


|
||
|
||
The concept of internationalization extends from the virtual to the physical realm. Many people wish to travel or even migrate to other countries at some point in their lives. Unfortunately, that’s sometimes easier said than done given the many legal documents, including valid IDs, passports, and others required.
In the past, some wanna-be international travelers met unsavory characters in the real world to obtain fake IDs. Today, all that has become doable online. And due to the demand, many threat actors have put up their own online marketplaces.
WhoisXML API threat researcher Dancho Danchev recently uncovered an email address allegedly belonging to one such proprietor—noveltypro1@hotmail[.]com. Our cybersecurity research team trooped to the DNS to find out how extensive the operation could be.
Our indicator of compromise (IoC) expansion analysis jumping off the malicious email address led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
To determine the extent of the fake ID proprietor’s network, we performed a WHOIS History Search for domains whose records contained the email address in their records. We uncovered nine such domains.
A bulk WHOIS lookup for the nine email-connected domains showed that:
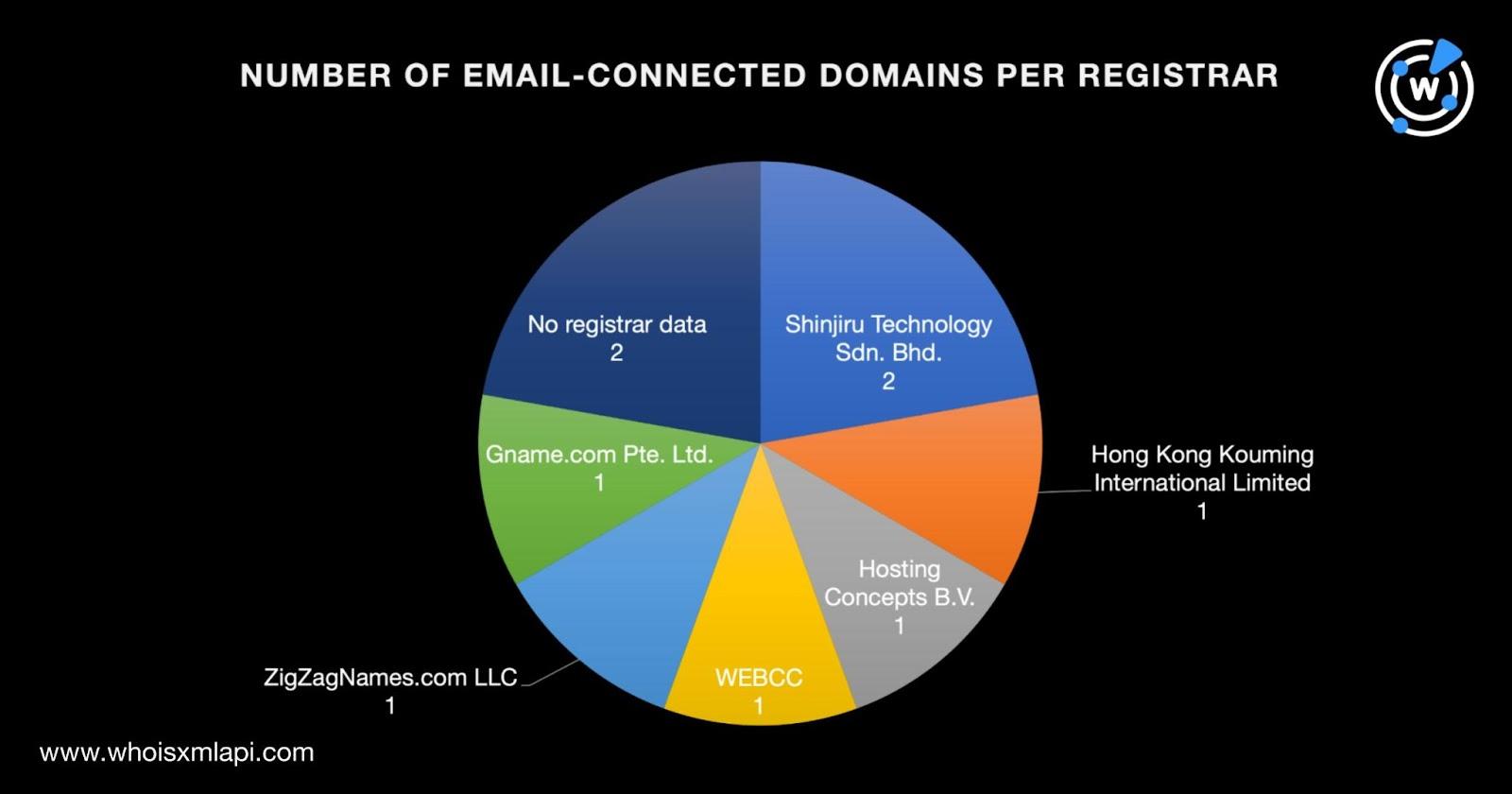
While two of the email-connected domains did not have current creation dates, the remaining seven were created between 2004 and 2023.
