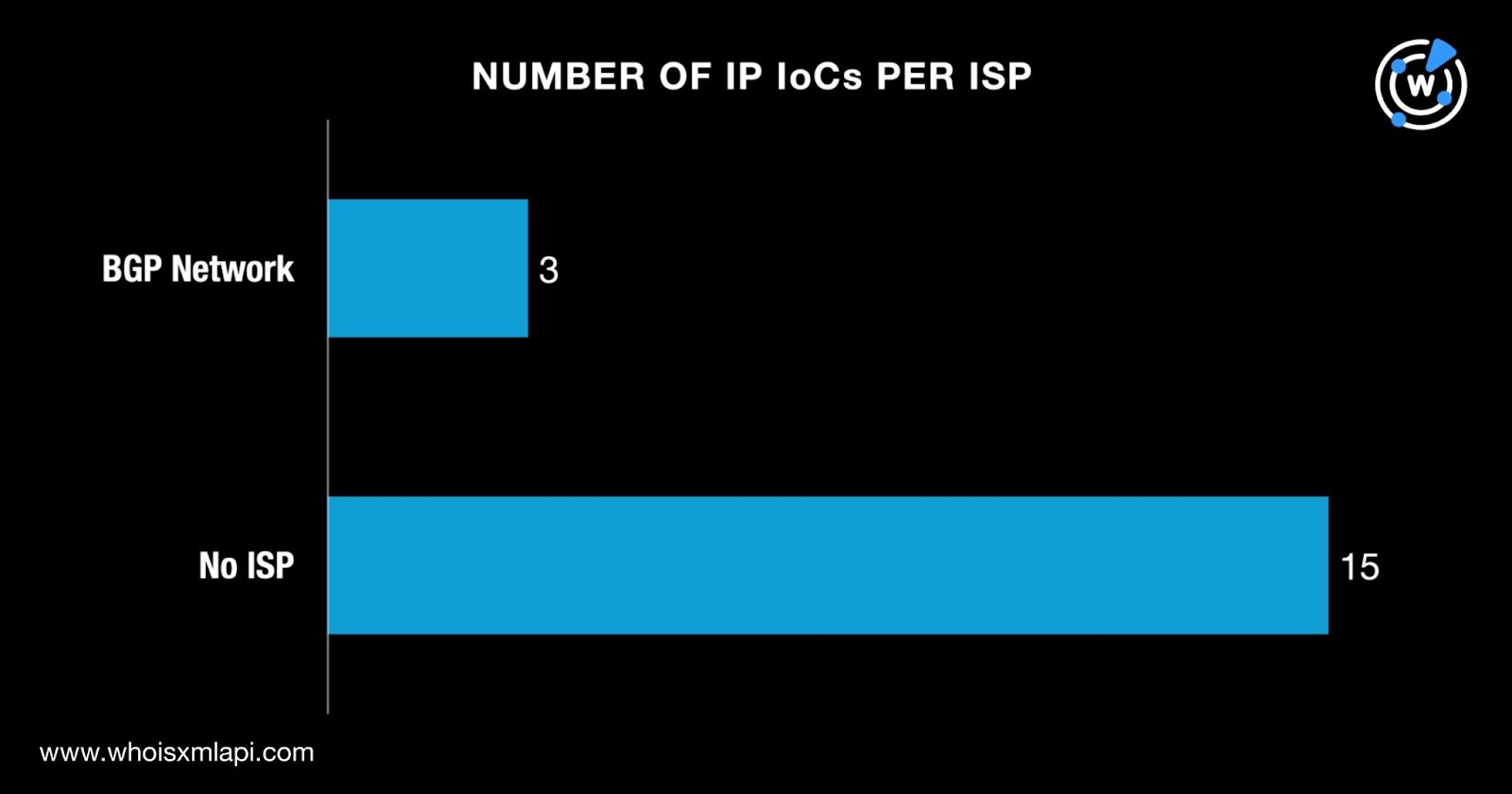
A DNS Chronicle API query for the 18 IP addresses identified as IoCs showed that all of them had historical IP-to-domain resolutions. Altogether, they posted 6,349 resolutions over time, The IP address 43[.]226[.]125[.]112 recorded the oldest resolution on 25 January 2019.
| IP IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| 43[.]226[.]125[.]112 | 601 | 01/25/19 | 12/08/25 |
| 137[.]220[.]135[.]86 | 774 | 11/08/19 | 09/04/25 |
| 27[.]124[.]43[.]12 | 150 | 11/12/19 | 11/05/23 |
| 27[.]124[.]43[.]7 | 191 | 12/26/19 | 10/29/25 |
| 43[.]226[.]125[.]125 | 19 | 08/31/19 | 02/16/20 |
Our search for new artifacts began with a WHOIS History API query for the 20 domains identified as IoCs. We discovered that 16 of them had email addresses in their historical WHOIS records. We unearthed 60 unique email addresses in all. Closer scrutiny showed that 33 were public email addresses.
A Reverse WHOIS API query for the 33 public email addresses showed that while none of them appeared in any domain’s current WHOIS record, all of them did so in historical WHOIS records. Nine public email addresses could belong to domainers so they were excluded from further analysis. The 24 public email addresses led to the discovery of 45,949 unique email-connected domains after those already identified as IoCs were filtered out.
The results of our Threat Intelligence API query for the 45,949 email-connected domains revealed that 51 have already been weaponized for various attacks.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byRadix

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byIPv4.Global
