


|
||
|
||
Rogue bulletproof hosts are part and parcel of the cybercriminal market that is hidden deep underground. Without means to easily evade detection, attribution, and incarceration, many of today’s cybercriminals would not be able to continue their malicious operations.
In our constant bid to make the Internet more transparent and safer, our threat researcher Dancho Danchev recently collated 308 domains believed to belong to rogue bulletproof hosting service providers, which the WhoisXML API research team expanded to identify potentially connected web properties.
Our DNS deep dive into the threat led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
As the first step in our in-depth analysis of the rogue bulletproof hosting services, we subjected the 308 domains identified as IoCs to a bulk WHOIS lookup that led to these discoveries:
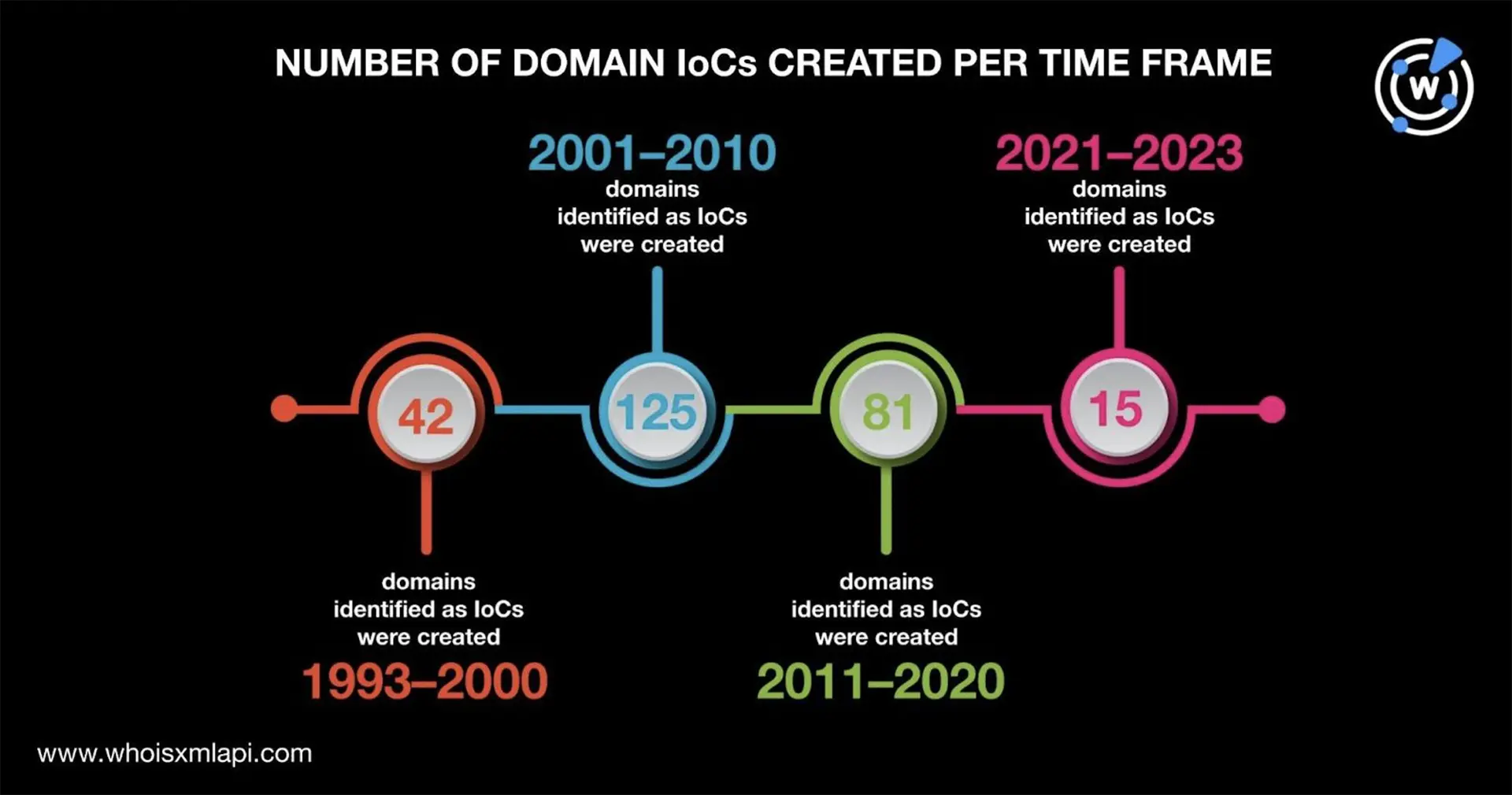
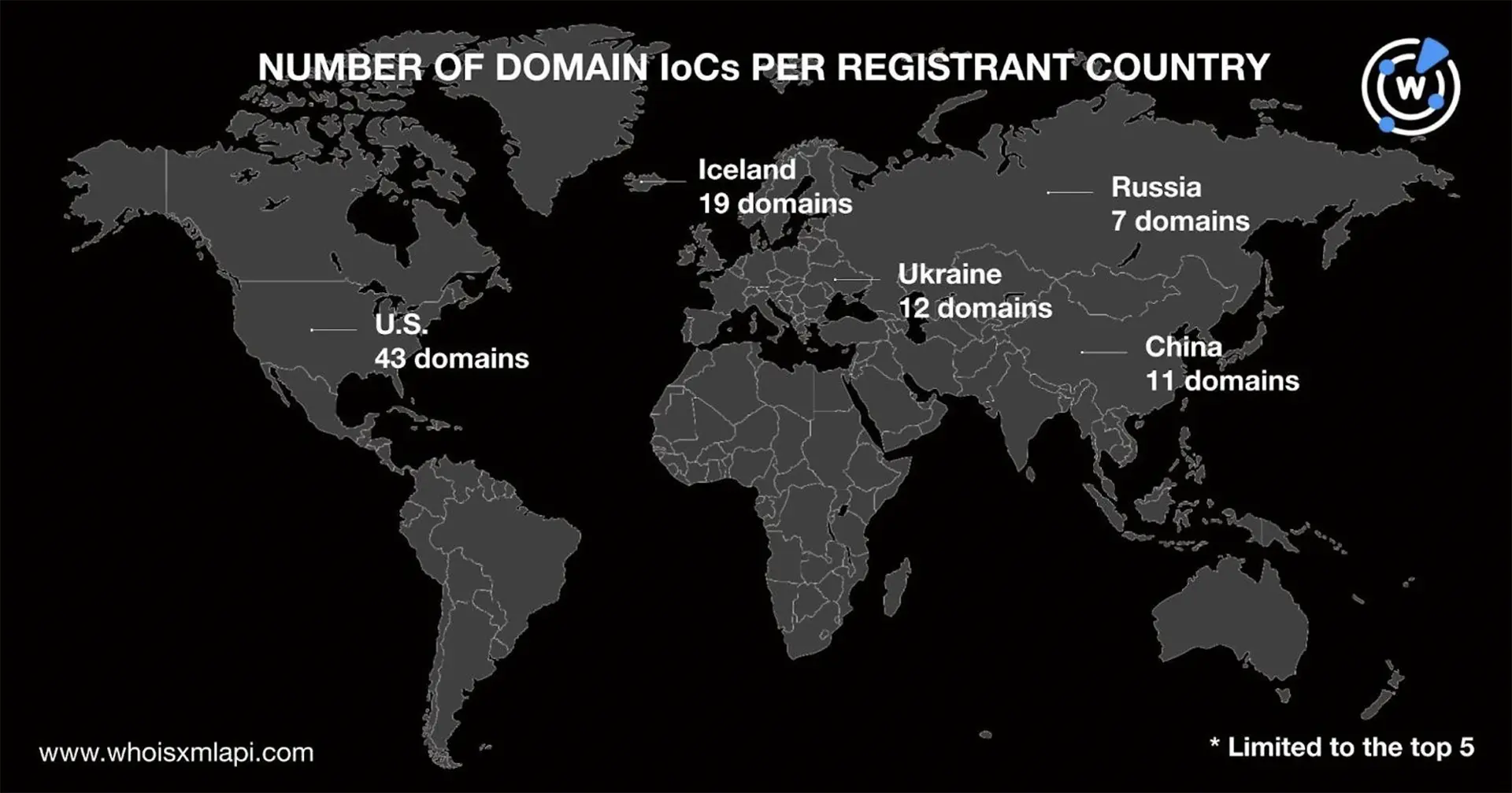
Only 183 domains had public registrant country information in their current WHOIS records. The U.S. (43 domains), Iceland (19 domains), Ukraine (12 domains), China (11 domains), and Russia (seven domains) were the top 5 registrant countries. The remaining 91 domains were registered in 39 other countries. A total of 125 domains did not have public registrant country data.
A closer look at the 308 domains identified as IoCs also enabled us to identify text strings closely related to bulletproof hosting services, such as:
The string host was the most commonly used (82 domains), followed by net (53 domains) and web (16 domains). Note that more than one text string could be present in some of the domains, such as in bulletproof-web[.]ru.

To find all potentially connected web properties, we first subjected the domains identified as IoCs to WHOIS history lookups, which led us to uncover 808 email addresses that appeared anywhere in their historical WHOIS records.
