


|
||
|
||
Even solutions meant to enhance security can sometimes fall prey to the best cyber attackers. That’s what happened to JumpCloud, a cloud-based directory service platform designed to centralize and simplify identity access management (IAM).
SentinelOne researchers analyzed the supply chain attacks and published 32 JumpCloud attack indicators of compromise (IoCs). WhoisXML API, in an effort to identify additional artifacts, if any, performed an IoC list expansion that uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
The SentinelOne JumpCloud supply chain attack analysis identified 13 domains and 19 IP addresses as IoCs.
As a first step, we subjected the 13 domains to a bulk WHOIS lookup, which revealed that:
It’s also interesting to note that the website categorization lookup results for the domains identified as IoCs classified all 13 as malware sites.
Next, we performed a bulk IP geolocation lookup for the 19 IP addresses identified as IoCs and found that:
The following image compares the domain registrant and IP geolocation countries of the IoCs. Only the U.S. consistently appeared as a registrant and IP geolocation country although the number of IP addresses and domains didn’t match.
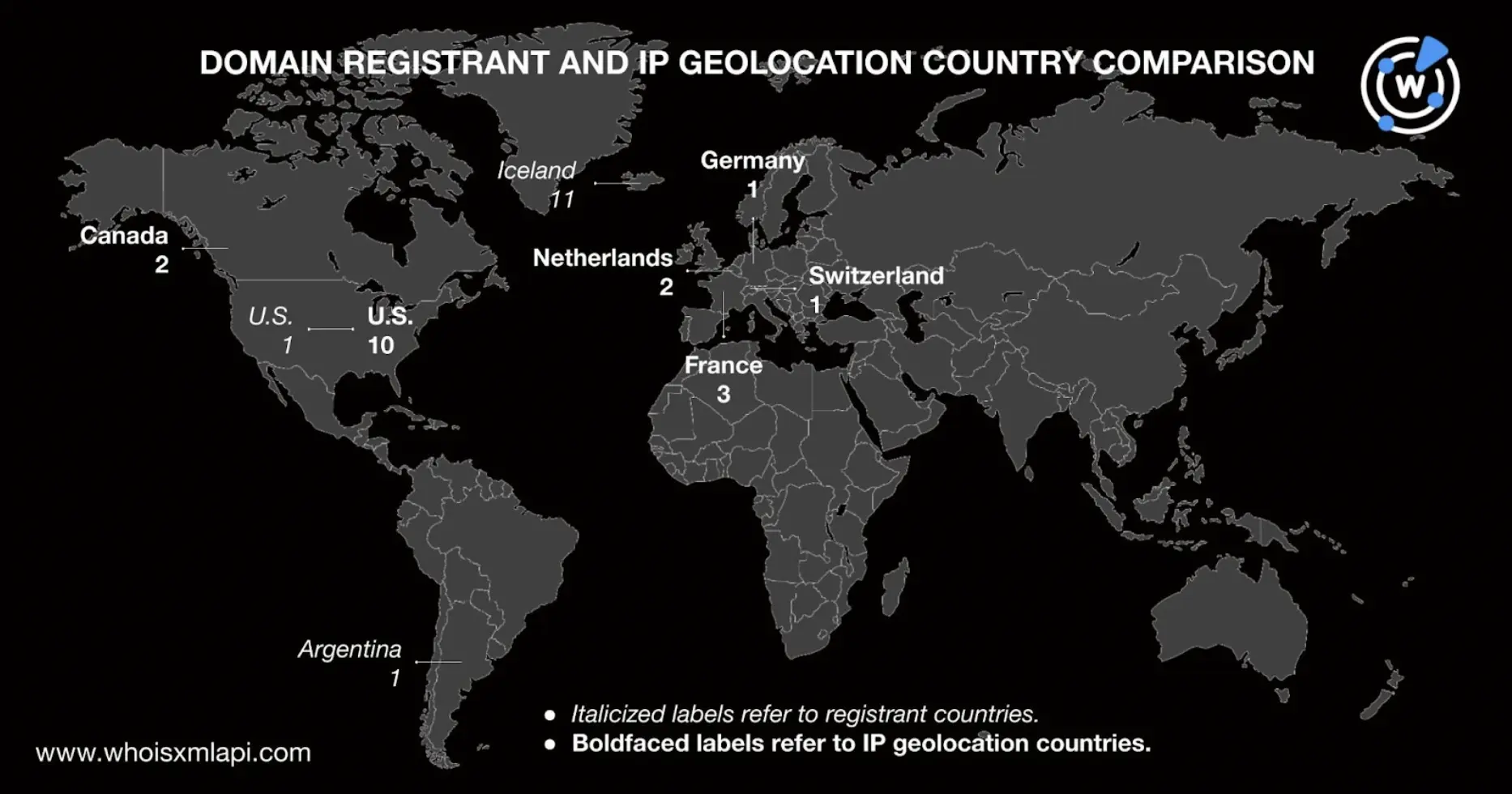
We began our DNS deep dive with DNS lookups, which showed that only two of the domains identified as IoCs continued to resolve to one IP address each—toyourownbeat[.]com to 192[.]185[.]5[.]189 and primerosauxiliosperu[.]com to 162[.]241[.]248[.]14. These IP resolutions, however, were already part of SentinelOne’s IoC list.
Next, reverse IP lookups for the 19 IP addresses identified as IoCs revealed that eight of them were dedicated hosts, one was possibly dedicated, and another one was shared. Three didn’t have active resolutions.
Our search also showed that the nine dedicated and possibly dedicated IP hosts were shared by 145 other domains. One of them, now unreachable—npmaudit[.]com—was classified a malware host by a bulk malware check.
