


|
||
|
||
The videogame industry has outperformed the movie and North American sports industry in 2020, and market experts expect the trend to continue on in 2021. So reports about the increasing cyber attacks targeting the said industry is not surprising as threat actors tend to go after lucrative targets.
In line with that, the WXA security research team decided to check how the gaming industry is represented in the Domain Name System (DNS), particularly in terms of domain registration.
Our analysis focused on four of the most popular gaming companies—Bandai Namco, Epic Games, Electronic Arts, and Ubisoft. Also included in the analysis is the broader term “esport.”
Feel free to download the complete list of additional IoCs and artifacts related to this threat research. Our main findings are also further detailed below.
Using Domains & Subdomains Search of the Domain Research Suite (DRS), we found 2,736 properties related to the aforementioned four gaming companies. When we add the results for the search string “esport,” this number balloons to more than 22,700 domains and subdomains. The table below shows the breakdown for each search string.
| Search String | Domains Added Since January 2020 as of 3 September 2021 | Subdomains Added Since January 2020 as of 3 September 2021 | Total | |
|---|---|---|---|---|
| Electronic Arts | “electronic” + “arts | 446 | 225 | 671 |
| Epic Games | “epic” + “games” | 684 | 395 | 1,079 |
| Bandai Namco | “bandai” + “namco” | 250 | 63 | 313 |
| Ubisoft | “ubisoft” | 397 | 276 | 673 |
| NA | “esport” | 10,000+ | 10,000+ | 20,000+ |
| Grand total | 11,777+ | 10,959+ | 22,736+ | |
Three of the four gaming companies had redacted WHOIS registrant email addresses, making it difficult to attribute domains to them. For the company with an unredacted registrant email address, we found 21 attributable domains.
We used the registrant organization and name revealed by Historical WHOIS Search for the rest of the companies and found 121 attributable domains. All in all, about 7% of the domains with WHOIS records returned by Bulk WHOIS Search can be publicly attributed to the gaming companies. Also, about 63% of the total number of domains and subdomains resolve to active IP addresses.
Some domains and subdomains were tagged “malicious” on the Threat Intelligence Platform (TIP). These include the following, which resolve to active IP addresses:
| epicsgames[.]net | 2[.]57[.]90[.]16 |
| epicgames[.]com[.]tw | 5[.]23[.]51[.]236 |
| epicgamesplay[.]com | 74[.]206[.]228[.]78 173[.]239[.]8[.]164 173[.]239[.]5[.]6 |
| g-2-esport[.]com | 185[.]178[.]208[.]160 |
| esportscase[.]ru | 95[.]181[.]152[.]14 |
| vivelesport[.]fr | 213[.]186[.]33[.]5 |
| epicgames-freevbucks[.]easytricky[.]com | 3[.]223[.]115[.]185 |
| www[.]epicgames-freevbucks[.]easytricky[.]com | 3[.]223[.]115[.]185 |
| yubisoft[.]twilightparadox[.]com | 129[.]159[.]45[.]185 |
| new-esport[.]itemdb[.]com | 209[.]126[.]1[.]27 |
A few IP addresses are noteworthy since they are shared by a few domains only and could be dedicated. The IP address 129[.]159[.]45[.]185, for instance, only had one domain resolving to it—the malicious domain yubisoft[.]twilightparadox[.]com.
The number of related domains can further be expanded by uncovering the historical WHOIS records of these malicious domains and looking for connected properties that share the same registrant email address.