A total of 138 email addresses were public (unredacted or could be attributed to specific individuals or organizations). They were also used to register 1—50 domains each only according to reverse WHOIS lookups. Altogether, the 138 public email addresses appeared in the current WHOIS records of 1,103 domains after duplicates and the IoCs were filtered out.
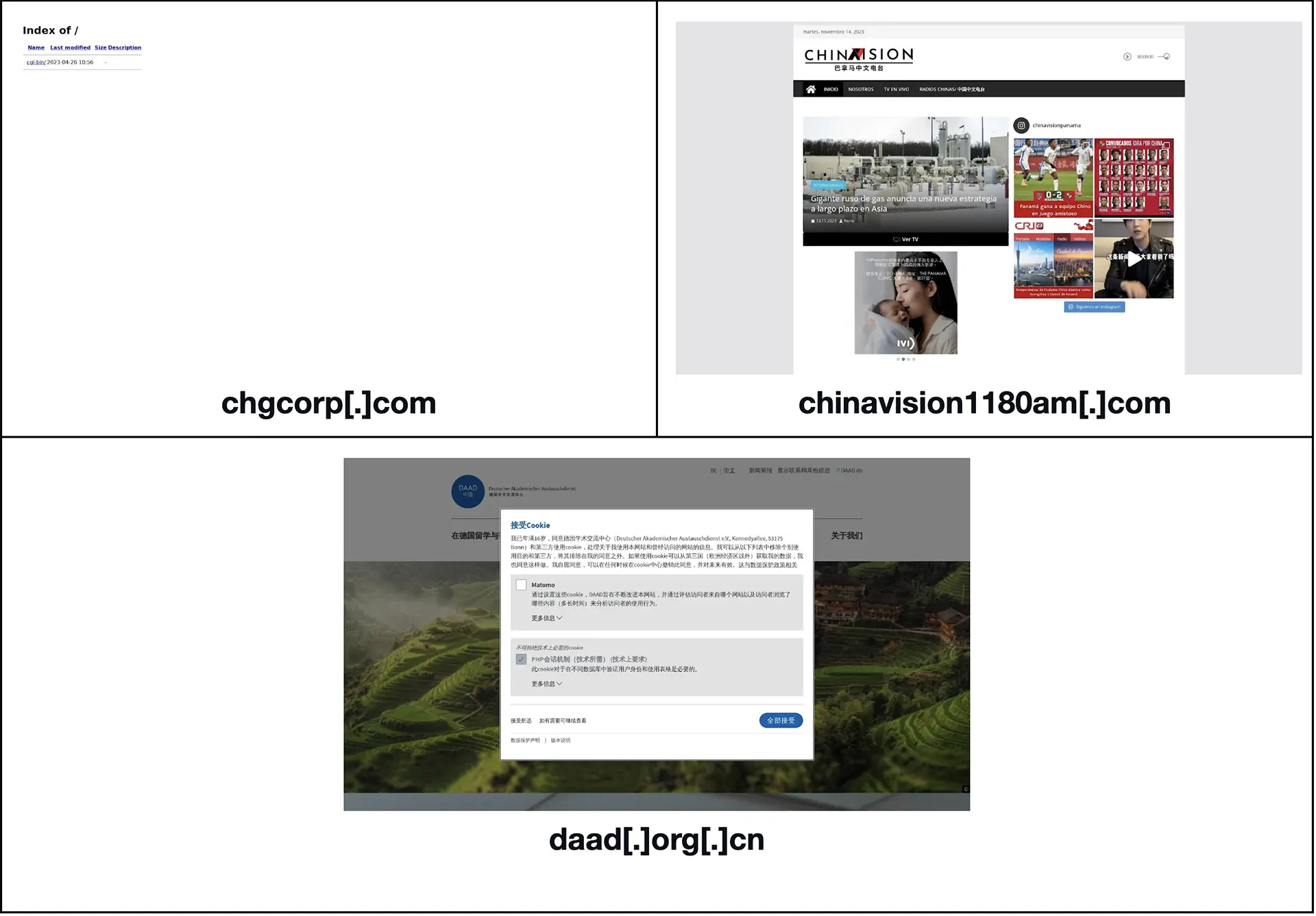
A bulk malware check for the 1,103 email-connected domains revealed that 10 of them were classified as malicious. Four of the 10 malicious domains remained accessible as of this writing based on screenshot lookups, three of which are shown below.
Next, we subjected the 308 domains identified as IoCs to DNS lookups and found that they resolved to 517 IP addresses after IPv6 addresses and duplicates were filtered out.
Reverse IP lookups for the 517 IP addresses showed that only 249 of them were seemingly private (only hosted 1—299 domains each). Fourteen of the 249 potentially private IP addresses turned out to be malicious based on malware checks.
