


|
||
|
||
The threat actors behind the RomCom malware, known for extorting government agencies, recently resurfaced with a new RomCom variant called “Snipbot” or “RomCom 5.0” by Palo Alto Networks Unit 42.
RomCom was first detected in 2022 when threat actors used fake online tools mimicking SolarWinds, Advanced IP Scanner, PDF Reader Pro, and other popular software to trick users into downloading and installing the malware. Back then, WhoisXML API researchers analyzed related threat IoCs and found several potential artifacts.
The malware has much evolved since then. Snipbot is stealthier than earlier versions, although it is based on RomCom 3.0 and uses techniques utilized by RomCom 4.0. It leverages initial downloaders with valid code signing certificates, making target systems think the downloaders are from trusted sources and effectively bypassing security controls. The threat actors can then execute commands and download more modules that aim to steal data.
Our researchers sought to compare the IoCs of the three most recent RomCom versions and pivot off these indicators to uncover relevant threat artifacts. Snipbot IoCs comprising 17 domains and one IP address were derived from Unit 42, while the IoCs of versions 3.0 (56 domains and two IP addresses) and 4.0 (nine domains) were published by Trend Micro in 2023. The analysis led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
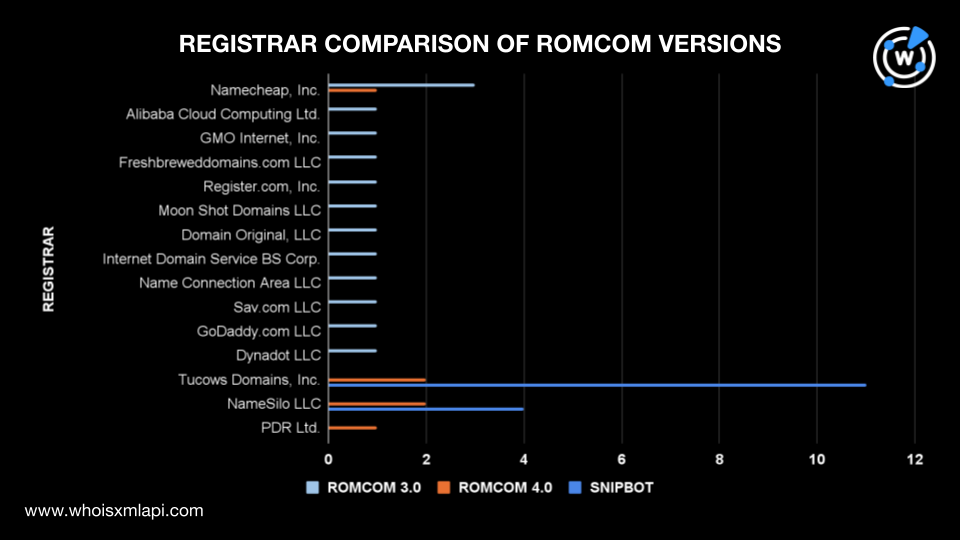
We performed separate bulk WHOIS lookups for each list to compare the IoCs of the three RomCom versions. We excluded domain IoCs that did not have current WHOIS data from our analysis. We were left with 42 of the 56 RomCom 3.0 IoCs, three of the nine RomCom 4.0 IoCs, and two of the 17 Snipbot IoCs. Below are our findings for the remaining indicators.
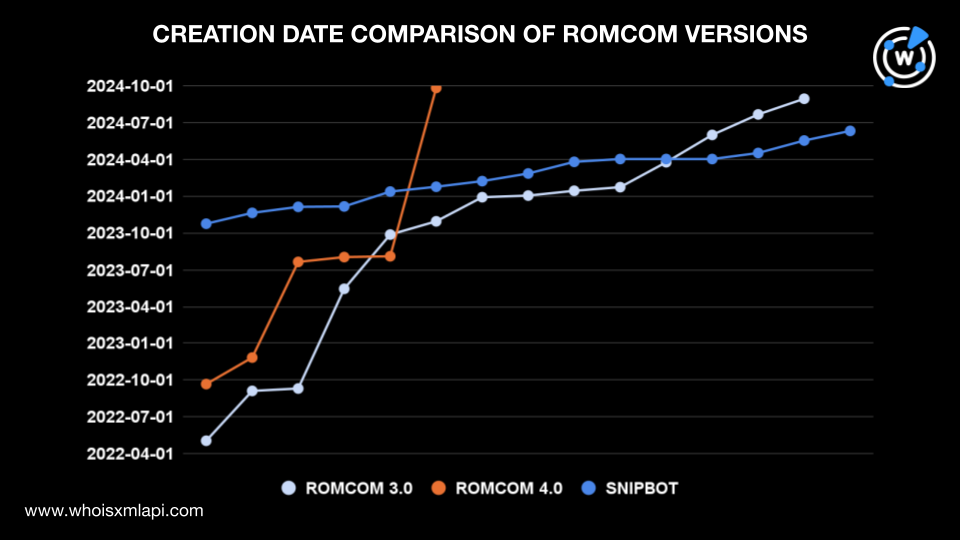
Four Snipbot domain IoCs were registered in the last quarter of 2023, but they were not detected in any incident until February 2024. A similar pattern can be seen for the 3.0 and 4.0 domain IoCs. Some were registered in 2022 but weren’t detected until 2023.