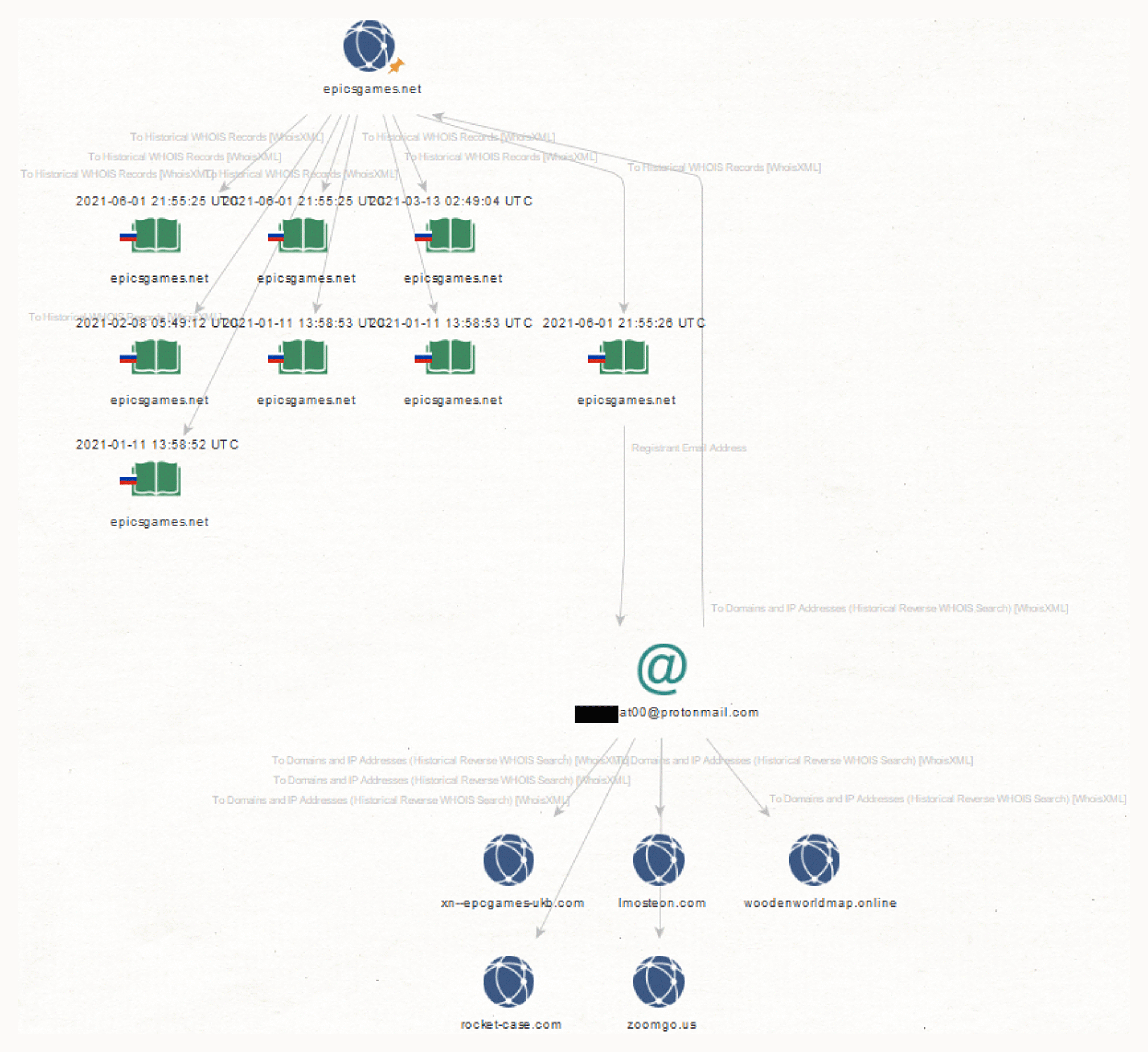
While many of the domains had redacted WHOIS records, a few of the registrant email addresses remained public. Take, for example, epicsgames[.]net whose registrant email address is *****lat00@protonmail[.]com (a few characters hidden for privacy). The Maltego Historical Reverse WHOIS Search transform reveals that five other domains had the same registrant email address.
