


|
||
|
||
The Cybersecurity & Infrastructure Security Agency (CISA) added CVE-2025-32433 and CVE-2024-42009 to the Known Exploited Vulnerabilities (KEV) Catalog on 9 June 2025 after they were reportedly abused by APT28 to hack government webmail servers in an operation dubbed “RoundPress.”
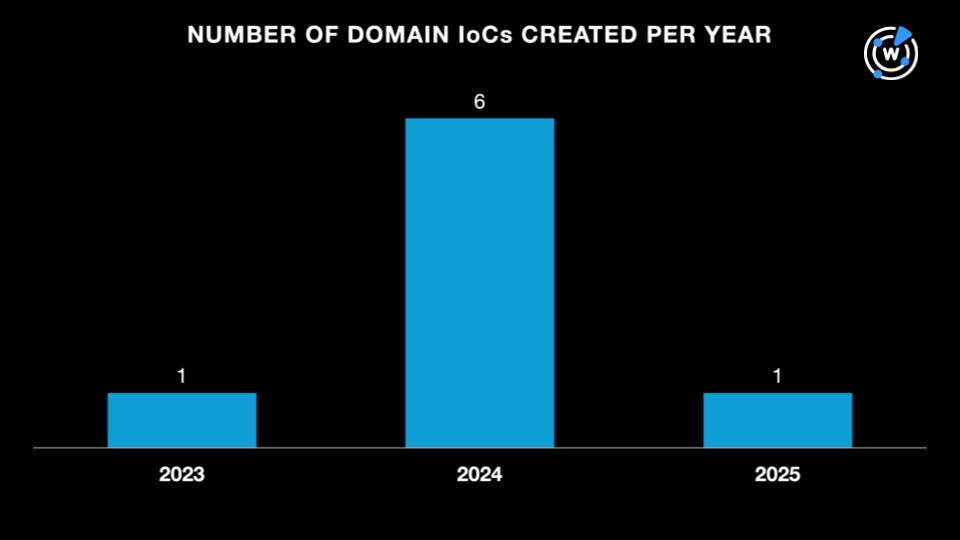
ESET researchers identified 19 indicators of compromise (IoCs) comprising 10 domains and nine IP addresses related to Operation RoundPress. WhoisXML API sought to uncover more potentially connected artifacts using domain and DNS intelligence and found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our analysis by seeking more information on the 10 domains identified as IoCs through a Bulk WHOIS API query. The results showed that eight of them had current WHOIS records.
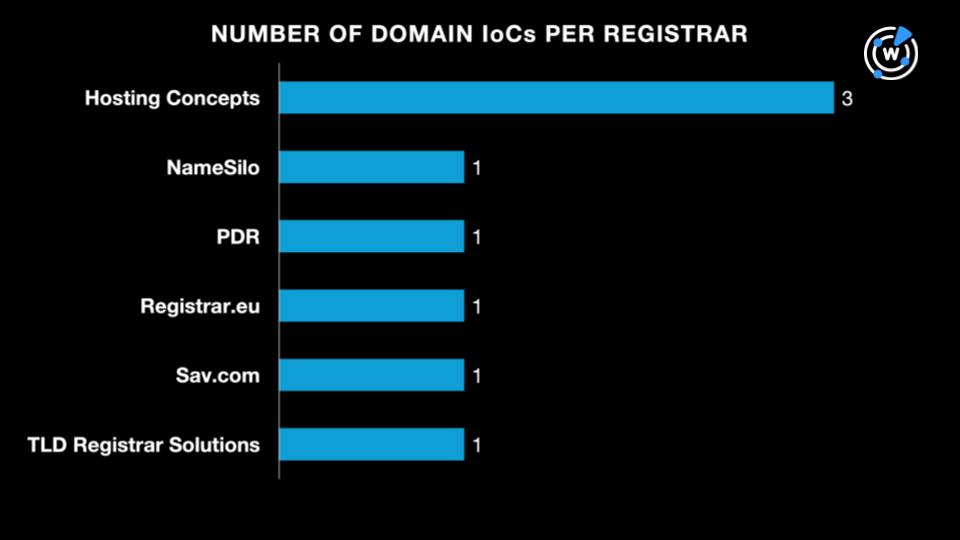
Hosting Concepts was the top registrar, accounting for three domains. In addition, one each was administered by NameSilo, PDR, Registrar.eu, Sav.com, and TLD Registrar Solutions.
