


|
||
|
||
Carding has been around since the 1980s but has evolved to the point that even less experienced cybercriminals can now launch campaigns. How? Via the carding forums that riddle the Web these days.
Security researcher Dancho Danchev recently amassed 220 email addresses believed to belong to carders. The WhoisXML API team subjected the indicators of compromise (IoCs) to an expansion analysis to identify potentially connected artifacts and found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
As a first step, we subjected the 220 email addresses identified as IoCs to advanced historical reverse WHOIS searches. We found that 97 of the 220 email addresses were recently used to register 72,197 domains.
We limited our study to the 76 email addresses used to register 50 domains at most. That left us with a sample of 865 email-connected domains.
A bulk malware check showed that 157 of them were malware-laden. A closer inspection of the malicious email-connected domains showed that 75 remained live—49 led to live pages, 44 of which were carding-related based on screenshot lookup results; 21 led to parked pages; and five led to blank pages. Take a look at sample screenshots of the live carding pages below.
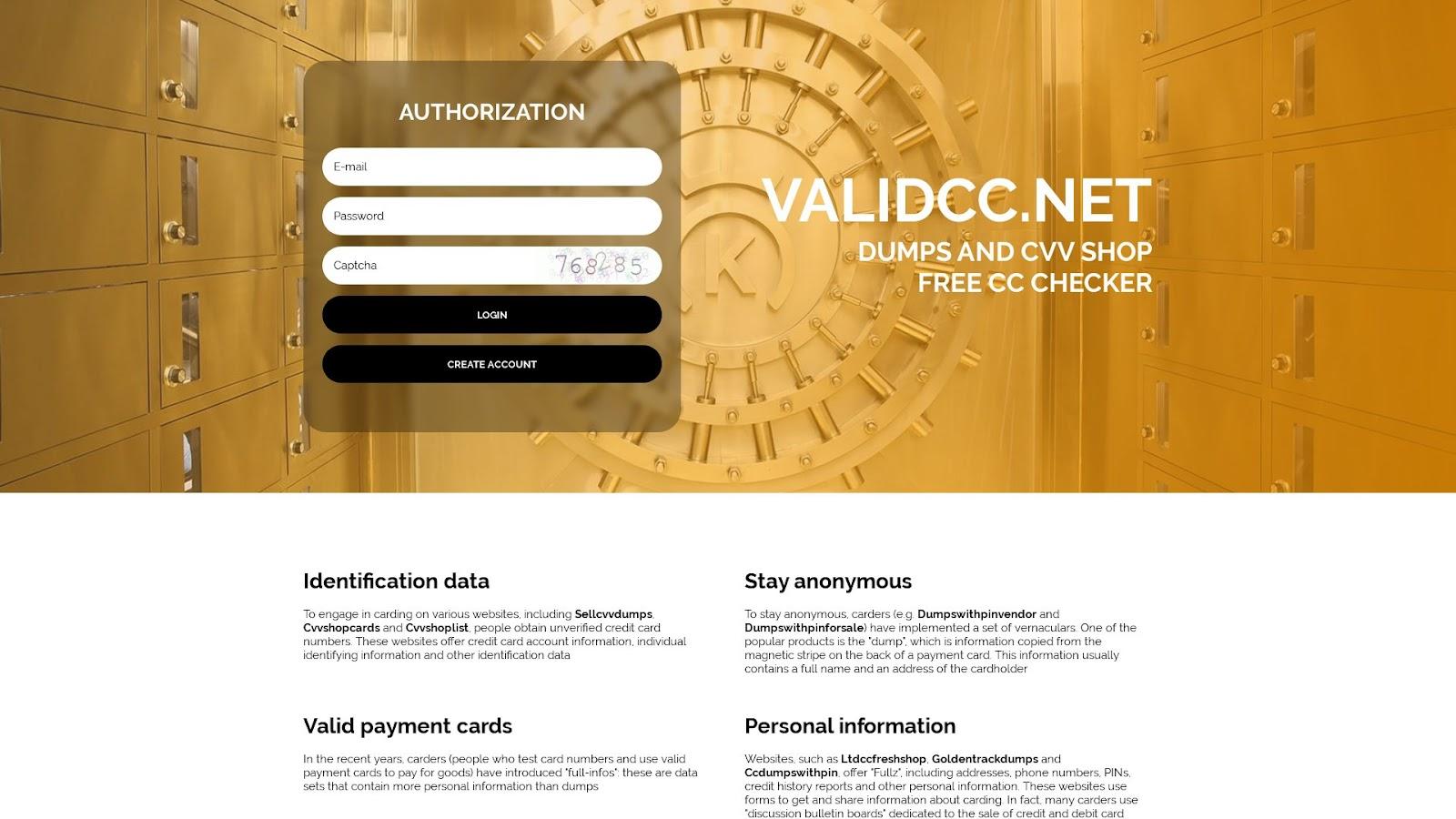
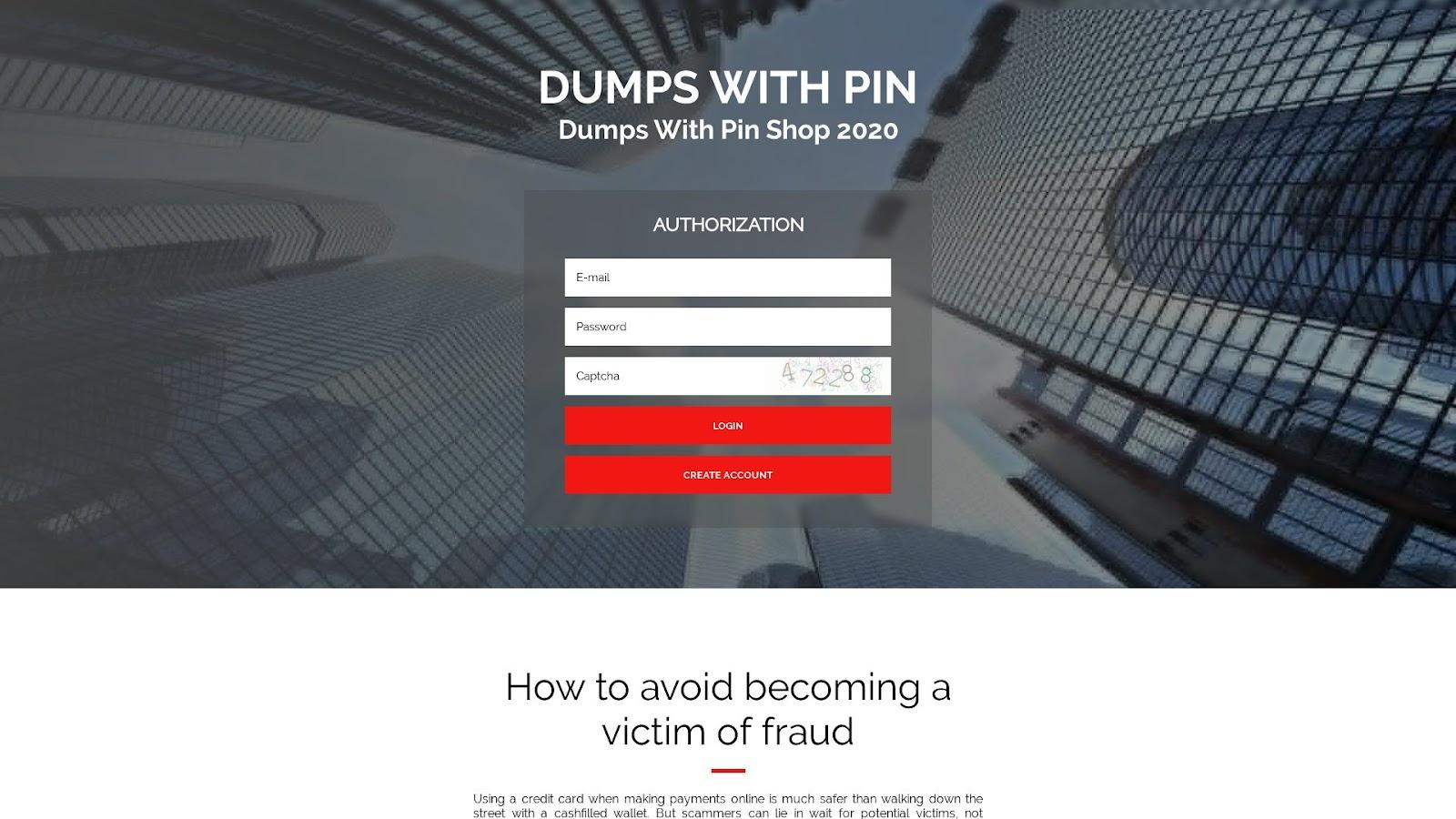
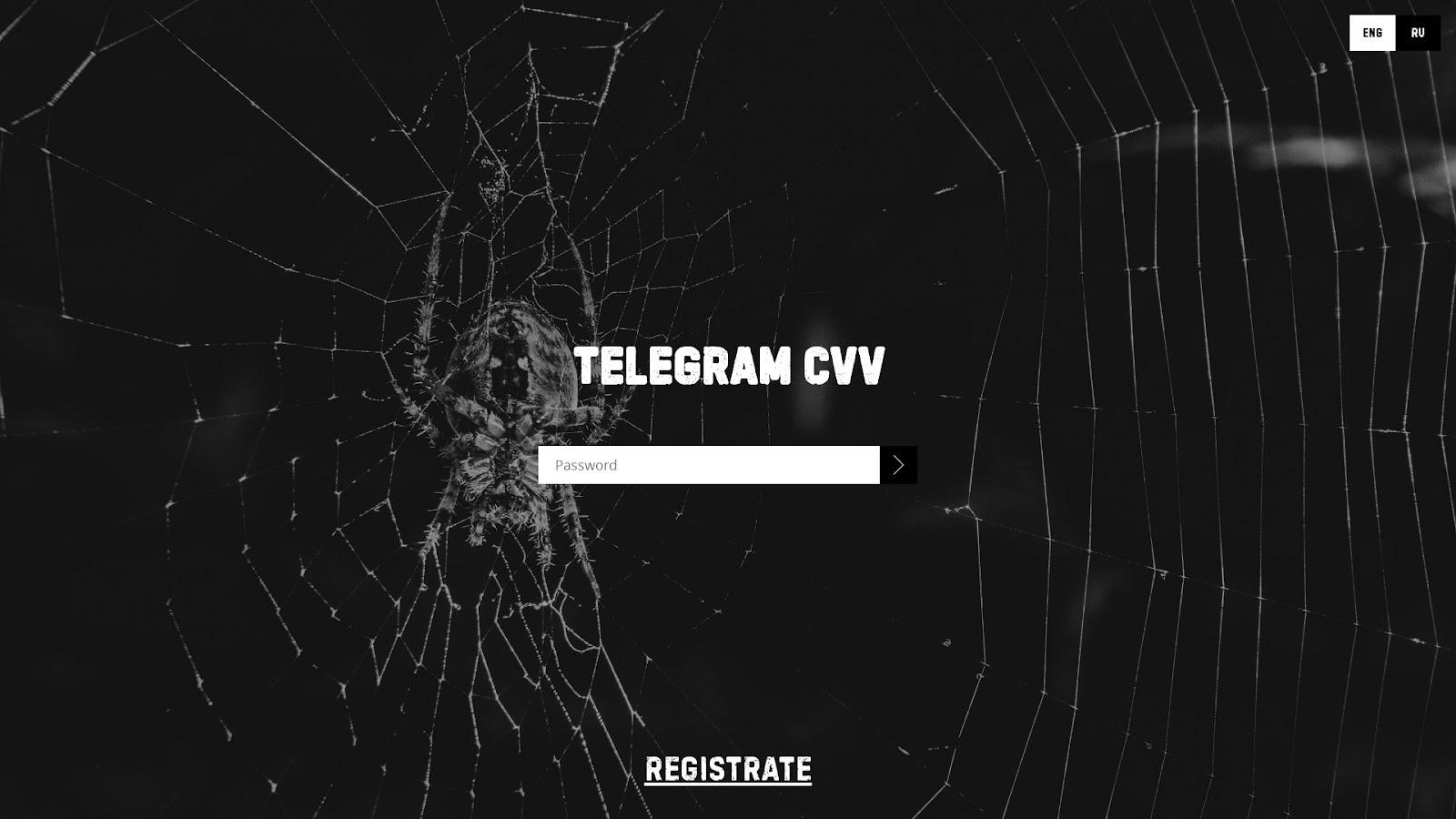
Another email-connected domain led to a carding forum.

Our analysis also allowed us to identify 12 text strings usually associated with carding that appeared in the email-connected domains. Note that some domains can have more than one string in them. The chart below shows a detailed email-connected domain volume breakdown per carding-related text string.
