


|
||
|
||
Threat actors have been seen yet again abusing a technology meant to make things easy for all of us—QR codes—in one of the most commonly utilized cybercriminal activities—phishing. The rise in QR code phishing isn’t surprising given that according to several studies, as much as 86% of the entire global population use their mobile phones for all kinds of transactions, including financial ones.
The large potential victim pool and the open-source nature of QR codes could be the rationale behind the technology’s usage in phishing. It also doesn’t help that determining the validity of QR codes is much harder than doing so for hyperlinks.
Trustwave researchers recently noted this trend and published the results of their in-depth study on ongoing QR code phishing scams, including 18 URLs that they identified as indicators of compromise (IoCs). In an effort to help curb similar attacks in the future, the WhoisXML API research team trooped to the DNS to look for as many unreported potentially connected artifacts as possible. Our deep dive led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
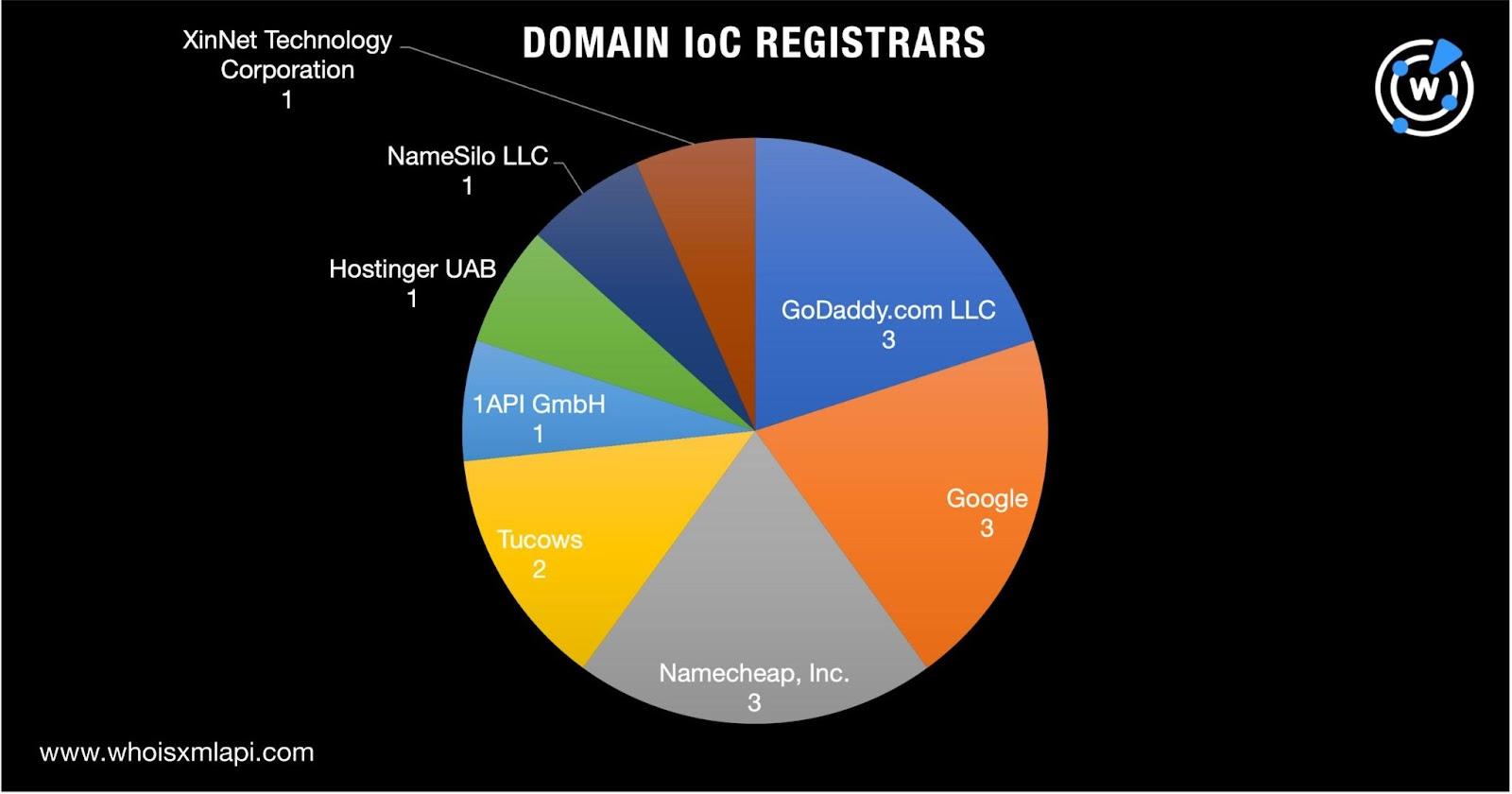
To gather as much information as possible about the threat actors’ infrastructure, we first subjected the IoCs to a bulk WHOIS lookup. We found that:
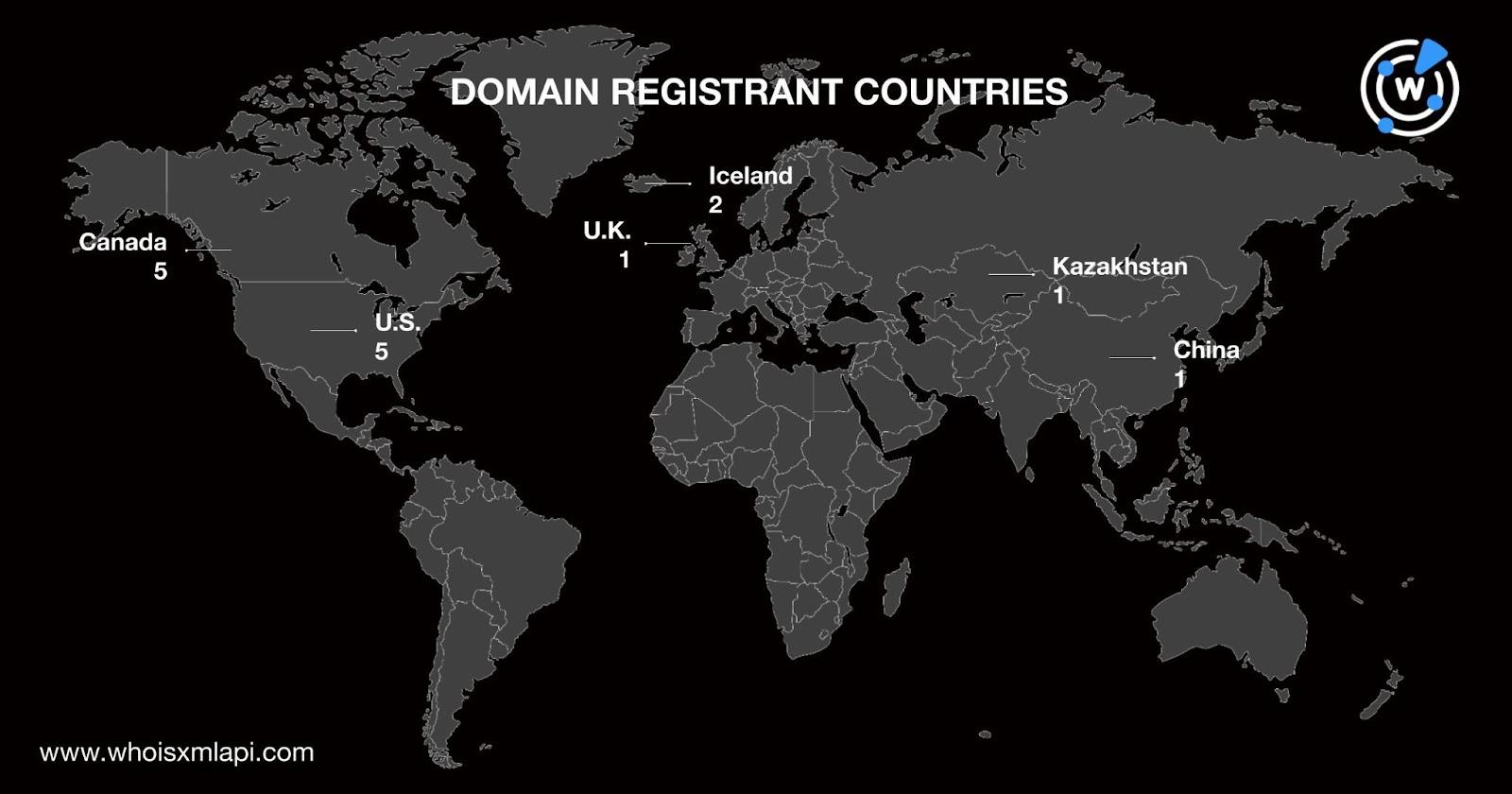
The 15 domains were registered in six countries led by Canada and the U.S., accounting for five IoCs each.
Our bulk WHOIS lookup for the 18 domains extracted from the URLs identified as IoCs uncovered an unredacted registrant name. A reverse WHOIS search revealed that the name appeared in the historical WHOIS records of at least 10,000 other domains. A bulk malware check for them showed that 10 were already being detected as malicious. To date, only one remained accessible although it led to a blank page.
To dig for connected artifacts which published reports may not contain, we then subjected the 18 extracted domains to DNS lookups. Seven of them resolved to 10 unique IP addresses. Reverse IP lookups for the IP resolutions revealed that two of them were seemingly dedicated. Altogether, the dedicated IP addresses hosted 114 domains that weren’t part of the IoC list, 26 of which are already being detected as malicious based on a bulk malware check.
Screenshot lookups for the 26 malicious IP-connected domains showed that 24 still hosted live content at the time of writing. Take a look at three examples shown below.
