


|
||
|
||
XLoader has been plaguing macOS users since it was first discovered in 2021. Back then, though, it only posed a threat to those who opted to install Java on their systems. That’s no longer the case, however, as its latest variant, encased in compromised OfficeNote installation packages (currently in beta mode), can cause damage to any macOS devices.
SentinelOne published 19 indicators of compromise (IoCs)—15 domains (extracted from the reported host names) and four IP addresses—for the latest XLoader variant, which we at WhoisXML API subjected to a DNS deep dive. Our probe led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our DNS probe with a bulk WHOIS lookup for the 15 domains identified as XLoader IoCs and found that:
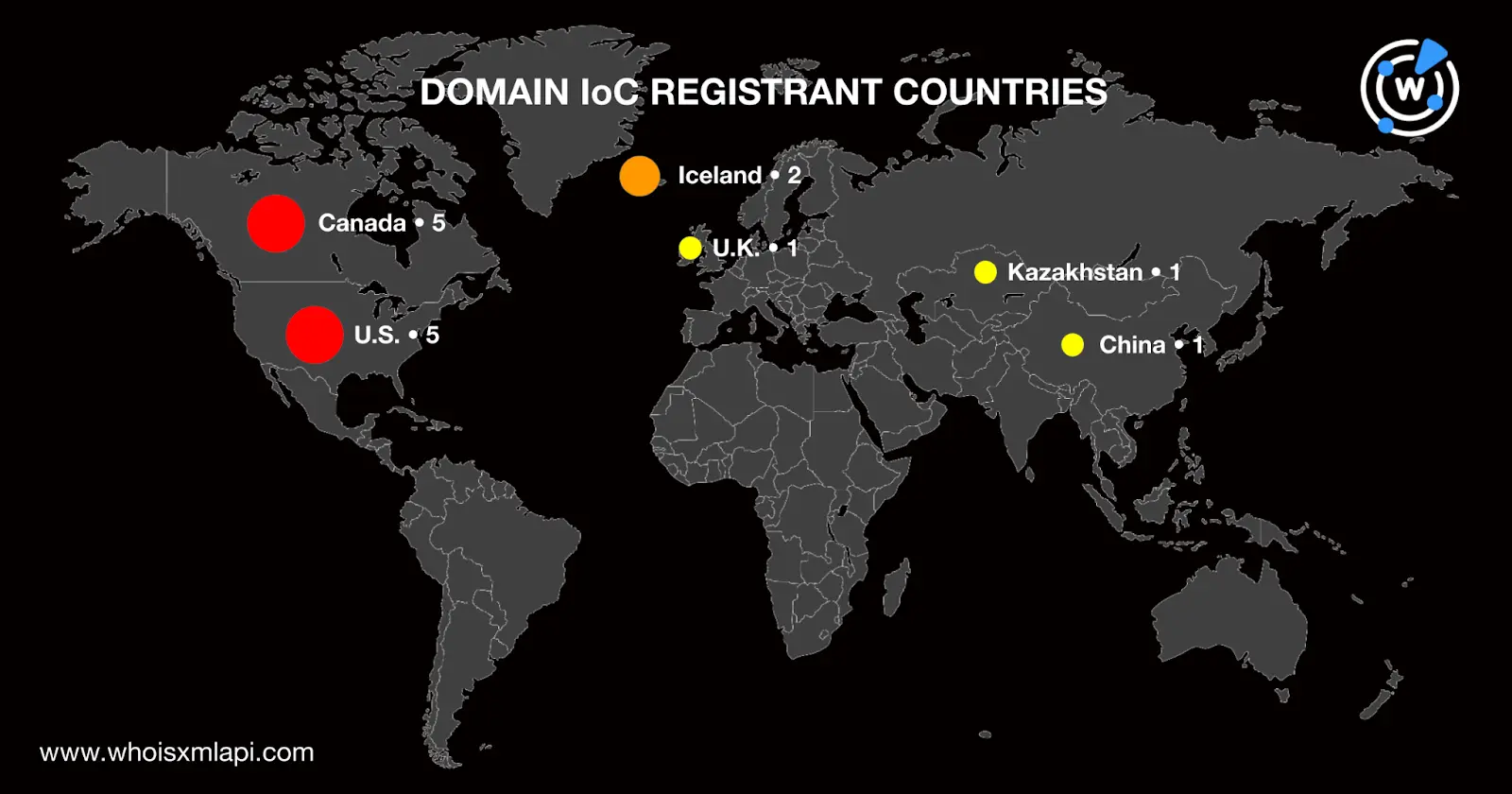
A bulk IP geolocation lookup for the four IP addresses tagged as IoCs followed, which led to these discoveries:
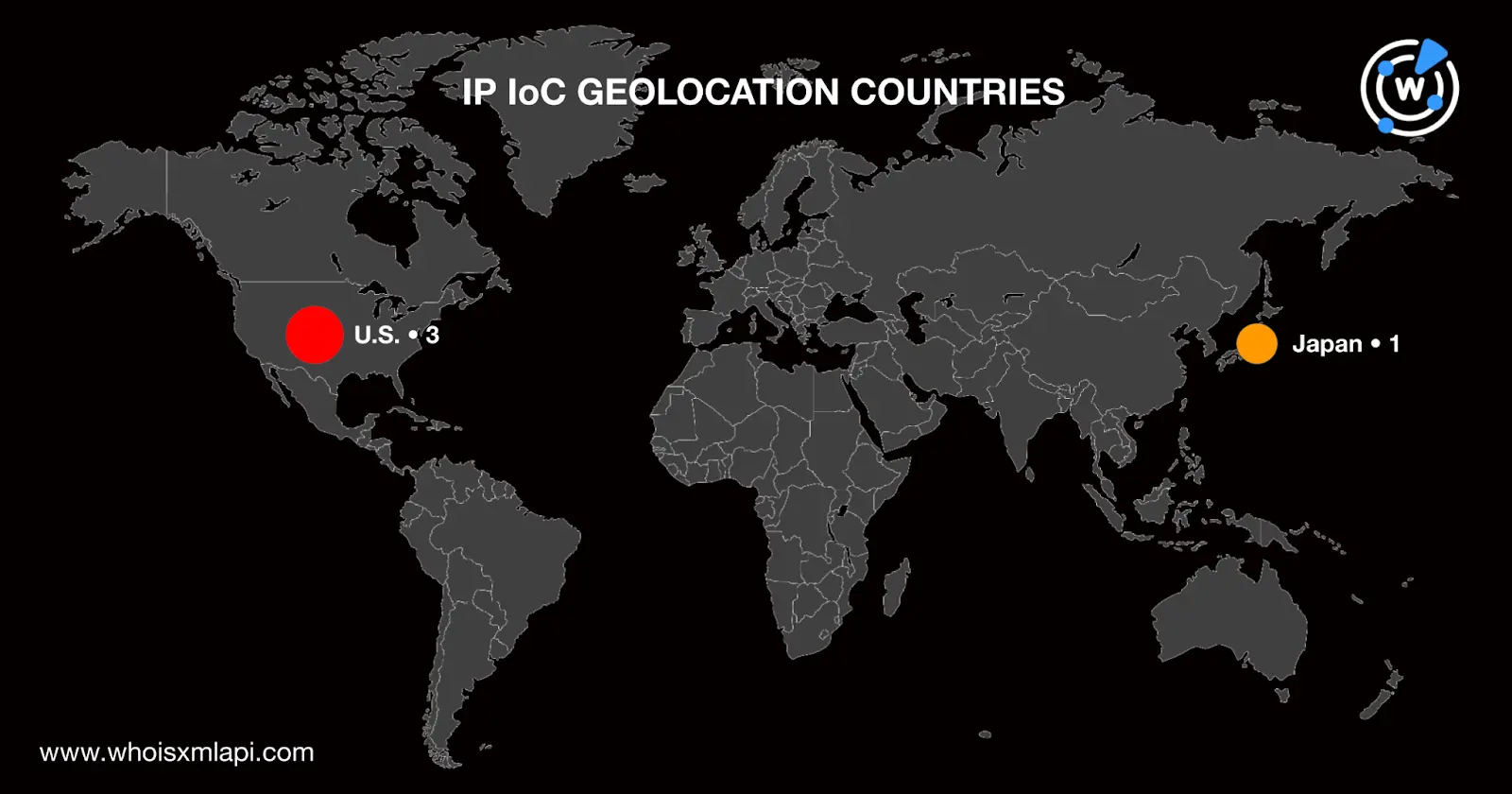
Note that a comparison of the domains and IP addresses classified as XLoader IoCs revealed these similarities:
Next, we began our list expansion with DNS lookups for the domains identified as IoCs. That led to the discovery of 27 IP resolutions for 11 domains, three of which were already part of SentinelOne’s list. None of the domains with active IP resolutions shared any of the identified hosts.