A closer look at the domains identified as IoCs allowed us to identify three unique strings—centos, datadog, and zscaler—that coincided with popular brand names shown in the table below.
| STRING | ASSOCIATED BRAND | DESCRIPTION |
|---|---|---|
| centos | CentOS | CentOS is a discontinued free, open-source, and community-supported Linux computing platform functionally compatible with its upstream source—Red Hat Enterprise Linux. |
| datadog | Datadog | Datadog is an observability service for cloud-scale applications that enables server, database, tool, and service monitoring via a SaaS-based data analytics platform. |
| zscaler | Zscaler | Zscaler is a cloud security company headquartered in San Jose, California that offers enterprise cloud security services. |
We used the above-mentioned strings as Domains & Subdomains Discovery search terms that led to the discovery of 392 domains.
While none of them were categorized as malicious after being subjected to a bulk malware check, many of them couldn’t be publicly attributed to the companies. We used the WHOIS record data points in the table below to determine domain ownership. Note that since Datadog’s WHOIS record didn’t indicate any readily identifiable WHOIS data point, we couldn’t make accurate record comparisons for it to determine brand-containing domain ownership.
| STRING | COMPANY | OFFICIAL DOMAIN NAME | WHOIS RECORD DETAIL |
|---|---|---|---|
| centos | CentOS | centos[.]org | Registrant organization:Red Hat, Inc. |
| zscaler | Zscaler | zscaler[.]com | Registrant organization:Zscaler, Inc. |
Our bulk WHOIS lookup and record comparison with the brand name owners’ official websites showed that 93% didn’t share the same WHOIS record data points, making them publicly unattributable to two of the legitimate companies left on our list. Many of the brand-containing domains could be owned by potential cybersquatters or even cyber attackers waiting for a chance to weaponize them.
