


|
||
|
||
Rhysida, a new ransomware currently plaguing users, may not be novel but it’s proving to be just as effective. Fortra published an in-depth analysis of the malware currently holding the data of healthcare organizations primarily based in the U.S. hostage. Other countries and their government agencies shouldn’t rest easy, though, as its operators have also gone after the Chilean army.
Since Rhysida’s emergence, the cybersecurity community has been amassing indicators of compromise (IoCs) related to the threat. AlienVault OTX, for one, has collated 50 domains and three email addresses so far.
The WhoisXML API research team dove deeper into the ransomware operators’ infrastructure via an IoC list expansion analysis in an effort to identify other potential attack vectors that may not yet be on organizations’ radar. We found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our in-depth analysis of Rhysida by looking for more information aided by our IP, DNS, and WHOIS tools.
A bulk WHOIS lookup for the 50 domains identified as Rhysida IoCs revealed that:
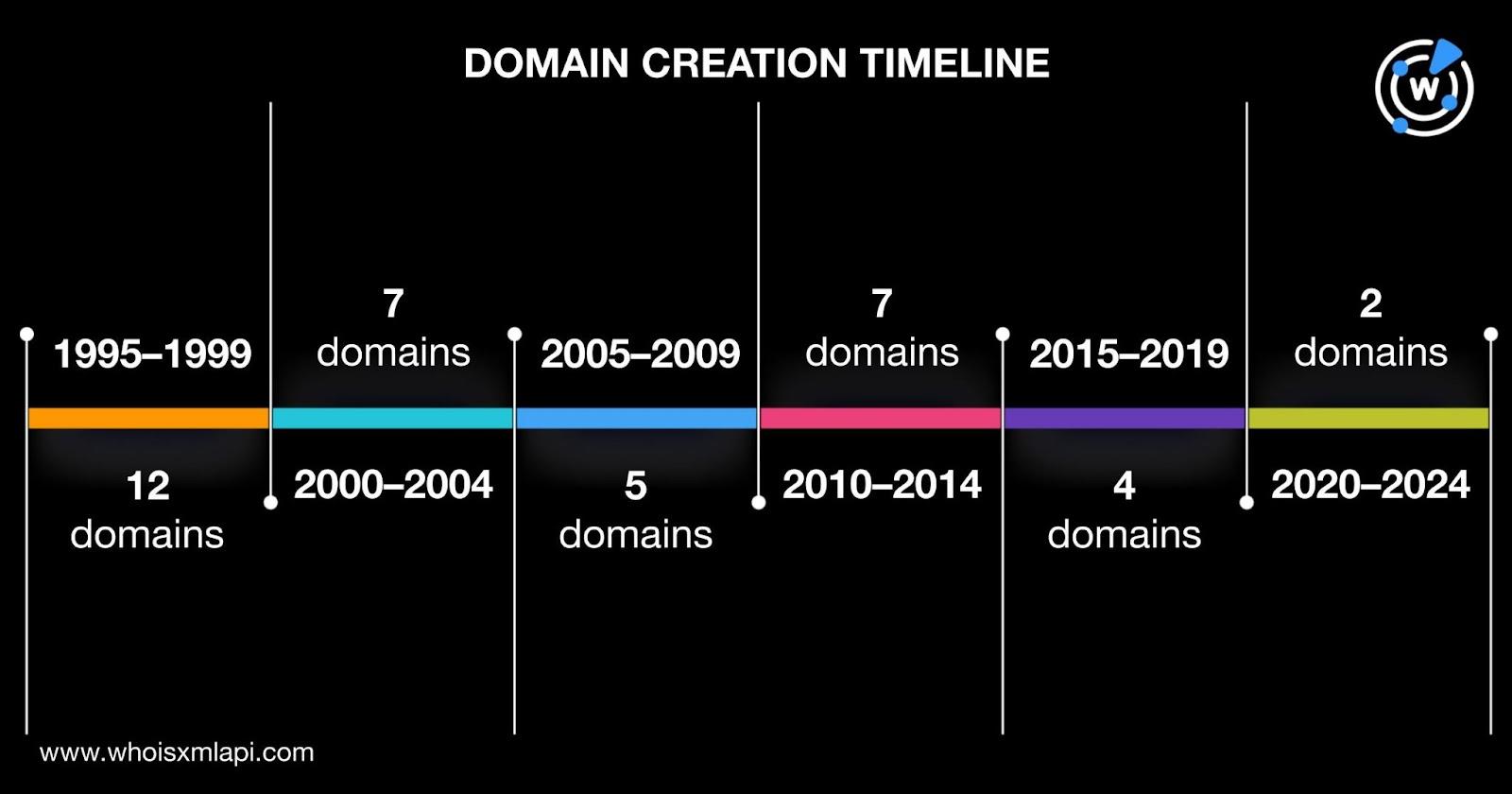
We also performed reverse WHOIS searches for the email addresses identified as IoCs but none were used to register domains.