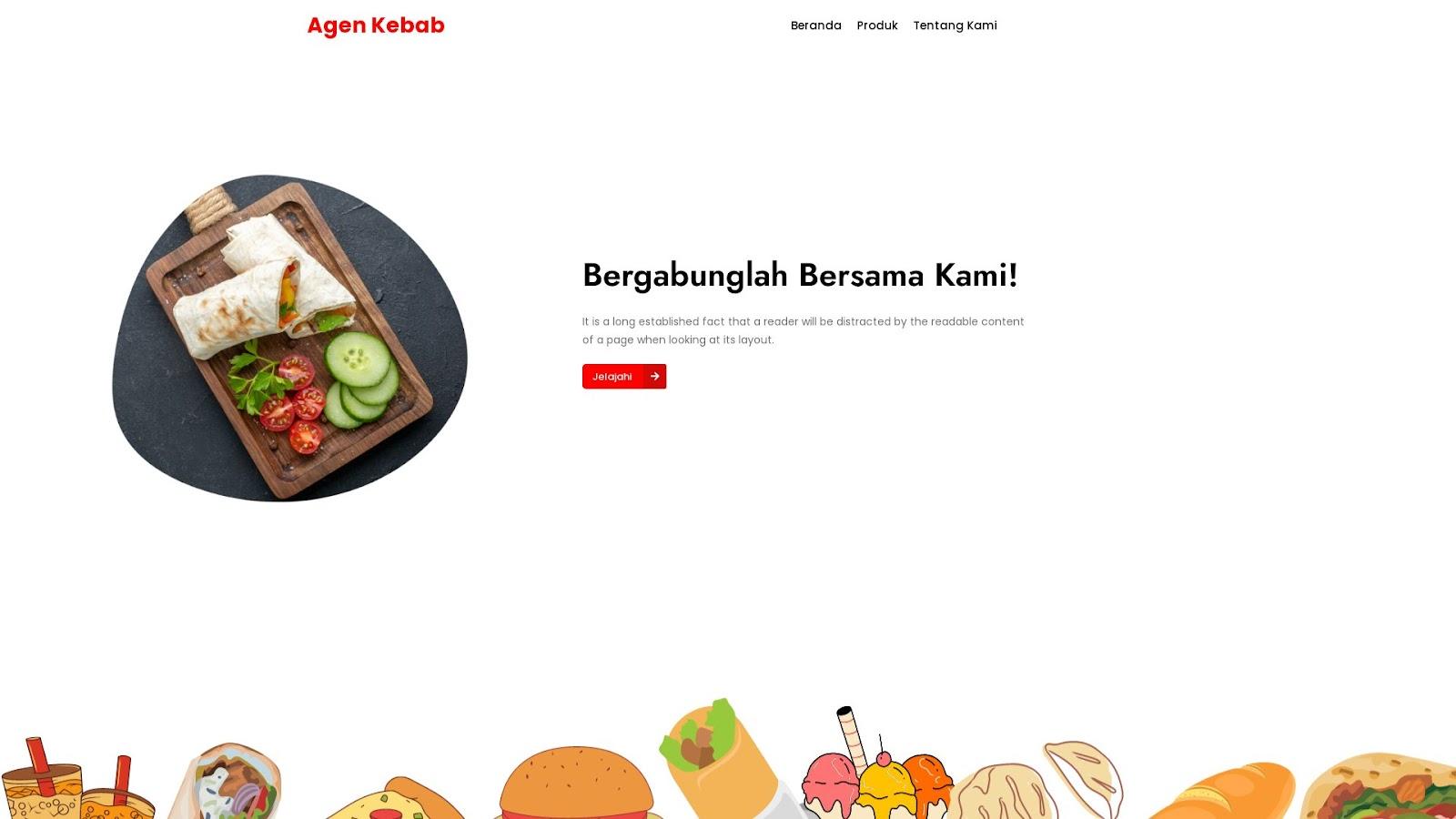
Based on screenshots of three pages hosted on the domains identified as IoCs, the QR code phishing campaign threat actors seemed to use web properties whose content could be mistaken for legitimate business pages. Three examples are shown below.

What was more interesting, however, was that the screenshots of the pages hosted on the IoC lockvvoodgroup[.]com and the newly discovered malicious IP-connected domain customsfee-supporthub[.]com led to web pages with the same content.
The other business pages seem to focus on products and services that potential victims may typically look for on any given day, such as sites that offer food delivery, courier, and travel services, hence upping the chances that they wouldn’t think twice about their content.
Strings found among six of the extracted domains listed below also appeared in 10,045 other domains based on Domains & Subdomains Discovery searches.
A bulk malware check for the 10,045 string-connected domains revealed that four were being detected as malicious. One continued to host live content at the time of writing.
Our list expansion analysis of the domains we extracted from 18 URLs identified as QR code phishing IoCs uncovered more than 20,000 possibly connected artifacts. It also brought to light the IP addresses the threat actors may have used during their attacks, apart from more malicious domains that could be part of their or other threat actors’ cybercriminal infrastructure.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byVerisign

Sponsored byRadix

Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byWhoisXML API