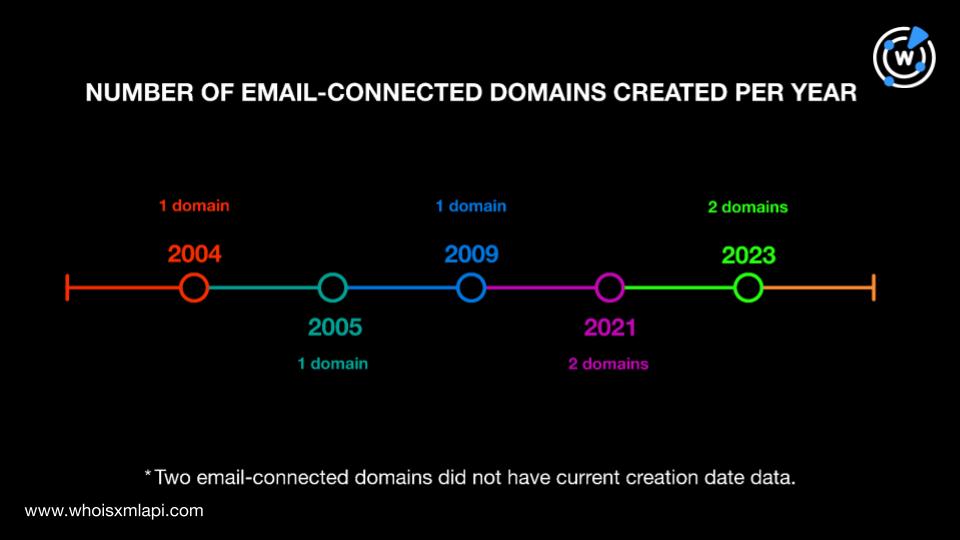
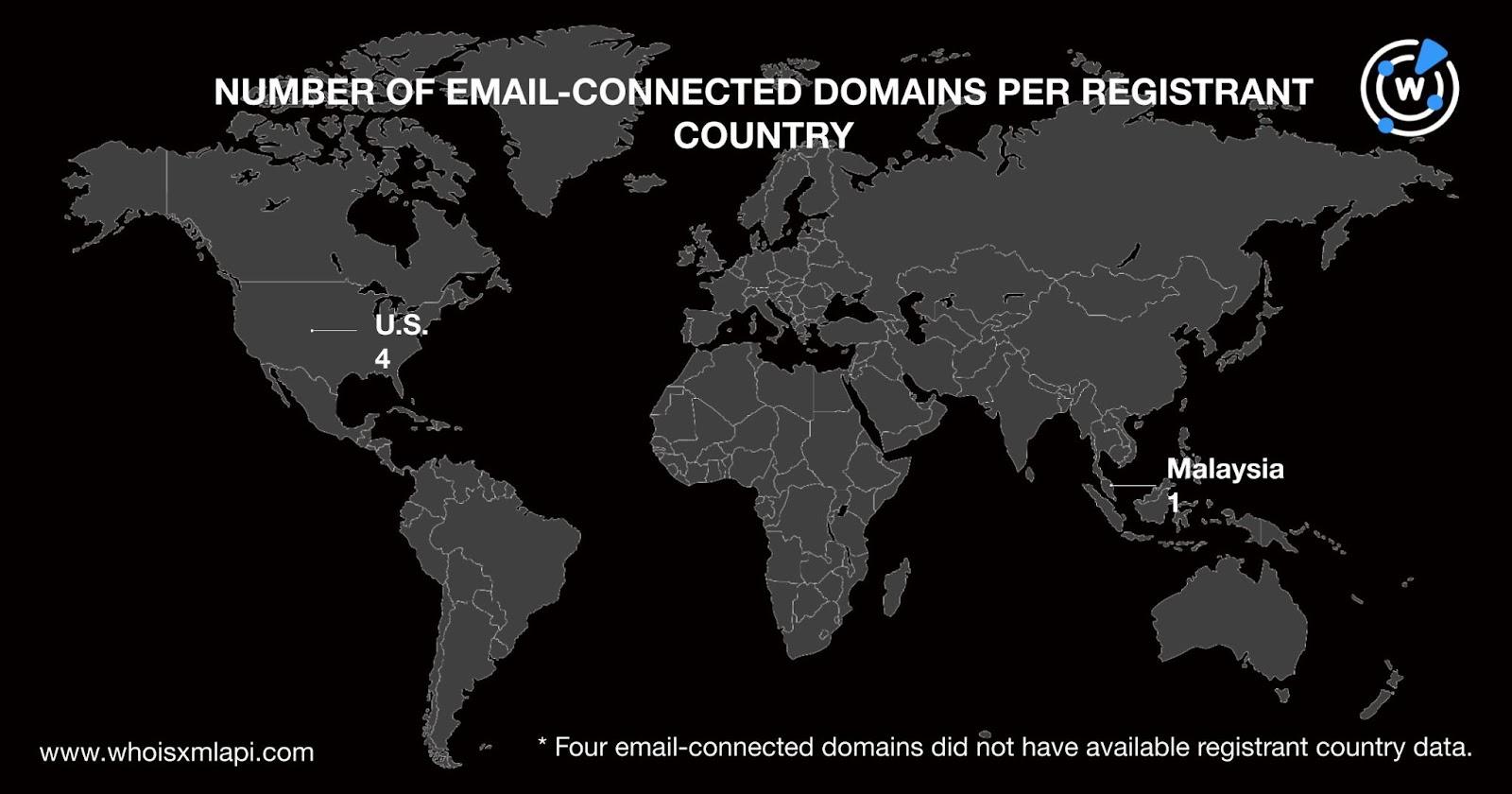
A majority of the email-connected domains, four to be exact, were registered in the U.S. One was registered in Malaysia. The remaining four did not have available registrant country data.
While five of the email-connected domains were unreachable as of this writing based on screenshot lookups, three continued to host live content and one led to an error page.
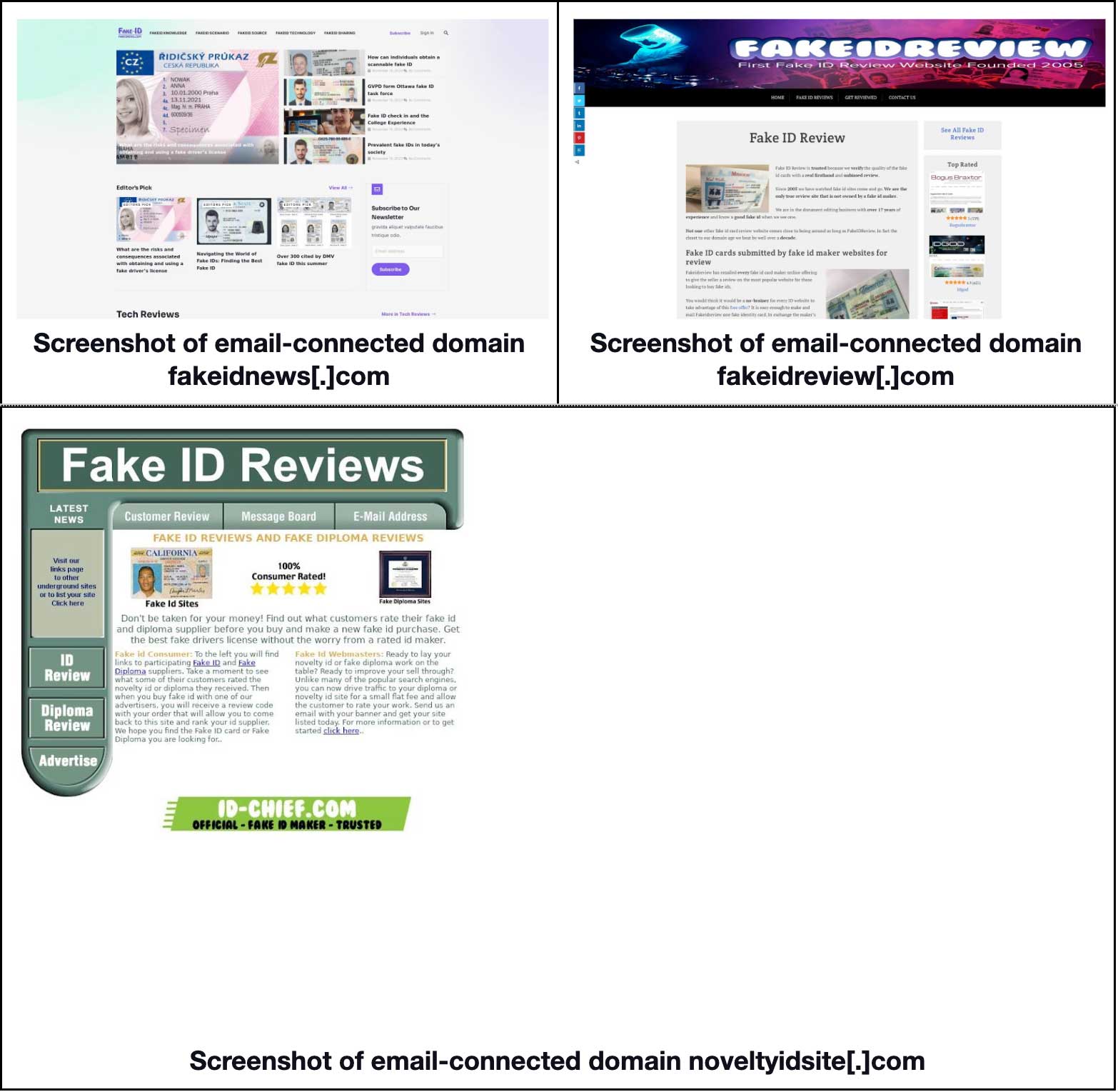
Based on their content, these three sites may offer fake IDs, even passports, licenses, and diplomas, to interested buyers.
