


|
||
|
||
Google’s announcement of the launch of the .zip ngTLD was met by a lot of debate. Many believe threat actors could abuse the ngTLD for phishing and other malicious campaigns, primarily since it could be easily confused with the .zip file extension. They weren’t wrong to be concerned since their fear did come to fruition. Shortly after the announcement, phishers began abusing .zip domains.
To help organizations avoid the potential perils that the .zip and similarly confusing ngTLD extensions (i.e., .app, .cab, .cam, .mobi, .mov, .pub, .rip, and .win) may pose, the WhoisXML API research team scoured the DNS for such domains created between 1 January and 31 May 2023 to see if any of them should be considered suspicious and treated with caution.
Our in-depth study covering the ngTLDs registered uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our investigation by obtaining a list of all the currently existing ngTLDs. We then identified which of them could be confused with file extensions (see the table below for the results).
| Possibly Confusing ngTLD | Registry/Sponsor | Application File Extension |
|---|---|---|
| .app | macOS application bundle | |
| .cab | Binky Moon, LLC | Archive file format for Microsoft Windows |
| .cam | CAM Connecting SarL | File created using Autodesk’s Eagle Drawing Editor |
| .mobi | dotMobi (subsidiary of Afilias) | File extension designed especially for e-books but mostly for Amazon Kindle |
| .mov | Video format developed by Apple; an MPEG 4 video container file primarily used with QuickTime | |
| .pub | Proposed by United TLD Holdco Ltd. (no registry specified as owner yet) | Microsoft Publisher document file format |
| .rip | Rightside/Demand Media (United TLD Holdco Ltd.) | Output file of audio files that have been ripped |
| .win | Global Registry Services Limited | Most commonly used for Windows system backup files |
| .zip | File format that can contain multiple files combined and compressed into one file |
Using Domains & Subdomains Discovery, we then collated domains registered from 1 January to 31 May 2023 that ended with the potentially confusing ngTLD extensions in the table above. We grouped the results into those that Google owned and those managed by other registries.
We found 21,035 .app, .mov, and .zip domains. Take a look at the breakdown below.
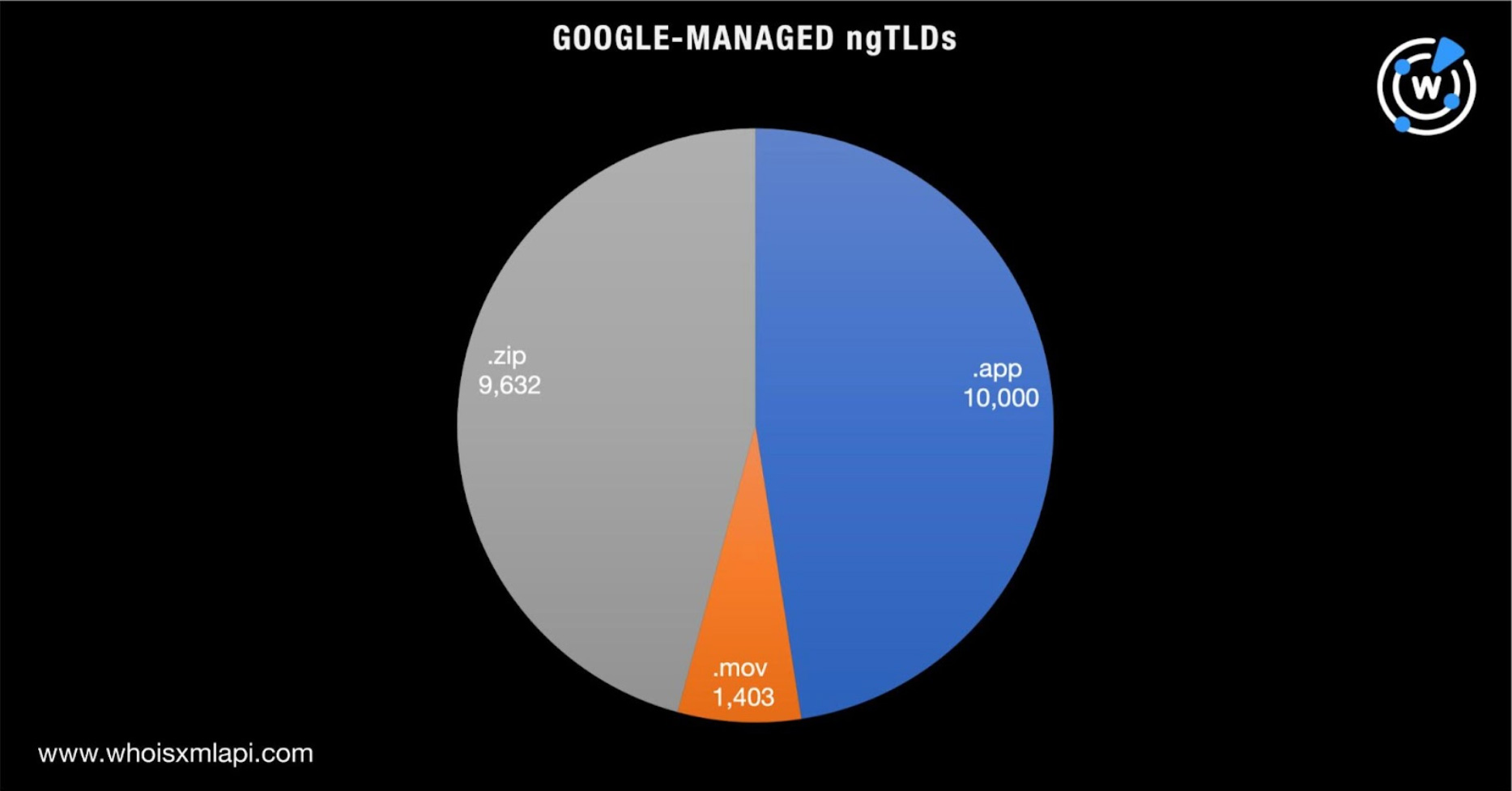
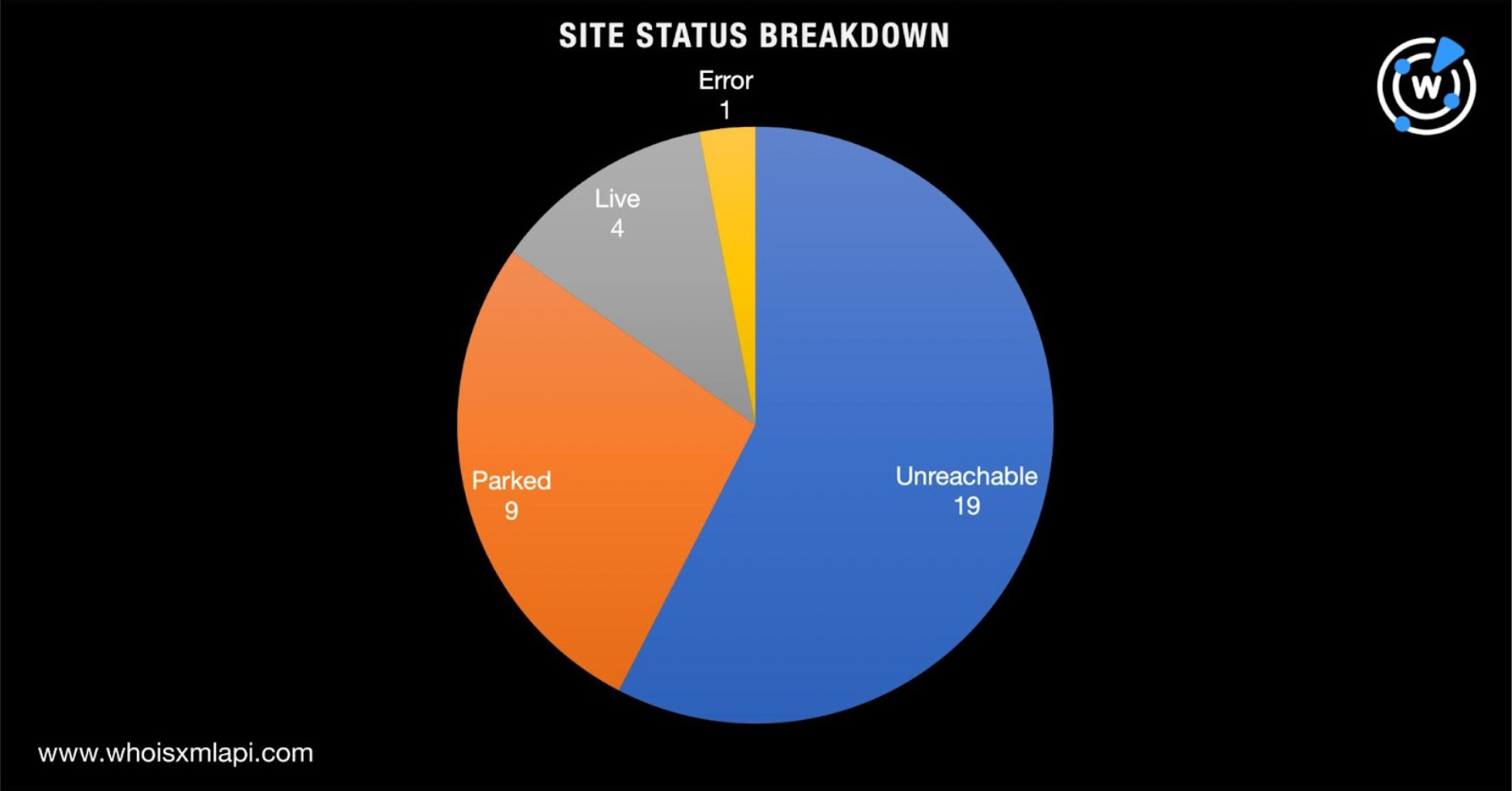
A total of 33 of the domains—26 .app and seven .zip domains—may have already been used in malicious campaigns based on a bulk malware check. A majority of the malware hosts or phishing domains were unreachable (see the chart below for their statuses based on screenshot lookups).
