


|
||
|
||
ReliaQuest named LockBit one of the most effective and undoubtedly most prolific currently active ransomware groups today. In fact, the malware topped their latest ransomware quarterly list for the first three months of 2023, a continuation of their 2022 observation.
LockBit initially piqued researchers’ interest when it was distributed via SocGholish infections last year. Today, the ransomware operators have taken to employing the ransomware-as-a-service (RaaS) model.
In line with our goal of making the Internet safer and more transparent, we sought to expand a publicly available list of LockBit IoCs to uncover other potentially connected artifacts. Our analysis found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
AlienVault OTX publicized 198 LockBit IoCs, specifically 195 domains and three IP addresses.
We began our investigation by determining which of the domains identified as IoCs remained live via screenshot lookups. A majority, 162 to be exact, continued to host live content.
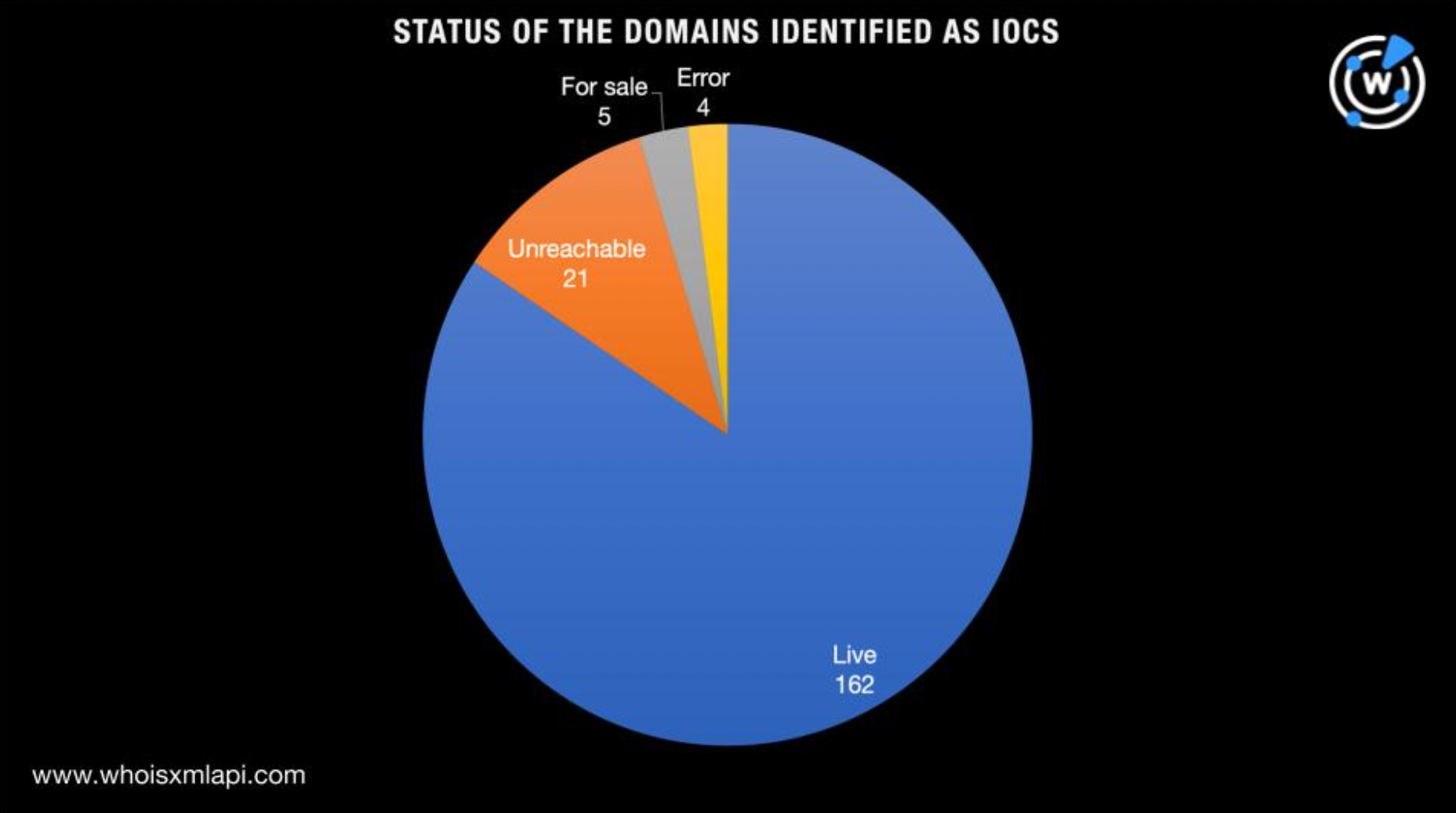
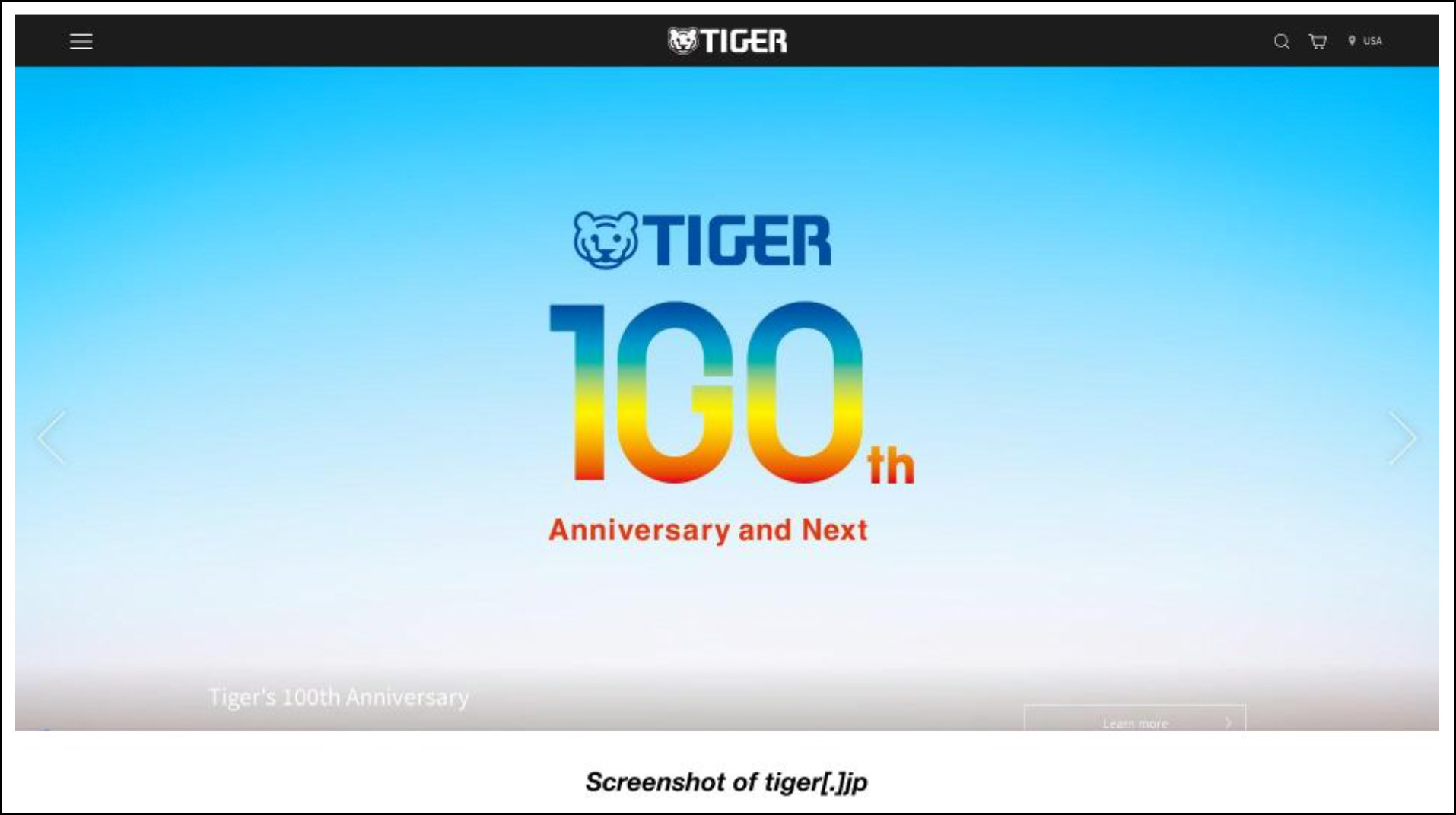
While it’s a common practice to take down malicious domains once detected, some may remain up because they are actually legitimate but have been compromised. An example would be tiger[.]jp, a legitimate domain of Tiger Corporation. A malware check for it, in fact, shows that it’s not currently considered malicious.