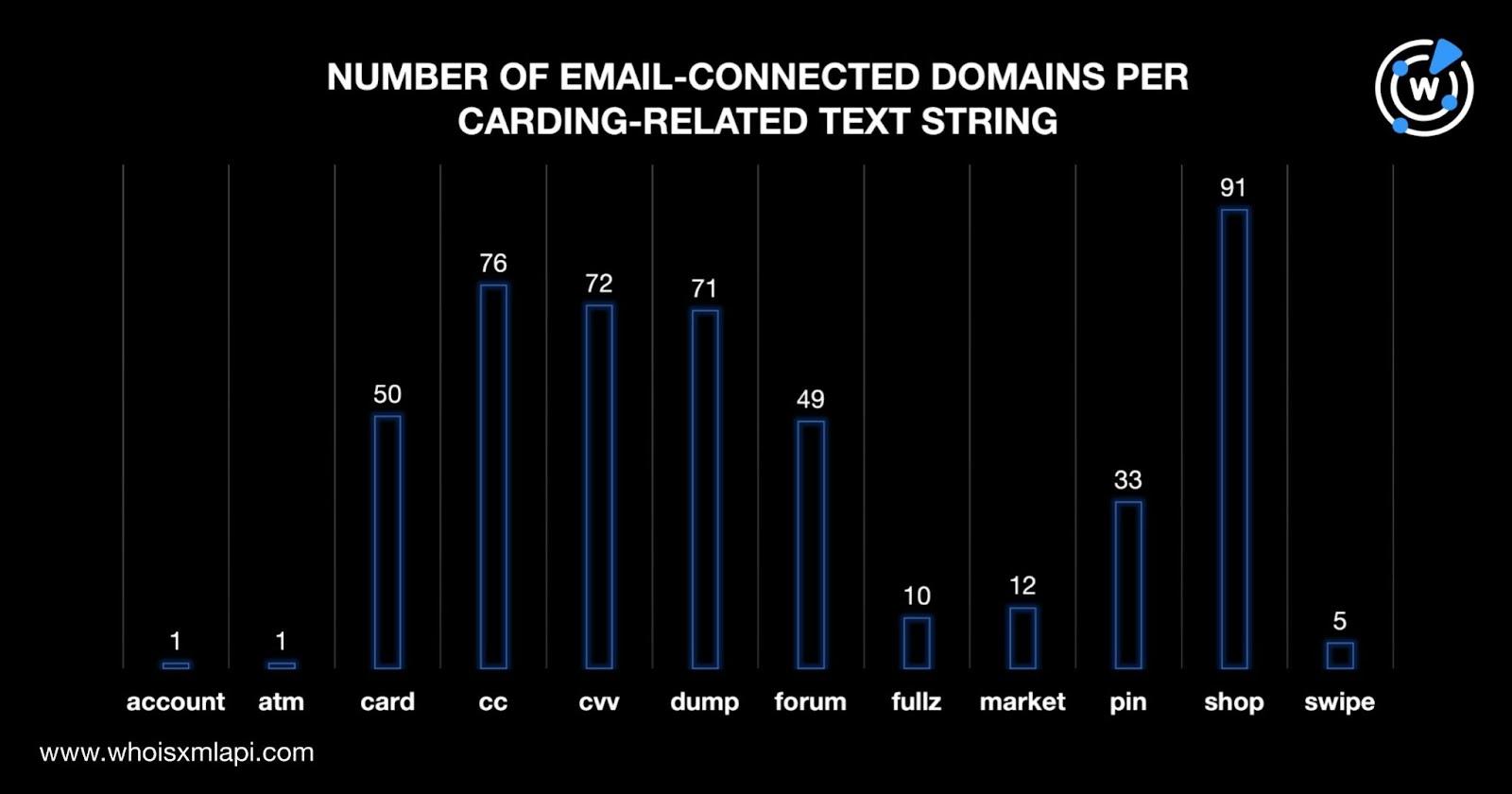
Shop topped the list in terms of text string usage, followed by cc (short for “credit card”) and cvv. Note that these numbers do not include domains with misspelled variants of the strings we identified.
