


|
||
|
||
This post was updated on Nov 14, 2023.
Analysts and researchers have been warning users about the dangers of newly registered domains (NRDs) for several years now. Of course, the simple fact of registering a new domain does not mean it is automatically bad. After all, virtually any new business or entrepreneurial activity starts with launching a website.
On the other hand, abusive new domain registrations with the intent of, say, cybersquatting known brands is still a recurring problem. For example, we keep identifying thousands of suspicious NRDs in our Newly Registered Domains Database, including those that look similar to known phishing domains.
Granted, a few thousand domains may not seem like a lot, bearing in mind that hundreds of thousands of new domains are registered daily. But that is still a lot, given the potential risks and damage a successful phishing attack could cause.
Since NRDs continue to be a threat, let’s recap what they are, the kinds of attacks they are part of, and how monitoring them can be beneficial to various cybersecurity stakeholders.
NRDs are domains that were registered or changed ownership within the past few weeks. Domain age is identifiable via WHOIS lookups or by integrating an NRD database into Internet-connected platforms and applications. The second option allows users to skip manual searches for WHOIS records to check if any domain of interest is newly registered.
Cyber attackers make it a point to avoid detection and blocking to succeed. And if their malware or exploits get discovered, they, of course, don’t want to be identified as perpetrators. These are some reasons why they use NRDs in their attacks, such as:
These days, users get tons of investment-related emails supposedly from reputable organizations giving updates, offering help, or promising refunds and huge sums of money.
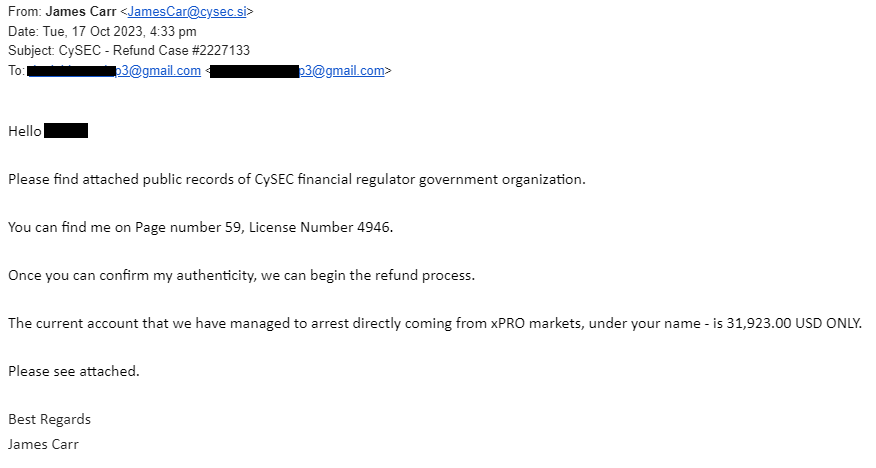
What may not be obvious at first is that attachments or embedded links and possibly even the email domains in these messages don’t belong to the institutions the senders claim to be from. And more often than not, the domains where the pages reside are newly registered and malicious.
Malware operators, including ransomware creators, often distribute their malicious wares via NRDs, too. This approach may allow them to successfully infiltrate even protected target networks because the domains they use have yet to appear in blacklists.
In light of these and other attacks involving recent domain registrations, integrating NRD lists into existing solutions and systems can help lessen the chances of yet unknown threat vectors bypassing security perimeters.
Three types of security enterprise users can benefit from NRD database integration, namely:
Security software manufacturers can integrate an NRD database into their offerings so they can alert users to dangerous NRDs attempting to communicate with their protected systems. Domains that seem to imitate big brands can also be tracked.
Depending on the plan selected, information about NRDs can also contain complete WHOIS records, which may come in handy in attributing domain ownership. Record redaction is, after all, probably a sign that the domains do not pertain to big established brands, as top Fortune companies often tend to leave their WHOIS records public.
Dedicated security or security operations centers (SOCs) personnel can work with security solution providers that incorporate NRD filtering into their security information and event management (SIEM) and security orchestration, automation, and response (SOAR) platforms so they can watch out for signs of malicious activity coming from potential attack vectors.
Managed security service providers (MSSPs) and other third-party security providers can also add an NRD list to their threat sources to screen them on behalf of clients. The database can serve as an additional source of threat intelligence so they can more effectively ward off attempts and attacks directed at their customers’ networks.
