


|
||
|
||
The Federal Bureau of Investigation (FBI) shut down BreachForums, a forum for English-speaking black hat hackers, on 21 March 2023, following the arrest of its owner Conor Brian Fitzpatrick. More recent reports, however, stated it’s back up under new management—that of hacking group ShinyHunters and original administrator Baphomet.
Threat researcher Dancho Danchev obtained 573 domains that belonged to several BreachForums members. The WhoisXML API research team expanded this list of indicators of compromise (IoCs) in an effort to obtain more information on their infrastructure. Our in-depth investigation led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
The first step we took to investigate the BreachForums IoCs Danchev collated was perform a bulk WHOIS lookup that provided these results:
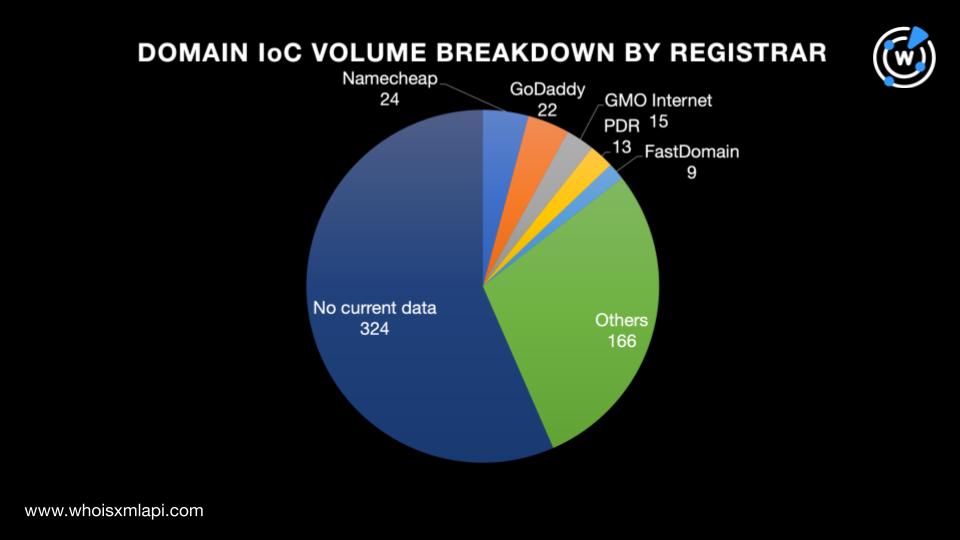
While 310 of the domains did not have retrievable creation dates, the remaining 263 with current WHOIS records were created between 1997 and 2023, with most, 72 to be exact, created in 2022.
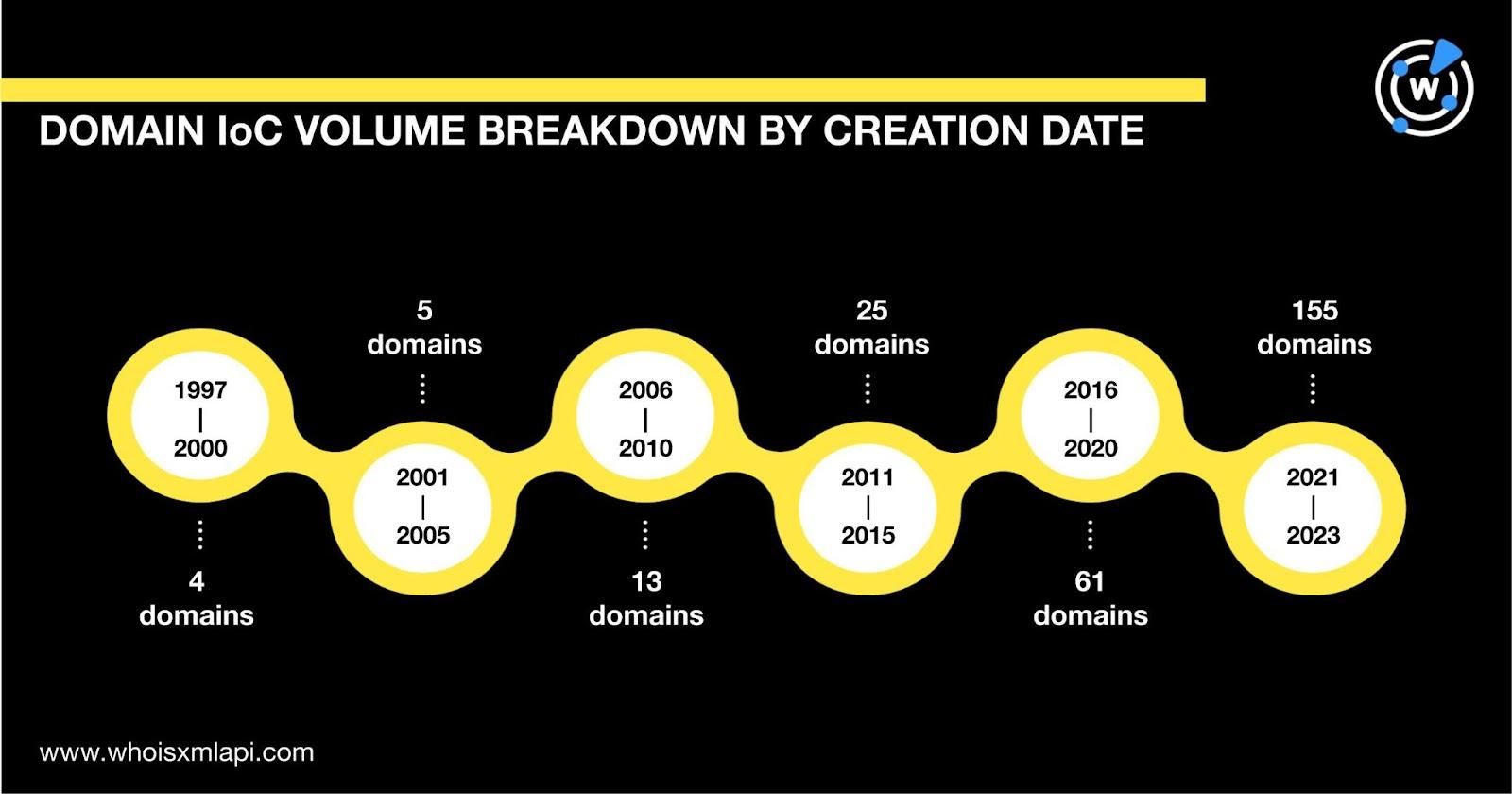
