


|
||
|
||
APT41, also known as “Winnti,” “BARIUM,” or “Double Dragon,” is an APT group said to originate from China. Having been active since 2012, APT41 rose to infamy by successfully launching targeted cyber espionage attacks on government agencies and private companies worldwide.
Lookout most recently discovered that the APT group employed at least two mobile spyware—WyrmSpy and DragonEgg—to siphon secrets off their chosen targets. The researchers believe the two spyware were linked to APT41 despite the fact that five cyberspies believed to be part of the threat group have already been caught. WhoisXML API thus sought to find DNS ties between them.
Using the five WyrmSpy IoCs Lookout identified as jump-off points, we uncovered eight domains containing the strings win10 + microsoft and andropwn, akin to two of the domains identified as IoCs.
Our expansion analysis of the list of seven DragonEgg IoCs, meanwhile, led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
In an attempt to determine if WyrmSpy and DragonEgg were indeed related to APT41, we first sought to find DNS traces of the APT group’s published IoCs. While these were publicized in 2022, we only need to determine their origins for comparison with the more recently publicized mobile spyware IoCs.
A bulk WHOIS lookup for the three domains identified as APT41 IoCs showed that:
A bulk IP geolocation lookup, meanwhile, for the two IP addresses identified as APT41 IoCs revealed that:
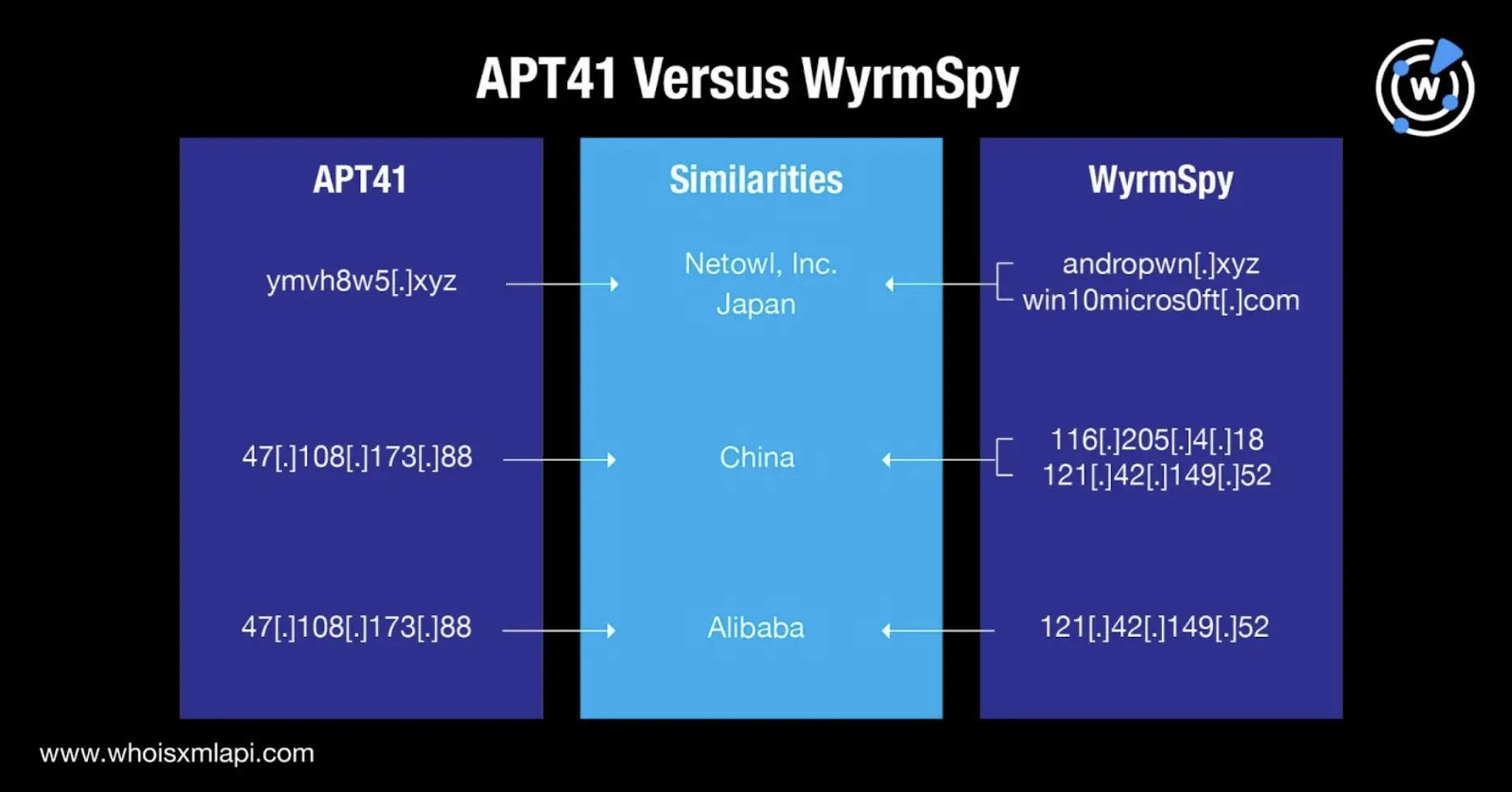
To identify commonalities between APT41 and WyrmSpy, we first subjected the three domains identified as WyrmSpy IoCs—win10micros0ft[.]com, andropwn[.]xyz, and umisen[.]com—to a bulk WHOIS lookup that led to these discoveries:
Even though andropwn[.]xyz and win10micros0ft[.]com were registered in Japan (not China where the group is believed to originate), they did share similarities with the APT41 IoC ymvh8w5[.]xyz. Umisen[.]com, meanwhile, was registered in China, believed to be APT41’s homebase.
Next, a bulk IP geolocation for the two IP addresses identified as WyrmSpy IoCs – 116[.]205[.]4[.]18 and 121[.]42[.]149[.]52 – also pointed to China. The IP address 121[.]42[.]149[.]52 was administered by Hangzhou Alibaba Advertising Co. similar to Alibaba Cloud-managed APT41 IoC 47[.]108[.]173[.]88.
The chart below sums up the APT41 and WyrmSpy commonalities that could point to close ties between them.
To find similarities between APT41 and DragonEgg, meanwhile, we performed the same DNS searches we did with the WyrmSpy IoCs.
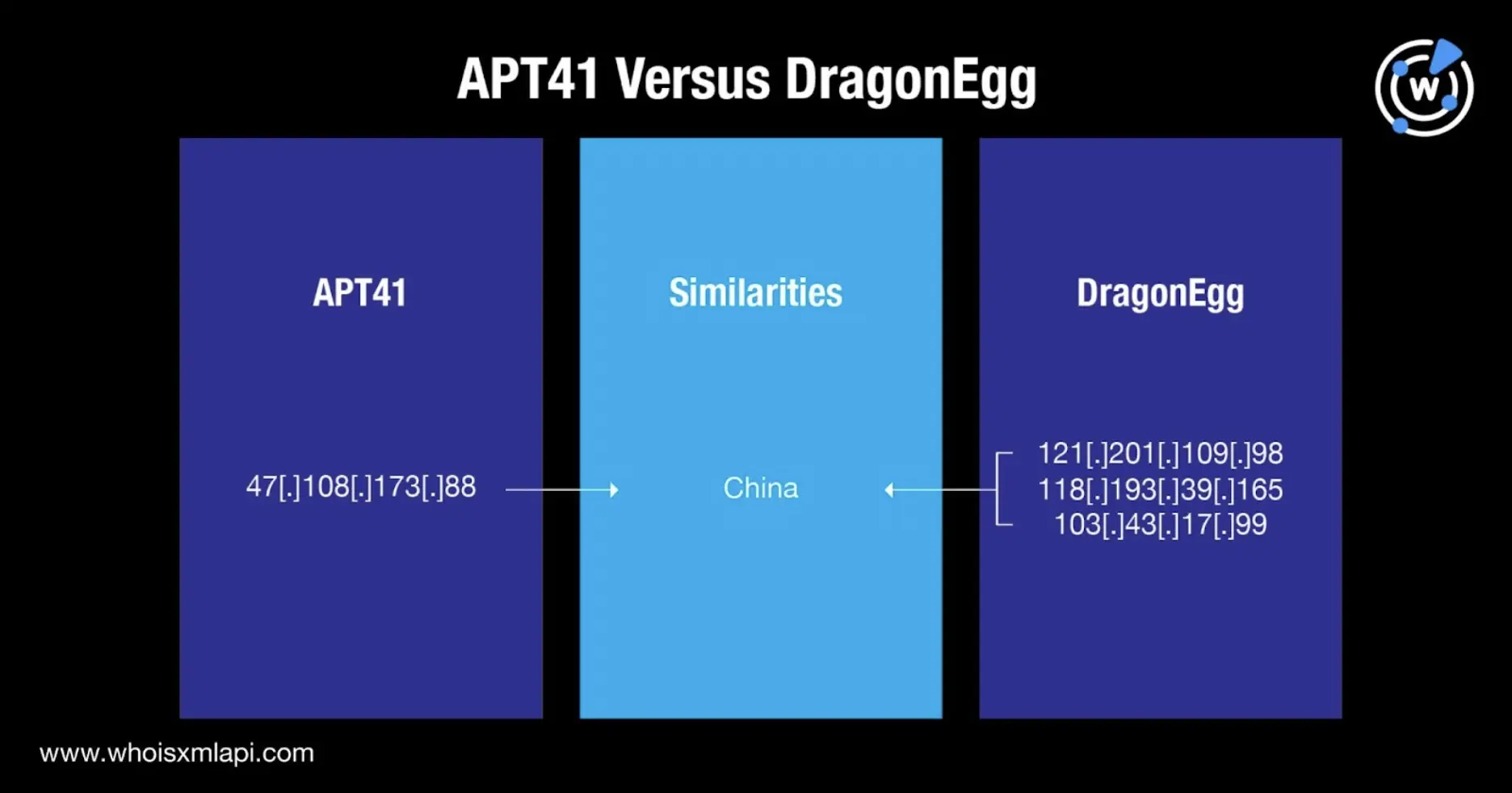
A bulk WHOIS lookup for the DragonEgg IoCs showed that while three of the four domains—tbtianyan[.]com, imwork[.]net, and yxwasec[.]com—didn’t share any of the APT41 domain registrars, they were registered in China—the APT group’s base of operations. The fourth IoC—huaxin-bantian[.]duckdns[.]org—was part of the Duck DNS infrastructure. As such, its WHOIS record details were excluded from our analysis.
Also, while a bulk IP geolocation lookup for the three IP addresses identified as IoCs—121[.]201[.]109[.]98, 118[.]193[.]39[.]165, and 103[.]43[.]17[.]99—didn’t show ISP similarities with APT41, all of them pointed to China as their origin, akin to the IoC 47[.]108[.]173[.]88. Take a look at the chart below.