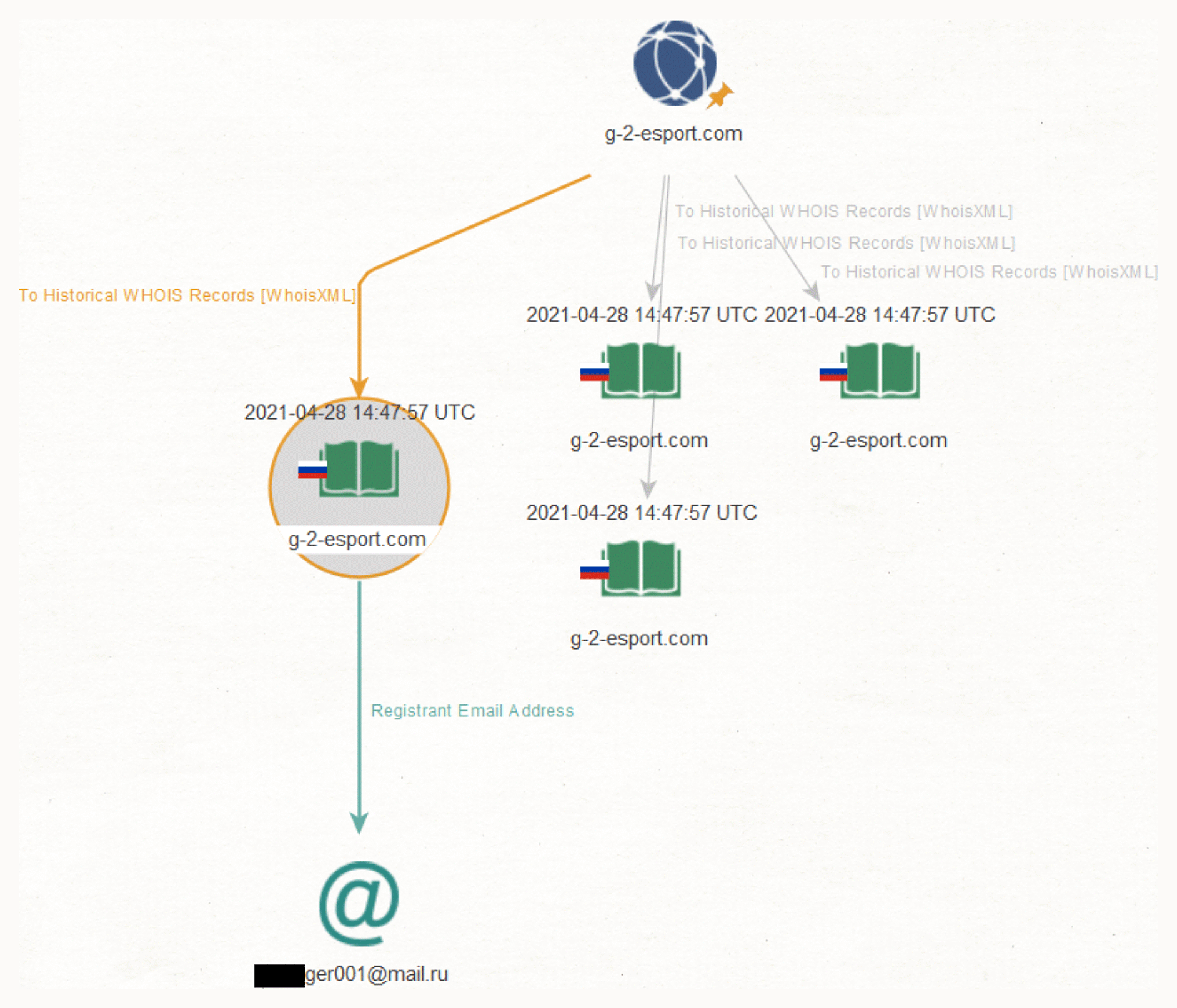
Another example is g-2-esport[.]com, whose registrant email address *****ger001@mail[.]ru is shared by 30 other domain names.
Most of the domains resolved to parked pages, while some subdomains resolved to 404 pages. The domain epicgames[.]com[.]tw remains active despite being reported as malicious. Users with less stringent firewall rules might still be able to visit the site and expose themselves to threat actors. The domain’s screenshot lookup result is shown below.
There have been many Internet properties related to gaming companies and added to the DNS since January 2020. While this could mean a growing interest in the industry, a portion of that growth could be suspicious at the very least—especially as some of them have already been flagged as malicious.
Suspicious domains and subdomains related to the gaming industry can provide additional cyber intelligence to reinforce your cybersecurity strategies. Do not hesitate to contact us for a complete list of the properties mentioned in this post or to discuss potential security research collaborations.
Sponsored byCSC

Sponsored byRadix

Sponsored byVerisign

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byDNIB.com