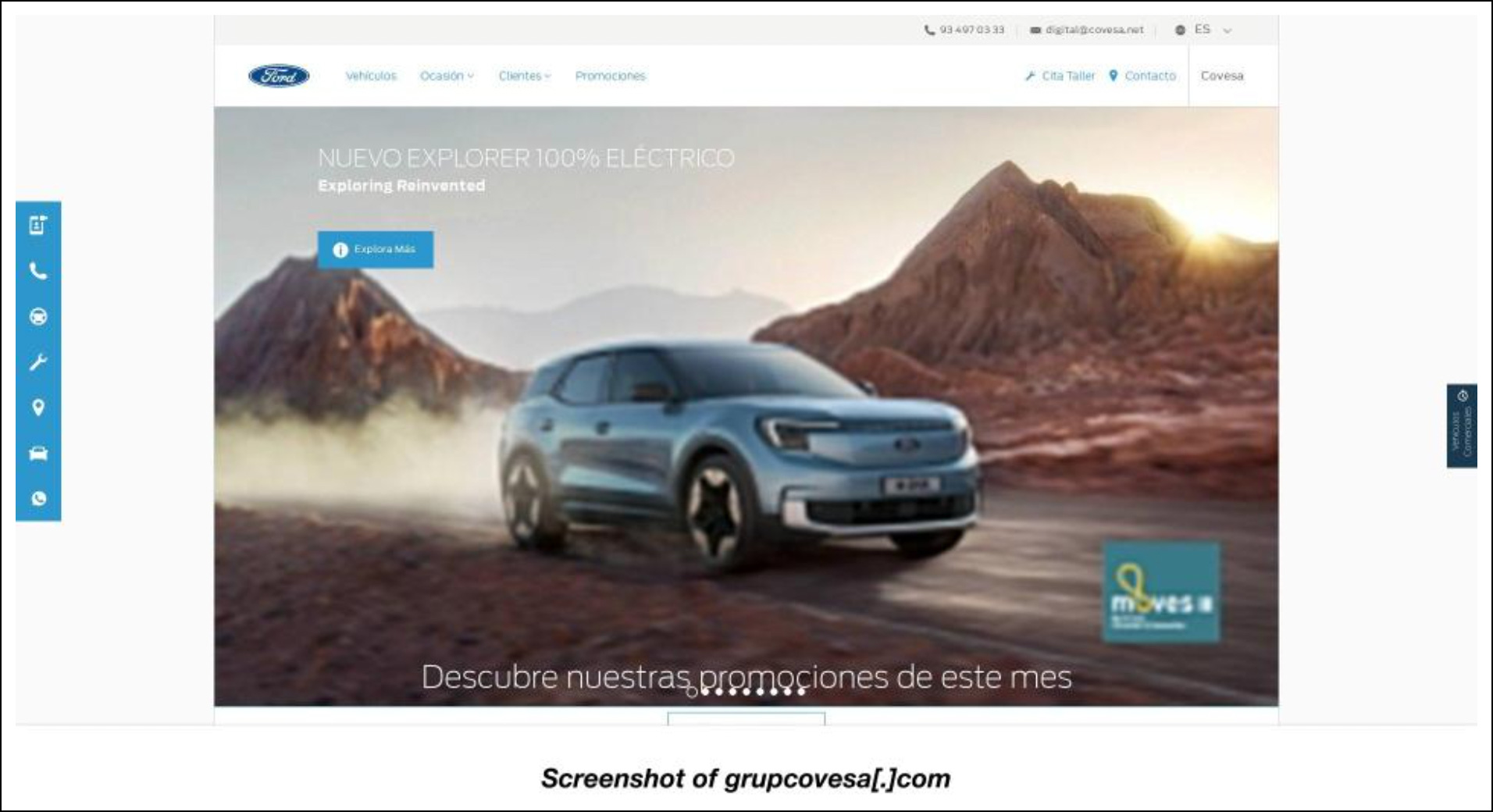
It’s also interesting to note that the site hosted on the IoC grupcovesa[.]com sported the Ford logo even if its registrant isn’t the same as that of ford[.]com, Ford Motor Company’s official website, based on a WHOIS lookup. It could be cybersquatting on the car manufacturer’s popularity and may have been used to lure in Ford customers to unknowingly download LockBit onto their computers. Grupcovesa[.]com was, however, the only one among the IoCs that could be categorized as a potential cybersquatter.
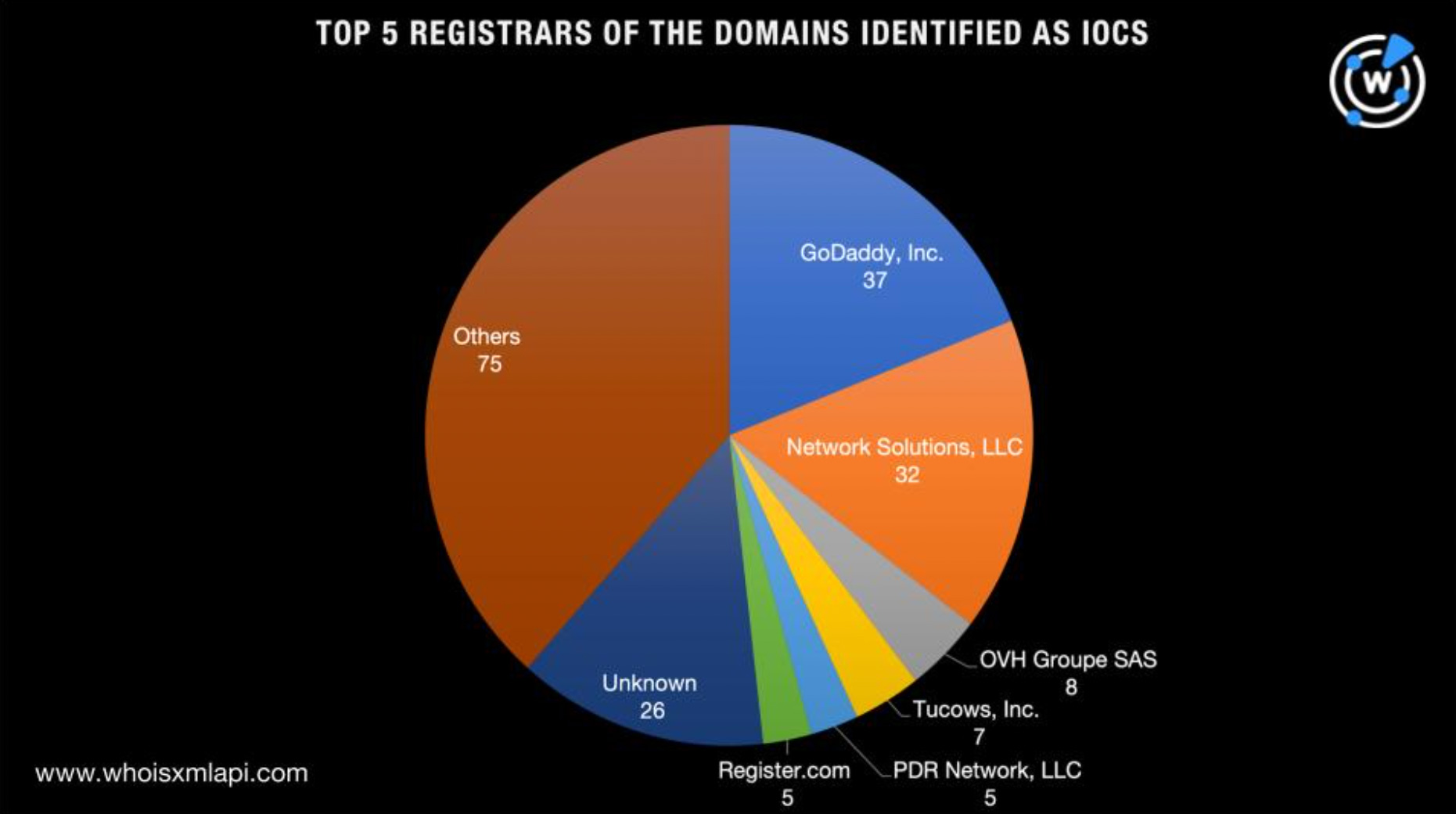
