

|
||
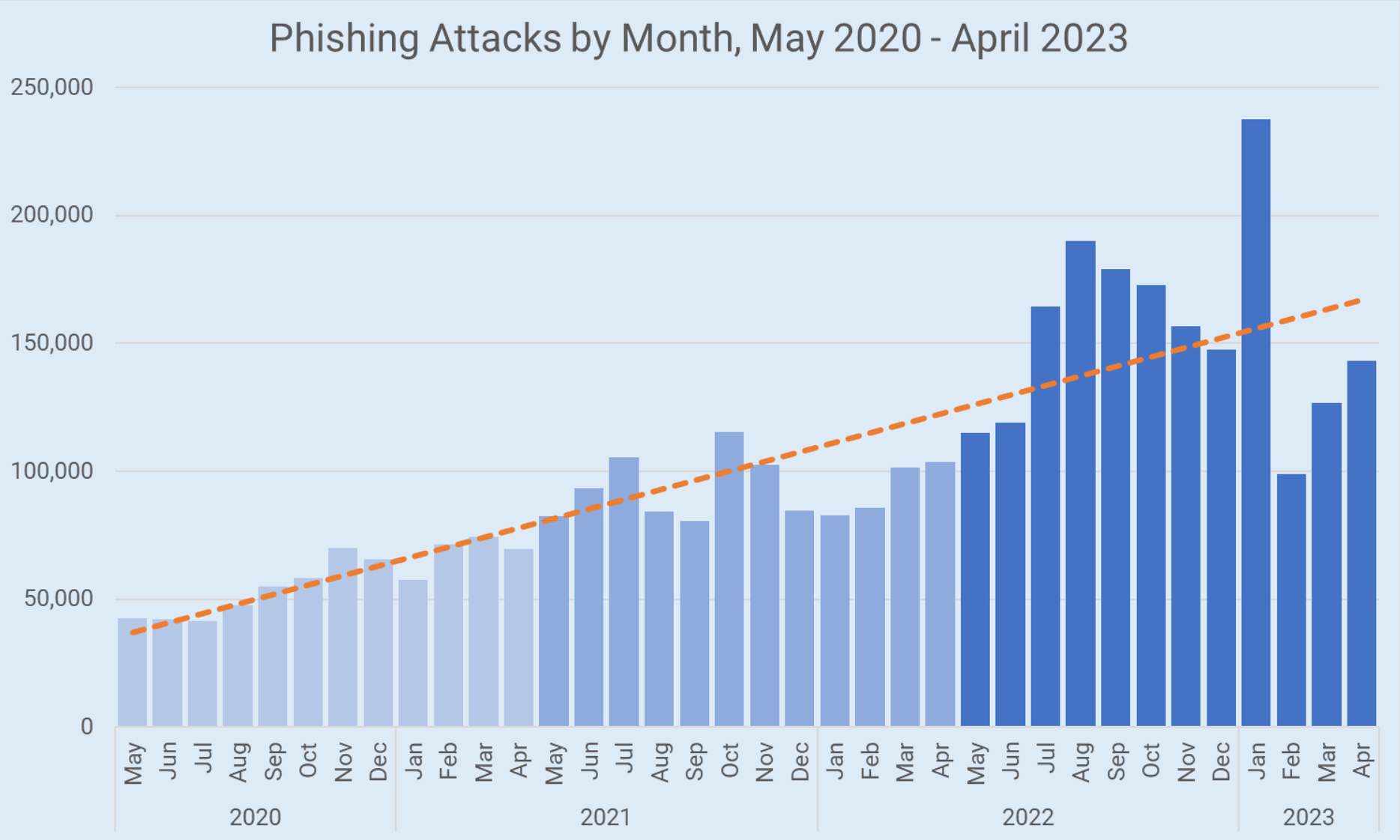
The alarming rise of phishing attacks has been underscored by a recent study “Phishing Landscape 2023: An Annual Study of the Scope and Distribution of Phishing conducted” by the Interisle Consulting Group, revealing a tripling of such attacks since May 2020. Despite efforts by companies and policymakers to combat this cybercrime, the data suggests that the prevailing strategies are ineffective and worsening each year.
The study calls for a “better strategy.” It calls for a renewed and coordinated approach involving proactive policy regimes, government-backed anti-phishing strategies, and legal action against organizations facilitating these attacks. “We call on the players who are in positions to disrupt the phishing supply chain: the global domain and web hosting industries, governments, and in the extreme, the parties most adversely affected by phishing.”
Data Insights
The study, which analyzed over six million phishing reports collected from May 2022 to April 2023, identified more than 1.8 million unique phishing attacks. The annual increase in attacks during this period was 65% compared to the previous study period (May 2021 to April 2022), and more than one million unique domain names were reported for phishing, the highest since observations began in May 2020.
Notably, new generic top-level domains (gTLDs) hosted a disproportionate and growing share of phishing domains, despite representing only 8% of registered domain names worldwide. Malicious domain name registrations were the most common method used by phishers, emphasizing the need for the domain name industry to prioritize the prevention and rapid takedown of these domains.
Moreover, the study revealed that more than 16% of all phishing attacks were launched from phishing pages hosted at subdomain service providers, with 80% of those attacks perpetrated using just eight subdomain service providers. This illustrates the potential for significant harm that can be created by abusing services of this type.
In a positive development, the cessation of registrations by Freenom in January 2023 led to its country-code top-level domains (ccTLDs) ceasing to be a resource for new phishing domains. Previously, Freenom domains were used for 14% of all phishing attacks worldwide.
The study also found that phishers prefer to host their websites in the US, with 42% of all phishing attacks concentrated in just five US-based hosting networks.
Bottom line: The current phishing mitigation strategy is not working, as evidenced by the persistent and growing tide of abuse. To stem this tide, the group says effective mitigation measures and incentives are needed for organizations that, wittingly or not, facilitate cybercriminal activity. Coordination, cooperation, and consistent action across a broad range of stakeholders and actors in the phishing supply chain are essential to making a significant impact on phishing. With cybercriminals constantly evolving their tactics, it is crucial that efforts to combat phishing are proactive, coordinated, and adaptive.
Sponsored byVerisign

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byCSC
