


|
||
|
||
Since its discovery in 2019, cyber espionage group RedHotel has successfully stolen secret information from at least 17 target nations worldwide. Four years later, they haven’t stopped. Regardless of the many names the threat actors have become known as—Aquatic Panda, Bronze University, Charcoal Typhoon, Earth Lusca, or Red Scylla—one thing is for sure, they’ve successfully breached their targets aided by readily available attack tools.
AlienVault OTX compiled 46 RedHotel indicators of compromise (IoCs)—20 domains and 26 IP addresses—over the course of the group’s three years of operation. Threat Intelligence Platform, in an effort to identify other potential threat vectors, conducted an expansion analysis that led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
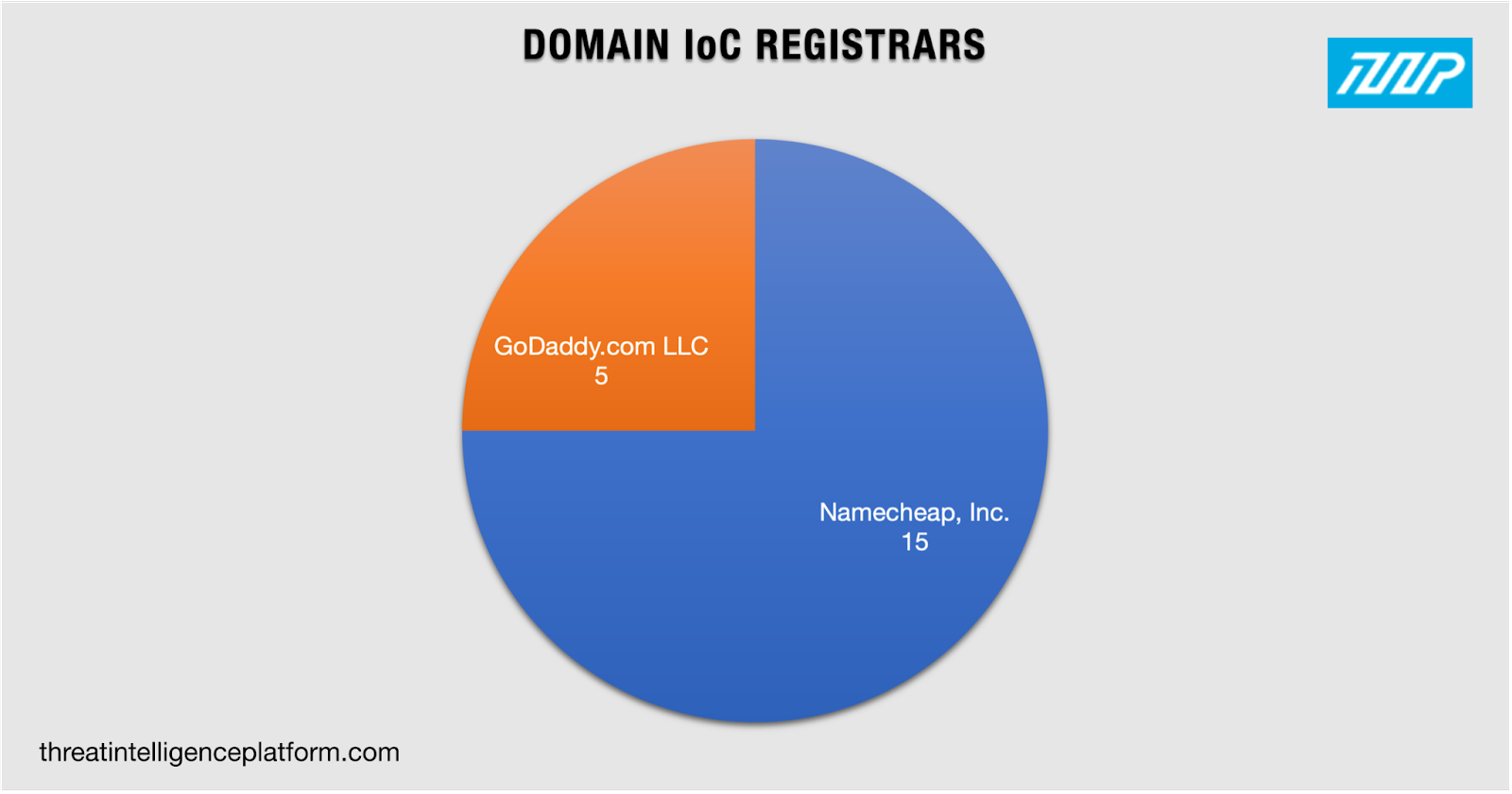
We began our analysis by subjecting the domains identified as IoCs to Threat Intelligence Platform (TIP) lookups. Those allowed us to uncover these WHOIS record findings:
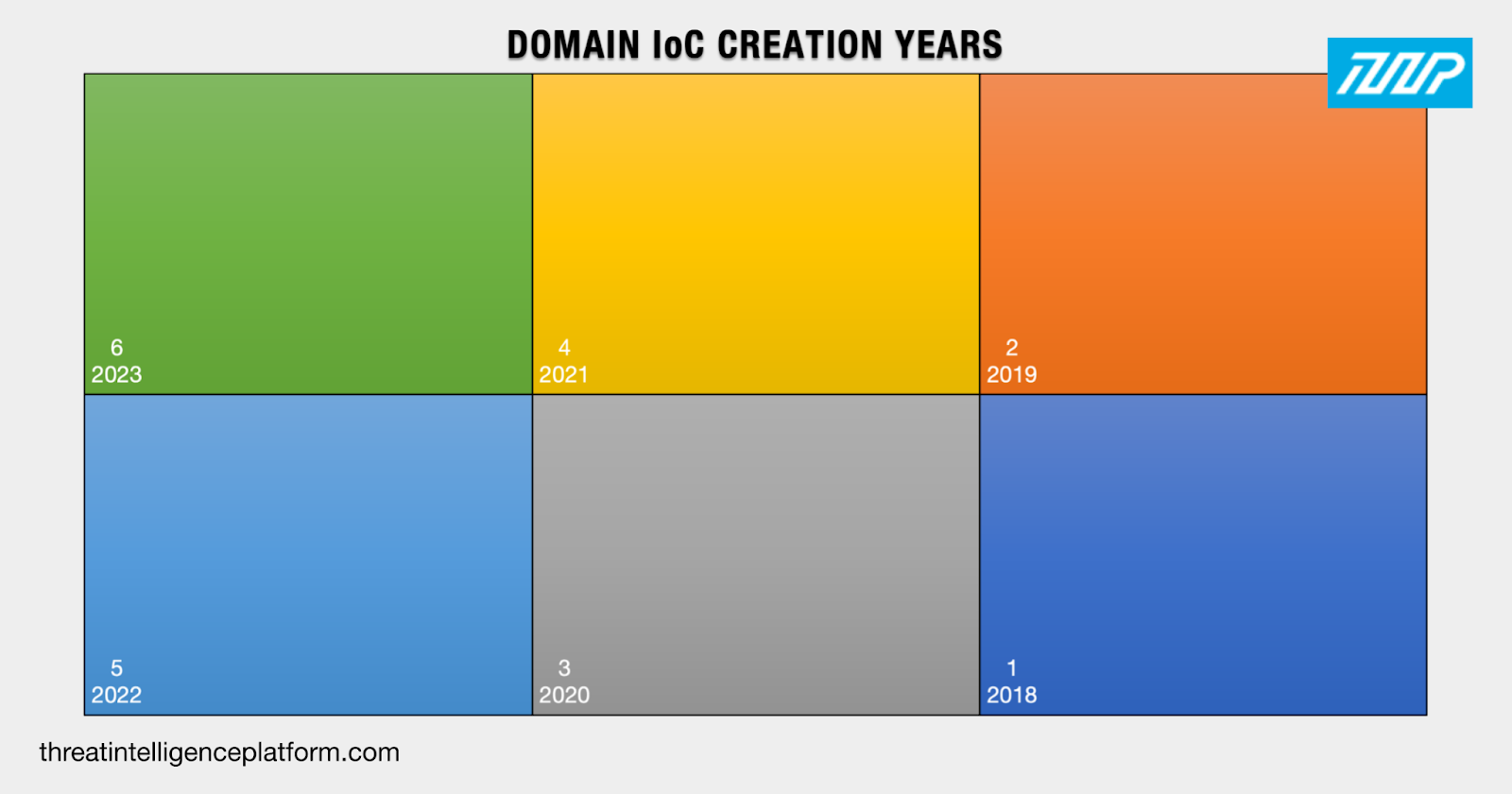
Noting that RedHotel first reared its head in 2019, the hackers seemed to prefer using newly registered domains (NRDs) in their campaigns given that they were created between 2018 and 2023.
