

|
||
A dramatic increase in DNS reflection/amplification DDoS attacks abusing Domain Name System Security Extension (DNSSEC) configured domains have been observed in the past few months, according to a security bulletin released by Akamai’s Security Intelligence Response Team (SIRT). Since the beginning of November 2015, Akamai SIRT reports to have observed the domain “leveraged to launch DDoS attacks against customers in multiple verticals over the same time period, and it is most likely the work of attackers making use of a DDoS-for-Hire service that uses purchased VPS services, public proxies, a classic botnet and basic attack types such as DNS reflection attacks, SYN floods, UDP floods, SSDP floods, NTP floods, ICMP floods and even HTTP GET floods.”
Traffic analysis for the attack campaigns have indicated that the DNS reflection and amplification attacks are abusing DNSSEC configured domains to amplify attack response.
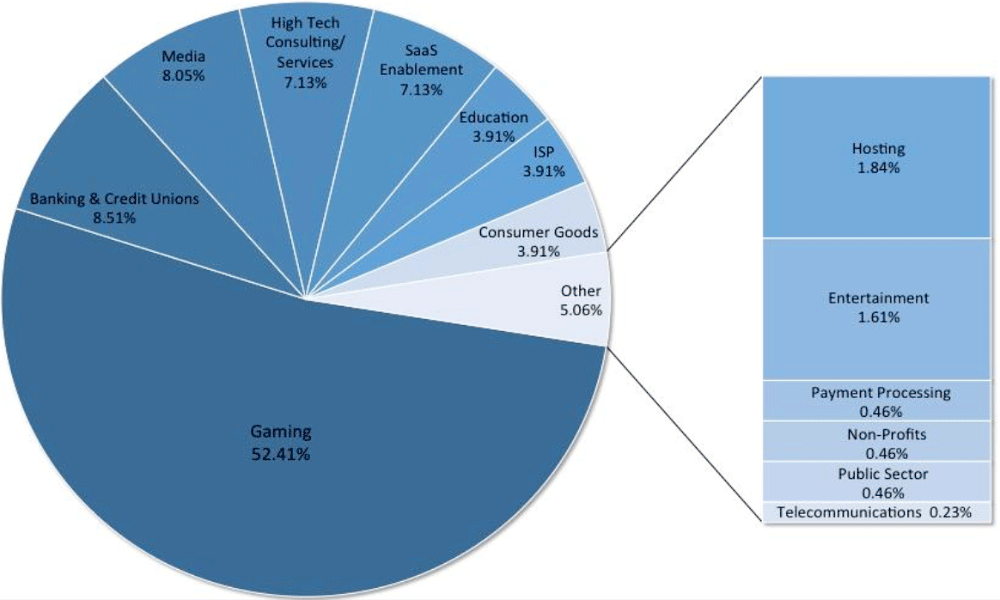 DDoS Attack Distribution by Industry Vertical – Breakdown by Industry Vertical of DDoS attacks mitigated against the DNSSEC reflection method (Source: Akamai / Click to Enlarge)
DDoS Attack Distribution by Industry Vertical – Breakdown by Industry Vertical of DDoS attacks mitigated against the DNSSEC reflection method (Source: Akamai / Click to Enlarge)
Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byCSC