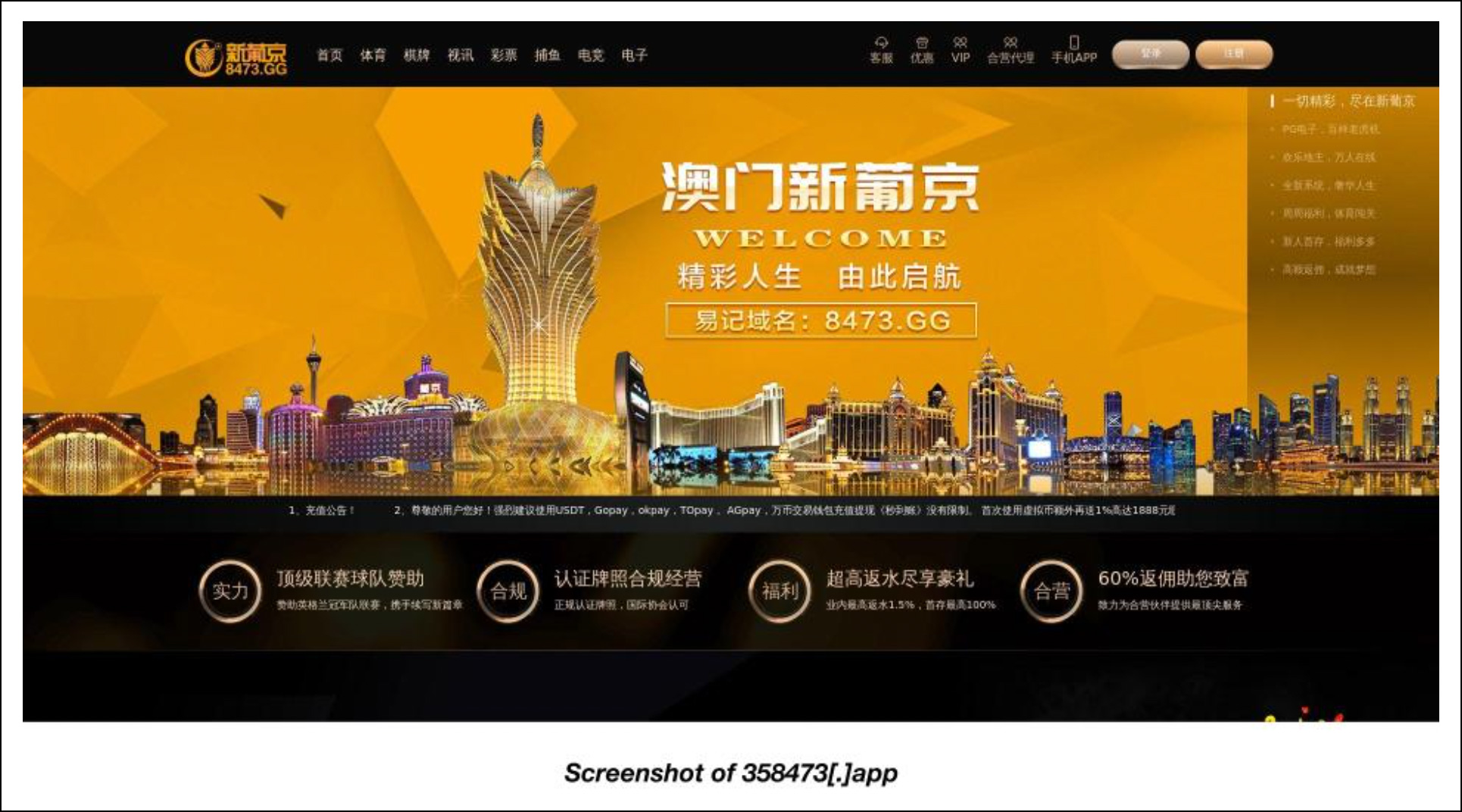
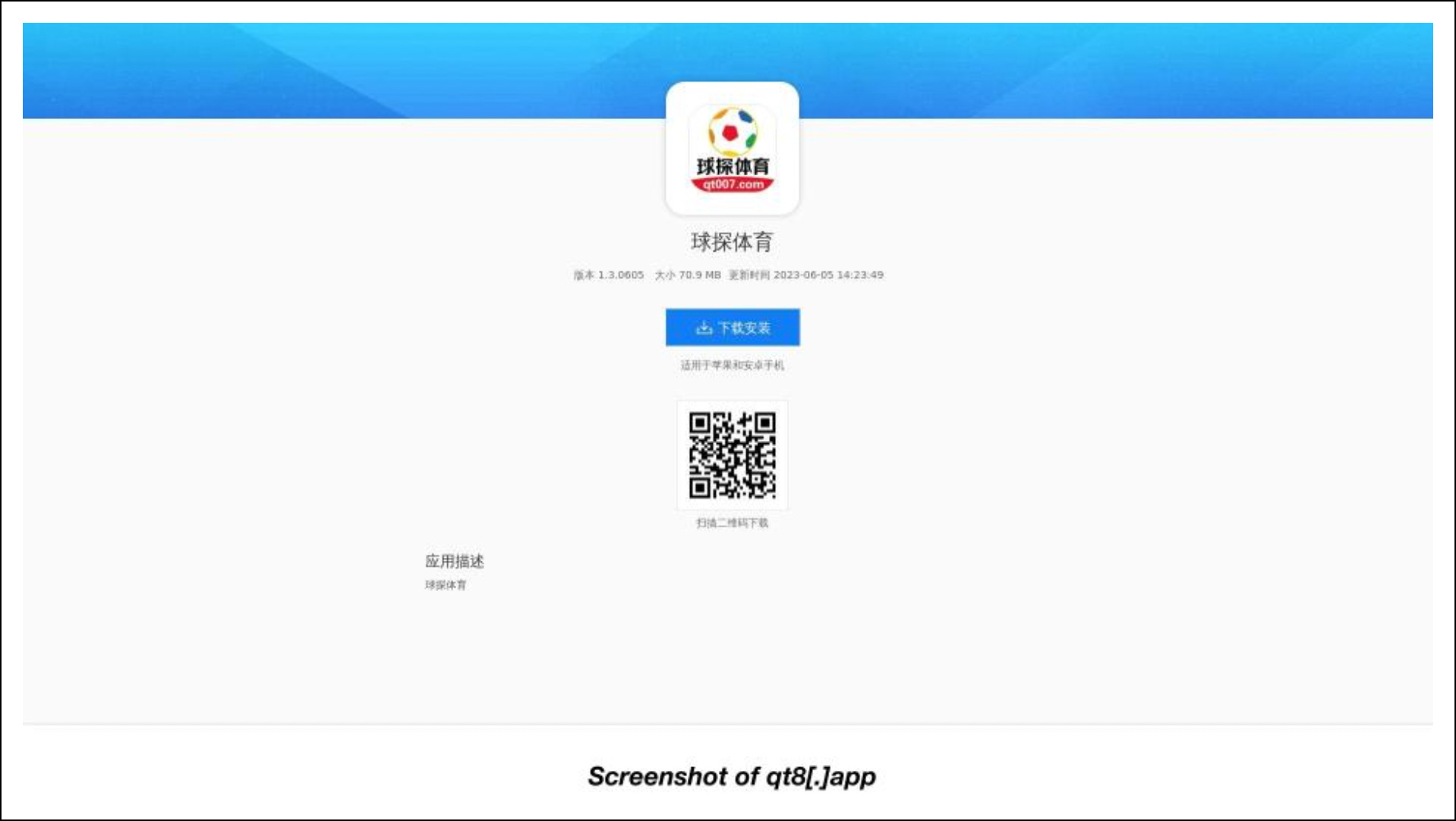
Here are screenshots of three still-live sites hosted on the malicious domains.
ngTLDs Not under Google’s Control
We also found 26,961 .cab, .cam, .mobi, .pub, .rip, and .win domains. Take a closer look at the breakdown below.
