


|
||
|
||
As long as cybercriminals remain in business, so will the number of underground marketplaces grow. And despite the crackdown on the biggest markets like Silk Road, cybercriminals will continue to strive to put up their own marketplaces, probably given their profitability.
Case in point? The Genesis Market began operating in 2017, four years after Silk Road closed shop. Like its predecessor, though, the Federal Bureau of Investigation (FBI) and other law enforcement agencies took the Genesis Market down last April.
The WhoisXML API research team sought to find out if Genesis Market’s infrastructure is truly down and out. We expanded a list of indicators of compromise (IoCs)—12 email addresses to be exact—researcher Dancho Danchev collated.
Our Genesis Market DNS deep dive led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
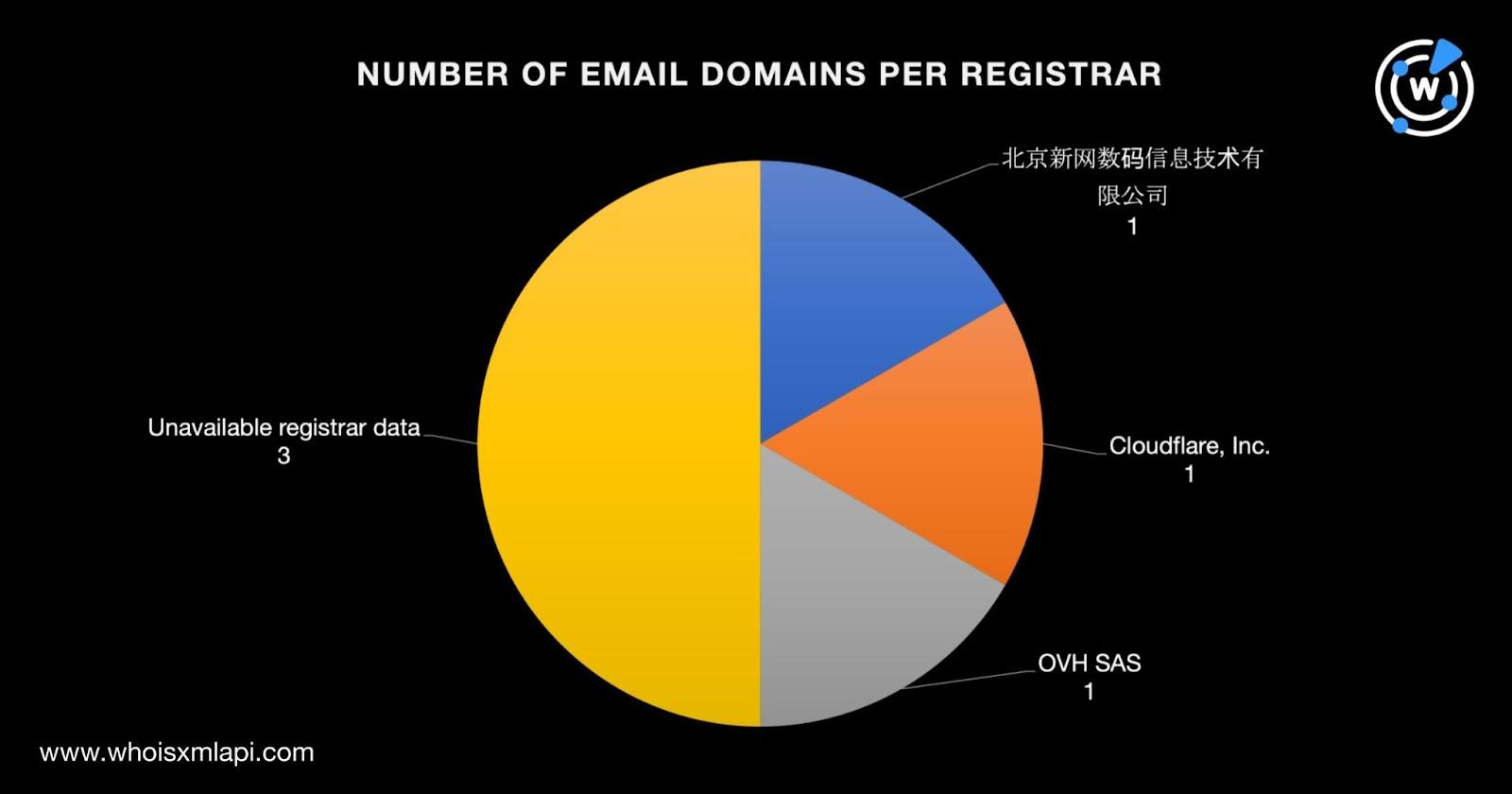
First off, we sought to find more information on the 12 email addresses identified as IoCs by looking more closely at their domains. We decided to focus our analysis on the six email addresses with custom email domains, as the Genesis Market operators may have specially crafted or compromised them for their malicious campaigns.
