


|
||
|
||
The first time the BlackCat ransomware gang breached Reddit’s network last February, they phished an employee to hack into the target network. This time, according to a ReversingLabs detailed report, they successfully dropped BlackCat onto the company’s systems and threatened to release its data if it fails to pay the ransom.
In WhoisXML API’s bid to make the Internet more transparent and safer for all users, we expanded the list of indicators of compromise (IoCs) comprising 13 IP addresses published on 4 June 2023. Our comprehensive DNS searches for traces the threat group may have left behind uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
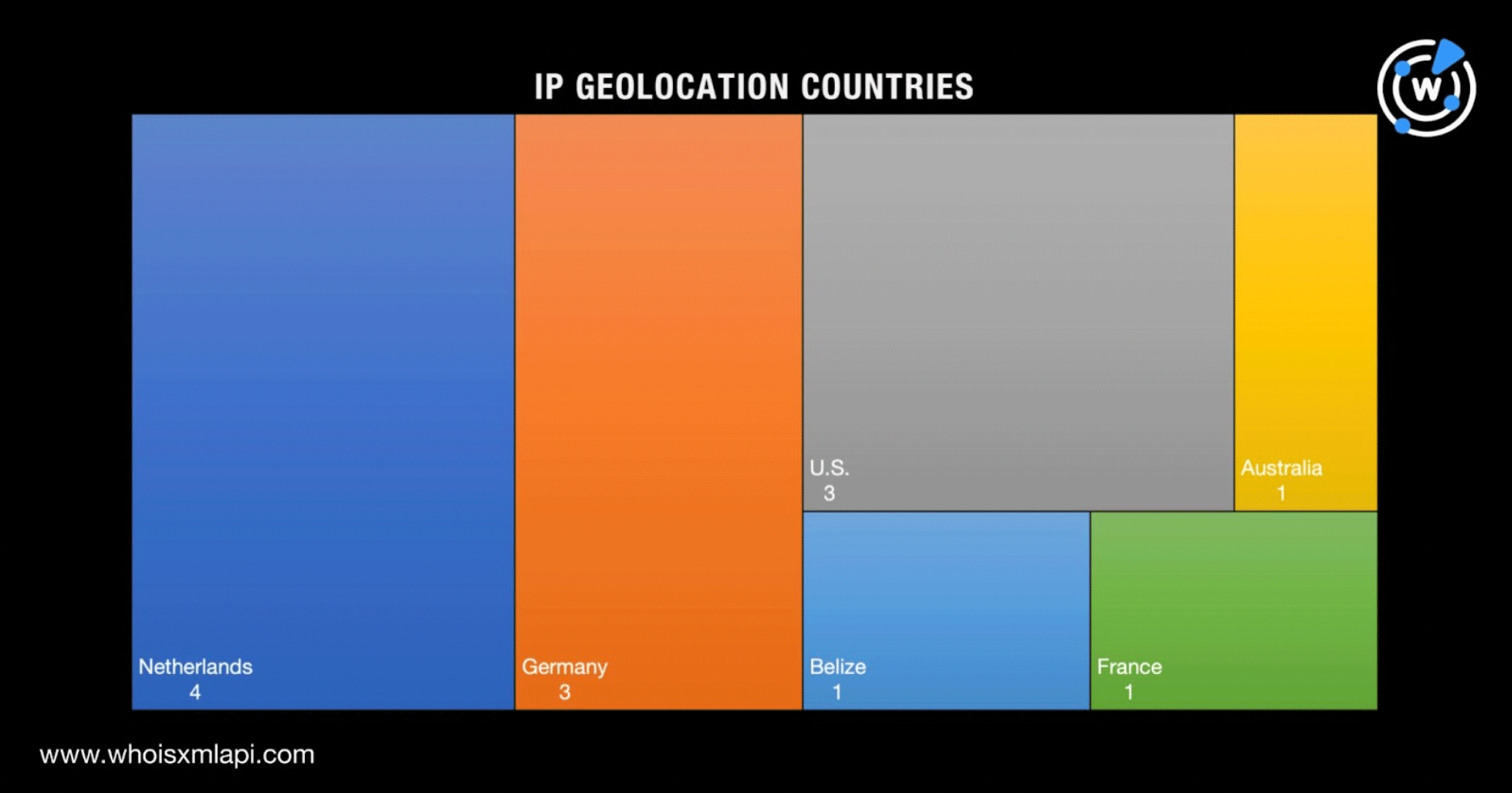
A bulk IP geolocation lookup for the IoCs revealed that they were geographically distributed across six countries led by the Netherlands, which accounted for four of the IP addresses. Germany and the U.S. tied in second place, accounting for three IP addresses each. Australia, Belize, and France completed the list, each accounting for one IP address.
