


|
||
|
||
It’s not uncommon for cybercriminals to tweak an existing piece of malware and then call it a new creation. We’ve seen that happen even in malware’s earliest days. It’s actually happening more and more these days, especially with the rise of the malware-as-a-service (MaaS) business model.
Netenrich recently published an in-depth analysis of one such malware they’ve dubbed “ADHUBLLKA,” which has been linked and likened to at least three older malware—CryptoLocker, LimeRAT, and GlobeImposter. The researchers identified 47 indicators of compromise (IoCs)—11 domains, 32 IP addresses, and four email addresses—so far.
Using the IoCs as jump-off points, the WhoisXML API research team performed a DNS deep dive that uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our investigation with a further analysis of the published ADHUBLLKA IoCs. First, we performed a WHOIS lookup for the only domain that wasn’t hosted on the Tor network—yip[.]su. That led to the discovery of an unredacted registrant email address—root@iplogger[.]com. We also learned that the IoC was administered by RUCENTER-SU and created on 17 January 2017.
Next, we subjected the 32 IP addresses identified as IoCs to a bulk IP geolocation lookup that led to these discoveries:
Finally, we conducted a bulk email verification lookup for the four email addresses identified as IoCs. Here’s a summary of our findings.
As it is our goal to make the Internet safer for all users, we sought to find artifacts potentially connected to ADHUBLLKA. We started by looking for the IP address yip[.]su resolved to. Our DNS lookup gave 148[.]251[.]234[.]93 as a result. The IP address, which turned out to be malicious according to a malware check, originated from Germany and was administered by Hetzner Online GmbH based on an IP geolocation lookup.
Next, we performed reverse IP lookups for the 33 IP addresses—32 identified as IoCs and one additional IP resolution—and found that 15 were seemingly dedicated. Together, they hosted 230 domains, 18 of which turned out to be malicious based on a bulk malware check.
Screenshot lookups showed that all of the malicious domains continued to host live content.
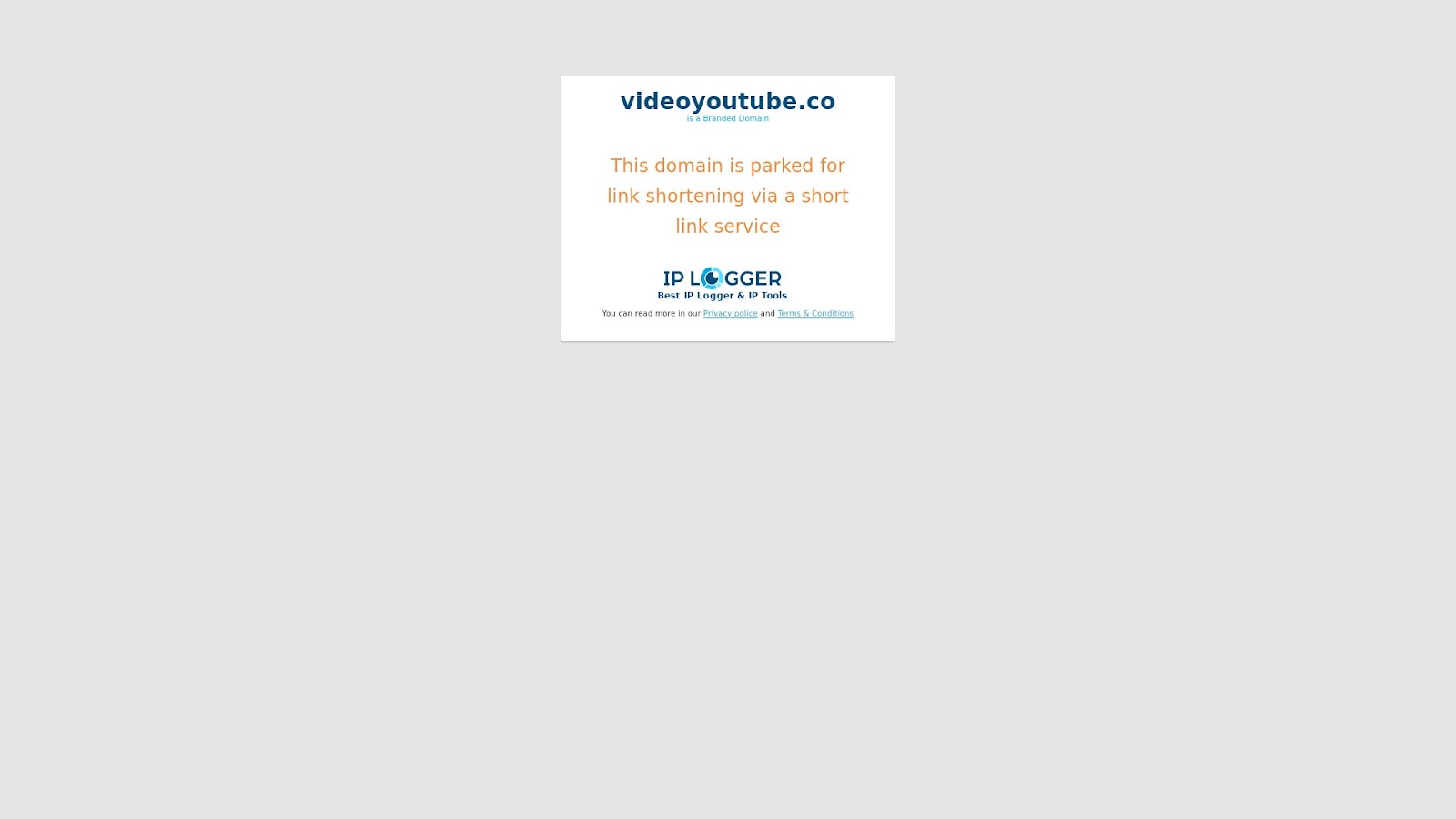
Two of the domain names were interesting since they contained brand names, specifically Instagram, albeit misspelled (lnsstagram[.]com), and YouTube (videoyoutube[.]co). WHOIS record comparisons with the brands’ official domains, however, revealed that the malicious properties weren’t publicly attributable to the tech giants. Both domains were seemingly parked via the short link service IP Logger.