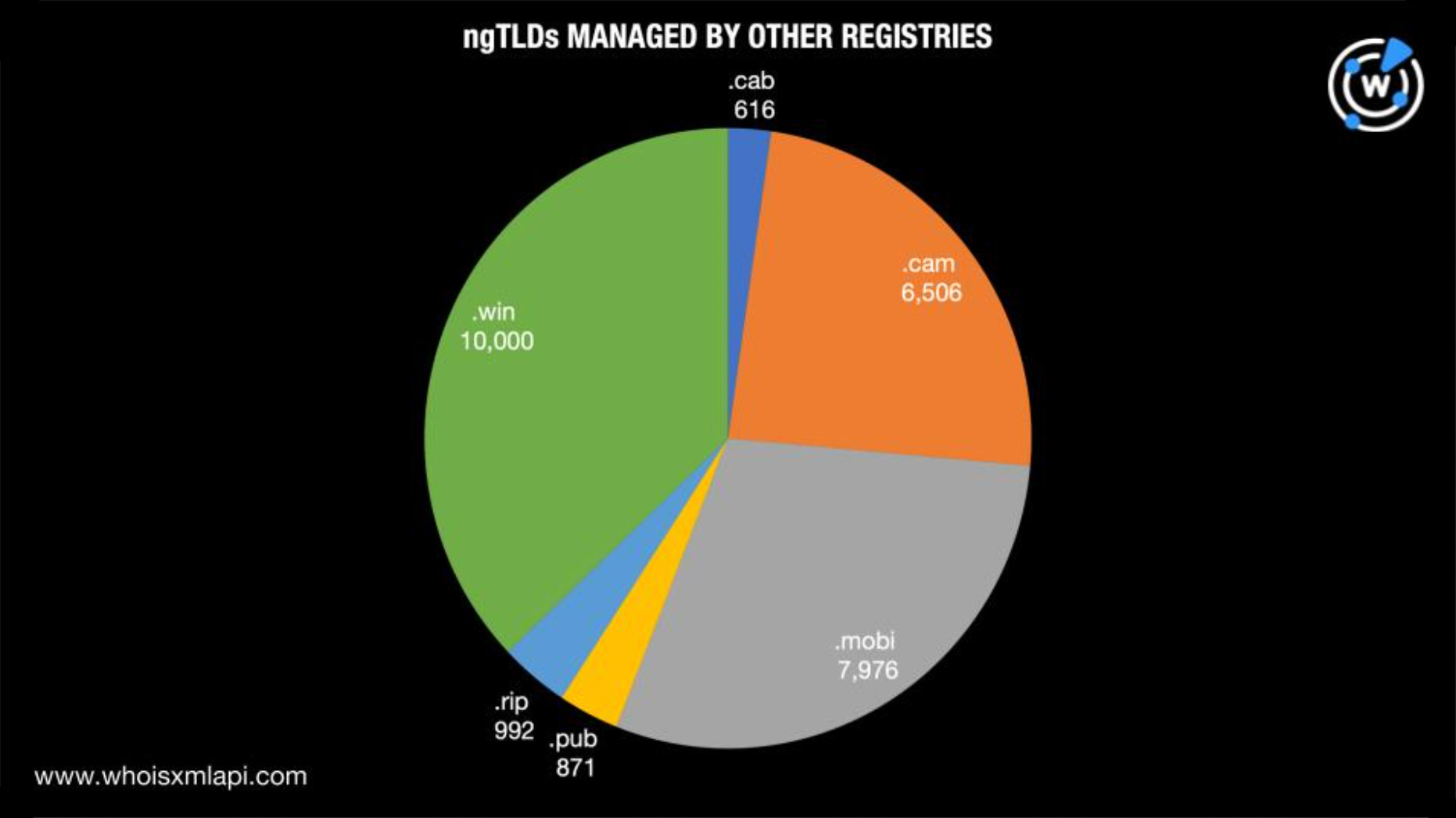
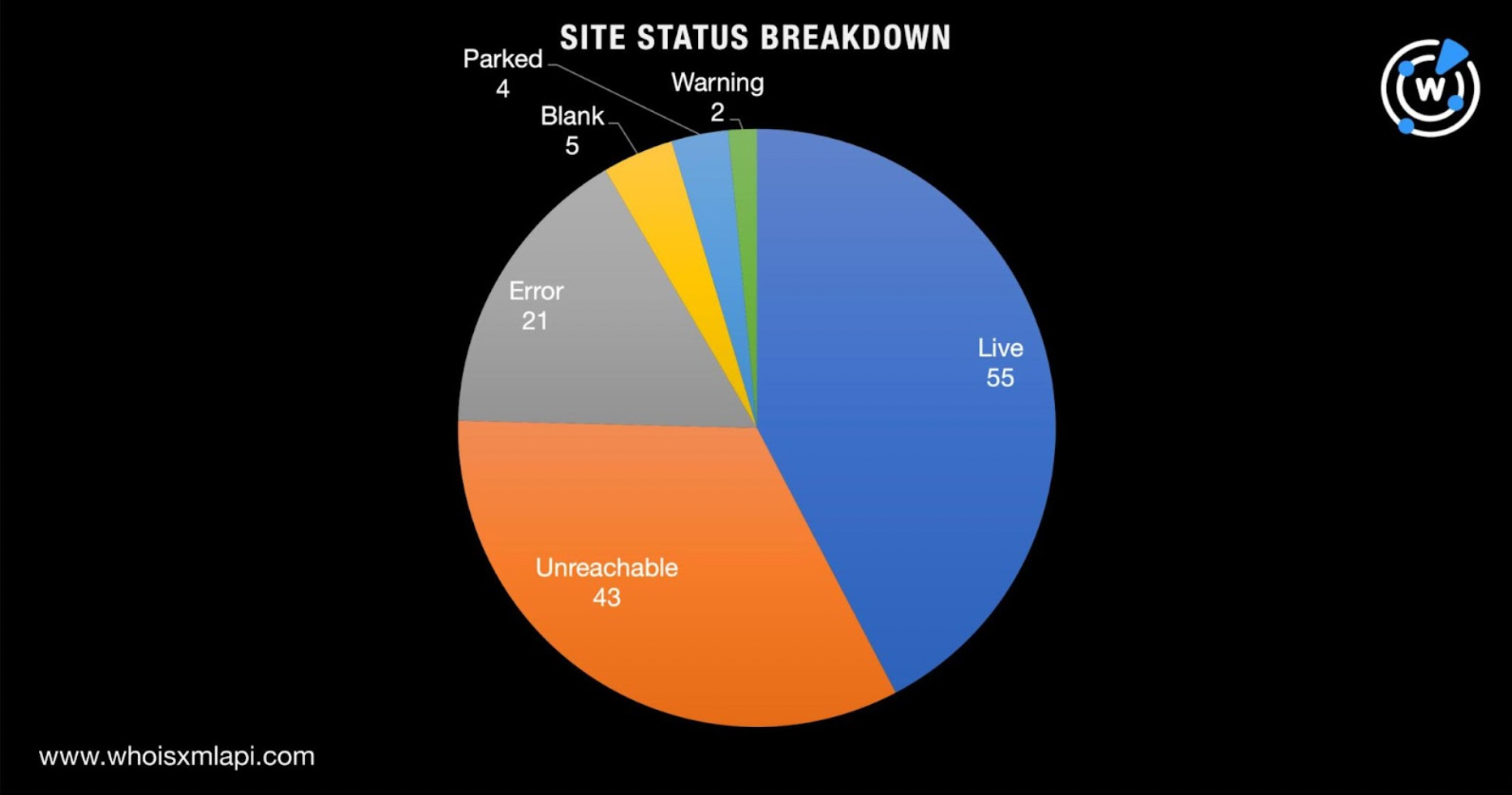
A total of 130 of the domains—one .cab, 49 .cam, 13 .mobi, three .pub, one .rip, and 63 .win domains—may have already been used in malware distribution or phishing attacks . Based on screenshot lookups, a majority of them remained live to date. Take a look at the domain status breakdown below.