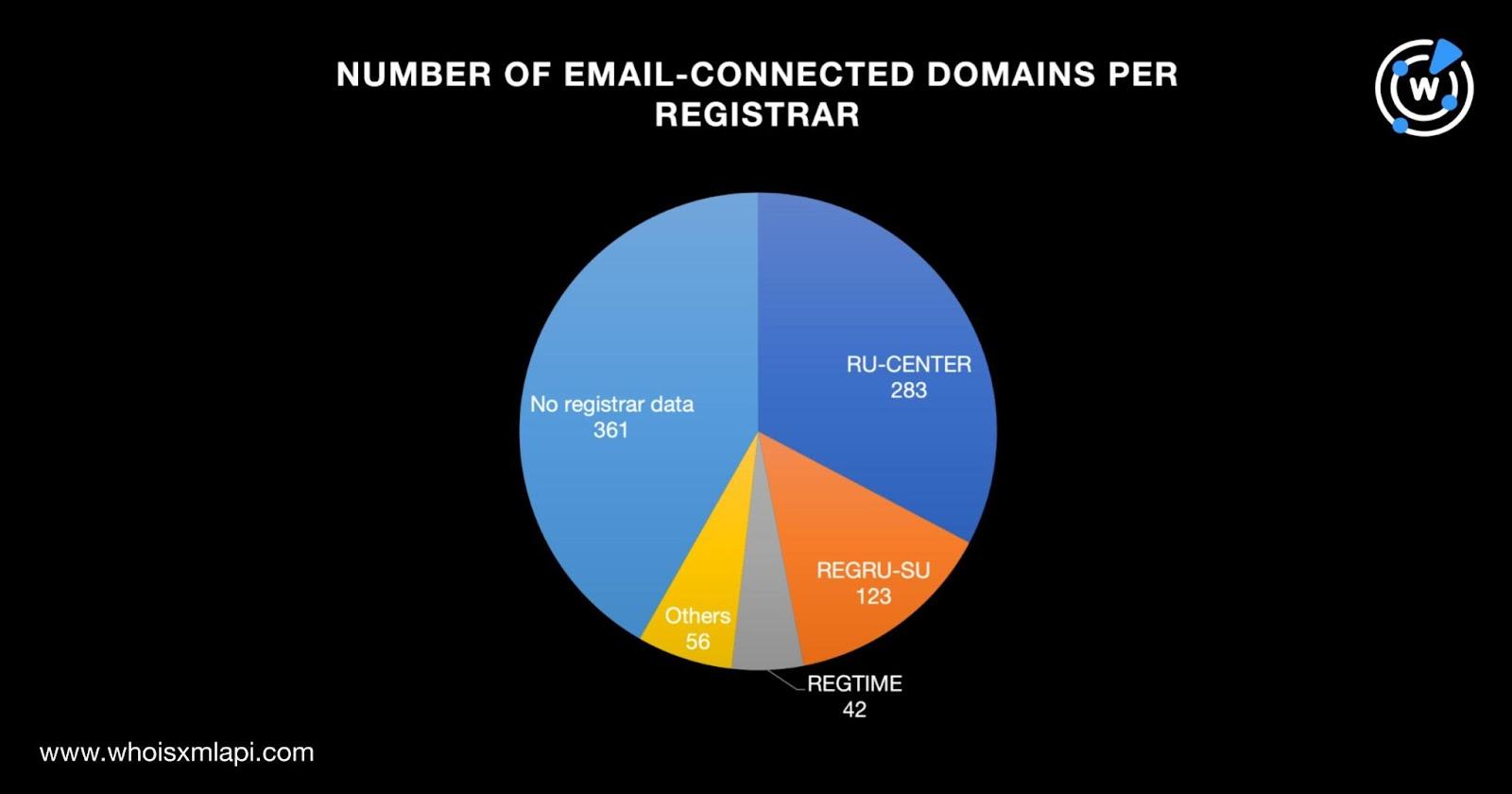
Next, we subjected the 865 email-connected domains to a bulk WHOIS lookup and found that the top 3 registrars were RU-CENTER (283 domains), REGRU-SU (123 domains), and REGTIME (42 domains). While 361 domains did not have publicly available registrar data, the remaining 56 were spread across 20 other registrars.