While 358 IoCs did not have retrievable public registrant country data, the remaining 215 with current WHOIS records were spread across 32 countries led by the U.S. (64 domains), Japan (17 domains), India (14 domains), France (12 domains), and China (10 domains).
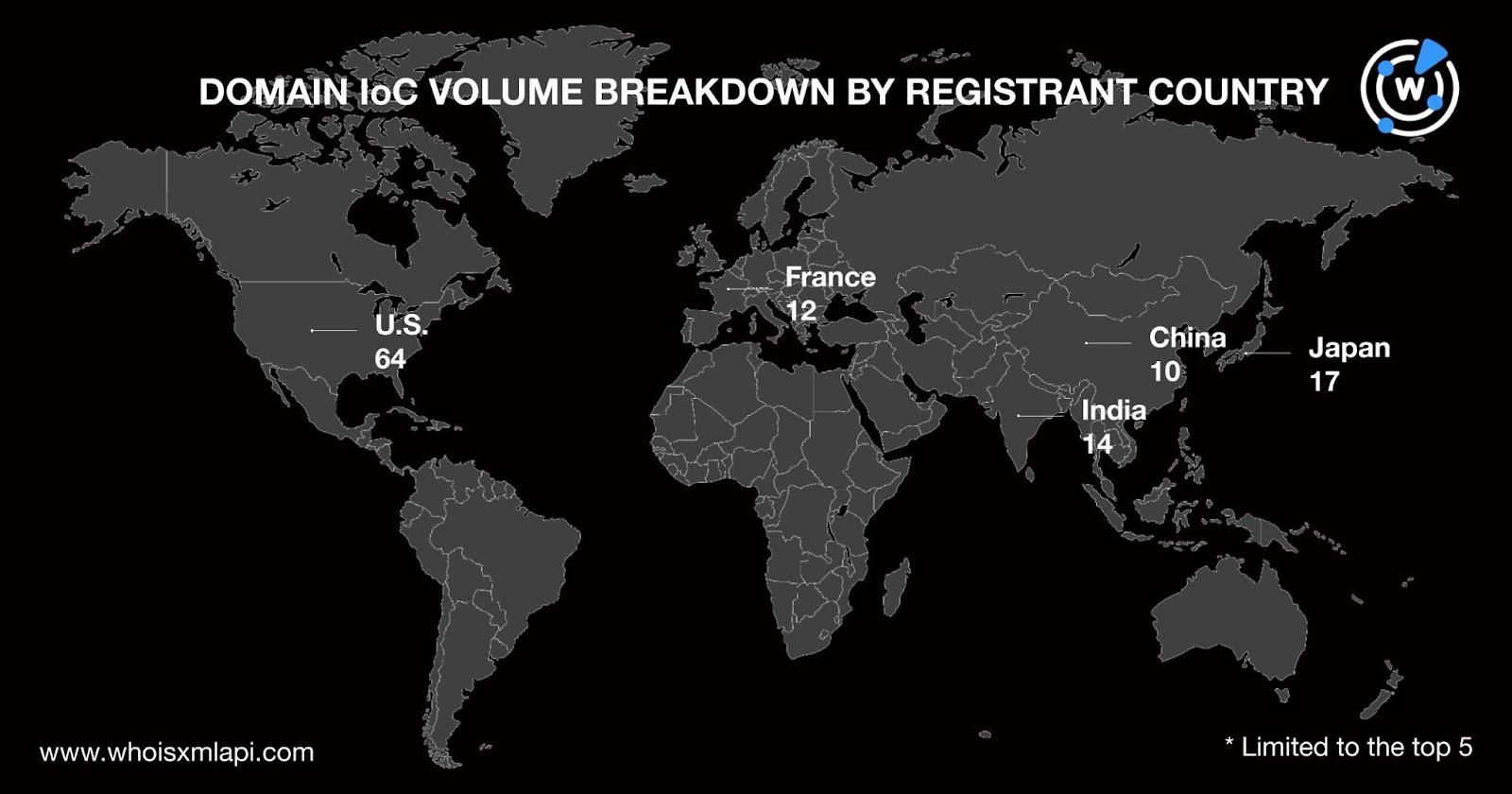
It is also interesting to note that the five most used top-level domain (TLD) extensions among the 573 domains identified as IoCs were .com (305 domains), .us (66 domains), .net (23 domains), .science (22 domains), and .org (19 domains). The remaining 138 domains sported 29 other TLD extensions.
To know more about the BreachForums members’ cybercriminal infrastructure, we subjected the 573 domains identified as IoCs to an expansion analysis.
A closer look at the IoCs with retrievable WHOIS records showed that several had public registrant email addresses (limited to those used to register 50 or fewer domains each), which were shared by 12 additional domains based on reverse WHOIS searches. One of the email-connected domains—carmainten[.]com—turned out to be malicious based on a bulk malware check.
