


|
||
|
||
APT29, believed to be an espionage group from Russia, became known for launching targeted attacks against organizations in Ukraine. But over the course of investigating the threat group, Mandiant discovered that it may have a hand in cybercriminal operations, specifically phishing, as well.
As far as security researchers could tell, APT29’s cybercriminal arm went by the moniker “NOBELIUM,” which has been trailing its sights on Microsoft’s cloud-based products. An in-depth investigation on the threat identified 48 indicators of compromise (IoCs)—41 domains and seven IP addresses to date.
The WhoisXML API research team expanded this list of IoCs in search of more artifacts potentially connected to APT29’s phishing operation arm NOBELIUM and uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We started our DNS deep dive into APT29’s phishing operation by looking for more information on the NOBELIUM IoCs.
A bulk WHOIS lookup for the 41 domains identified as IoCs led to these discoveries:
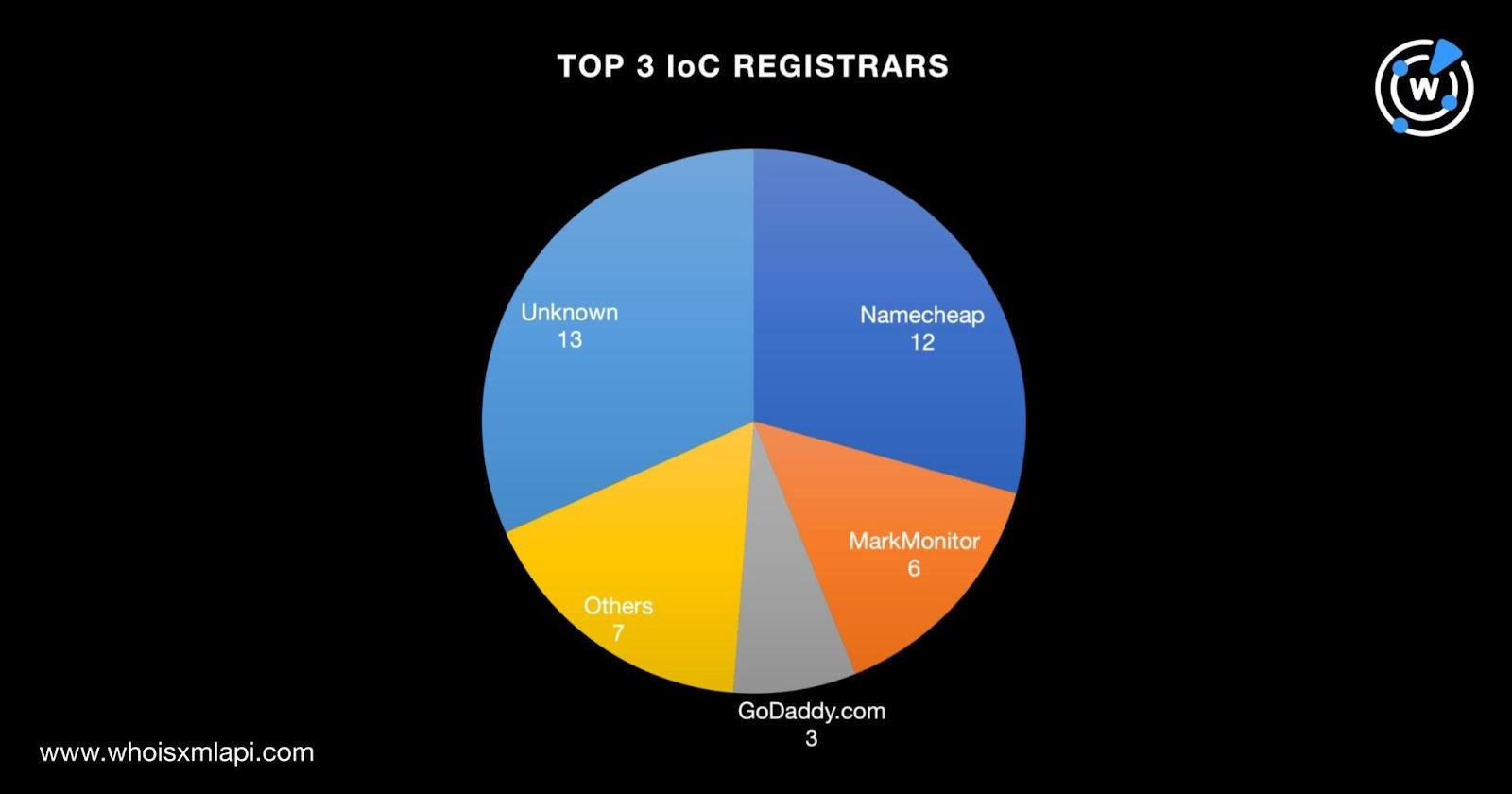
A bulk IP geolocation lookup, meanwhile, for the seven IP addresses identified as IoCs led to these findings:
In a bid to find other potential NOBELIUM artifacts, we ran historical WHOIS searches on the 41 domains identified as IoCs and found that the registrants of 22 of them registered 22 other domains that aren’t part of the current IoC list.