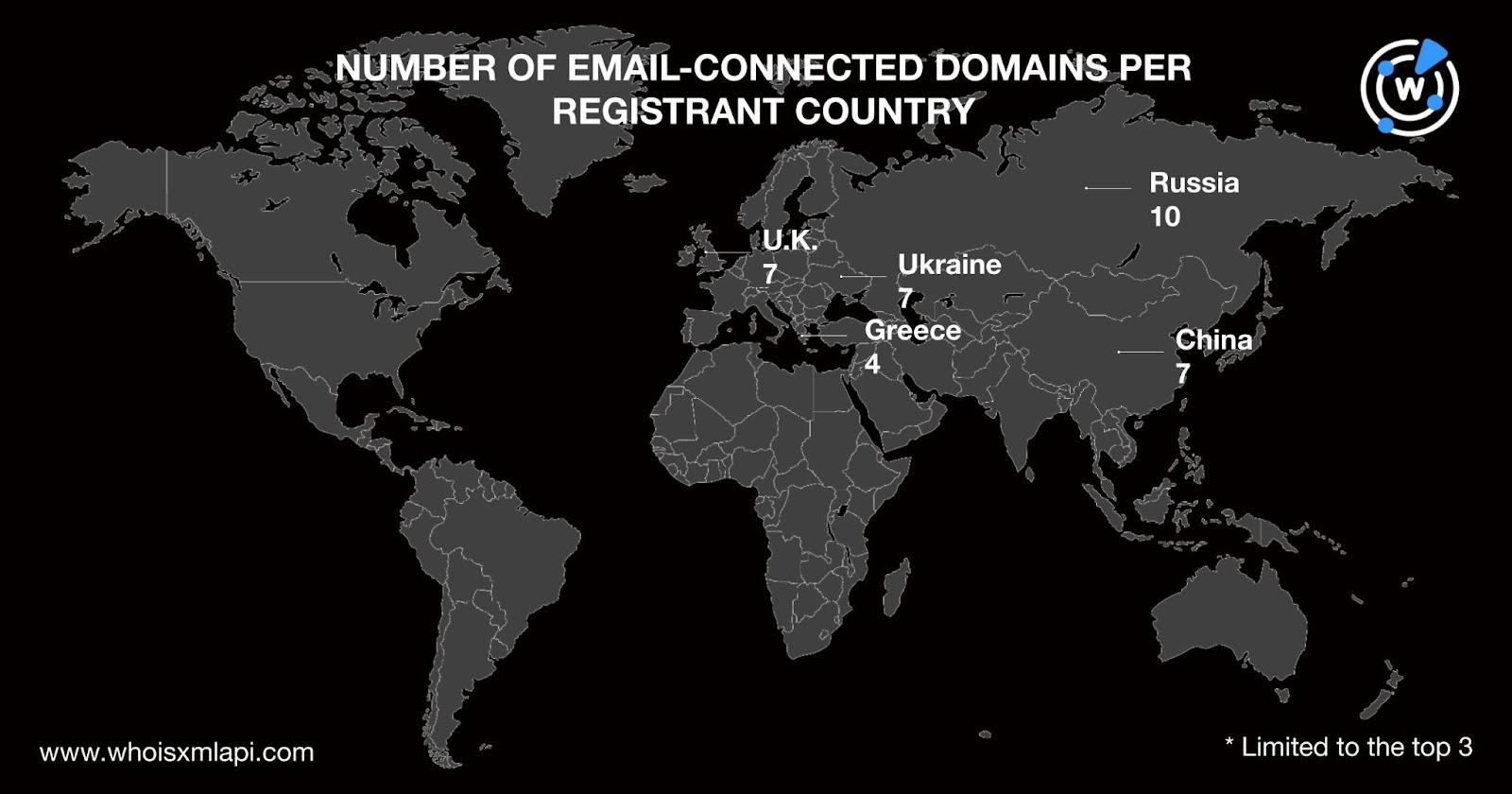
Russia (10 domains) led the pack in terms of registrant country. China, Ukraine, and the U.K. (seven domains each) tied in second place. Greece (four domains) rounded out the top 3 registrant countries. While 823 email-connected domains did not have publicly available registrant country data, the remaining seven domains were registered in four other countries.
To gather more potentially connected artifacts, we ran DNS lookups for the 865 email-connected domains and found that 602 had active IP resolutions. After removing duplicates, we were left with 361 IP addresses—211 IPv4 and 150 IPv6 addresses.