Next, we conducted DNS lookups for the 573 domains identified as IoCs and found that they resolved to 253 IP addresses, one of which—137[.]184[.]161[.]21—turned out to be malicious based on malware checks.
A bulk IP geolocation lookup for the 253 IP addresses showed that:

Three of the top 5 IP geolocation and registrant countries—China, Japan, and the U.S.—coincided with one another.
While one of the IP addresses did not have public Internet service provider (ISP) data, the remaining 252 were spread across 87 ISPs led by Cloudflare (61 IP addresses), Amazon (15 IP addresses), Web-hosting (11 IP addresses), Unified Layer (nine IP addresses), and Google and Hostinger (eight IP addresses each).
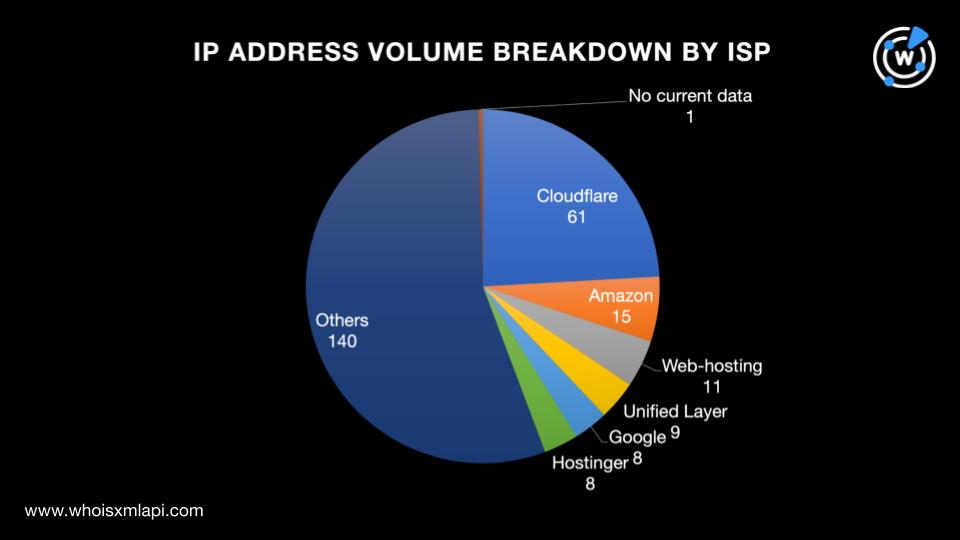
The lookups also allowed us to limit our study to the 60 dedicated IP addresses that played host to 3,884 domains based on reverse IP lookups. Twenty-two of the IP-connected domains turned out to be malicious based on a bulk malware check. All but two of the malicious domains remained accessible as of this writing.
