


|
||
|
||
The WailingCrab malware has gained notoriety for its stealth. IBM X-Force security researchers recently published an in-depth analysis of the malware, which has been abusing Internet of Things (IoT) messaging protocol MQTT.
The researchers publicized 24 indicators of compromise (IoCs) as part of their report, including one domain and 14 URLs. After extracting the URLs’ domains, we were left with 15 IoCs that we then subjected to an expansion analysis that led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
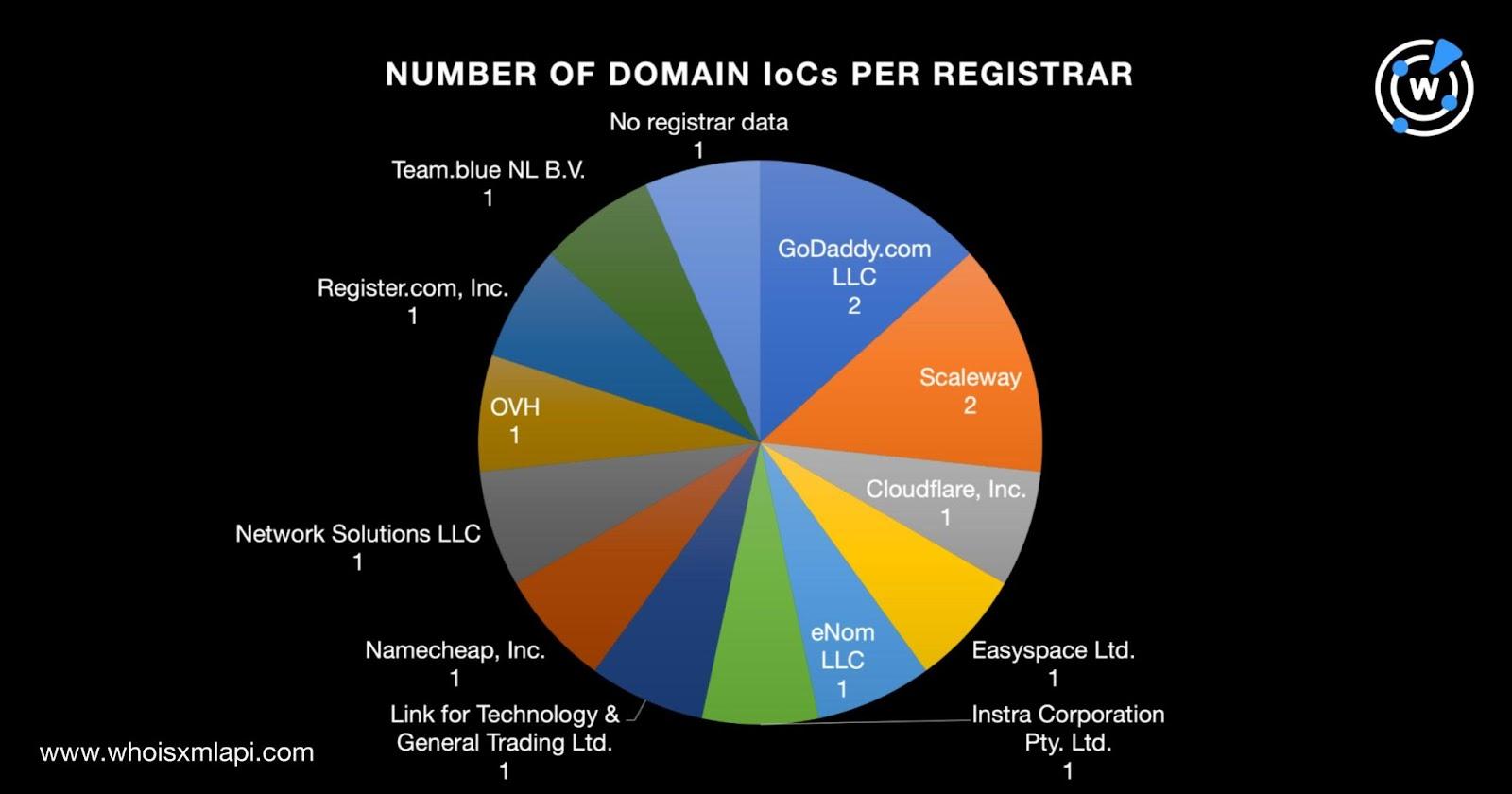
We began our in-depth investigation with a bulk WHOIS lookup for the 15 domains identified as IoCs and found that:
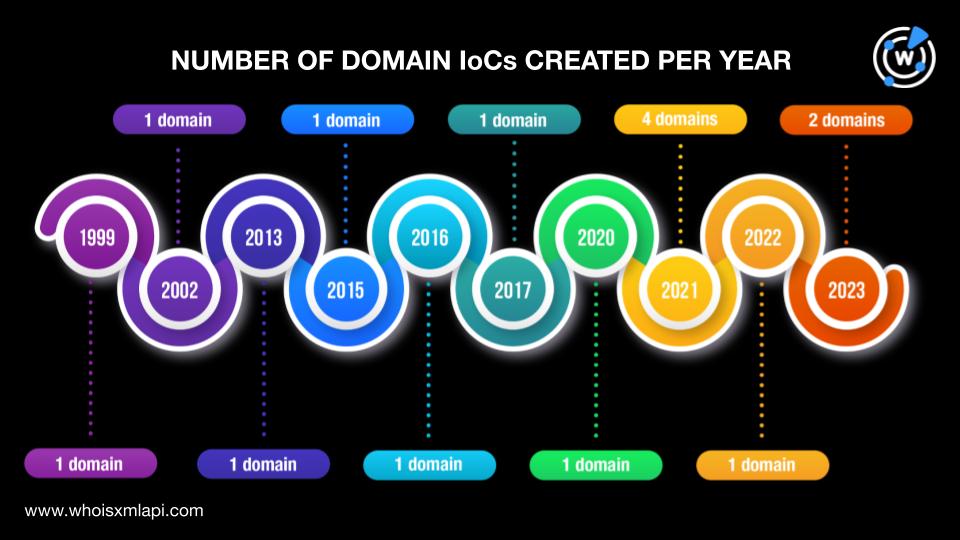
Four domains were created in 2021; two in 2023; and one each in 1999, 2002, 2013, 2015—2017, 2020, and 2022. One domain did not have a public creation date.