Here are three screenshots of the still-accessible sites hosted on 43 of the malicious domains.
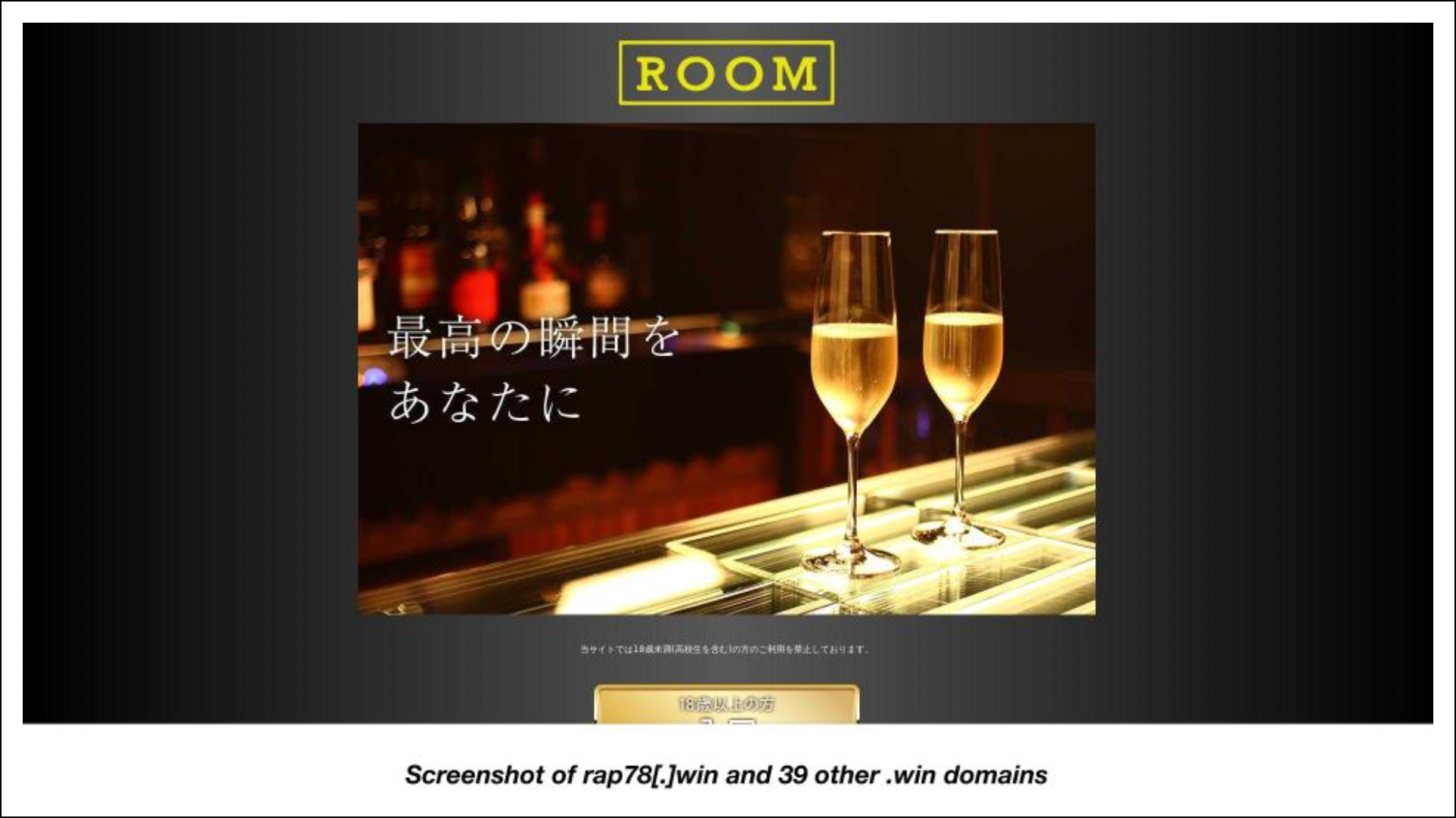
We discovered that 40 malicious domains used the same content and similarly constructed strings comprising random number-and-letter combinations, hinting that they could have been used for the same malware-instigated attack.