A bulk WHOIS lookup for the domain IoCs also showed they were spread across 58 registrars topped by GoDaddy (37 domains); Network Solutions (32 domains); OVH Groupe SAS (8 domains); Tucows (7 domains); and PDR Network and Register.com (5 domains each).
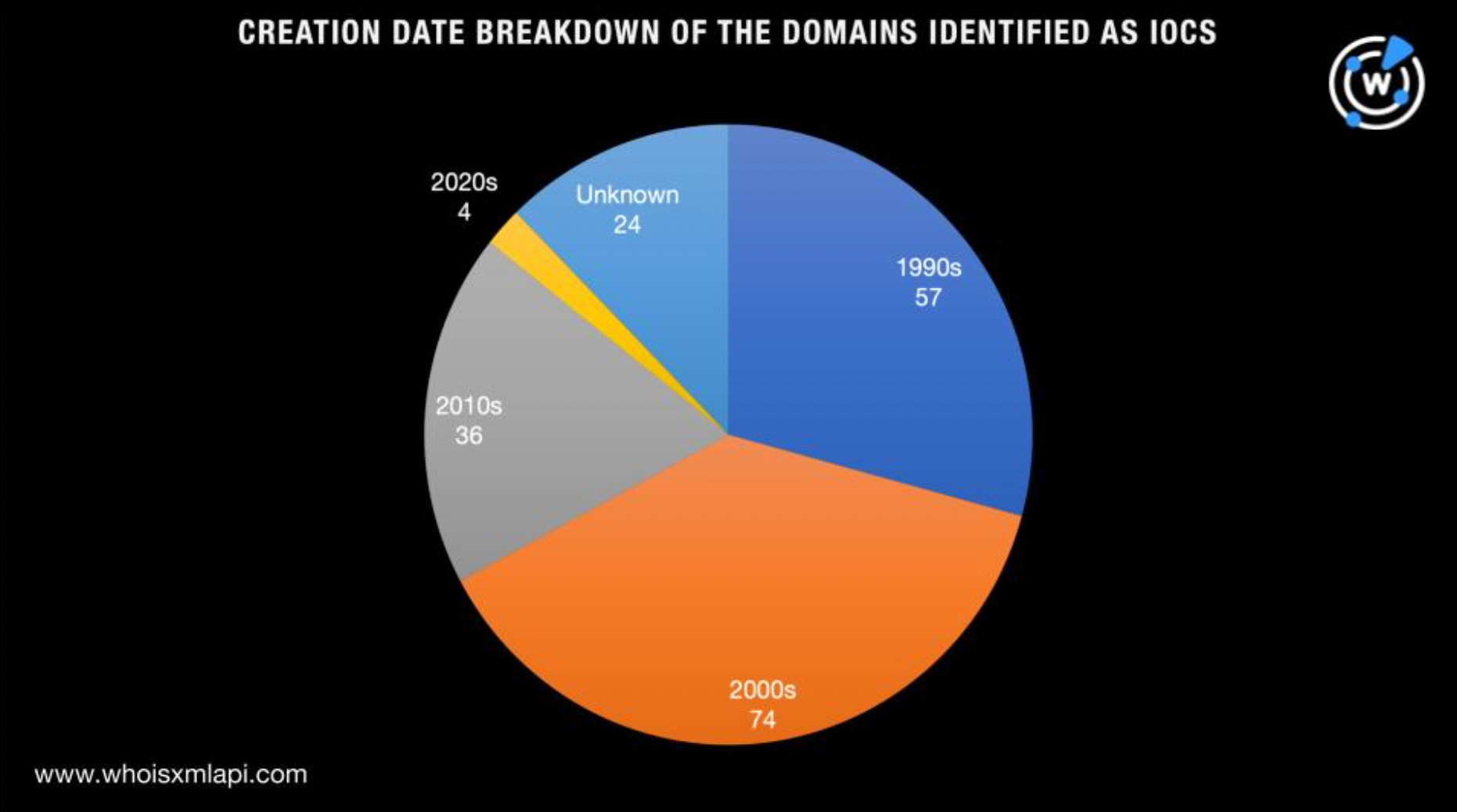
The LockBit operators also didn’t seem to discriminate in terms of domain age since they used a mix of both old and new domains.
A bulk IP geolocation lookup for the three IP addresses identified as IoCs, meanwhile, revealed that they all pointed to a single country—Singapore—even if they were distributed across two ISPs. The Constant Company managed two of the hosts while the remaining one was under Choopa’s control.