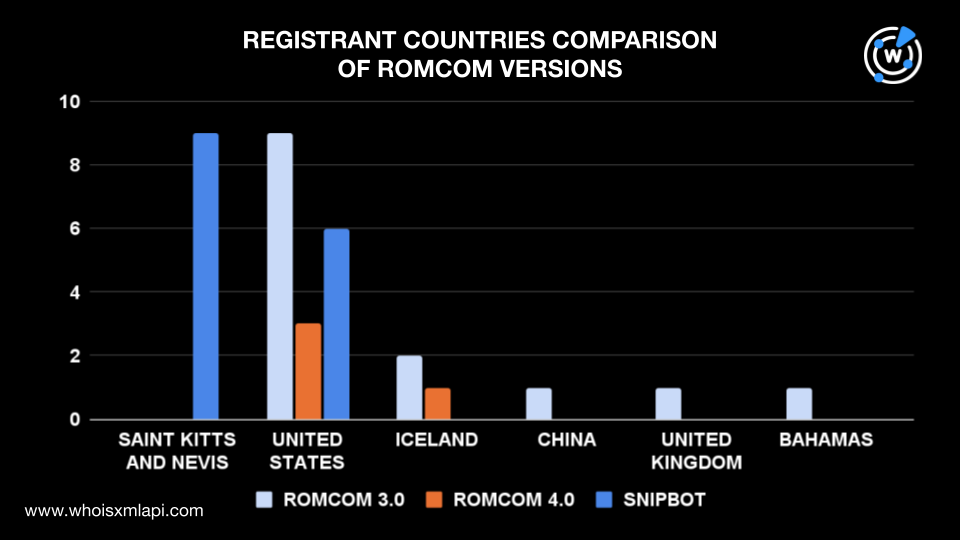
Only two registrant countries were consistent across the domain IoCs in the different RomCom versions. Nine from version 3.0, three from version 4.0, and six from Snipbot were registered in the U.S. Two domain IoCs from RomCom 3.0 and one from 4.0 were registered in Iceland. The IoCs of the newest version were primarily registered in Saint Kitts and Nevis.
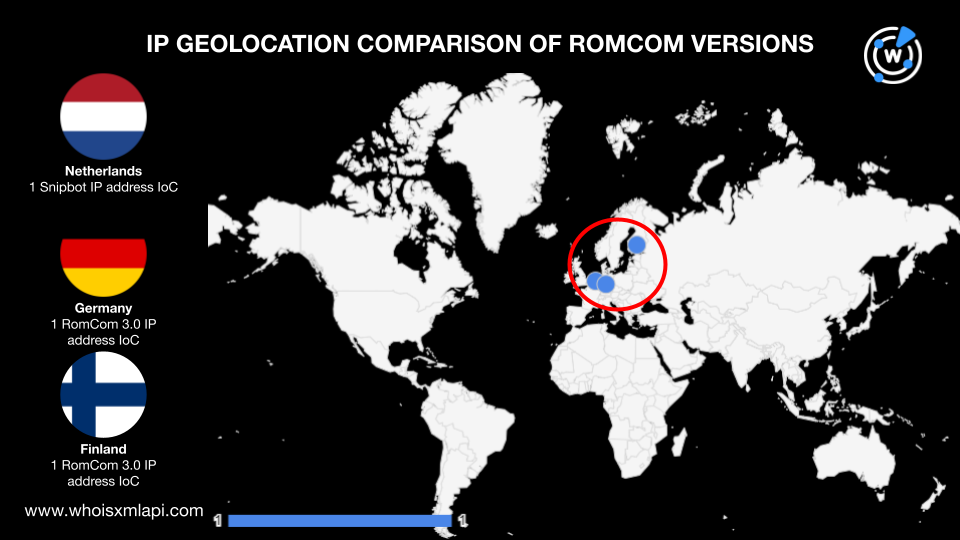
Next, we ran a bulk IP geolocation lookup for the three IP addresses identified as IoCs (one for Snipbot and two for RomCom 3.0) and found that:
The IoC list expansion for all three RomCom versions was performed on 82 domain IoCs, which we queried on WHOIS History API. The results showed they had 155 email addresses in their historical WHOIS records, 31 of which were public.
We queried the 31 public email addresses on Reverse WHOIS API and found 20 email-connected domains after removing duplicates and the IoCs. According to Threat Intelligence Lookup, one of these artifacts was involved in a malware attack.
The next step in our threat-hunting efforts was to run the 82 domain IoCs on DNS Lookup to find their IP resolutions. We found that 57 did not have active resolutions, while the remaining 25 resolved to 27 unique IP addresses, which were not on the original IoC list. Threat Intelligence Lookup revealed that all of them were associated with various threats. Some examples are shown below.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byRadix

Sponsored byCSC