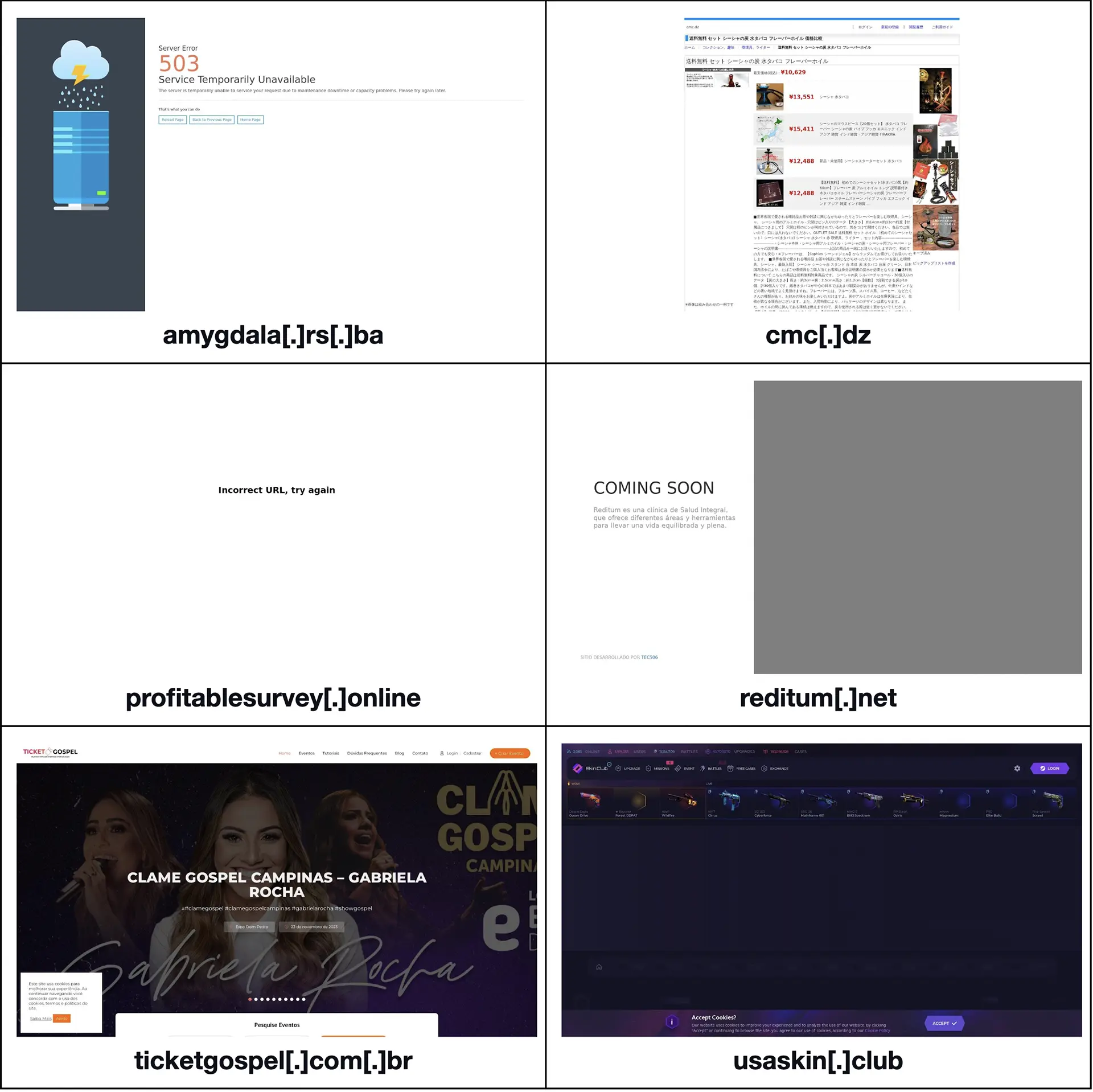
Altogether, the 249 seemingly dedicated IP addresses hosted 4,028 domains after duplicates, the IoCs, and email-connected domains were filtered out. A bulk malware check for the IP-connected domains showed that seven of them were malicious and remained accessible as of this writing, six of which are shown below.
Our IoC expansion analysis showed signs that bulletproof hosts and their infrastructure may still remain up and running as evidenced by the 6,456 potentially connected web properties we uncovered, comprising 808 email addresses; 1,103 email-connected domains; 517 IP addresses; and 4,028 IP-connected domains. It is also worth noting that 31 of them (10 email connected domains, 14 IP addresses, and seven IP-connected domains) were already classified as malicious.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byCSC
