


|
||
|
||
In the recently published “Top 10 Malware Q2 2025,” the Center for Internet Security (CIS) Cyber Threat Intelligence (CTI) Team named the top 10 malware for the quarter, along with their corresponding indicators of compromise (IoCs).
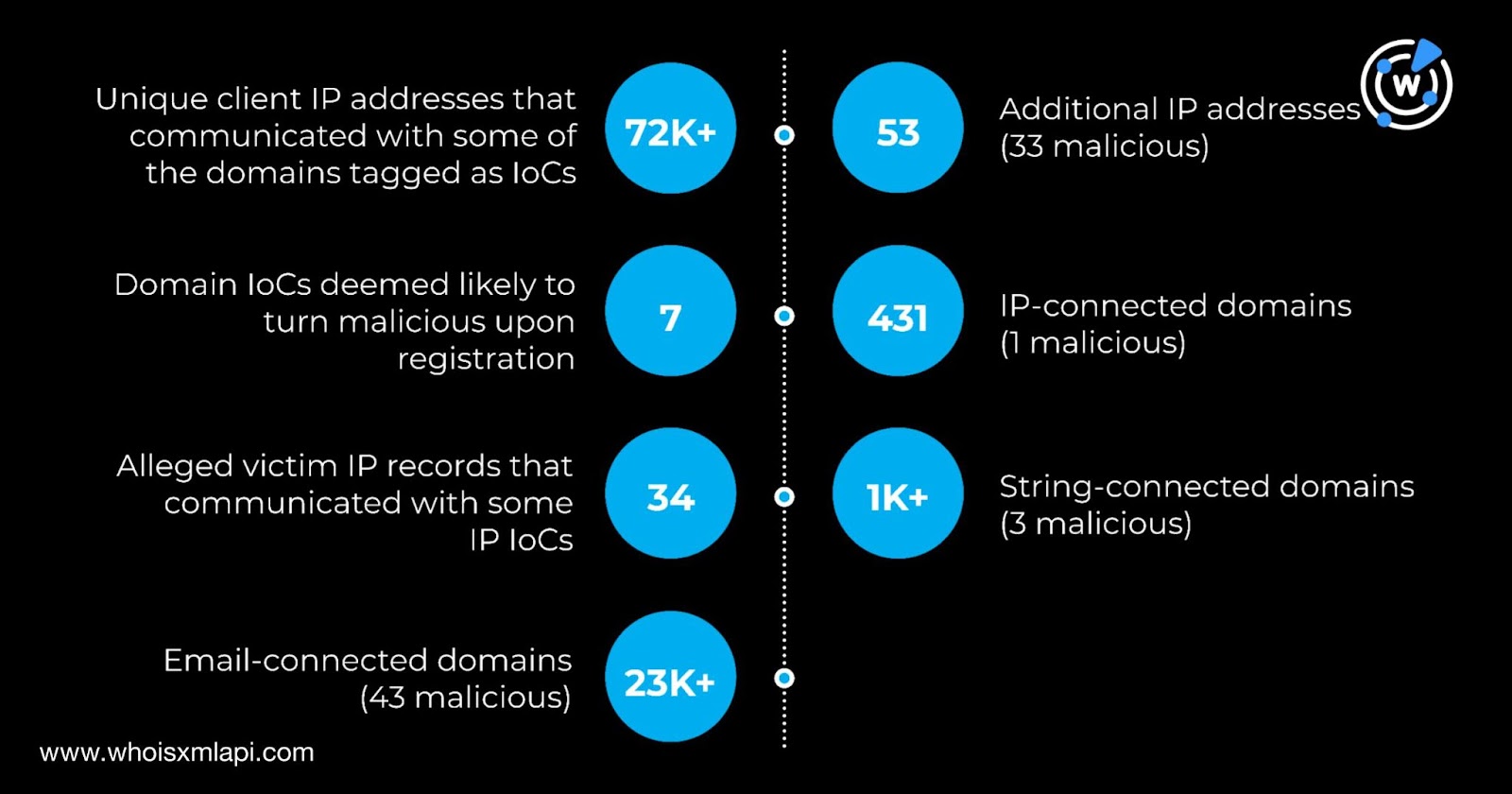
The team identified 62 IoCs for nine of the malware comprising 53 domains and nine IP addresses. Take a look at the breakdown below.