Checks on Domains & Subdomains Discovery showed that 169 of the strings that appeared in the domains identified as IoCs were also present in 9,588 other domains. Thirty of them turned out to be malicious based on a bulk malware check.
Further scrutiny of the domains identified as IoCs allowed us to see that 23 of them contained six popular brand names—Amazon, Facebook, Gmail, iPhone, Tesla, and Yandex. It is interesting to note that these brand names also appeared in 127 IP- and string-connected domains. We identified some samples in the table below.
| Famous Brand Name That Appeared a Text String | Domains Identified as IoCs | IP-Connected Domains | String-Connected Domains |
|---|---|---|---|
| Amazon | 2verification-amazon-fr[.]fr | 2amazonyrosa[.]in | 5amazon-firebiz[.]nom[.]za |
| 1facebooksexlist[.]com | |||
| Gmail | 17f-gmail[.]com | 4account-my-mail-gmail[.]com | 71albagulizia-gmail[.]com |
| iPhone | 1findmyiphone-view[.]com | 1iphone-15.com[.]ua | 1iphonebiz[.]com[.]br |
| Tesla | 1teslamemorial[.]science | 1teslamemorial[.]biz[.]at | |
| Yandex | 1yandex-toloka[.]ru[.]com | 42x0br[.]storage[.]yandexcloud[.]net |
None of the 127 brand-containing domains we uncovered could be publicly attributed to any of the six companies cited above based on their WHOIS records. And based on screenshot lookups, 101 of them remained accessible as of this writing even though many led to error or index pages.
Finally, we sought to find out how many of the 13,484 domains potentially connected to the threat by email address, IP address, or string usage shared the five TLD extensions the threat actors most abused based on our further scrutiny of the IoCs earlier. We found that:
Take a look at the comparison between the TLD extension usage among the domains identified as IoCs and connected domains below.
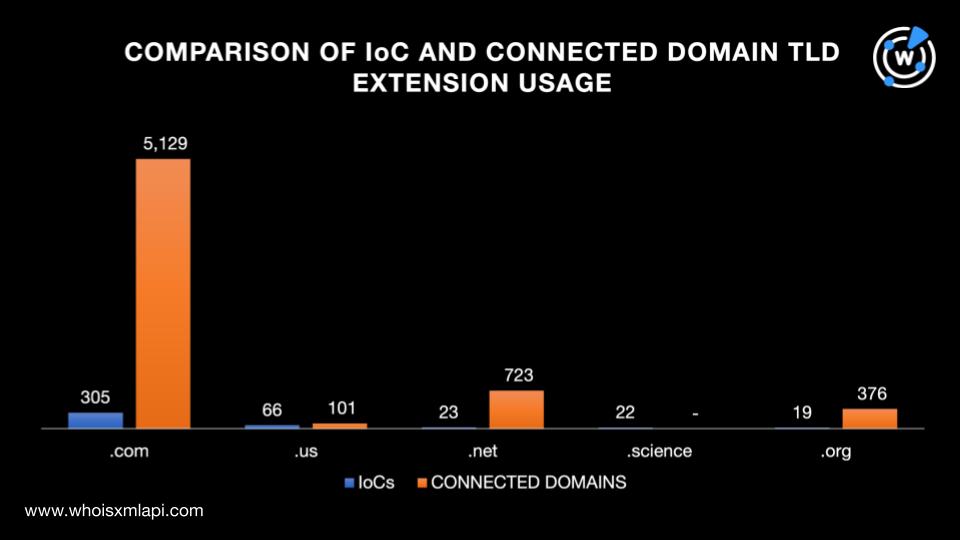
Our analysis and expansion of the list of BreachForums domains allowed us to uncover 13,484 potentially connected web properties, 53 of which turned out to be malicious based on malware checks. We also identified commonalities between the domains identified as IoCs and the connected domains, such as that .com seemed to be the most abused TLD extension.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byRadix