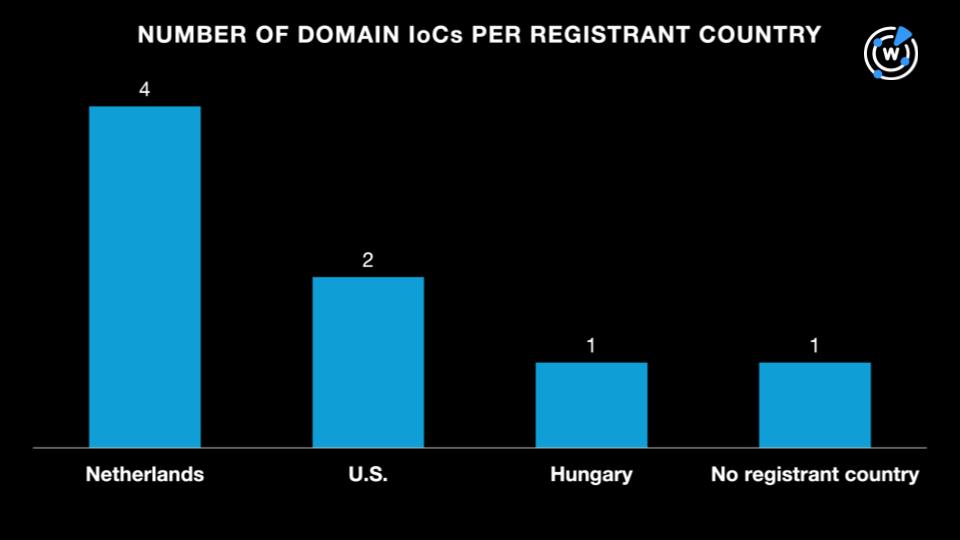
While one of the eight domains with current WHOIS records did not have a registrant country on record, the remaining seven were registered in three nations led by the Netherlands, which accounted for four domains. The U.S. accounted for two domains while the last one was registered in Hungary.
Next, we queried the 10 domains identified as IoCs on DNS Chronicle API and found that all of them had a total of 351 historical domain-to-IP resolutions. The IoC rnl[.]world, which accounted for 252 resolutions, recorded the oldest resolution dated 14 September 2018. Take a look at the details for five examples below.