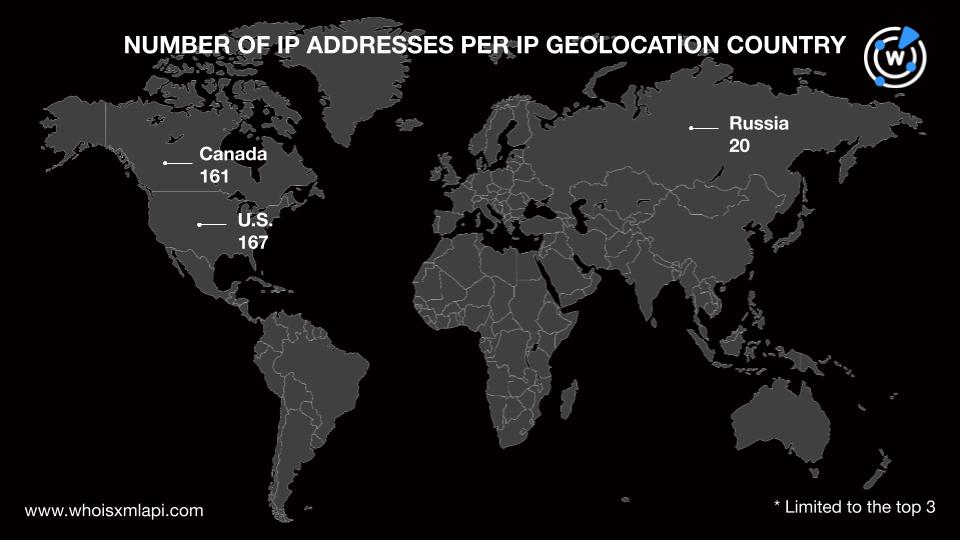
A bulk IP geolocation lookup for the 361 IP addresses showed that the top 3 geolocation countries were the U.S. (167 IP addresses), Canada (161 IP addresses), and Russia (20 IP addresses). The remaining 13 IP addresses were spread across six other countries.
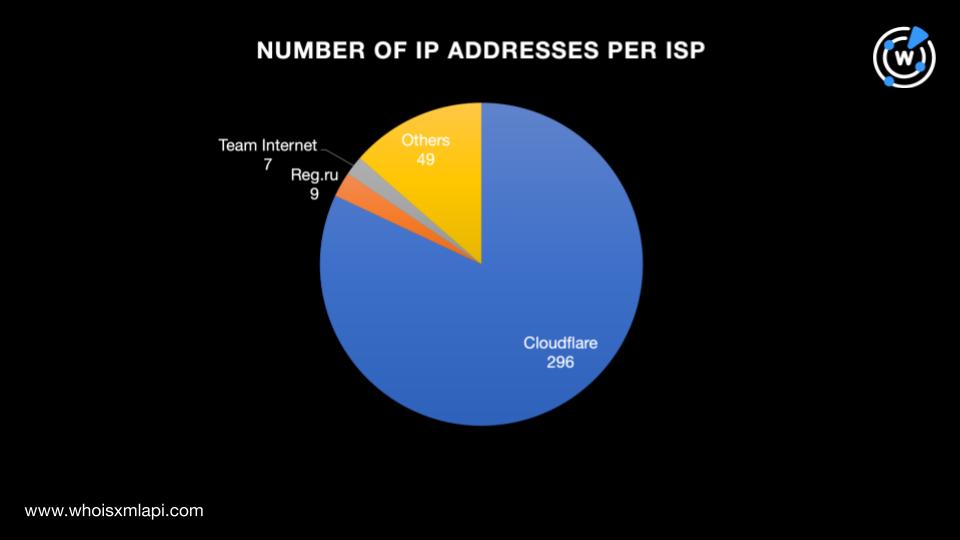
We also found that the 361 IP addresses were distributed among 34 Internet service providers (ISPs) led by Cloudflare (296 IP addresses), Reg.ru (nine IP addresses), and Team Internet (seven IP addresses). The remaining 49 IP addresses were spread across 31 other ISPs.
Next, we limited the scope of our analysis to the 211 IPv4 addresses only. Reverse IP lookups for the addresses revealed that 192 were shared, 14 were seemingly dedicated, and five did not currently host domains. To ensure that we obtain artifacts that are as closely related to the threat as possible, we further limited the sample to the seemingly dedicated IP addresses only.
The 14 IP addresses hosted 531 domains. After removing duplicates and domains identified as email-connected earlier, we were left with 489 IP-connected domains. A bulk malware check for the domains showed that two were malware-laden. Both malicious IP-connected domains remained online though none of them seemed related to carding.