Last but definitely not least, we sought to identify other WyrmSpy and DragonEgg connected artifacts that could put organizations at risk.
We noticed unique strings—win10 + microsoft and andropwn—in two of the WyrmSpy IoCs, alluding to Microsoft and Android ownership. Domains & Subdomains Discovery searches led to the discovery of eight additional domains—seven for win10 + microsoft and one for andropwn. None of them, however, have been classified as malicious as of this writing.
We learned from DNS lookups for the domains identified as IoCs that alxc[.]tbtianyan[.]com resolved to the IP address 43[.]229[.]153[.]189, which wasn’t part of Lookout’s list and was malicious based on a malware check.
Reverse IP lookups for the four IP addresses (three IoCs and one additional IP resolution) revealed that three of them were dedicated hosts. Three out of the four IP addresses were shared by 94 domains, also yet unreported.
Finally, as with WyrmSpy, we also noticed unique strings among the domains identified as IoCs. We scoured the DNS for domains containing the strings alxc., smiss., imwork., huaxin-, and bantian. and uncovered 3,085 such web properties, 14 of which turned out to be malicious based on a bulk malware check.
DNS deep dives, like the ones featured in this post, could aid organizations looking for commonalities that threats and threat groups share. We have, for instance, found ties that somewhat bound WyrmSpy and DragonEgg to APT41 in support of what Lookout initially believed. They can also help identify other yet-unreported threat artifacts that may enhance cybersecurity processes and solutions.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byCSC