| DOMAIN IoC | NUMBER OF HISTORICAL DOMAIN-TO-IP RESOLUTIONS | FIRST HISTORICAL DOMAIN-TO-IP RESOLUTION DATE |
|---|---|---|
| hfuu[.]de | 5 | 6 March 2024 |
| ikses[.]net | 7 | 1 December 2024 |
| lsjb[.]digital | 12 | 2 July 2024 |
| sqj[.]fr | 7 | 18 April 2024 |
| tuo[.]world | 26 | 18 March 2023 |
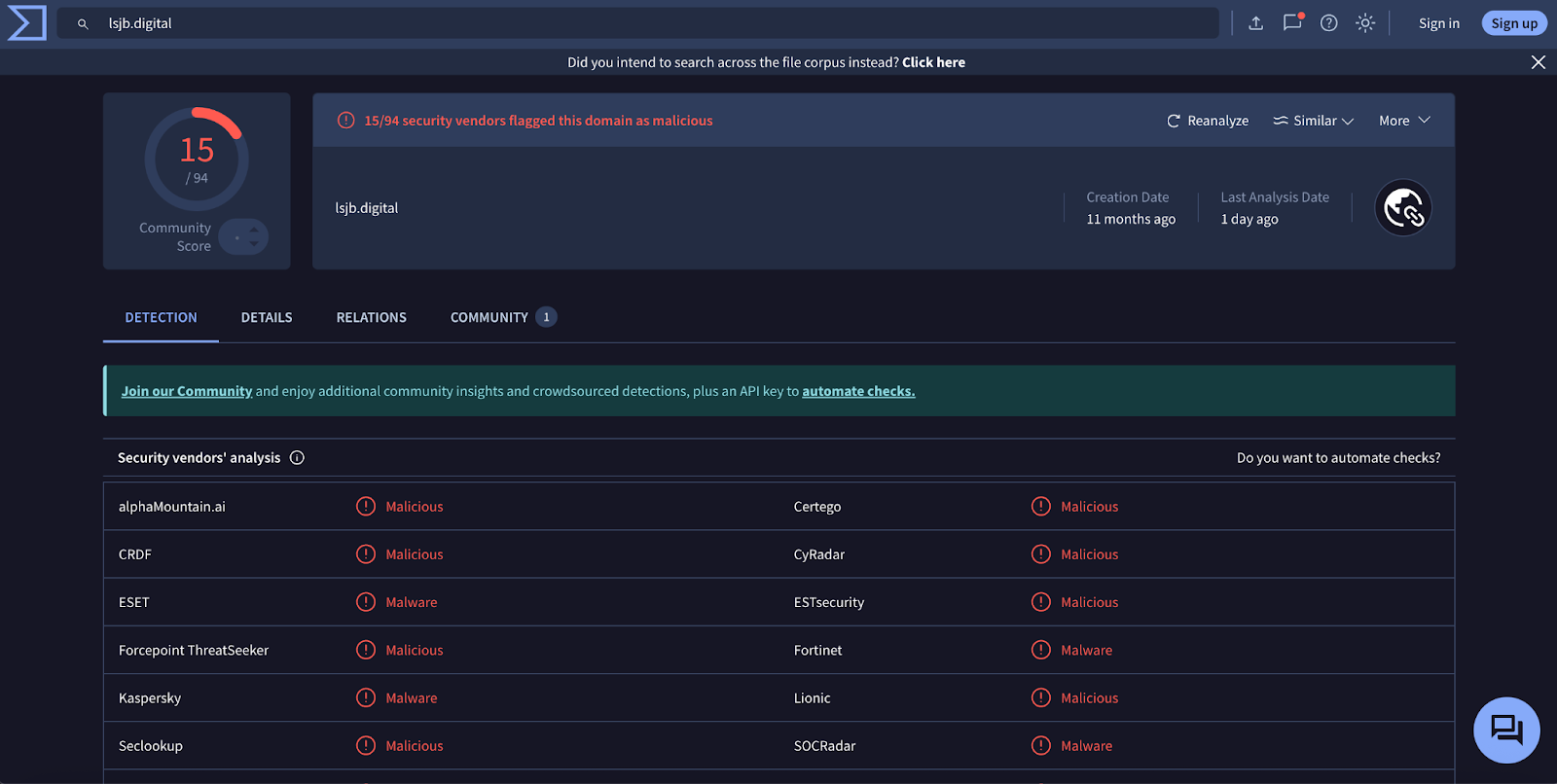
We also searched First Watch Malicious Domains Data Feed for the 10 domains identified as IoCs and discovered that lsjb[.]digital appeared as a domain likely to turn malicious on 1 July 2024, 318 days before it was classified as an IoC by ESET on 15 May 2025. Today, it is considered malicious by 15 out of 94 engines on VirusTotal.