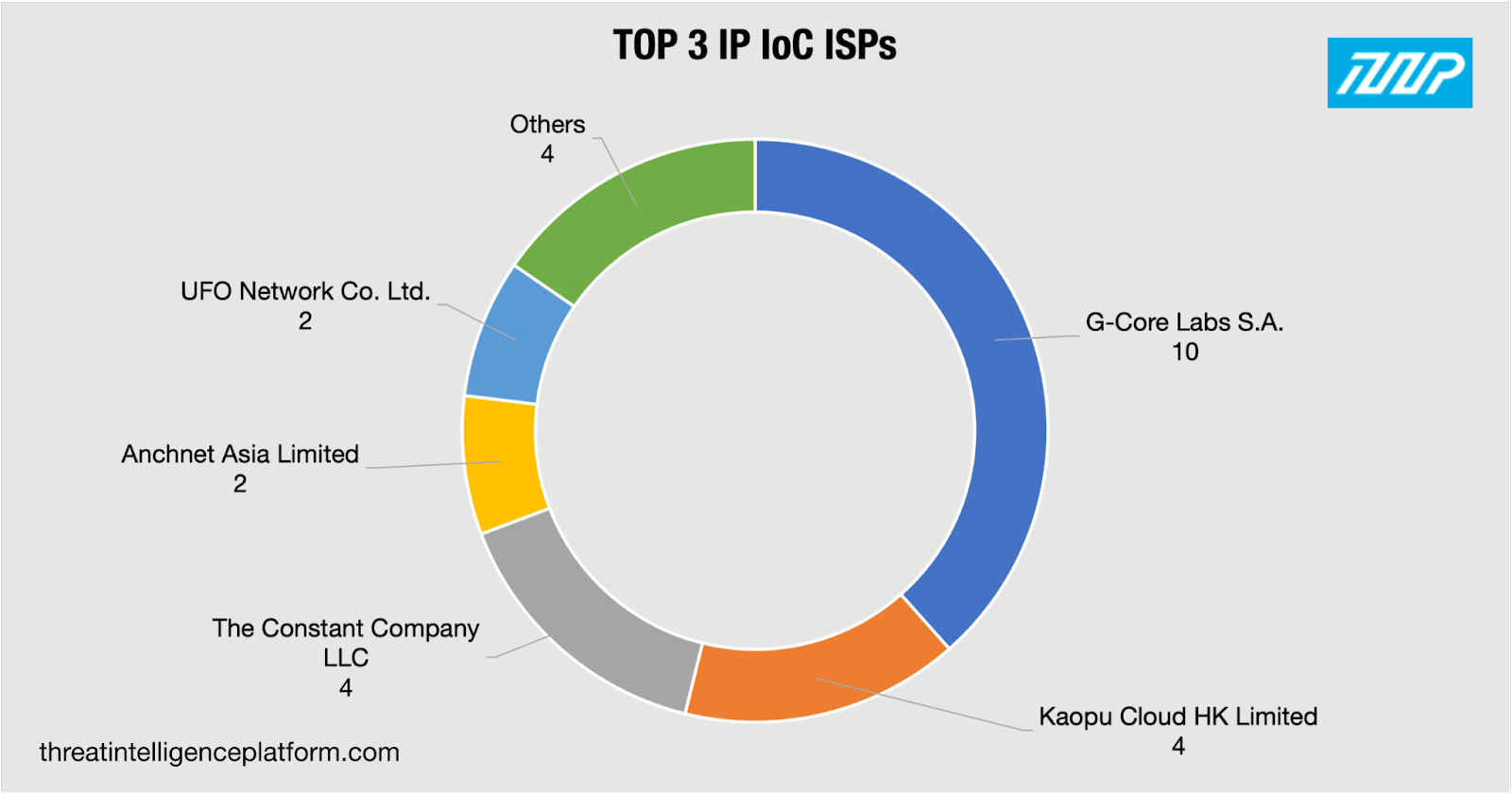
Our TIP lookups also uncovered these IP geolocation results:
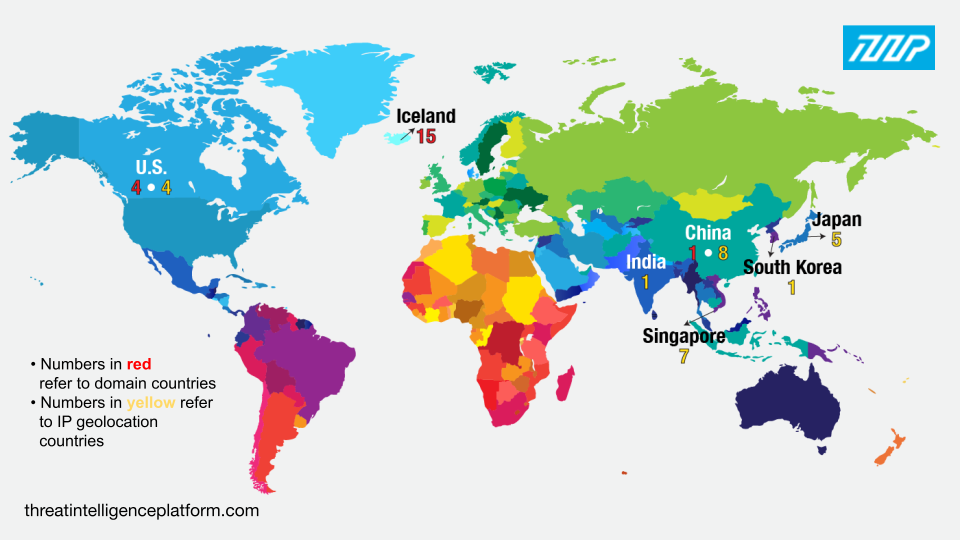
Next, we compared the IoCs’ registrant and geolocation countries and found that the domains and IP addresses only shared the U.S. and China as both registrant and geolocation origin. We can thus infer that the threat actors had a penchant for registering most of their domains in a remote country—Iceland—while using servers located nearer their homebase—in various parts of Asia.
To find potential RedHotel attack vectors that security researchers haven’t published yet, we first sought to determine if the threat actors used IP addresses other than those AlienVault already named. We found four, namely, 3[.]232[.]69[.]202, 34[.]193[.]242[.]162, 162[.]255[.]119[.]254, and 34[.]102[.]136[.]180, all geolocated in the U.S. TIP also revealed that two of them were malware hosts.