We also found that four of the malicious domains contained the string iplogger. We could not, however, explicitly determine if they were owned by the company since the WHOIS record details of iplogger[.]org (its official domain name) is redacted. However, all four domains sported the company’s brand name and logo. They also had the same content as, or redirected to, its official website.
In addition, the pages hosted on 10 other malicious domains also sported the shortened link service provider’s logo. Examples are shown below.


To check if other possibly connected artifacts were present in the DNS, we looked for domains containing the same text string as the only IoC that wasn’t hosted on the Tor network—yip[.]su. Our Domains & Subdomains Discovery search allowed us to uncover 200 such domains.
The Netenrich analysis revealed ADHUBLLKA connections to at least three malware—the ransomware CryptoLocker, the remote access Trojan (RAT) LimeRAT, and another ransomware GlobeImposter. We thus sought to see if they had DNS ties, too.
We obtained seven IP addresses identified as CryptoLocker, LimeRAT, and GlobeImposterIoCs. A bulk IP geolocation lookup comparison showed that only the LimeRAT IoC 20[.]199[.]13[.]167 had something in common with the ADHUBLLKA IoC 40[.]126[.]32[.]133, that is, they shared the same ISP—Hetzner Online GmbH).
Our ADHUBLLKA IoC list expansion analysis led to close to 500 artifacts that could be related to the threat, in addition to another IP address that could further link the newly discovered ransomware to LimeRAT. Also, we noted the presence of several malicious domains containing the string iplogger and the use of the domain iplogger[.]com in the email address used to register the IoC yip[.]su.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byRadix

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byVerisign

Sponsored byWhoisXML API