We then subjected them to DNS lookups that uncovered 13 unreported IP addresses to which some of the domains identified as IoCs resolved. Three of them hosted several domains as shown in the table below.
| 199[.]36[.]158[.]100 | 34[.]120[.]160[.]131 | 3[.]64[.]163[.]50 |
|---|---|---|
| cdnappservice[.]web[.]app logicworkservice[.]web[.]app humanitarian-forum[.]web[.]app security-updater[.]web[.]app supportcdn[.]web[.]app | eventbrite-com-default-rtdb[.]firebaseio[.]com cdnappservice[.]firebaseio[.]com humanitarian-forum-default-rtdb[.]firebaseio[.]com security-updater-default-rtdb[.]firebaseio[.]com supportcdn-default-rtdb[.]firebaseio[.]com | aimsecurity[.]net stsnews[.]com |
Ten of the 13 IP resolutions also turned out to be malicious based on malware checks. In fact, nine of them were reported to AbuseIPDB several times as shown below.
| IP RESOLUTION | NUMBER OF TIMES REPORTED ON ABUSEIPDB |
|---|---|
| 199[.]36[.]158[.]100 | 204 |
| 3[.]64[.]163[.]50 | 72 |
| 64[.]91[.]249[.]20 | 3 |
| 35[.]205[.]61[.]67 | 20 |
| 162[.]55[.]100[.]32 | 68 |
| 208[.]91[.]197[.]46 | 5 |
| 13[.]248[.]169[.]48 | 19 |
| 23[.]227[.]38[.]32 | 52 |
| 76[.]223[.]54[.]146 | 13 |
Reverse IP lookups for the seven IoCs and additional IP addresses showed that:
NOBELIUM also reportedly targeted Microsoft’s cloud-based products. We sought to find if potential threat vectors, particularly domains and subdomains created this year, already exist in the DNS. We used these strings as Domains & Subdomains Discovery search terms based on a list of five of the company’s cloud services.
| MICROSOFT CLOUD SERVICE | SEARCH TERM |
| Microsoft 365 | microsoft365 |
| Microsoft OneDrive | microsoftonedrive |
| Microsoft Dynamics 365 | microsoftdynamics365 |
| Microsoft Teams | microsoftteams |
| Microsoft Intune | microsoftintune |
We found 236 domains and 341 subdomains containing the five strings listed above. Take a look at their volume breakdown below.