To determine other web properties that could be part of the Rhysida infrastructure, we expanded the current list of IoCs starting with DNS lookups that revealed that 47 of the domains resolved to 60 unique IP addresses, eight of which turned out to be malicious based on a bulk malware check.
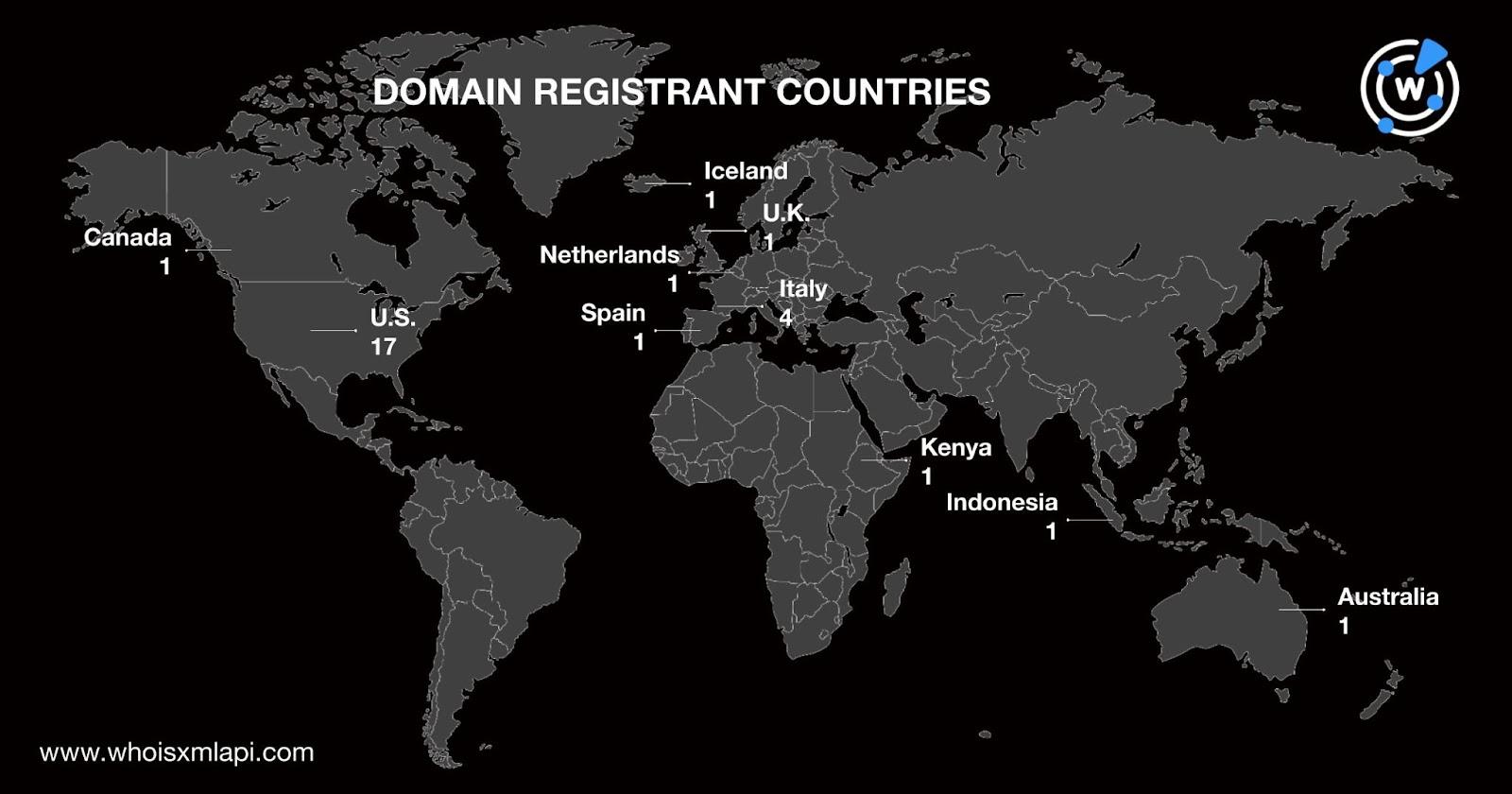
A bulk IP geolocation lookup for the domain IoCs’ hosts revealed that:

They were distributed among 33 ISPs led by Cloudflare (16 IoCs), Amazon (six IoCs), and Wix.com (three IoCs).
