


|
||
|
||
BlackNet RAT, first discovered during the COVID-19 pandemic and being distributed via spam messages offering an effective cure for the virus, seems to have outlived the global crisis. The remote access Trojan (RAT)‘s operators continued on with their nefarious activities. The BlackNet botnet was named one of the top botnets of the first quarter of 2023.
Throughout BlackNet RAT’s three years of operation, several researchers have analyzed and published reports about the malware. Alienvault OTX contributors collated thousands of indicators of compromise (IoCs) related to the threat.
The WhoisXML API research team expanded the published list of IoCs, specifically 54 IP addresses and 531 domains, to identify unreported artifacts, if any, using comprehensive DNS intelligence. Our analysis found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our investigation by taking a closer look at the 585 IoCs in Alienvault OTX’s list.
A bulk WHOIS lookup for the 531 domains led to these findings:
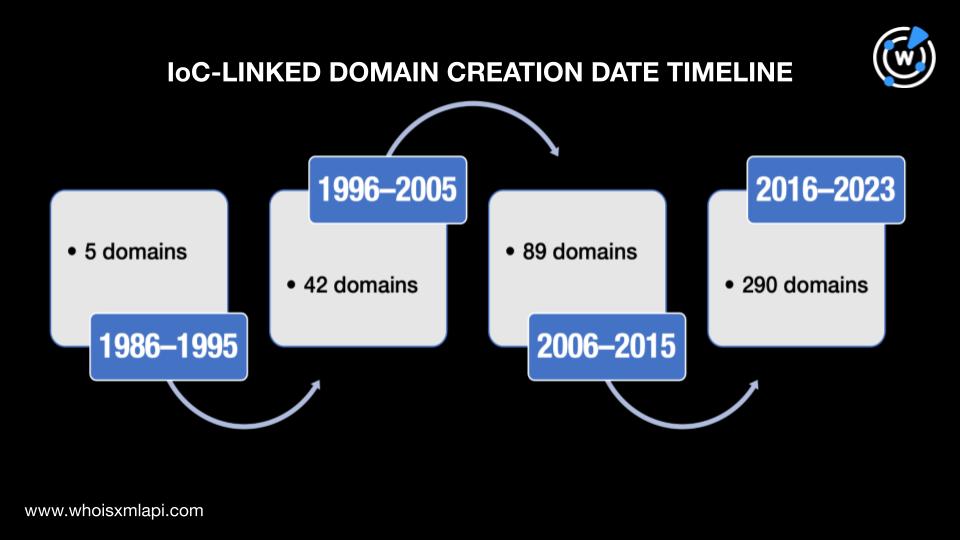
The IoC-linked domains were created between 1986 and 2023. Given the widespread nature of the domains’ creation dates, we could infer that the BlackNet RAT operators didn’t discriminate when it came to the age of the properties they used to host malware-laden pages. Note, however, that 105 of the IoC-linked domains didn’t have viewable creation dates.