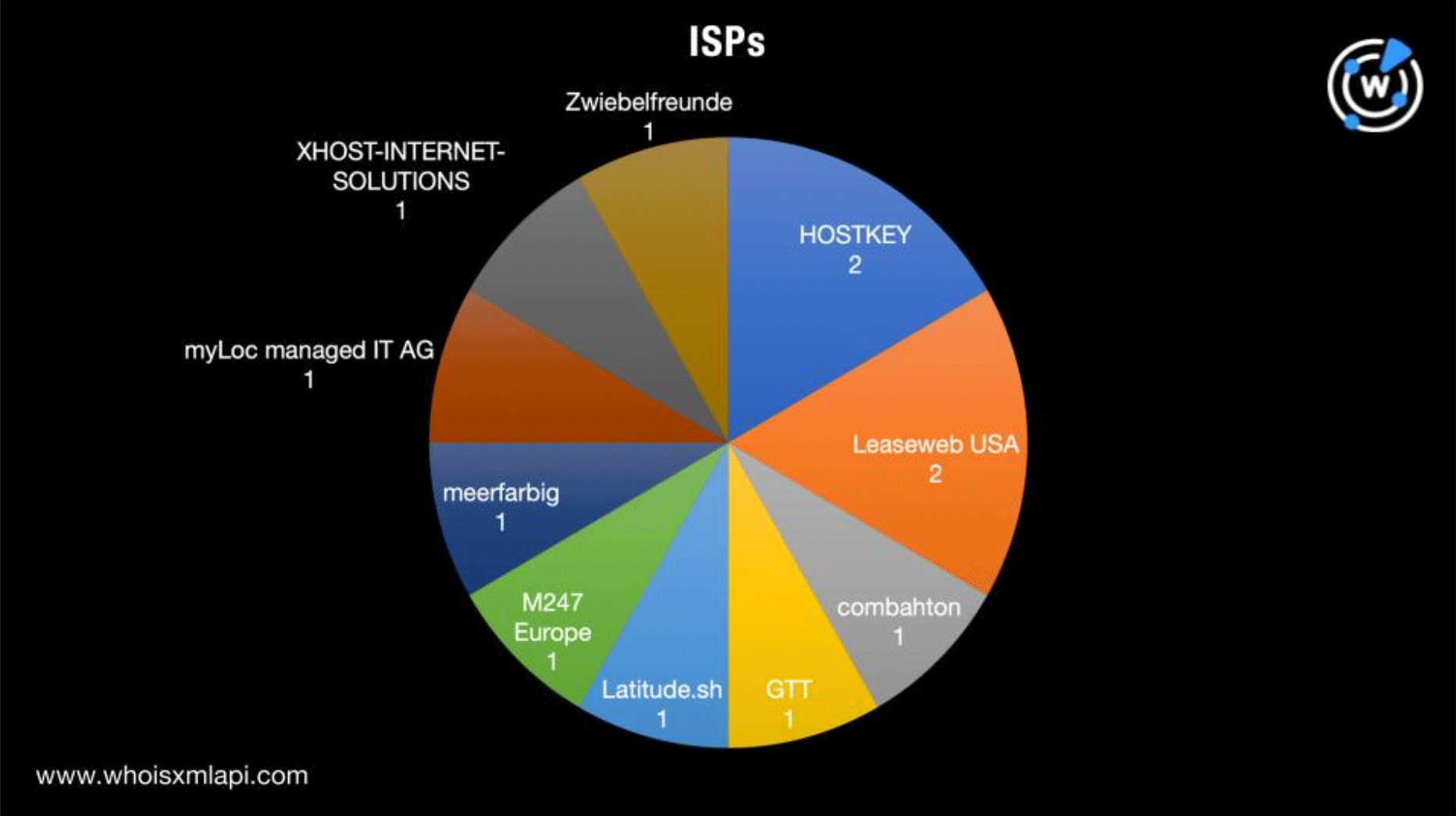
Further scrutiny showed the IoCs were spread across 10 ISPs led by HOSTKEY, Leaseweb USA, and M247 Europe, which accounted for two IP addresses each. Combahton, GTT, Latitude.sh, Meerfarbig, myLoc managed IT AG, Xhost Internet Solutions, and Zwiebelfreunde rounded out the list, each accounting for one IP address.
We began our DNS deep dive with reverse IP lookups for the IoCs, which allowed us to determine that two of them were dedicated hosts. Together, 89[.]44[.]9[.]243 and 185[.]220[.]102[.]253 hosted three domains. While two out of three of the IP-connected domains continued to host live content, one turned out to be a Tor exit node. The other two appeared to be cybersquatting properties based on their domain names alone.
The first, off365logs[.]online, could be passing itself off as a Microsoft-owned Office 365 page though it’s parked at present. Its WHOIS record, however, didn’t bear any similarity to that of microsoft[.]com. In particular, it didn’t share the legitimate domain’s registrar and registrant email address.
The second, secure-rbcbank[.]net, could be pretending to belong to Canada-based RBC Bank. Like the first potential cybersquatter, it, too, didn’t have the same WHOIS record details as rbcbank[.]com. Its screenshot also shows a Kahoot! login page.

Both potentially cybersquatting sites aren’t considered malicious to date but threat actors could easily weaponize them for attacks targeting Office 365 users and RBC Bank customers. It’s also interesting to note that secure-rbcbank[.]net’s current WHOIS record contained an unredacted registrant email address that may help security researchers and law enforcement agencies conduct more in-depth investigations.
To gather more artifacts, we looked for domains containing the names of the brands that could also belong to the threat actors behind BlackCat ransomware.
Our Domains & Subdomains Discovery searches for domains containing the string office365logs, off365, or office365 created since 1 January 2023 that could be weaponized to target Office 365 users allowed us to uncover 437 such web properties. A bulk WHOIS lookup for the Office 365 string-connected domains revealed that only three of them could be publicly attributed to Microsoft based on their registrant email address. A bulk malware check, meanwhile, showed that 53 of them were tagged as malicious. Here are other interesting findings:
Next, we performed a similar search for domains containing the string rbcbank created in the same period and found 19 such web properties. Unlike some of the Office 365 string-connected domains, none of them could be publicly attributed to RBC Bank. Also, two of them have been tagged as malicious based on a bulk malware check. Here are other noteworthy findings:
Further scrutiny of the latest BlackCat attack on Reddit led to the discovery of 460 yet-unpublished artifacts with close IP connections to and string similarities with the IoCs. A total of 55 of the newly found domains may have already figured in cyber attacks or phishing campaigns, given that they are currently being detected as malicious by a malware checker. A huge majority of the artifacts could also easily be weaponized for other attacks specifically targeting Office 365 users and RBC Bank customers.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byWhoisXML API