1. Go to the NRD Database page by accessing https://newly-registered-domains.whoisxmlapi.com/ on your browser.
2. Reach out to us for more information about the product by clicking “Order database” and filling out the contact form or access data samples by clicking “Download database samples.”
We offer a variety of data packages covering the features identified below.
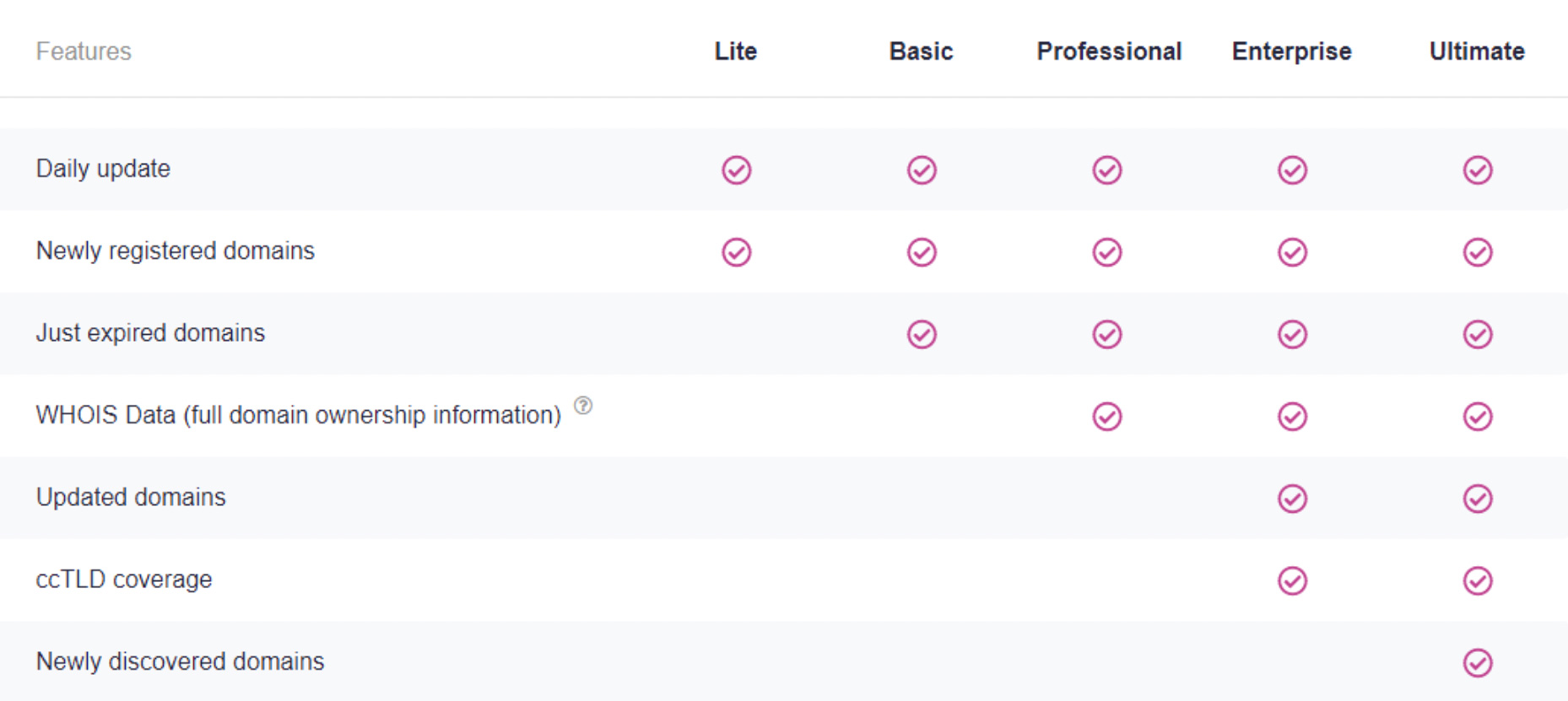
Ultimate Simple: These NRD files contain everything in the Ultimate package, except for the raw data fields (i.e., rawText, registryDataRawText, registrantContact.rawText, whoisRecordRawText, administrativeContact.rawText, billingContact.rawText, technicalContact.rawText, zoneContact.rawText), making them more lightweight than the Ultimate files. Download data samples here.