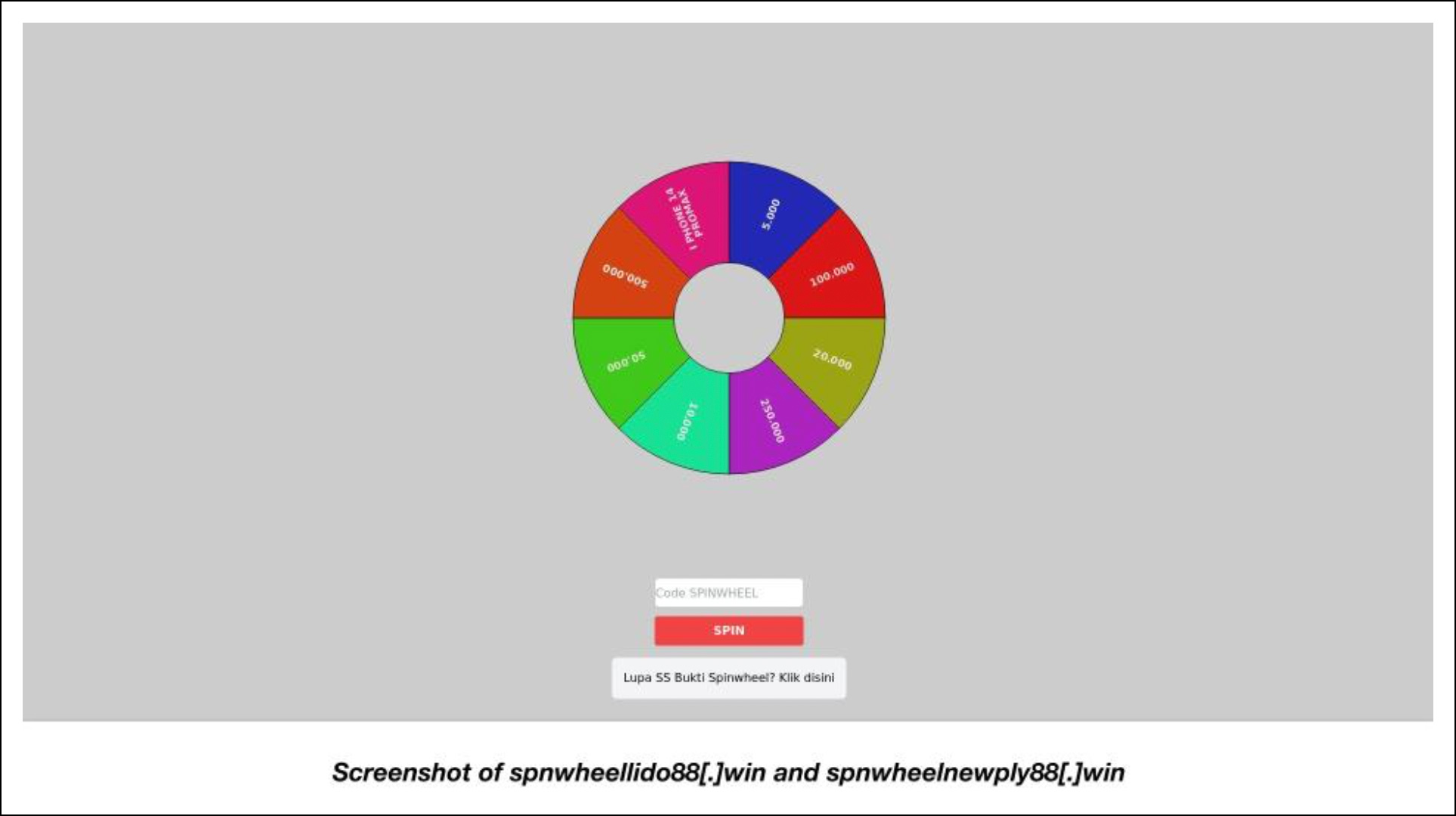
Like the first set of malicious domains under this section, the last two domains’ use of the same content and TLD extension could indicate they figured in the same malicious campaign. Add to that the fact that they both contain the exact string spnwheel.