Here’s a summary of our findings:
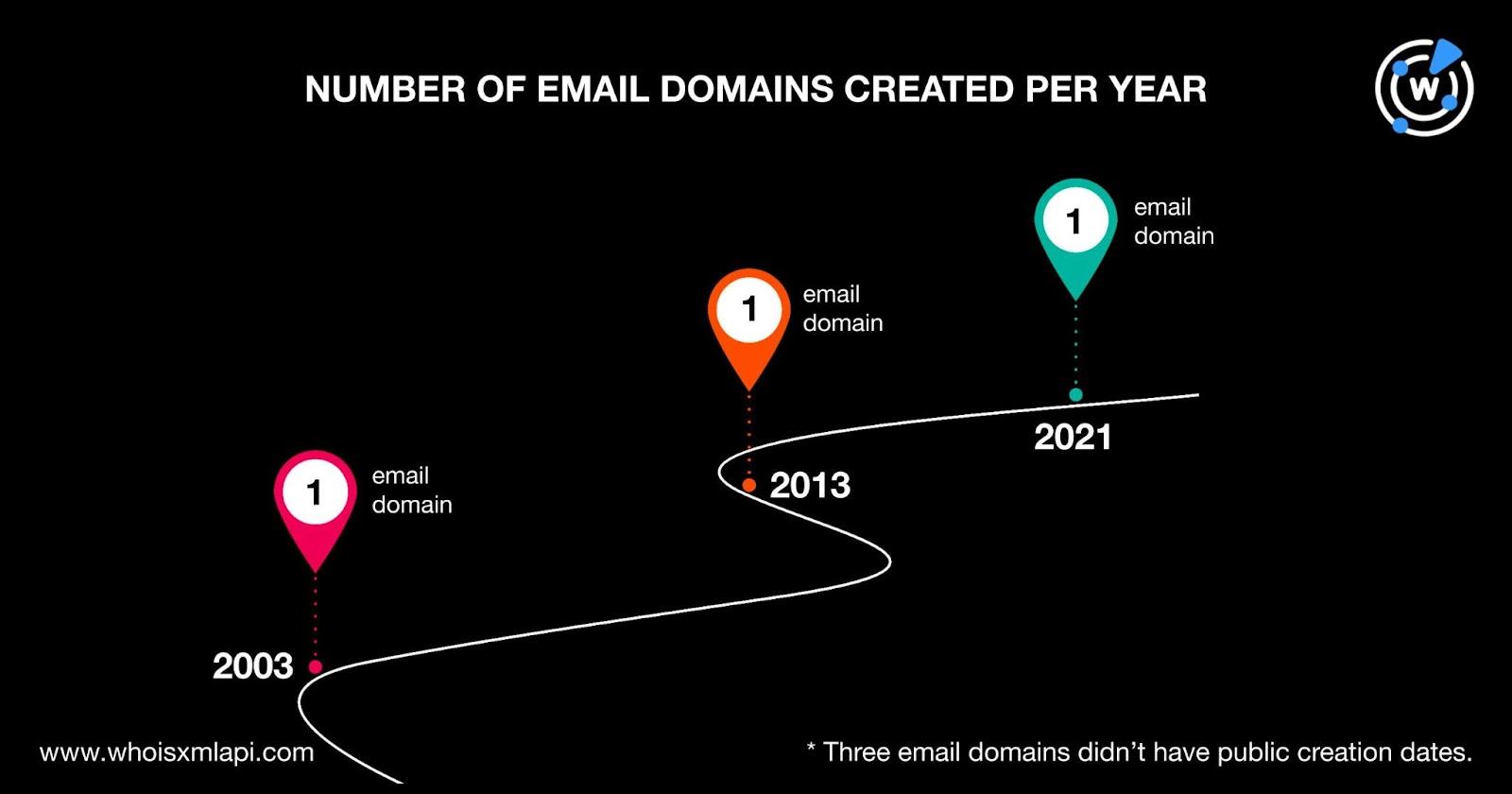
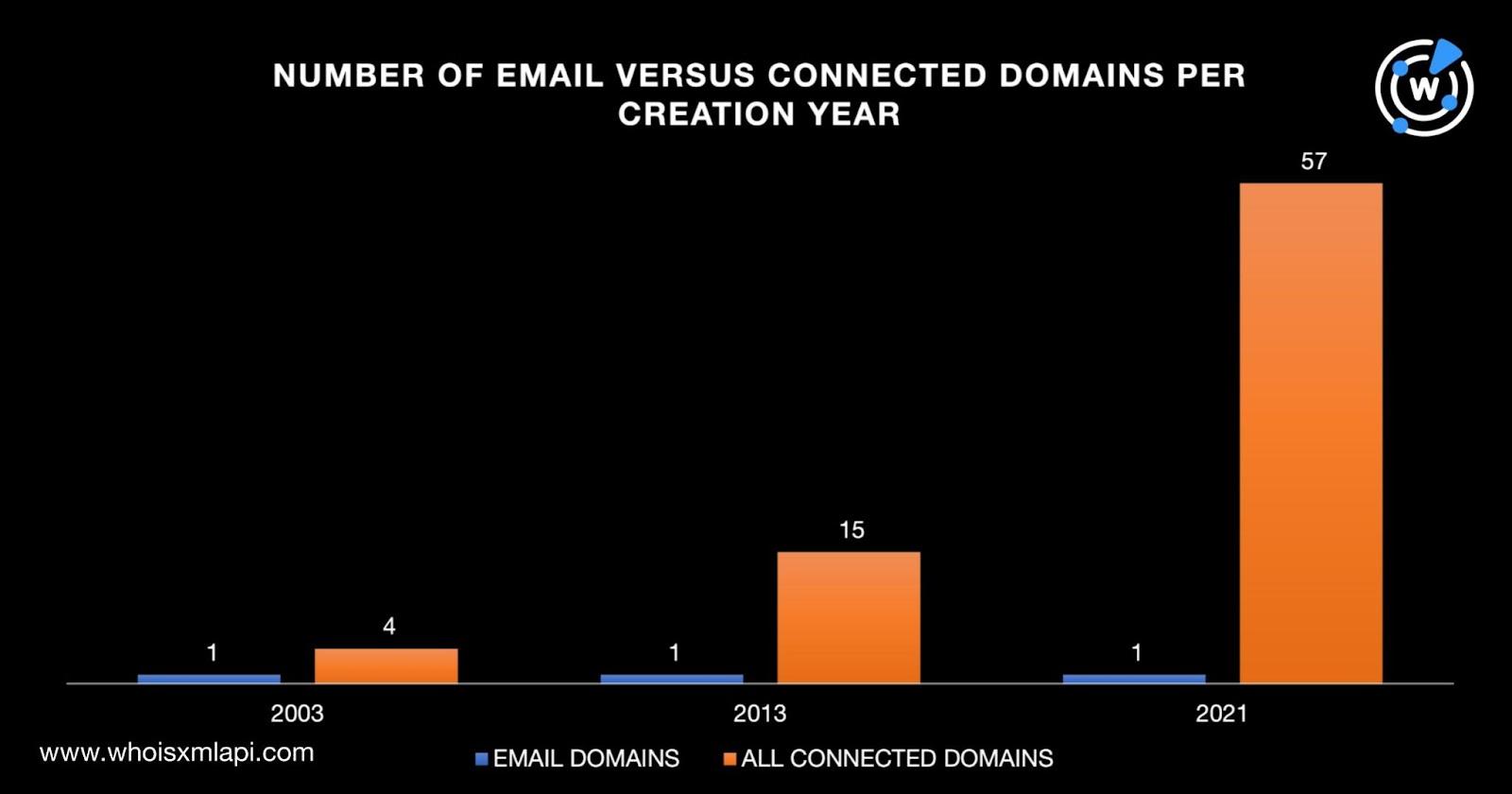
Only three of the six email domains had current public creation dates. One each was registered in 2003, 2013, and 2021.