Next, we subjected the email-connected domains to DNS lookups, which revealed that they resolved to seven unique IP addresses. Threat intelligence lookups for them yielded interesting findings about five of them. Take a look at the table below.
| IP ADDRESS | THREAT TYPE CLASSIFICATION |
|---|---|
| 172[.]67[.]148[.]80 | GenericPhishing |
| 208[.]91[.]197[.]46 | GenericPhishingMalwareSuspiciousC&C |
| 172[.]67[.]132[.]236 | GenericPhishingMalware |
| 104[.]21[.]29[.]28 | GenericPhishing |
| 104[.]21[.]13[.]182 | GenericPhishingMalware |
A bulk IP geolocation lookup for the seven IP addresses showed that:
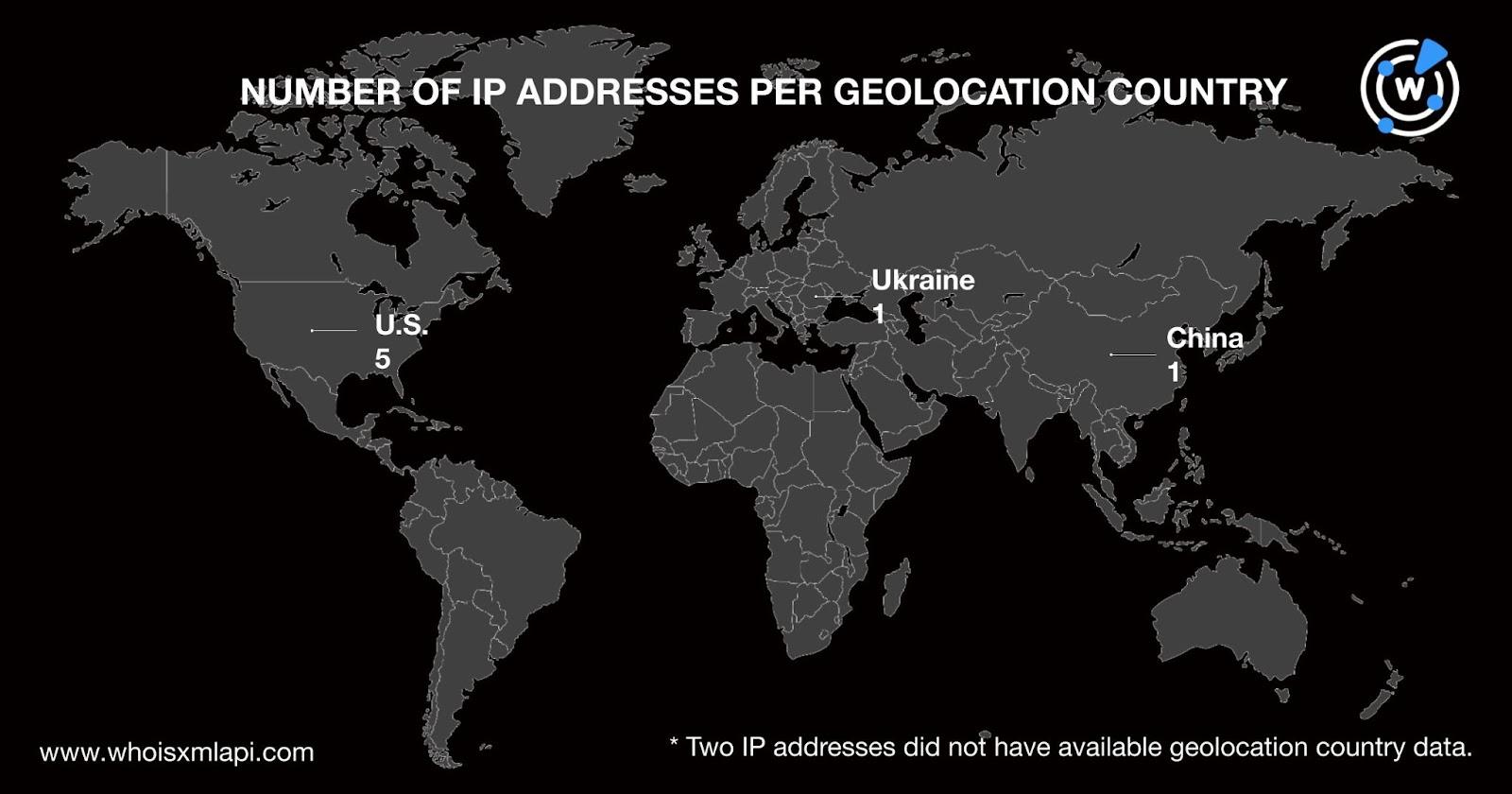
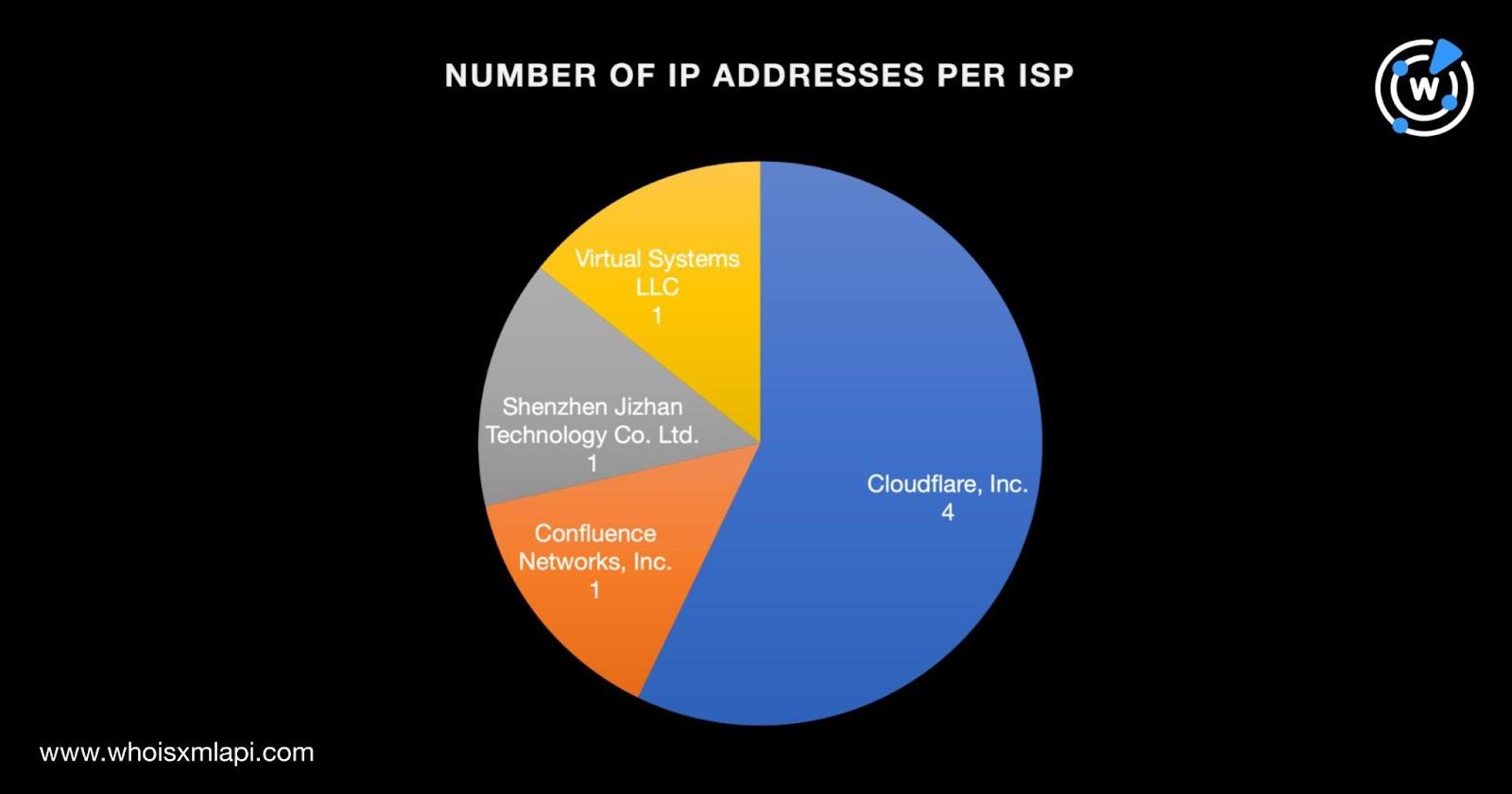
The top Internet service provider (ISP) was Cloudflare, Inc., which accounted for four IP addresses. Virtual Systems LLC; Shenzhen Jizhan Technology Co. Ltd.; and Confluence Networks, Inc. each administered one of the three remaining IP addresses.
We then performed reverse IP lookups on the seven IP addresses and found that two of them were seemingly dedicated. They hosted three domains. After we removed duplicates and the email-connected domains, we were left with one IP-connected domain—handyman-joes[.]com.
Further scrutiny of the email-connected domains allowed us to identify six text strings that are likely to appear in fake ID-related web properties. We used them as Domains & Subdomains Discovery search terms to uncover other domains and subdomains created or added since 1 January 2023. Take a look at the detailed list in the table below. Note that the number of domains indicated still include those that have already been identified as email- and IP-connected.
| TEXT STRING | NUMBER OF STRING-CONNECTED DOMAINS | NUMBER OF STRING-CONNECTED SUBDOMAINS |
| cloneid | 3 | 11 |
| fakeid | 195 | 685 |
| fakeidentity | 6 | 0 |
| idclone | 10 | 46 |
| identityclone | 0 | 1 |
| idfake | 17 | 34 |
After filtering the string-connected domain and subdomain lists to exclude duplicates and those that have already been tagged as either email- or IP-connected, we were left with 231 and 777 string-connected domains and subdomains, respectively.
A total of 522 string-connected web properties remained accessible to date—152 domains and 370 subdomains.