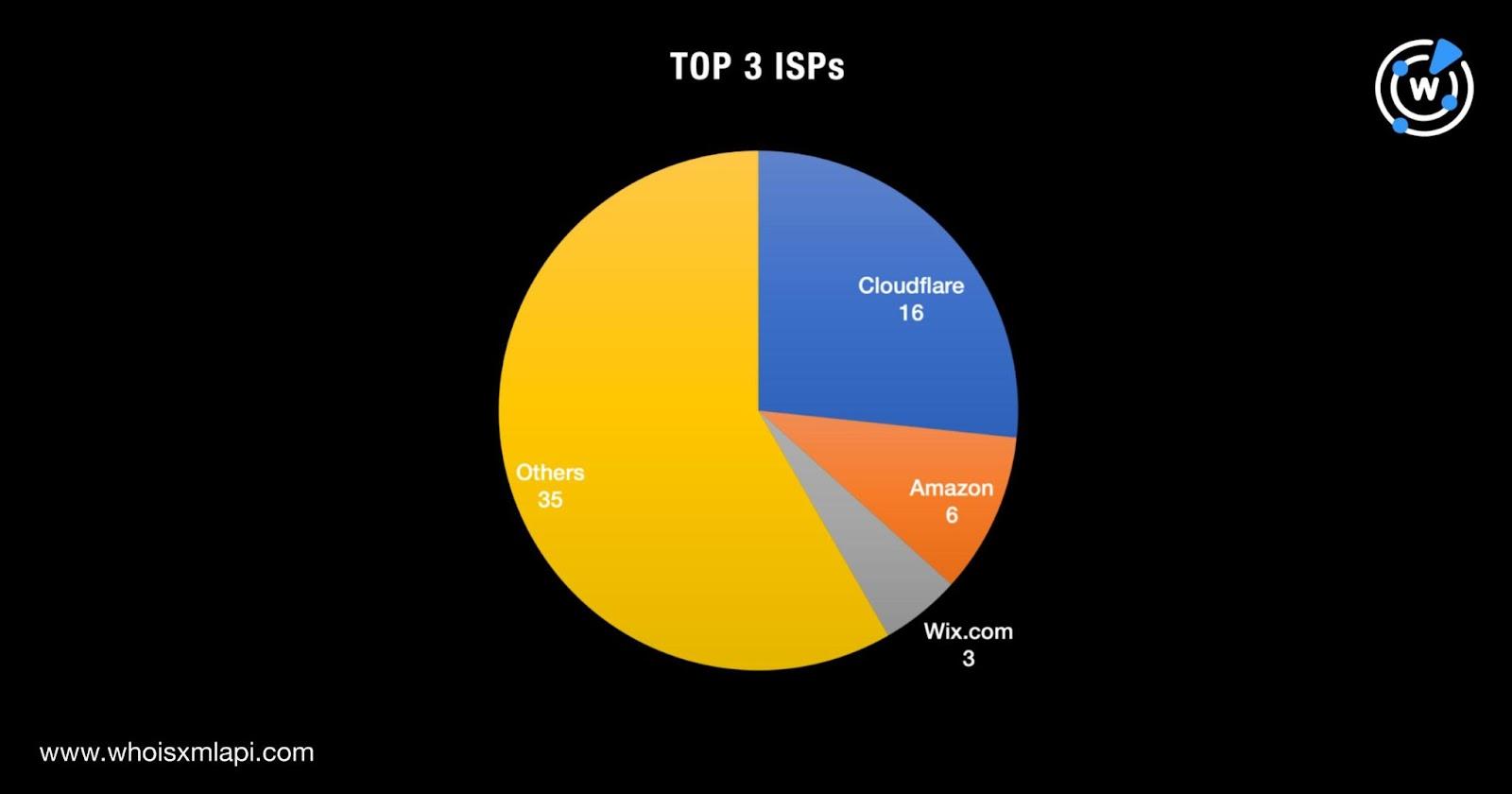
Reverse IP lookups for the 60 IP resolutions showed that 44 were seemingly dedicated and played host to 1,461 domains not yet on the published list of IoCs. Three of the IP-connected domains are already being detected as malicious and one continues to host a live page to date based on a screenshot lookup.
To widen our threat hunting coverage, we also used these strings found among 47 of the domains identified as IoCs as Domains & Subdomains Discovery search terms:
That led to the discovery of 11,774 domains, 19 of which turned out to be malicious according to a bulk malware check. Only one continues to host live content as of this writing. Based on a WHOIS lookup, dworekpodlipami[.]katowice[.]pl was created on 17 August 2006 with Home.pl S.A. as its registrar.
The 18 remaining malicious domains were either unreachable, parked, or led to blank or error pages.
Our in-depth analysis of the published Rhysida IoCs allowed us to uncover more than 18,000 possibly connected artifacts. It also shed more light on the ransomware operators’ modus operandi. For instance, we found that they seem to prefer using aged domains over NRDs, with the newest ones created two years ago. They also chose to distribute parts of their infrastructure to several service providers (registrars and ISPs alike) and countries.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byRadix

Sponsored byCSC