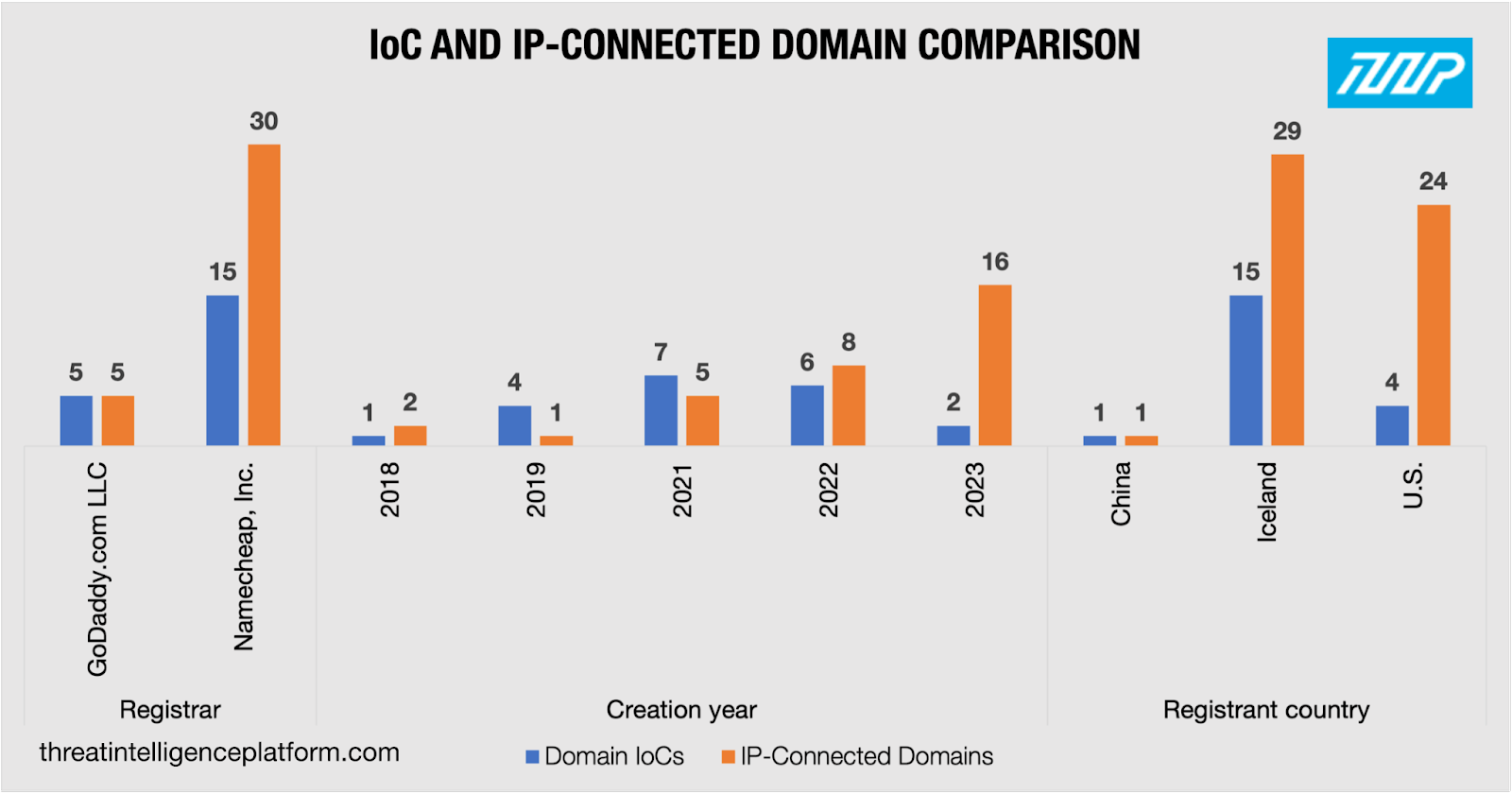
We limited the number of IP-connected domains by focusing only on those that resolved to dedicated hosts. Our search provided 38 unreported domains.