| RANK | MALWARE | DESCRIPTION | NUMBER OF DOMAIN IoCs | NUMBER OF IP IoCs |
|---|---|---|---|---|
| 1 | SocGholish | Downloader disguised as fake browser updates | 12 | 0 |
| 2 | ZPHP | Downloader disguised as fake browser updates | 5 | 0 |
| 3 | AgentTesla | Remote access Trojan (RAT) sold on cybercriminal forums | 6 | 0 |
| 4 | VenomRAT | RAT distributed via malicious spam | 4 | 0 |
| 5 | CoinMiner | Cryptocurrency miner either dropped by other malware or distributed via malicious spam | 1 | 0 |
| 6 | Mirai | Malware botnet for distributed denial-of-service (DDoS) attacks on Internet of Things (IoT) devices | 0 | 0 |
| 7 | NanoCore | RAT sold on cybercriminal forums distributed via malicious spam | 2 | 3 |
| 8 | Arechclient2 | RAT notable for its evasion tactics | 9 | 6 |
| 9 | ClearFake | Downloader disguised as fake browser updates | 6 | 0 |
| 10 | LandUpdate808 | Downloader disguised as fake browser updates | 8 | 0 |
Note that no domains or IP addresses were identified as IoCs for sixth placer, Mirai.
Read “Top 10 Malware of Q2 2025: A Deep Dive into the IoCs” to explore our findings obtained from our comprehensive array of WHOIS and DNS intel-gathering tools.
We traced the WHOIS and DNS footprints of the top 10 malware by expanding the list of IoCs. Our analysis led to these discoveries:
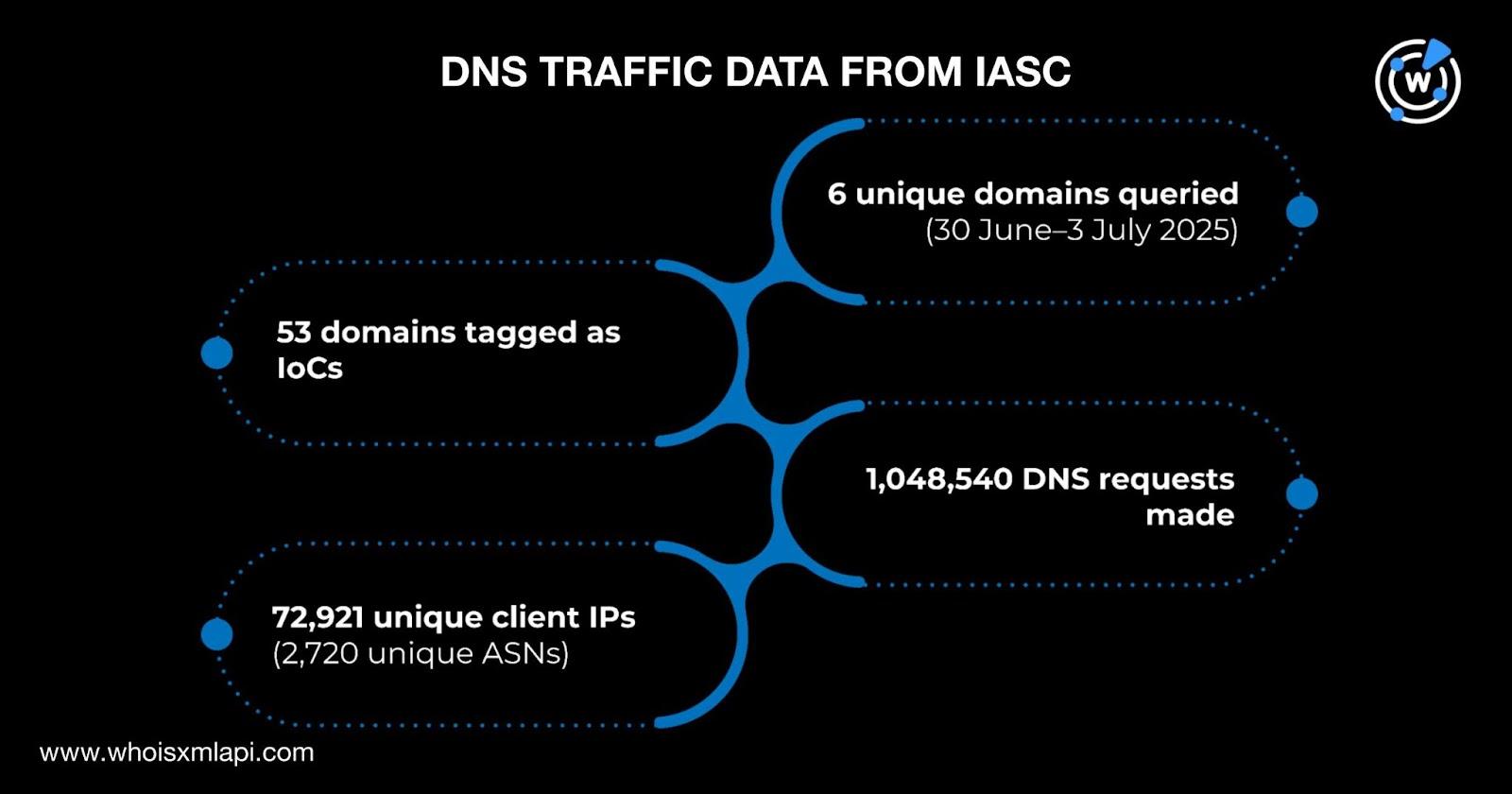
Apart from the WHOIS and DNS record findings we uncovered about the 62 IoCs, we also looked at sample DNS traffic data from the Internet Abuse Signal Collective (IASC) to further analyze the 53 domains tagged as IoCs. The sample data revealed that 72,921 unique client IP addresses tied to 2,720 unique ASNs queried six distinct domains between 30 June and 3 July 2025 via 1,048,540 DNS requests.
In addition, we queried the 53 domains tagged as IoCs on First Watch and found that seven appeared on various feeds 31—233 days before they were reported as attack IoCs on 18 July 2025. Take a look at three examples below.
| DOMAIN IoC | MALWARE | FIRST WATCH DATE ADDED | NUMBER OF DAYS PRIOR TO REPORTING DATE |
|---|---|---|---|
| emeraldpinesolutions[.]com | SocGholish | 17 June 2025 | 31 |