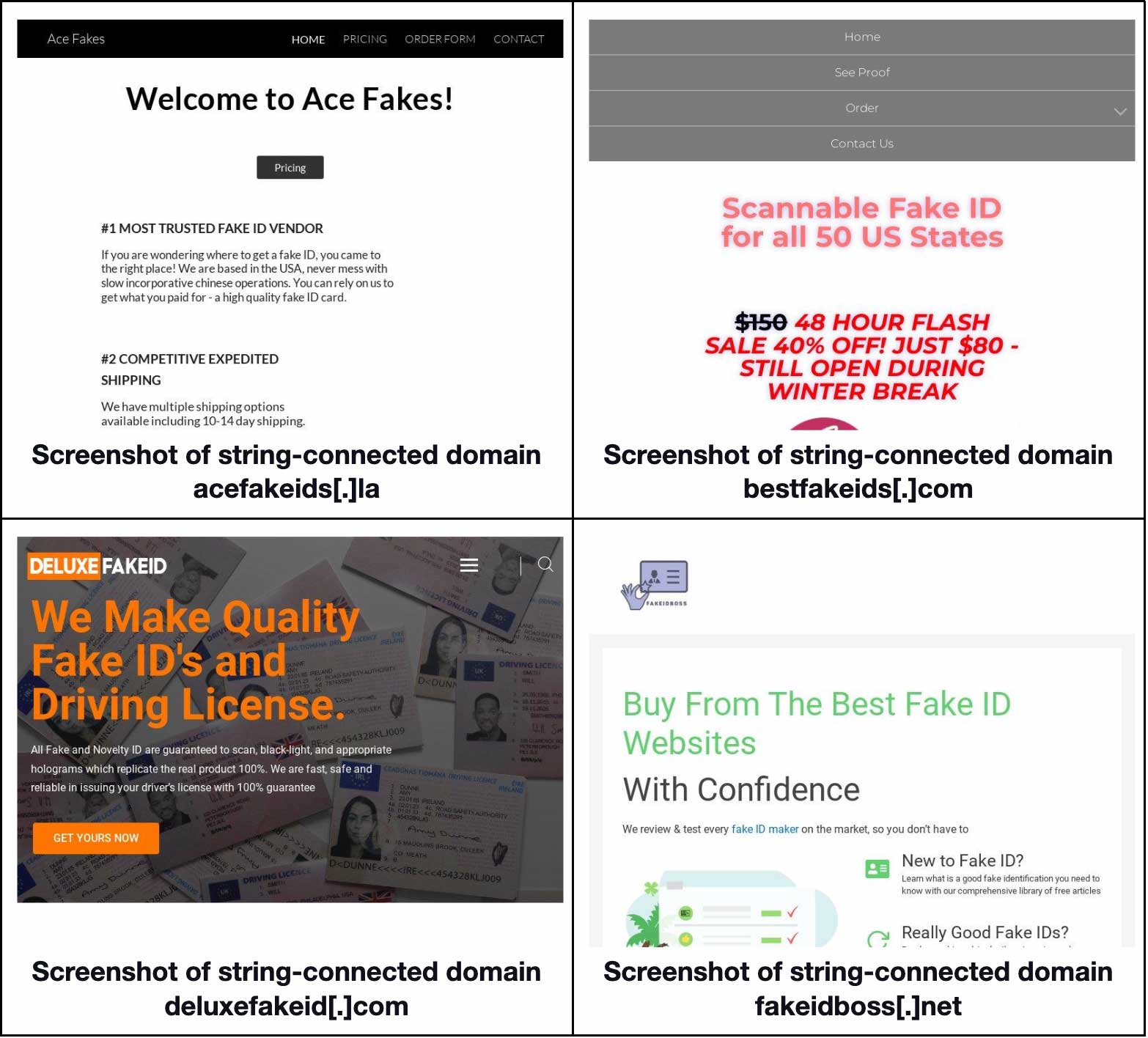
Based on their screenshots, 42 of the 152 string-connected domains did host sites that seemingly sold fake IDs or promoted them. Take a look at four examples below.