WHOIS record comparisons between the domains identified as IoCs and the IP-connected domains led to these discoveries:
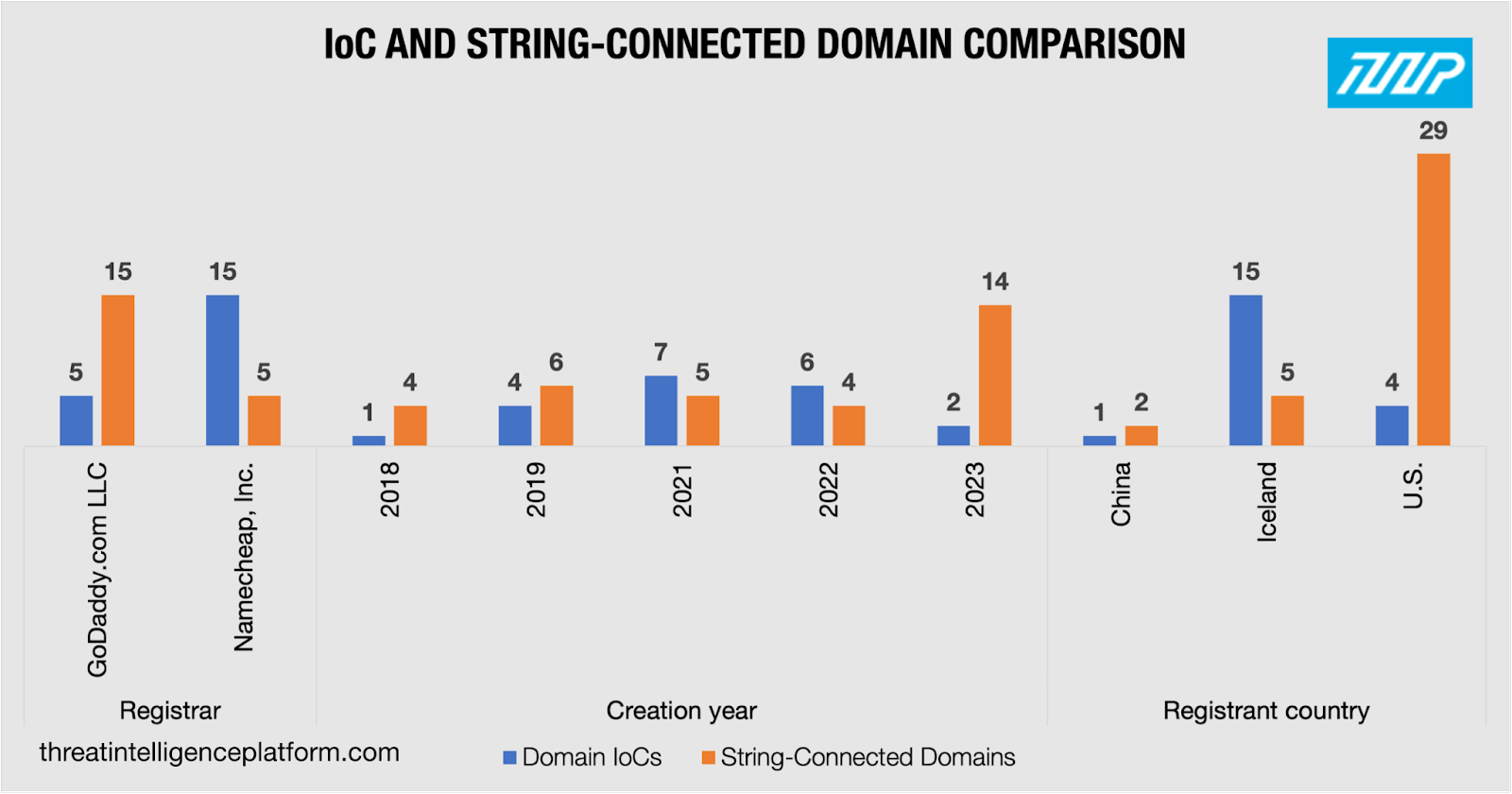
A closer scrutiny of the domains identified as IoCs enabled us to identify these unique strings:
They appeared in 2,157 other domains that could have ties to RedHotel. One in particular—livehost[.]space—was classified as a malware host and led to an index page.
Four of the strings on our list—0nenote, officesuport, livehost, and liveonlin—also alluded to connections to Microsoft products OneNote, Office, and Live. We thus compared their WHOIS details with that of microsoft[.]com and found that despite possible hints at links to the tech giant, none of them were publicly attributable to the company.
Like the IP-connected domains, we compared the string-connected properties to the domains identified as IoCs and found that the owners of a number of the string-connected domains left their personally identifiable information. Specifically:
We also discovered that:
Our DNS deep dive into the RedHotel attack infrastructure uncovered findings, such as the fact that the threat group registered most of their domains in remote countries, favored using NRDs, and used two of the most popular registrars.
Our IoC expansion analysis, meanwhile, led to the discovery of three additional malicious web properties—two IP addresses and one domain—that could have ties to RedHotel.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byVerisign

Sponsored byRadix