A bulk IP geolocation lookup for the 24 additional IP addresses revealed that:
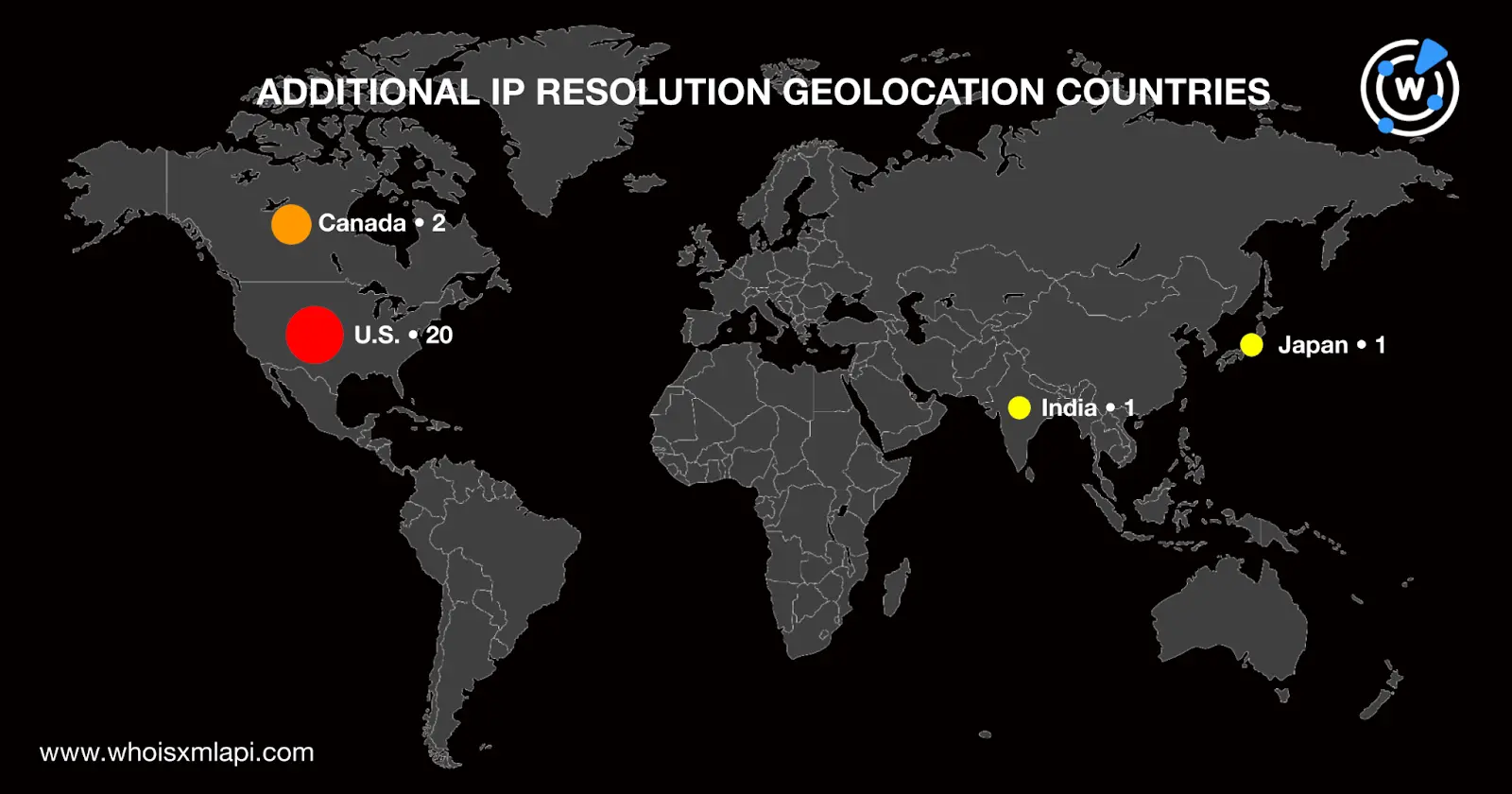
A bulk malware check for the unreported IP resolutions showed that 19 were malicious.
Our DNS lookups also revealed that six of the now 27 IP addresses in total—the three identified as IoCs and 24 additional resolutions—were seemingly dedicated. They hosted a total of 53 unique domains, three of which turned out to be malicious according to a bulk malware check.
Screenshot lookups for the three malicious IP-connected domains showed they continued to host or lead to live pages. Artkit[.]top led to an e-commerce shop while both e6796[.]com and e9579[.]com led to an app store.
Next, we used text strings found among the 15 domains identified as IoCs to look for similar-looking XLoader artifacts via Domains & Subdomains Discovery. Specifically, we looked for domains containing, or in certain cases starting, with the strings:
Our DNS foray uncovered 446 string-connected domains.
Finally, we know from the SentinelOne post that XLoader targets macOS and soon-to-launch app OfficeNote. We thus used the brands as Domains & Subdomains Discovery search terms (exactly matched macos and contained officenote) to look for subdomains that could figure in future campaigns, possibly phishing attacks against the brands or their users. We found 492 brand-containing subdomains in total.
Bulk WHOIS lookups for the macos and officenote subdomains revealed that:
Our XLoader DNS deep dive led to the discovery of more than 500 possibly connected artifacts. It also allowed us to uncover close to 500 subdomains containing the two brands the threat actors trailed their sights on—macOS and OfficeNote.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byRadix

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign