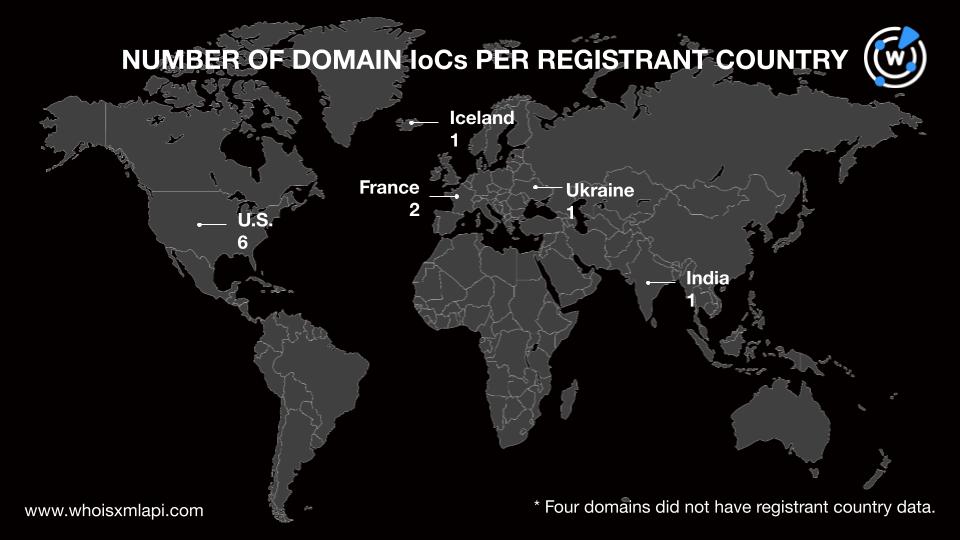
The U.S. was the top registrant country, accounting for six domains. France took the second spot with two domains. One domain each was created in Iceland, India, and Ukraine. Four domains did not have registrant country information.
To find every potentially connected artifact in the DNS, we first performed a bulk WHOIS history search for the 15 domains identified as IoCs. That allowed us to obtain 94 email addresses found anywhere in their historical WHOIS records after duplicates were removed.
A bulk reverse WHOIS search allowed us to limit the scope of this study to include only the email addresses that appeared in the current WHOIS records of 1—50 domains and were not privacy-protected. We were left with six email addresses to further analyze. They were shared by 26 other domains after duplicates and those already identified as IoCs were removed.
A bulk screenshot lookup revealed that five of the email-connected domains continued to host live content. Only two, however, led to seemingly functional websites. The three remaining domains led to error or blank pages or were parked.


Next, we ran DNS lookups for the 15 domains identified as IoCs and found that they resolved to 17 unique IP addresses.
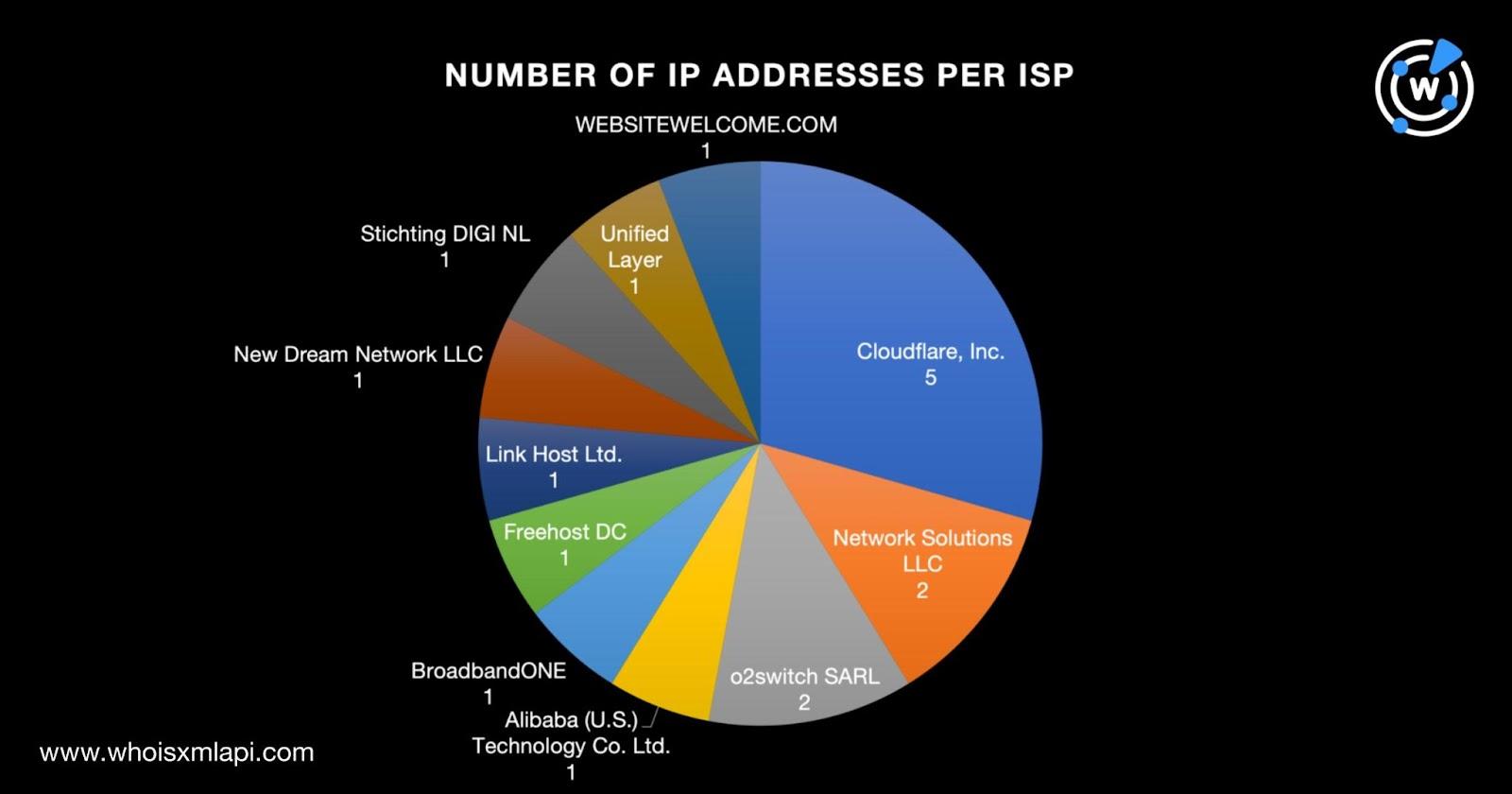
IP geolocation lookups for the 17 IP addresses showed that:
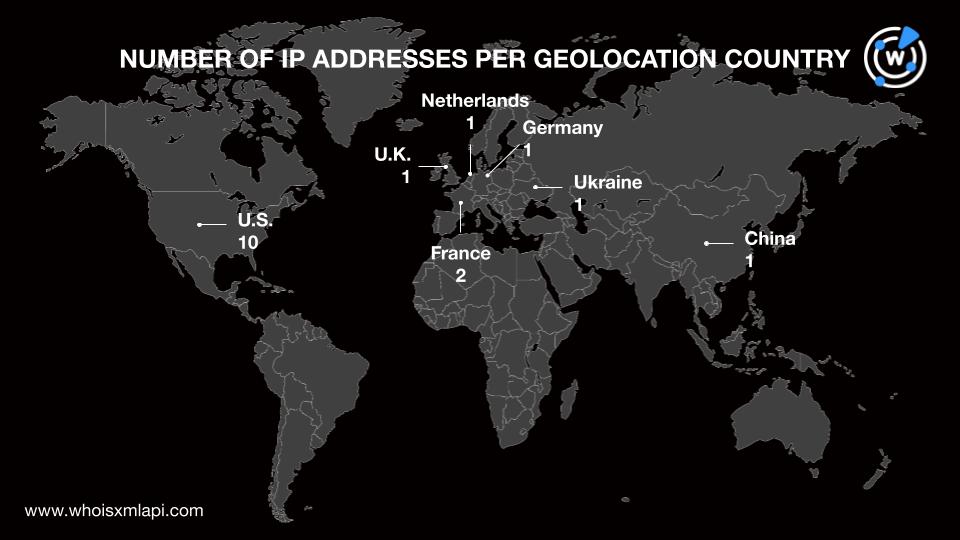
Cloudflare, Inc. was the top Internet service provider (ISP), accounting for five IP addresses. Network Solutions LLC and o2switch SARL tied in second place with two IP addresses each. The remaining eight IP addresses were spread across Alibaba (U.S.) Technology Co. Ltd., BroadbandONE, Freehost DC, Link Host Ltd., New Dream Network LLC, Stichting DIGI NL, Unified Layer, and WEBSITEWELCOME.COM.
Threat Intelligence Lookup embedded intelligence also revealed that 12 of the IP addresses were associated with 1—3 threats each. Take a look at the detailed results in the table below.
| IP ADDRESS | THREAT INTELLIGENCE LOOKUP FINDING | ASSOCIATED THREAT TYPES |
|---|---|---|
| 109[.]234[.]161[.]16 | Associated with two threats | PhishingMalware |
| 162[.]159[.]129[.]233 | Associated with three threats | MalwareAttackGeneric |
| 162[.]159[.]130[.]233 | Associated with two threats | MalwareGeneric |
| 162[.]159[.]133[.]233 | Associated with two threats | MalwareGeneric |
| 162[.]159[.]134[.]233 | Associated with two threats | MalwareGeneric |
| 162[.]159[.]135[.]233 | Associated with two threats | MalwareGeneric |
| 162[.]241[.]224[.]104 | Associated with three threats | PhishingMalwareGeneric |
| 185[.]104[.]29[.]64 | Associated with two threats | PhishingMalware |
| 185[.]13[.]5[.]52 | Associated with one threat | Malware |
| 188[.]64[.]139[.]53 | Associated with one threat | Phishing |
| 209[.]17[.]116[.]165 | Associated with one threat | Phishing |
| 50[.]116[.]86[.]129 | Associated with two threats | PhishingMalware |
Reverse IP lookups for the 17 IP addresses revealed that nine of them could be dedicated, each playing host to less than 300 domains at most. Altogether, they hosted 524 domains after duplicates, the IoCs, and the email-connected domains were removed.
Three of the IP-connected domains contained popular brand names, namely:
WHOIS record comparisons aided by WHOIS Lookup with the official domains of Amazon (amazon[.]com) and Zoom (zoom[.]us) showed that none of the three IP-connected domains could be publicly attributed to the companies whose brands appeared in them. In particular:
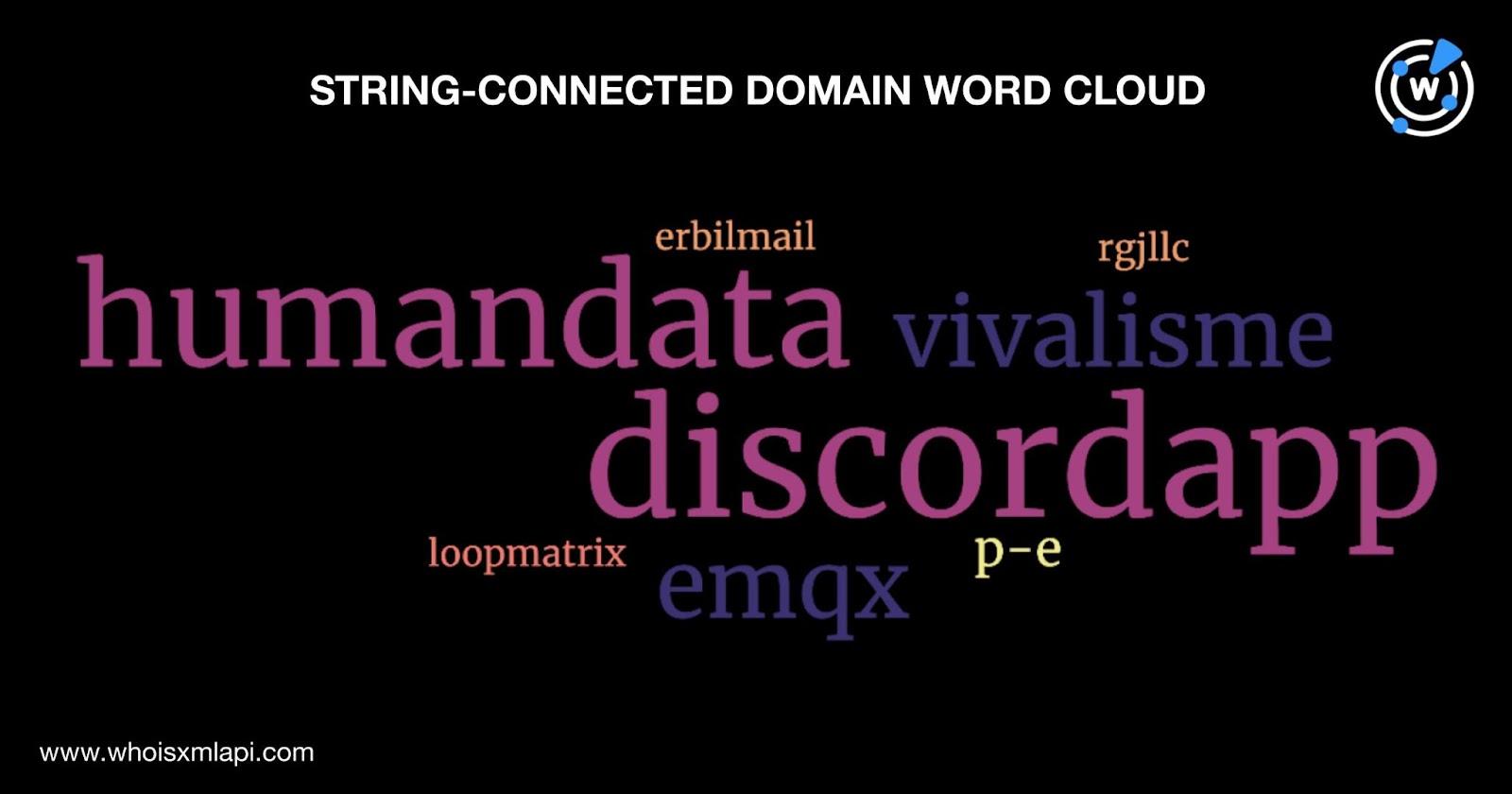
As a last step, we scoured the DNS for other domains and subdomains that contain text strings found among the IoCs, specifically:
Domains & Subdomains Discovery provided us with 978 domains and 2,002 subdomains after duplicates, the IoCs, and email- and IP-connected domains were removed. We also excluded the domains and subdomains containing flow. as there were more than 10,000 results for each web property type, which could include tons of false positives. Take a look at the word clouds that represent the text strings’ occurrence among the domains and subdomains.

Our expansion analysis of the WailingCrab IoCs led to the discovery of 3,547 potentially connected artifacts, including 12 IP addresses associated with 23 known threats.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byWhoisXML API