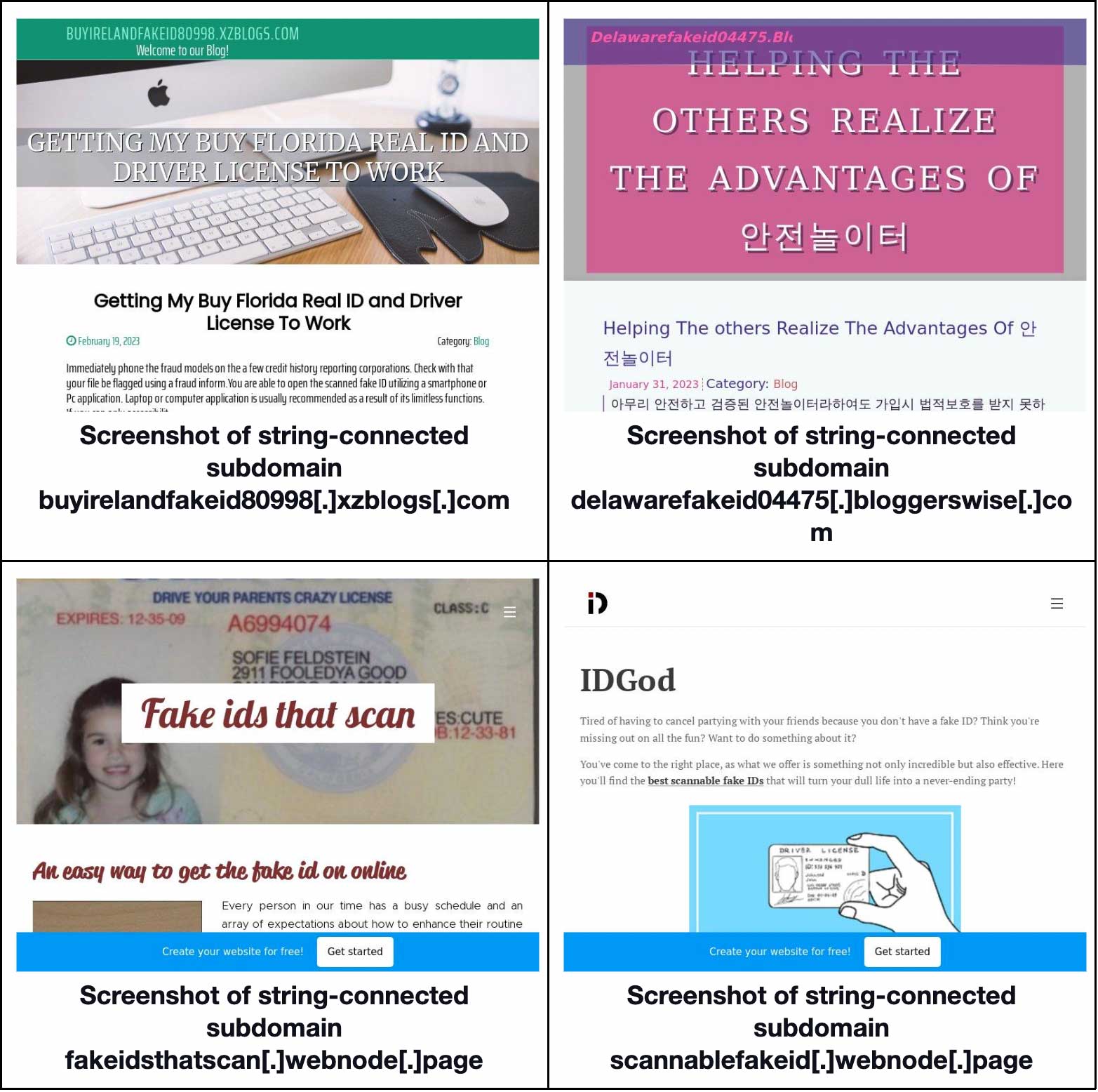
In addition, 24 of the string-connected subdomains also hosted pages that were seemingly related to the proliferation of fake ID usage. Certain of them also appear to fall under free blogging platform domains. Take a look at four examples below.
Our in-depth analysis of the sole email address belonging to a fake ID peddler led to the discovery of 17 web properties—nine email-connected domains, seven IP addresses, and one IP-connected domain—that could be part of the same malicious infrastructure. We also found 522 domains and subdomains that could belong to fellow fake ID sellers.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byWhoisXML API
