


|
||
|
||
Evolution isn’t only for humans and other living things. Apparently, malware can evolve, too, and IcedID is a good example.
First detected as a banking trojan in 2017, IcedID continues to undergo updates that make it even more dangerous. In the past few months, IcedID variants have been observed to deliver ransomware payloads instead of performing its original function—stealing financial data.
Another notable change was that victim hosts now connect to the IceID command-and-control (C&C) servers using port 443 instead of 8080, making the action harder to detect. These latest activities inspired Cymru researchers to continuously track and analyze the IcedID BackConnect Protocol. In a recent report, they listed 34 IP addresses that pointed to the malware’s C&C servers, namely:
WhoisXML API researchers also found more indicators of compromise (IoCs) listed on three AlienVault OTX pulses, adding nine IP addresses and 15 domains to the list. Our analysis and expansion of the IoC lists led to these key findings:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We subjected all 43 IP addresses tagged as IoCs to a bulk IP geolocation lookup and found that all except 45[.]61[.]137[.]159 had active resolutions. They were primarily managed by Digital Ocean (40%) and BL Networks (21%). Several of them also pointed to live pages. Take a look at some of them below.

On the other hand, the domains tagged as IoCs by AlienVault told a different story. Only one out of the 15 domains had current WHOIS records—2fgithub[.]com, which uses Perfect Privacy LLC as its WHOIS privacy protection provider.
Upon further investigation, we found that some of the domains continued to host or redirect to live pages.

We dug deeper into the IcedID infrastructure in hopes of finding more related properties that may not have been identified yet. The threat actors may have inadvertently left traceable artifacts. They could also be waiting to use some of them in the future or may already be doing so.
Reverse IP lookups for all of the IP addresses tagged as IoCs revealed that only 12 had resolving domains. Each was connected to only four or fewer domains, indicating a dedicated IP network. In total, we found 22 unique domains resolving to the malicious IP addresses.
We looked into the malicious domains’ historical WHOIS records to see if other digital properties were connected to them. This led us to five unredacted email addresses, two of which were used to register more than 50 domains and therefore could be owned by a domainer. Thus, we decided to focus on the 44 connected domains registered using the remaining three email addresses.
We also looked at the IoCs’ IP resolutions and found that only six out of the 15 led to live content. Three of them shared their IP addresses with more than 250 other domains. That left us with 33 domains with a higher probability of being part of or connected to the malicious domain network.
In total, we identified 99 probable IP- and domain-connected artifacts. About 14% of them have been classified as malicious.
We also ran a bulk WHOIS lookup for the connected domains and found that only 53 had current WHOIS records with Domain Cost Club as registrar.
Their IP geolocation lookup results revealed that they were spread out across seven countries, including those that were either close to or the country locations of the IP addresses the Cymru researchers named. The map below shows these countries.
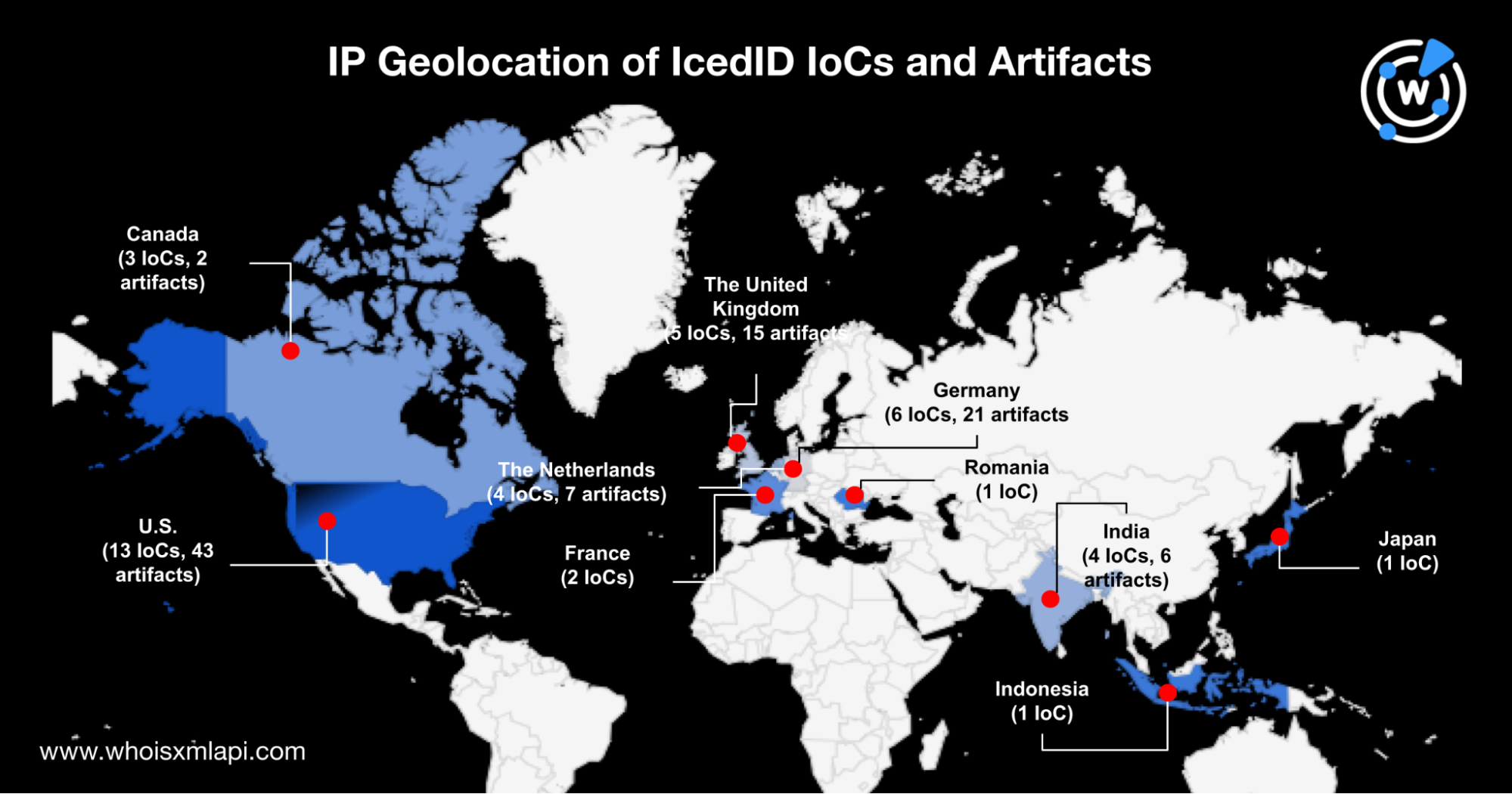
From an initial list of 59 IoCs, the DNS bread crumbs IceID left led us to 99 additional domains that could be part of or connected to the threat’s infrastructure. The artifacts’ connection to the IoCs may warrant further scrutiny and suspicion.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byVerisign

Sponsored byRadix

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byIPv4.Global