3. ewly Registered Domains 2.0 data feed files are available through a directory sorted by date.

For a given date, you can select the file format you want to download (JSON or CSV) and the file you are interested in. For the actual NRD data, select the file with “data” in the name (e.g., nrd.2023-11-01.lite.daily.data.csv.gz). The “stats” file, meanwhile, gives you an overview of the number of records available for each TLD on the selected day.
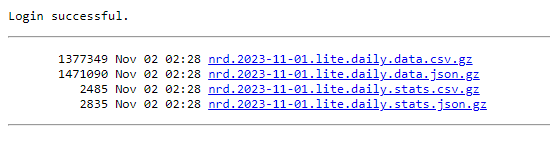
To illustrate the functionalities of the NRD Database, we downloaded the NRD data feed dated 1 November 2023, containing 466,034 newly added and recently expired domains. Below are some of the capabilities of the data feed, along with sample data.
The NRD Database can complement the intelligence sources of security platforms to help warn users against suspicious domains that could figure in cyber attacks.
For example, among the NRDs in the data feed is lemontsrade[.]site, which was already flagged as malicious a day after it appeared in the DNS.
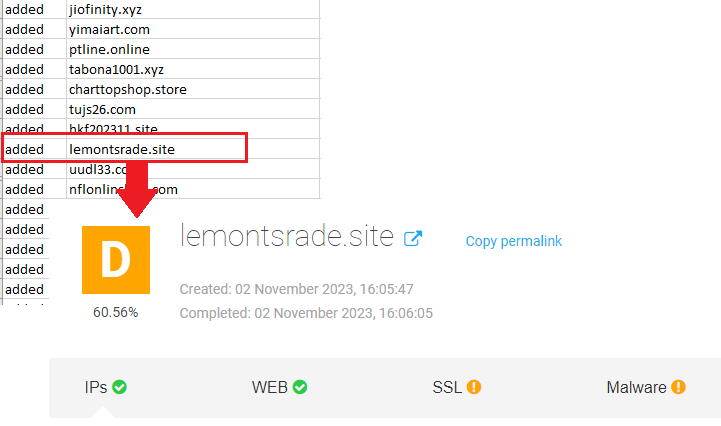
Find Attributes to Uncover Connected Artifacts
The NRD Database can also come with complete WHOIS records, giving security teams more data to uncover connected artifacts. For example, the domain weesc[.]com has the following WHOIS information:
Filtering the database using these details, we uncovered two more domains that the same person could have registered on the same day.
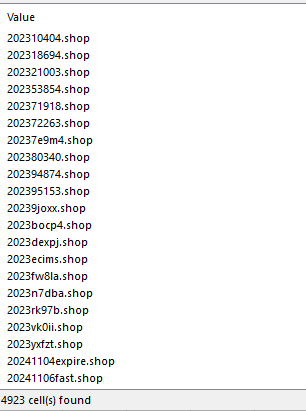
With the help of the NRD Database, domain names possibly created using domain generation algorithms (DGAs) can be detected, screened, and flagged accordingly. Some possible DGA-created domains found in the database dated 1 November 2023 were:
In the same way, you can filter the data feed to see DGA-created domains that were recently updated or have expired. Hundreds of .shop domains that began with the strings 2023 or 2024 and contained random alphanumeric characters were detected in the 1 November 2023 data feed. Some have already been tagged as malicious.
These dropped domains may have been registered in bulk by the same threat actors and left to expire, possibly after only a few of them were gradually utilized.
Domains that are left to expire may have some interesting stories to tell. Some may have been dropped after a business failure, while other registrants may have lost interest. On the other hand, some expired domains may have served their purposes already.
For instance, the domain jkgyg0hdxdg4fgd1login[.]com was among those dropped on 1 November 2023. It contains the string login and has been reported as malicious. Since the domain has already been flagged and most likely blocked by various security teams, the registrant may have left it to expire. There are dozens of recently expired malicious domains on the 1 November 2023 data feed, including:
The Enterprise and Ultimate packages also give you access to recently updated domains. This data allows you to answer insightful questions, including:
While it’d be unfair to treat all NRDs as malicious, suspicious instances remain commonly found in our feeds daily. Several of the examples above, for instance, illustrate the importance of monitoring NRDs to remain on the safe side.
Sponsored byCSC

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign