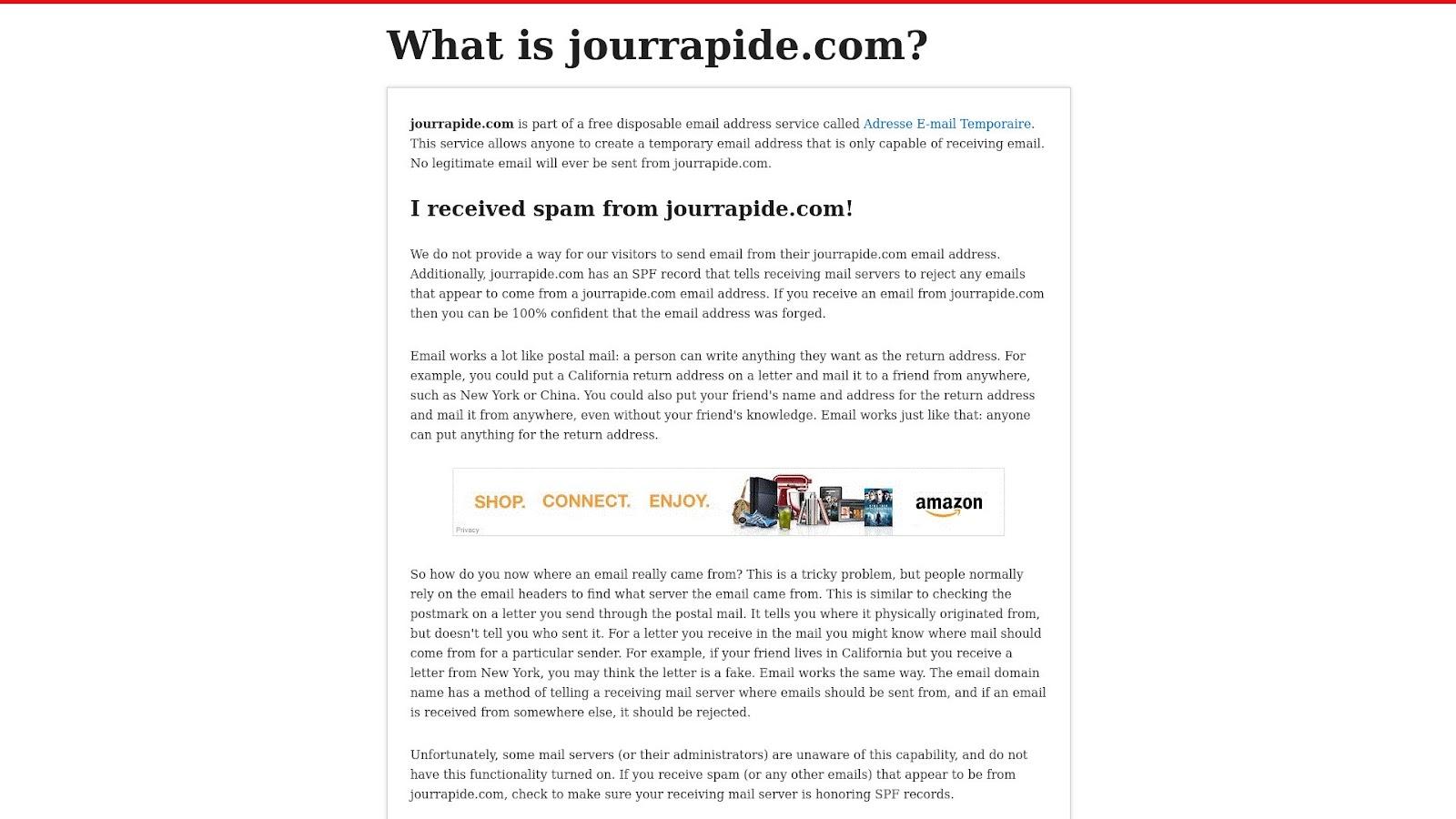
Based on the results of malware checks, one of the email domains—jourrapide[.]com—turned out to be malicious. A screenshot lookup for the malicious email domain showed that it remained accessible as of this writing.
To scour the DNS for traces that Genesis Market may have left behind after its takedown, we performed reverse WHOIS searches for the 12 email addresses identified as IoCs. Only one of the email addresses appeared in the current WHOIS records of 28 domains.
Next, we subjected the 28 email-connected domains to DNS lookups. We discovered that they resolved to five unique IP addresses.
Four of the IP addresses were seemingly dedicated. Altogether, they hosted six domains. After removing duplicates and the email-connected domains, we were left with two IP-connected domains.
Further scrutiny of the email- and IP-connected domains allowed us to collate a list of 22 unique strings that Genesis Market may have specifically chosen to use for their malicious campaigns. These text strings were:
Using the 22 strings above as Domains & Subdomains Discovery historical search terms enabled us to collate 12,442 string-connected domains using the Contains parameter. To reduce the number of false positives, we filtered out the results for nsr. (which appeared in 10,000+ domains), along with duplicates and the domains already classified as email- and IP-connected domains. That left us with 2,417 string-connected domains.
A bulk malware check for the 2,417 string-connected domains revealed that three of them were already categorized as malicious. Screenshot lookups showed that one of the malicious domains—silk-road[.]xyz—remained accessible even if it led to an error page. Note the appearance of the string silk-road in the domain, too. Silk Road was the first darknet market established in 2011.
Our in-depth analysis of the Genesis Market IoCs and connected domains also showed some similarities, namely:
Four, 15, and 57 connected domains were created in 2003, 2013, and 2021, respectively, akin to the email domains. While 1,634 connected domains didn’t have current public creation dates, 734 were created in 1995–2002, 2004–2012, and 2022–2023.
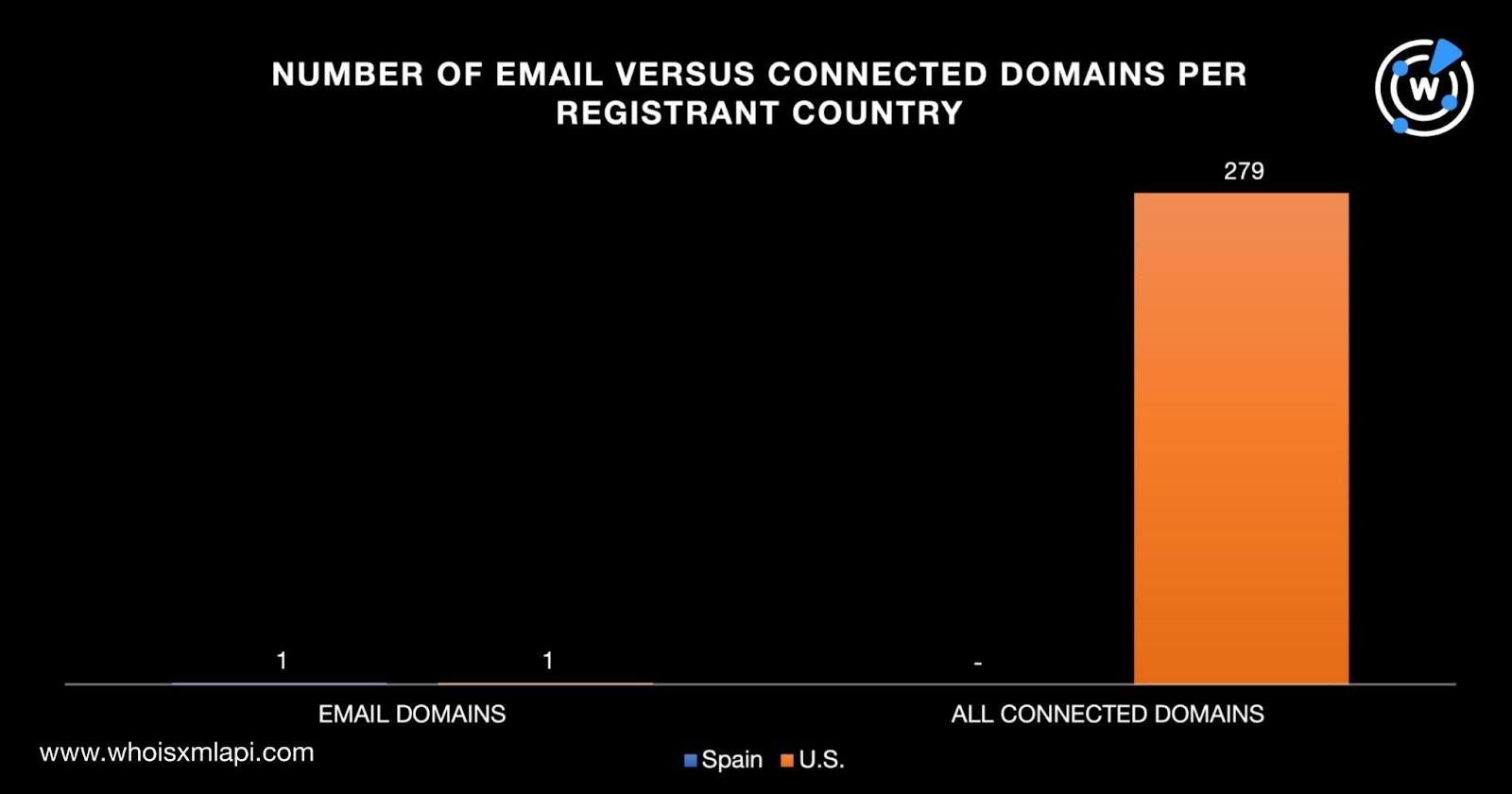
While none of the connected domains were registered in Spain, 279 were registered in the U.S. like one of the email domains.