| sixfiguredigital[.]group | AgentTesla | 27 November 2024 | 233 |
| candyxpdf[.]com | Arechclient2 | 26 February 2025 | 142 |
After looking deeper into the 62 IoCs CIS CTI identified, we hunted for new artifacts and unearthed 25,633 web properties.
Our hunt for additional IP addresses began with a DNS Lookup API query for the current IP resolutions of the 53 domains identified as IoCs. We discovered that 42 of the domains actively resolved to 53 unique IP addresses after removing duplicates and those already identified as IoCs.
We then queried the 53 IP addresses on Threat Intelligence API and found out that 33 have already been weaponized for various attacks. Here are five examples.
| MALICIOUS ADDITIONAL IP ADDRESS | ASSOCIATED THREATS |
|---|---|
| 104[.]18[.]21[.]135 | Generic threat |
| 15[.]197[.]148[.]33 | Phishing Generic threat Malware distribution Suspicious activity Command and control (C&C) |
| 172[.]67[.]128[.]220 | Phishing Malware distribution Generic threat |
| 173[.]254[.]31[.]34 | Attack Spam campaign Malware distribution |
| 216[.]144[.]210[.]189 | C&C |
Note that Bulk IP Geolocation Lookup also provided us with critical insights particularly regarding similarities between the nine IP addresses tagged as IoCs and the 53 additional IPs from our analysis. Specifically, we discovered that India, Russia, and the U.S.—three of the four geolocation countries of the IoCs—also appeared in the list of origins for the additional IP addresses. DigitalOcean—one of the two ISPs for the IoCs—also appeared in the list of administrators for the additional IP addresses.
After adding the 53 IP addresses to the nine already tagged as IoCs, we queried the 62 IP addresses on Reverse IP API and found out that 18 could be dedicated hosts. The 18 possibly dedicated IP addresses hosted 431 IP-connected domains after filtering out duplicates, those already tagged as IoCs, and the email-connected domains.
Want to know more about the top 10 malware of Q2 2025? Download our threat report “Top 10 Malware of Q2 2025: A Deep Dive into the IoCs” now.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byVerisign