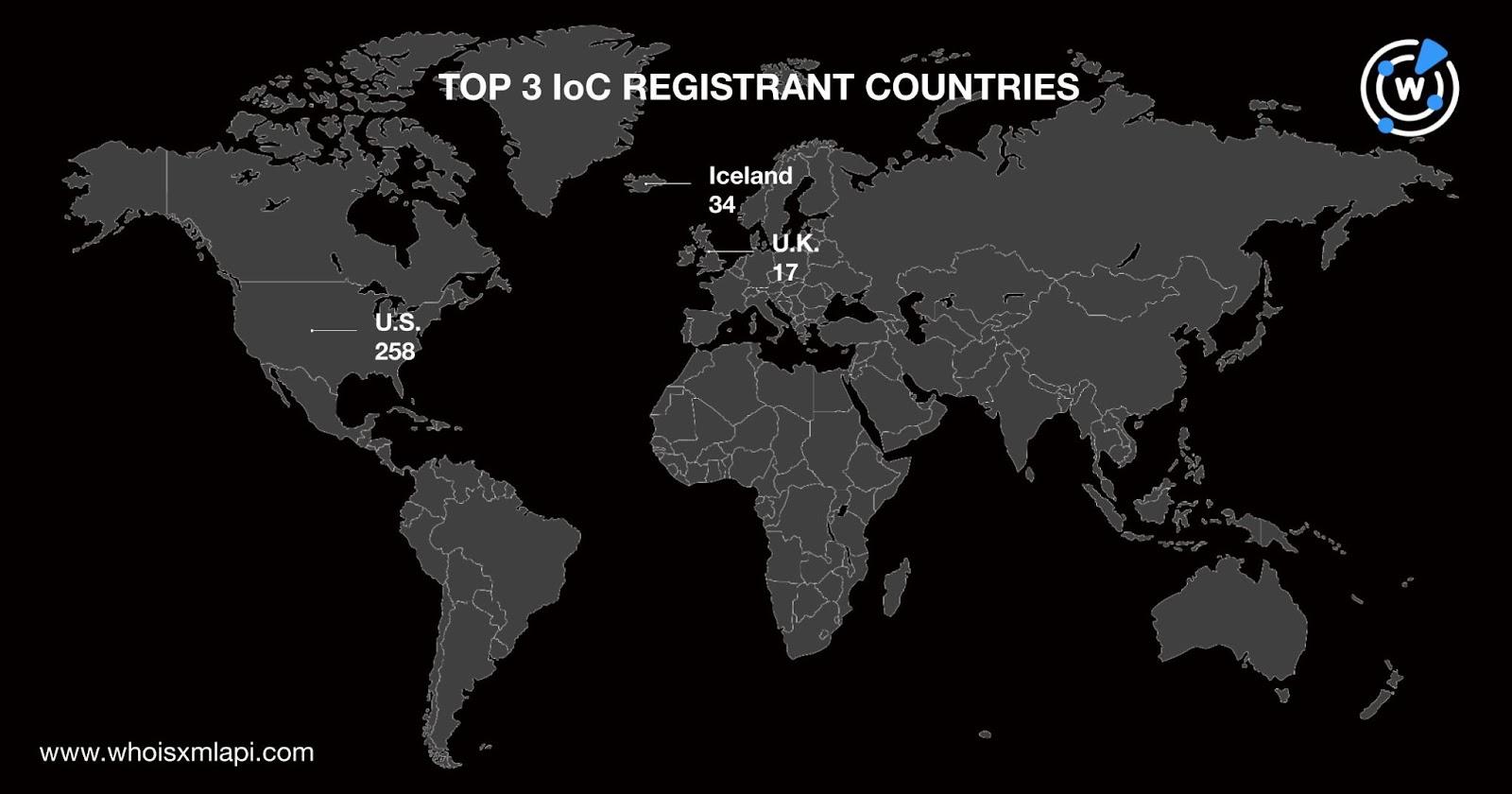
The U.S. (258 IoCs), Iceland (34 IoCs), and the U.K. (17 IoCs) were the domains’ top 3 registrant countries. A total of 125 IoC-linked domains didn’t have public registrant country information while the remaining 97 were spread across 34 other countries.
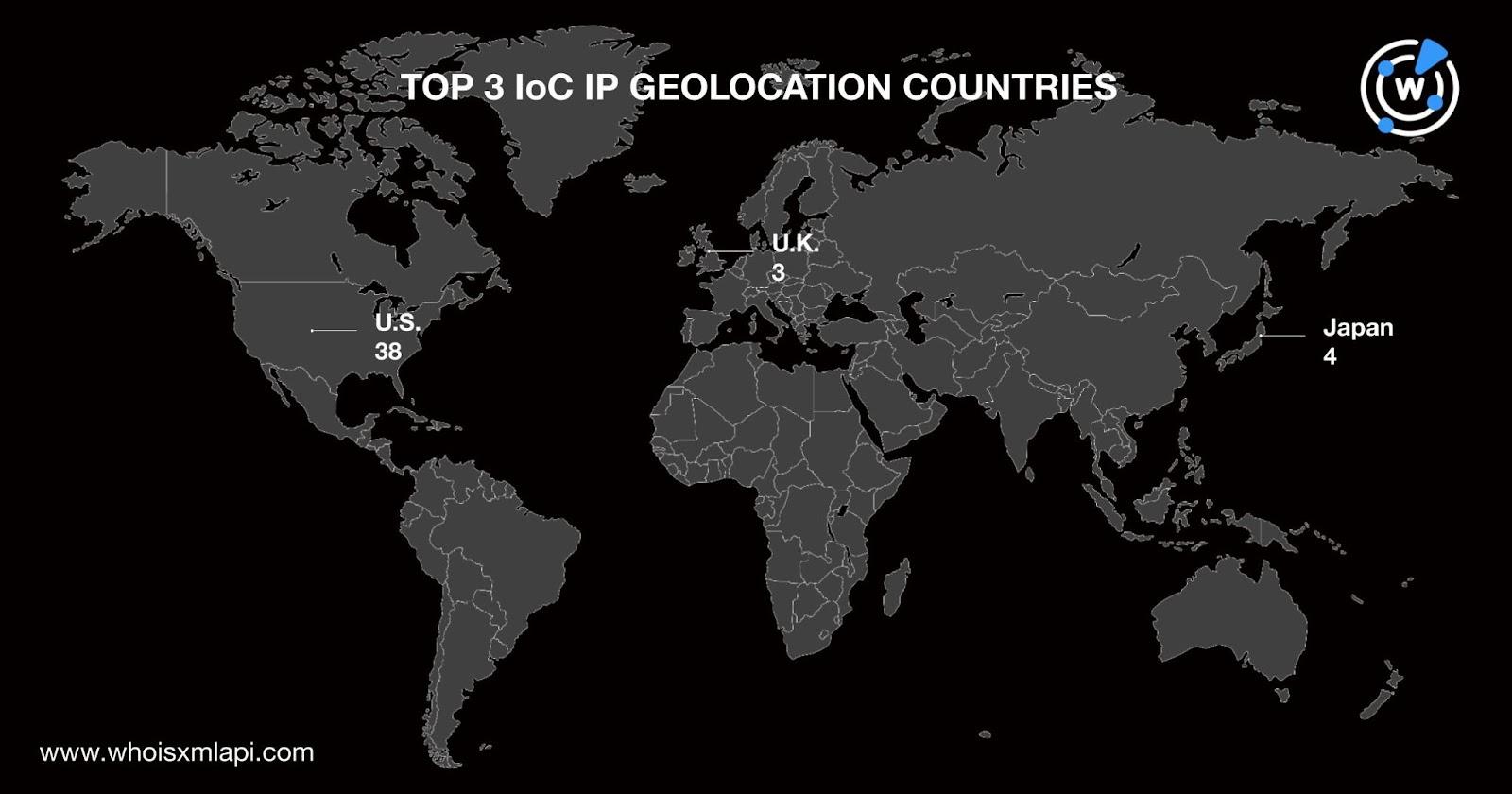
Next, we subjected the 54 IP addresses to a bulk IP geolocation lookup that uncovered these results:
Thirty-eight of the IP address IoCs originated from the U.S., coincidentally the domain IoCs’ top registrant country. Japan and the U.K. rounded out the top 3 IP geolocation countries, accounting for four and three of the IoCs, respectively. The nine remaining IoCs were spread across six other countries.
To uncover unreported potentially connected artifacts, we expanded the current list of IoCs published on Alienvault OTX.
WHOIS history searches for the 531 domains revealed that 495 of them had publicly available registrant email addresses in their historical WHOIS records.
Using these as reverse WHOIS search terms led to the discovery of 697 email-connected domains, three of which turned out to be malicious based on a bulk malware check. One, which led to a blank page, proved interesting in that it contained a popular URL shortening service’s brand name—go-bitly[.]com—even if a WHOIS lookup showed that it couldn’t be publicly attributed to the company.
Next, DNS lookups for the 531 domains led to the discovery of 244 IP addresses that weren’t included in the current IoC list, 33 of which turned out to be malicious based on malware checks.
We then subjected the 298 IP addresses—54 that have already been identified as IoCs and 244 additional IP resolutions—to reverse IP lookups. We found that 152 of them were seemingly dedicated hosts. Altogether, they hosted 5,232 domains that weren’t part of the current IoC list. Nine of the IP-connected domains turned out to be malicious based on a bulk malware check.
Two of the malicious IP-connected domains continued to host live content based on screenshot lookups.
Our BlackNet RAT IoC list expansion analysis led to the discovery of 6,173 potentially connected artifacts, including 45 malicious web properties—33 IP addresses and 12 domains.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byRadix
