


|
||
|
||
Last year, several governments reportedly used the NSO Group’s spyware Pegasus to exploit a zero-day vulnerability in WhatsApp to spy on journalists, opposition politicians, and dissidents via their mobile devices. Apple quickly addressed the issue by launching more powerful data protection features.
This April, another zero-click spyware maker QuaDream surfaced in relation to ongoing espionage campaigns targeting anyone who owns an iOS device running iOS 14. The threat group’s spyware dubbed “KingsPawn” exploits a zero-day vulnerability in the Calendar app.
Microsoft published an in-depth analysis of KingsPawn where they named 164 domains as indicators of compromise (IoCs). We added the string com.apple from the file and folder host names cited in the research. We then expanded the existing IoC list by identifying other possibly connected web properties through DNS connections, including:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Despite being identified as KingsPawn IoCs, 40 of the domains Microsoft listed in their report weren’t currently being detected as malicious. Half of them are:
Of the 40 domains listed, 36 appeared to be unreachable. The remaining four IoCs are currently up for sale based on our screenshot lookups.
A bulk WHOIS lookup for the IoCs revealed they were created between 4 January 2022 and 3 April 2023, about 10 days before news about the KingsPawn attack broke. The 149 domains that had retrievable WHOIS records were spread across six registrars. Porkbun accounted for 78 of the web properties, followed by GoDaddy with 67 domains. 1API GmbH, Netim, Sav.com, and Xin Net Technology Corp., meanwhile, were responsible for one IoC each.
To identify other KingsPawn-related artifacts, we subjected the IoCs to DNS lookups, which gave us 19 resolving IP addresses scattered across four countries led by the U.S. (16 IP addresses). The remaining three nations—France, Germany, and Switzerland—accounted for one IP address each. A bulk malware check for the IP hosts revealed that 11 of them were malicious.
Four of the IP hosts were each shared by a number of domains. 34[.]102[.]136[.]180, for instance, hosted nordmanetime[.]com and hotalsextra[.]com while 44[.]227[.]76[.]166 played host to zeebefg[.]com, topuprr[.]com, and koraliowe[.]com.