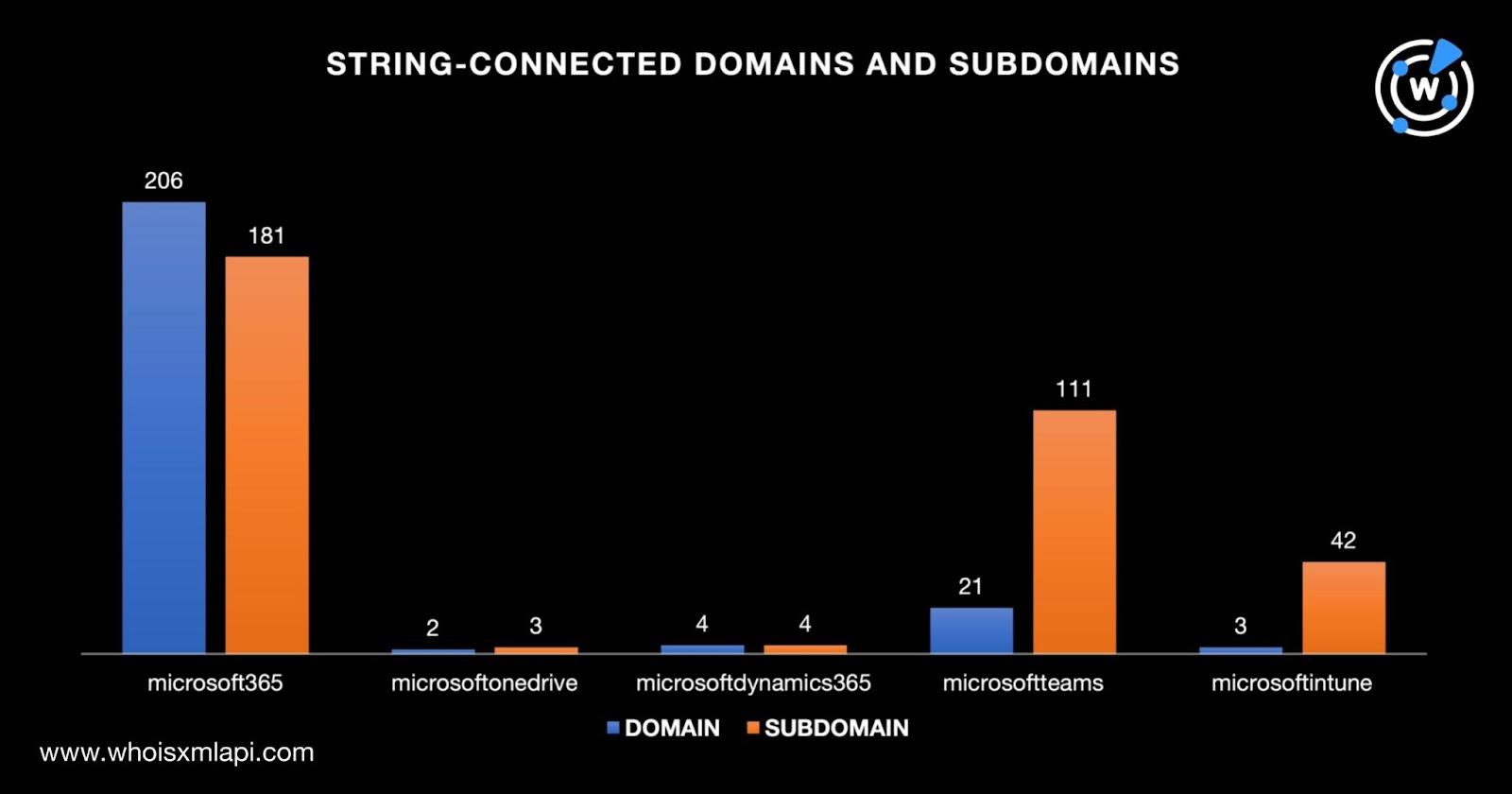
A bulk WHOIS lookup for the 236 string-connected domains showed that only three were Microsoft-owned. They had the same registrant organization as the company’s official domain microsoft[.]com. A bulk malware check, meanwhile, revealed that five of them have already been categorized as malicious and, as expected, none of them belong to Microsoft despite bearing its name. And one of the malicious domains was currently up for sale.
A bulk WHOIS lookup, meanwhile, for the 341 string-connected subdomains showed that only three belonged to Microsoft based on their registrant organization. A bulk malware check showed that five of them were already classified as malicious and none were owned by the company. Four of them remained accessible—two led to index pages while the other two led to error pages.
Our expansion analysis of the APT 29-NOBELIUM IoCs led to the discovery of 1,034 potentially connected artifacts that could figure in future attacks. At least 20 of them may have or are already being used as threat entry points to date. Preventing access to them would be a good idea.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byVerisign