After that, we queried the nine IP addresses identified as IoCs on Bulk IP Geolocation Lookup and found that:
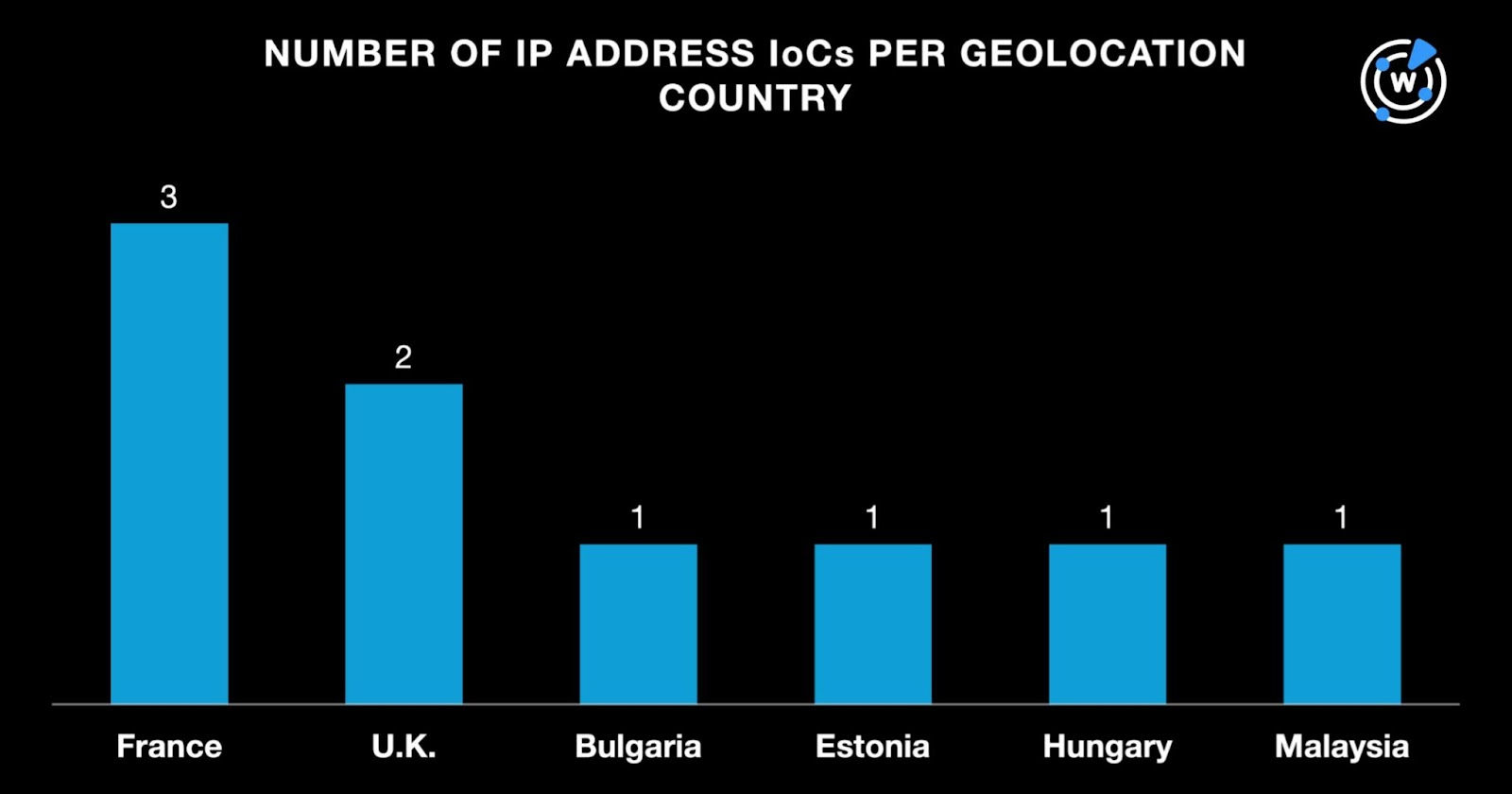
While two IP addresses did not have ISPs on record, the seven remaining ones were split among five ISPs led by M247, which accounted for three IPs. BelCloud, NET23VNet, Shinjiru Technology, and VibeGAMES administered one IP address each.

Our search for connected properties began with a WHOIS History API query for the 10 domains identified as IoCs. We discovered that three of them had email addresses in their historical WHOIS records. We uncovered five unique email addresses, three of which were public.
While a Reverse WHOIS API query for the three public email addresses did not turn up email-connected domains via current WHOIS records, we did uncover 8,222 email-connected domains via historical WHOIS records after duplicates and those already identified as IoCs were filtered out. Notably, many of them resembled the IoCs in that they were made up of 3—5 letters or letter-and-number combos.
A Threat Intelligence API query for the 8,222 email-connected domains showed that seven have already figured in cyber attacks.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign

Sponsored byRadix

Sponsored byWhoisXML API