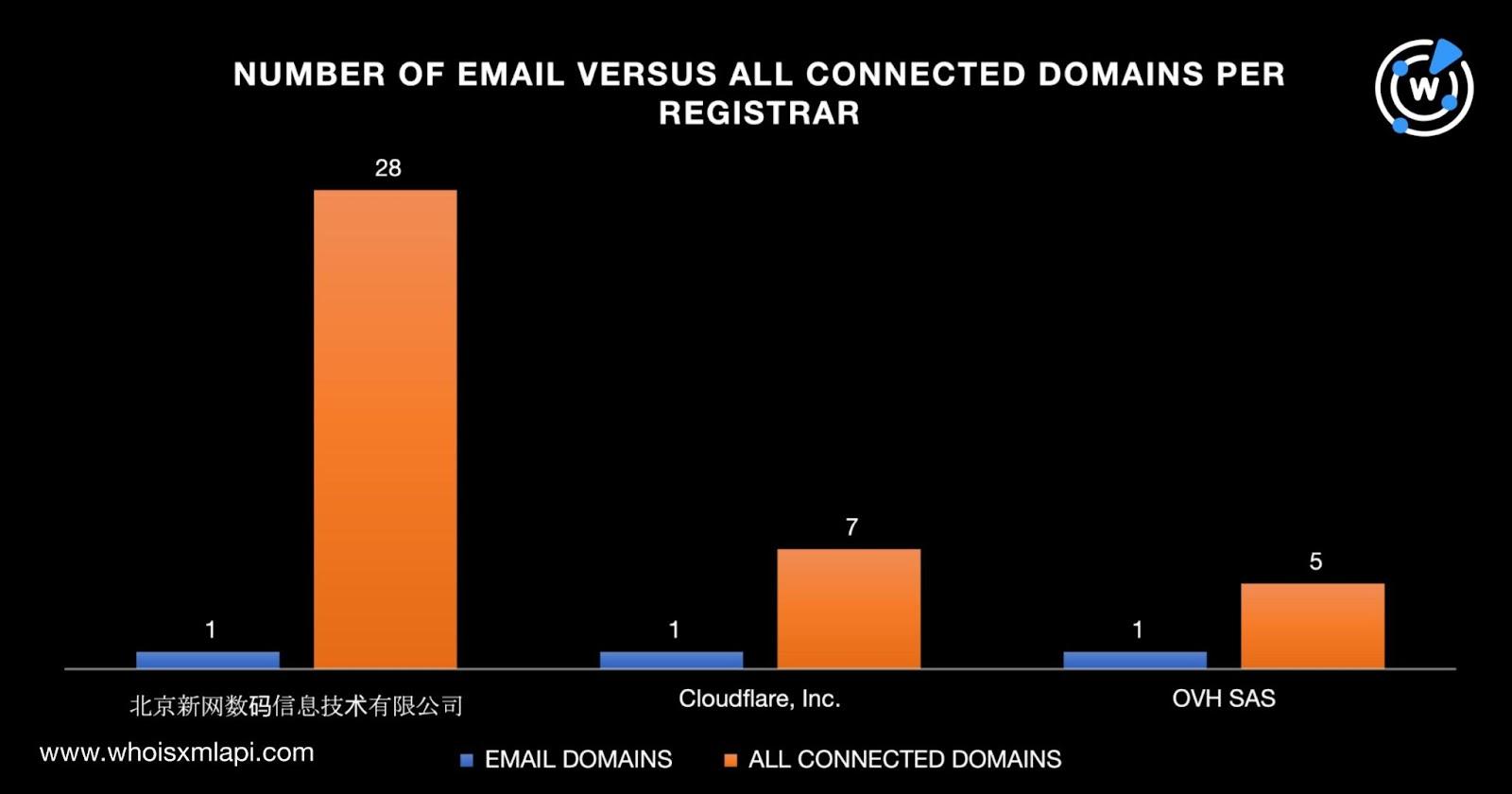
Our DNS deep dive into the Genesis Market IoCs led to the discovery of 2,452 potentially connected artifacts. We also found that 40 connected domains shared the email domains’ registrars, 76 shared the email domains’ creation years, and 279 shared the email domains’ registrant countries.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byVerisign