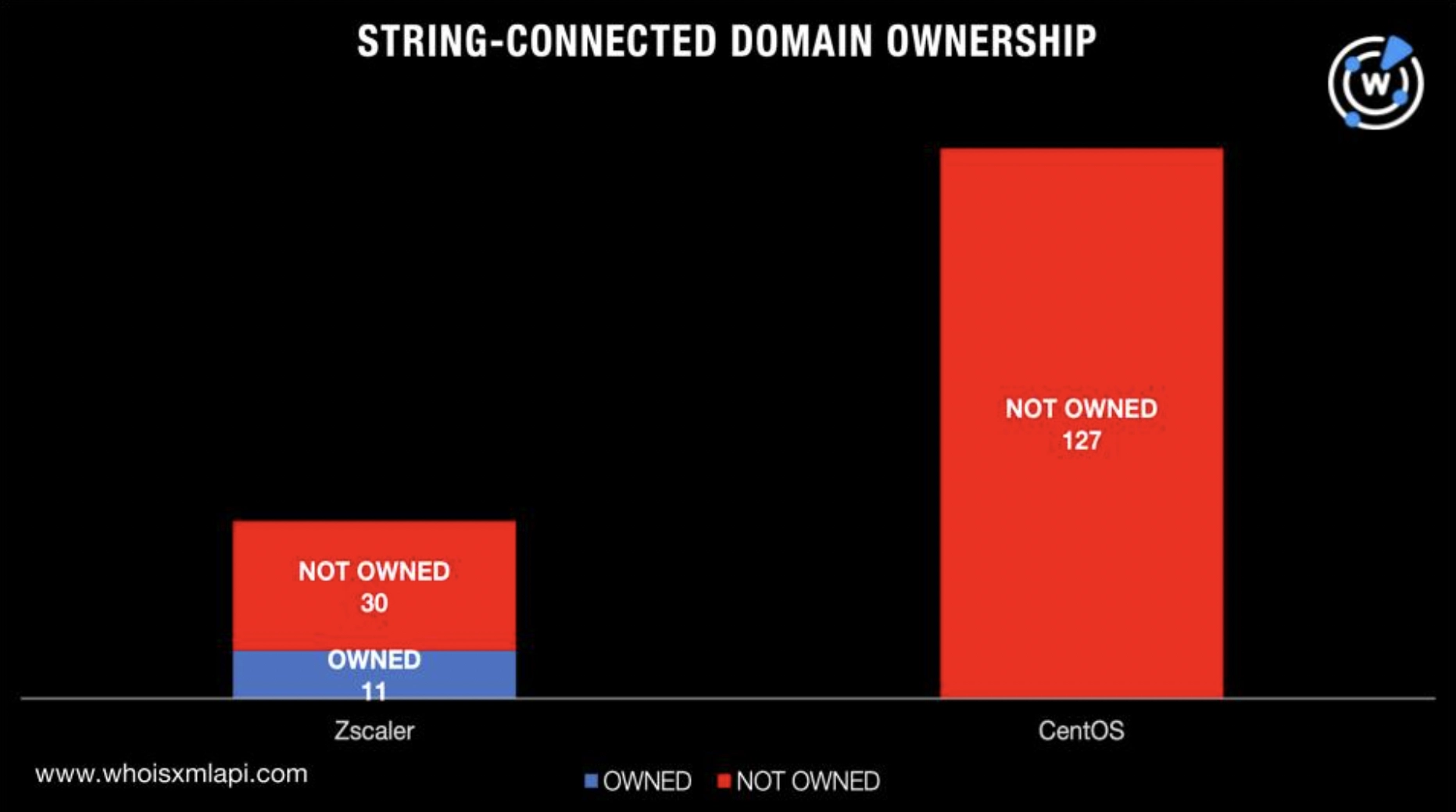
Our IoC list expansion analysis for the JumpCloud supply chain attacks found that their perpetrators could have 145 IP-connected domains they could weaponize for future campaigns. It also revealed that threat actors could potentially utilize 189 look-alike domains for attacks zooming in on CentOS, Datadog, and Zscaler users or the solution developers themselves, especially since 93% of the centos- and zscaler-containing domains couldn’t be publicly attributed to the solutions developers.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byVerisign

Sponsored byCSC

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byDNIB.com