Next, we collated all of the malicious possibly confusing ngTLD domains to further investigate them. We ended up with a list of 163 .app, .cab, .cam, .mobi, .pub, .rip, .win, and .zip domains.
A bulk WHOIS lookup showed these results:
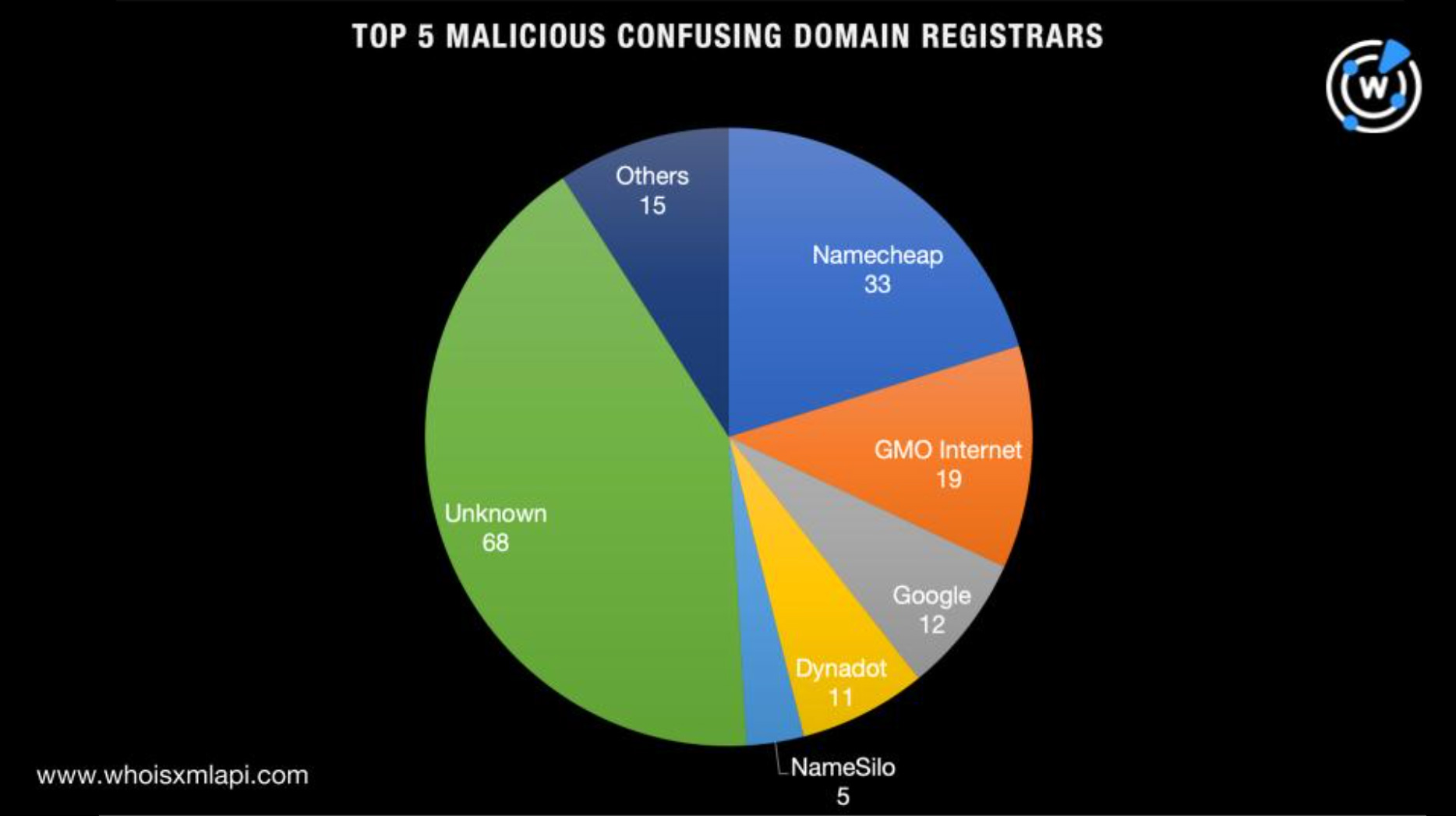
A bulk IP geolocation lookup for them, meanwhile, revealed that:
As a final step to find as many potential threat artifacts as possible, we subjected the four malicious IP hosts to reverse IP lookups. They led to the discovery of 137 additional domains, 32 of which have been categorized as malware hosts.
Our DNS deep dive into domains under ngTLDs that could be easily confused with commonly used file name extensions like .zip found that many could already have been weaponized by threat actors.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byCSC

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byIPv4.Global