To gather as much intelligence on LockBit’s infrastructure and its operators, we performed DNS lookups on the domains identified as IoCs. The 195 domains resolved to 226 unique IP addresses.
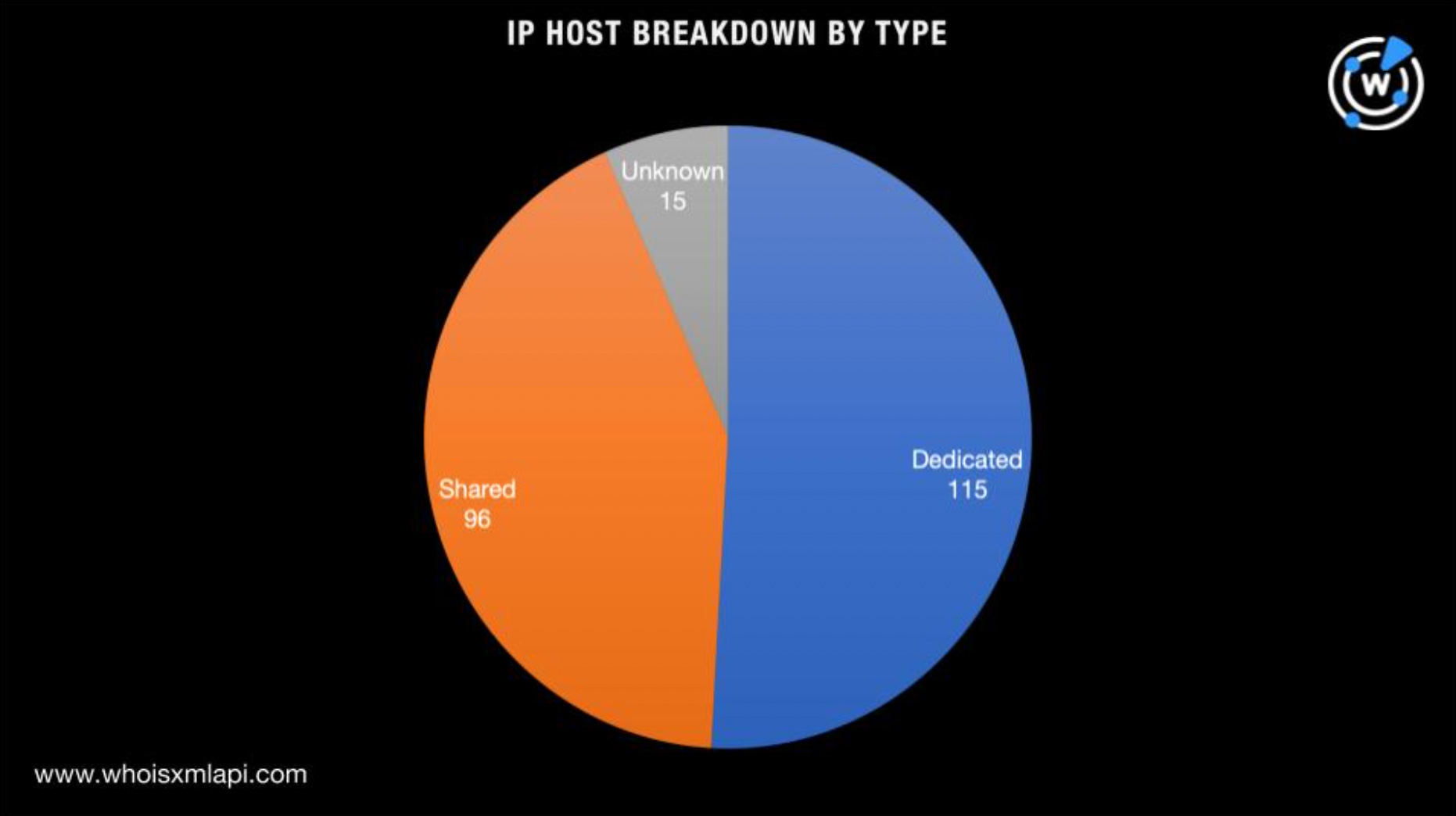
We then subjected the 229 IP addresses—the three that have been identified as IoCs and the additional 226 from our DNS lookups—to reverse IP lookups. A majority of the IP hosts (51%) were seemingly dedicated as they each had less than 300 connected domains while 42% were shared hosts for having more than 300 connected domains each. The remaining 7% of the IP addresses didn’t appear to have connected domains.
Nine of the dedicated IP hosts turned out to be malicious. A bulk IP geolocation lookup for them revealed that most, four to be exact, were geolocated in the U.S.
In addition to the IP host types, our reverse IP lookups also found 6,066 domains that shared the dedicated IP hosts of some of the IoCs. Malware checks then revealed that 16 of them were malicious.
Due to LockBit’s aforementioned connection to SocGholish in the past, we sought to determine if the artifacts we discovered for the two malware left similar DNS traces, if any. Here’s a summary of our comparison.
Overall, therefore, the latest LockBit variant’s connection to SocGholish could be just as the ReliaQuest researchers thought—now nonexistent.
IoC expansion analyses aided by comprehensive DNS intelligence are effective means to identify as many possibly connected artifacts to specific threats as possible. They can also help determine the scale of a specific threat groups’ infrastructure. Our LockBit investigation, for instance, showed that its operators may have favored compromising legitimate domains instead of using newly registered domains (NRDs). It also supported other security researchers’ claim regarding a change in the ransomware group’s distribution tactic. The latest LockBit variant no longer has ties to SocGholish.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byRadix