As with the email-connected domains, we determined how many of the 211 IP-connected domains had the same 12 carding-related text strings. Take a look at the detailed breakdown below.
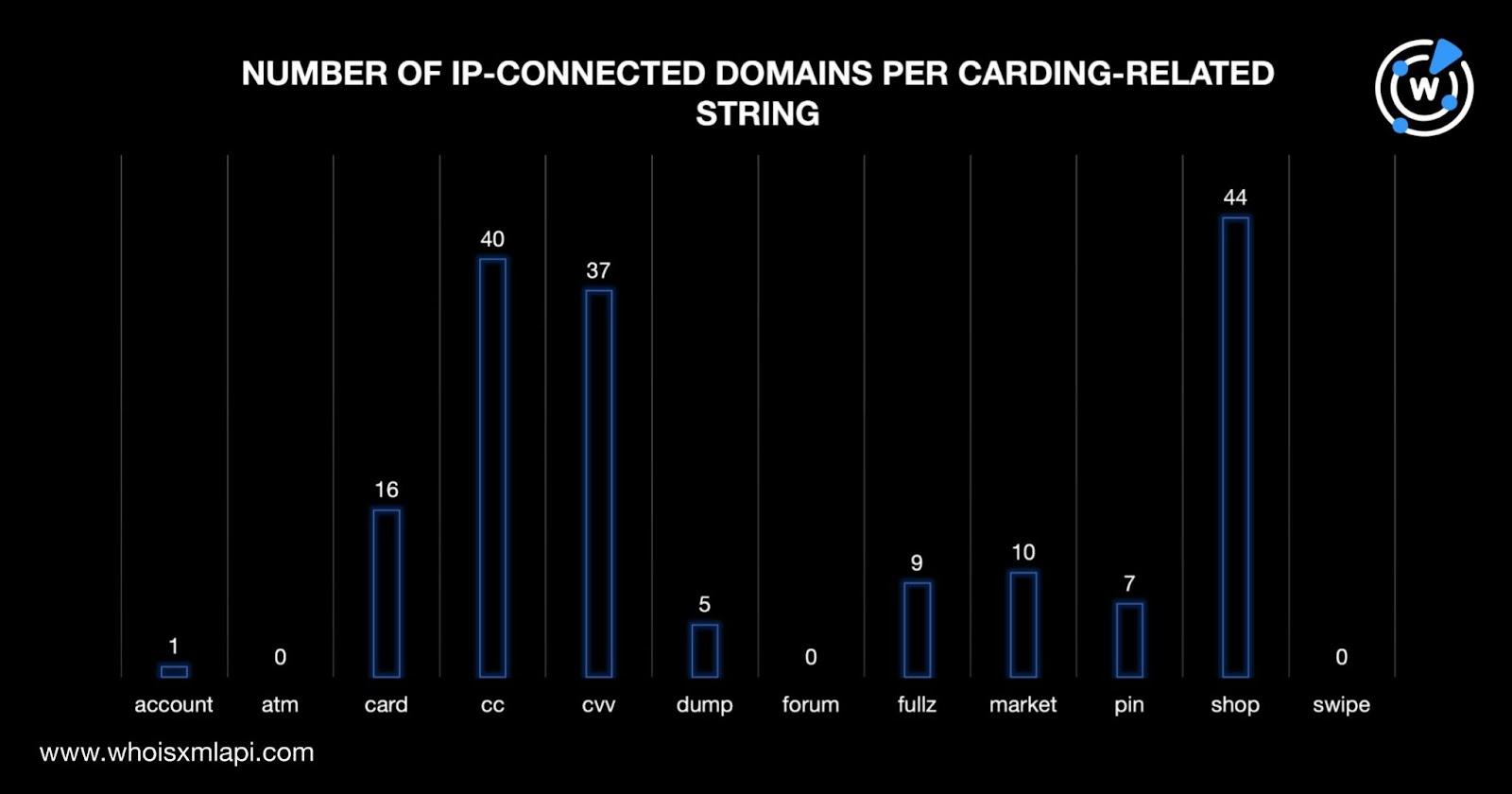
Shop also topped the list in terms of IP-connected domain text string usage, followed by cc and cvv, consistent with the results for the email-connected domains.
Our DNS deep dive into the 220 email addresses identified as carding IoCs led to the discovery of 1,715 connected domains and IP addresses in total. Malware checks also classified 159 of the newly discovered connected artifacts as malicious.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byRadix