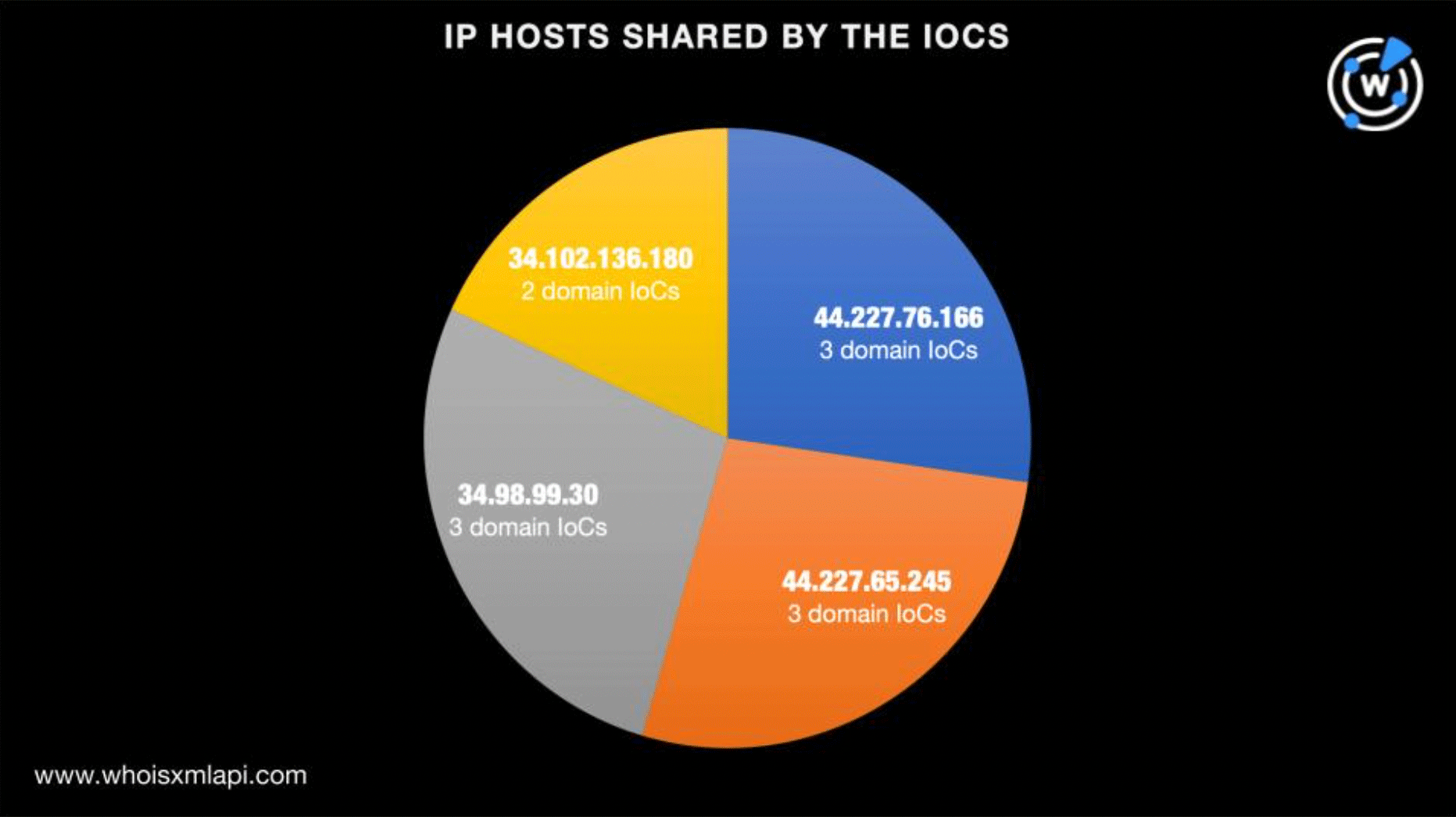
We then looked for domains hosted on the resolving IP addresses. Our reverse IP lookups uncovered 2,101 domains, 11 of which turned out to be malware hosts. Only one of them was up for sale while the remaining 10 were parked.
Microsoft’s KingsPawn study also identified three host-based IoCs, namely:
All three IoCs contained the string com.apple, which we then used to search for potentially connected subdomains on Domains & Subdomains Discovery. Our inquiry led to the discovery of 1,066 such web properties.
While 421 of the subdomains contained Apple’s legitimate domain name apple.com, manual scrutiny of each showed none were likely owned by the company. Also, 19 of them, now unreachable, turned out to be malware hosts.
The string-connected subdomains fell under the five domains in the following table.
| OMAIN | NUMBER OF MALICIOUS SUBDOMAINS |
|---|---|
| kinderramadan[.]com | 10 |
| ios-confirm[.]net | 3 |
| a-inc[.]tk | 2 |
| bijuprabhakar[.]com | 2 |
| tondi-asu[.]com | 1 |
Also, besides the legitimate Apple domain, other popular strings typically connected to the company and its products also appeared as strings in the subdomains. The string appleid and its variations, including those with typos, apple-id, apple.id, appleld, and id-apple, appeared most (442 subdomains). The string icloud, meanwhile, was present in 131 subdomains. Capping the top 3 was appstore and its variation applestore, which could be found in 31 subdomains. The nine remaining strings we observed were:
Note, though, that some of the subdomains contained more than one of the Apple-specific strings above. Examples include icloud[.]com[.]apple[.]applecare-support[.]us, icloud[.]com[.]apple[.]id-identify[.]us, and icloud[.]com[.]apple[.]findmylphone[.]top.
Our IoC expansion analysis revealed that more than 3,000 domains and subdomains containing Apple’s company, product, and service names already exist in the DNS. They could serve as hosts to zero-click spyware like KingsPawn.
If you wish to perform a similar investigation or get access to the full data behind this research, please don’t hesitate to contact us.
Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byCSC

Sponsored byVerisign

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byDNIB.com
