


|
||
|
||
In 2019, Credit Suisse was hit by a spying scandal that quickly spiraled into several things—a public confrontation, a resignation, and a death. Iqbal Khan, the bank’s former head of wealth management, confronted a private investigator on the streets on 17 September after noticing that someone was following him. Chief operating officer (COO) Pierre-Olivier Bouée resigned after admitting that he placed Khan under surveillance. The bank’s contractor, who hired the private investigator, then committed suicide.
As the bank continues to face the spying scandal and its reputational repercussions, our Typosquatting Data Feed also kept detecting Credit Suisse-related domains. Although these two events are likely unrelated, it goes to show that even when a company is facing all sorts of problems, cybersecurity remains a pressing concern.
The typosquatting database detected 53 domain registrations that refer to credit suisse in their names since the beginning in October 2019. Among these were those reported on IBM X-Force Exchange on 6 May. These indicators of compromise (IoCs) were flagged for ties to phishing, typosquatting, and credential theft. Below are the domains and the IP addresses they resolve to:
These domains’ registrar is Panama-based Namecheap. And WhoisGuard protects their registrants’ contact details. The typosquatting database also detected other domains that don’t share any similarities with the others in terms of WHOIS details. Two of them are:
Both domains shared the same IP address and were registered on 27 March. Their registrar is also Colorado-based Name.com.
Given the potentially malicious domains and their respective IP addresses, security teams are advised to block access to them at the URL and IP levels. There may be other possible IoCs, particularly typosquatting domains.
Using Reverse IP/DNS API, we can see lists of domains associated with the IP addresses. For 91[.]195[.]240[.]94, for instance, the reverse IP/DNS tool returned at least 300 records, including adult-related domains like thedatingdiva[.]net, 09512[.]mmsex[.]info, roomgirl[.]net, and asiadx[.]com, among many others. Although some of the domains may seem legitimate, a majority contained random strings of alphanumeric characters, making them suspicious. On top of that, the IP address is deemed malicious by Threat Intelligence Platform (TIP).
That said, blocking access to the IP address may help protect organizations from hundreds of malicious domains. Note, though, that doing so will prevent users from visiting legitimate domains that share the same IP address.
The domains therealcreditsuisse[.]com and theofficialcreditsuisse[.]com also use the same name server—ns1[.]name[.]com. Given that, we can see a list of domains that use the same name server via Reverse NS API.

As shown in the screenshot above, 16,877 domains use the same name server as therealcreditsuisse[.]com and theofficialcreditsuisse[.]com—likely because ns1[.]name[.]com is a widely shared resource.
Now that we have seen the typosquatting domains’ infrastructure let’s take a look at the legitimate Credit Suisse domain, credit-suisse[.]com. Using DNS Lookup API, we found the following details:
The Domain Name System (DNS) details of credit-suisse[.]com vastly differed from those of the typosquatting domains. The five domains associated with its IP address, for instance, are all related to the bank. As such, we can say that Credit Suisse does not use shared IP services, unlike the IoCs.
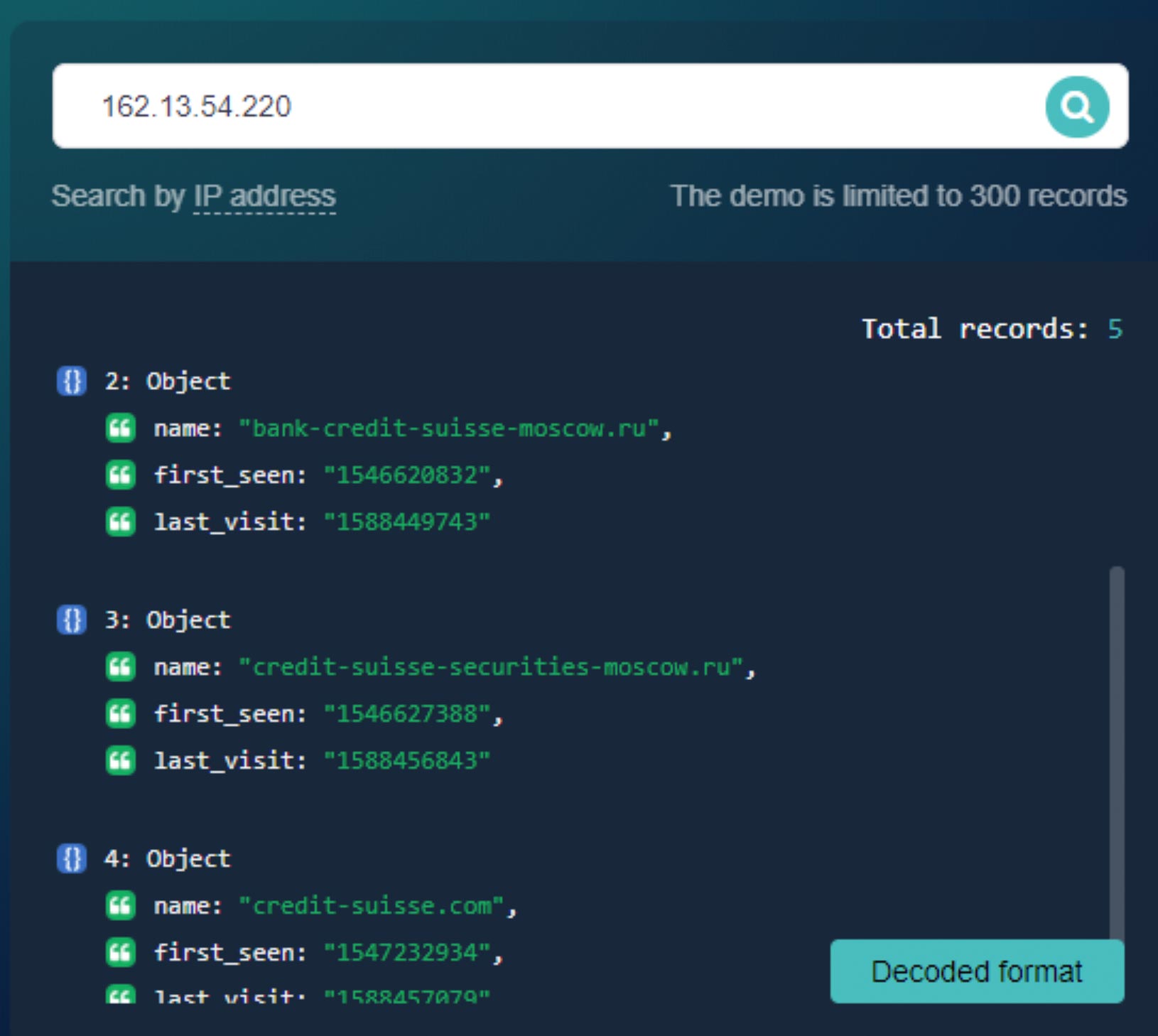
A Reverse MX API query shows that 75 domains, most of which are owned by Credit Suisse as well, share the same mail server.

A reverse NS lookup, meanwhile, showed 878 domains, a far cry from the 16,877 that used the name server of the typosquatting domain.

Although Credit Suisse already has a lot on its plate, its cybersecurity team can’t afford to get sidetracked. Cybercriminals have their eyes on them and are registering typo domains that they could use to victimize the bank’s clients. Preventing threats would thus be a lucrative initiative. But as we’ve shown, typosquatting data feeds and passive DNS lookup tools may be able to help.
Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byVerisign
