


|
||
|
||
The Log4Shell zero-day vulnerability, also known as “CVE-2021-44228,” proved to be one of the worst bugs disclosed in December 2021. And while a patch for it has been made available via the Log4j 2.17.1 release seven days after its discovery, some affected systems could remain vulnerable to date. It’s thus not surprising to see threat actors distribute Log4Shell malware to further their illicit campaigns.
Case in point? The Threat Intelligence Platform (TIP) research team recently obtained a total of 64 Log4Shell malware indicators of compromise (IoCs) comprising 58 domains and six subdomains. We used them as jump-off points for an IoC list expansion analysis that allowed us to uncover:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Before we start looking for additional artifacts related to the Log4Shell malware campaign, let’s dive deeper into the IoCs first.
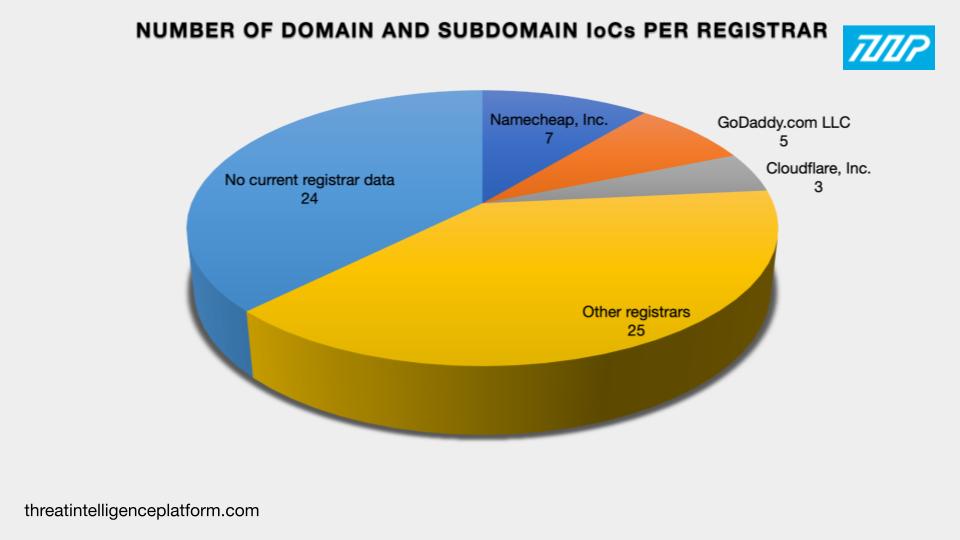
Closer scrutiny of the 64 domains (58 named as IoCs and six extracted from the subdomains identified as IoCs) showed that:
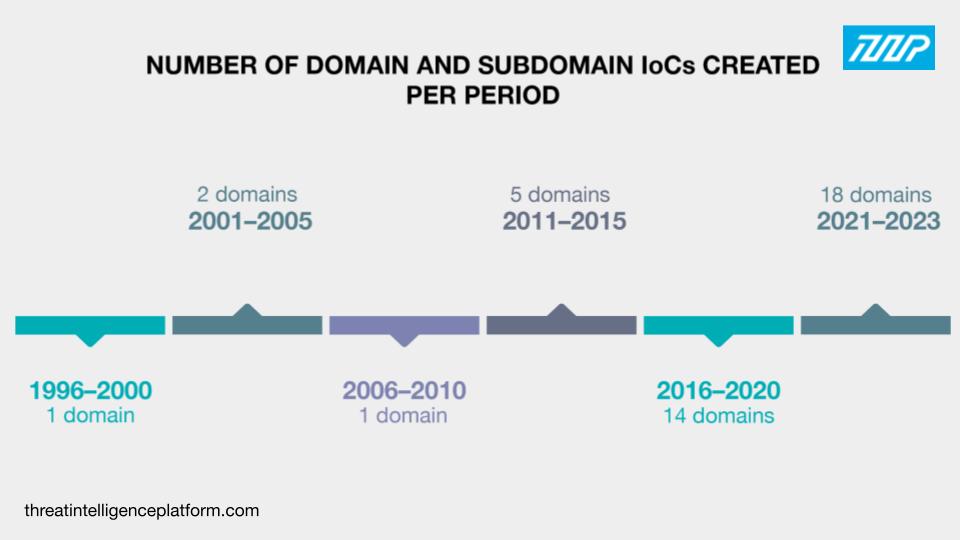
The 40 domains with current WHOIS records were created between 1996 and 2023. The largest number, 12 domains to be exact, were created in 2021. Twenty-three IoCs didn’t have public creation dates.
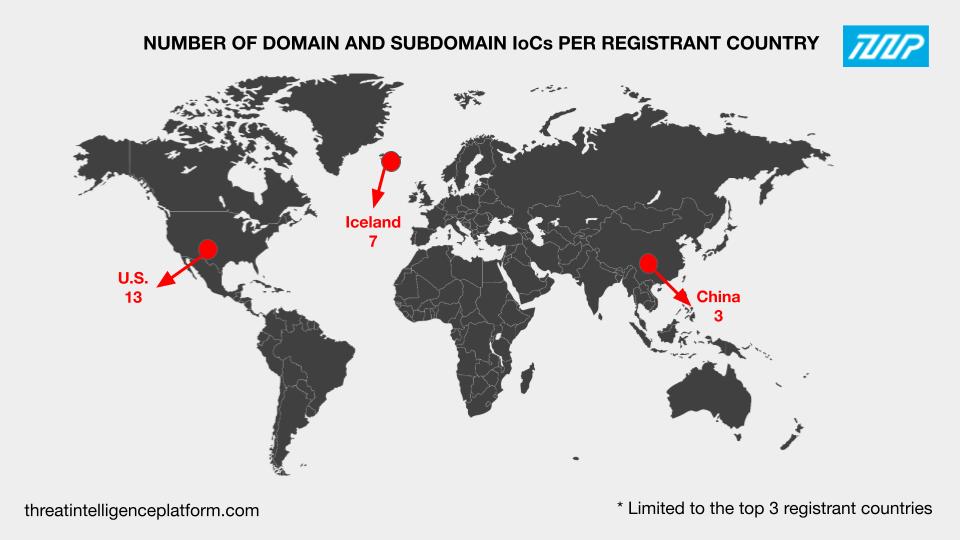
The U.S. (13 IoCs), Iceland (seven IoCs), and China (three IoCs) were the top 3 registrant countries of the domains and subdomains identified as IoCs. Eleven IoCs were spread across seven other registrant countries. Thirty of the IoCs didn’t have registrant country information in their current WHOIS records.
Diving into the historical WHOIS records of the 64 Log4Shell attack IoCs allowed us to obtain 237 email addresses, five of them were public and used to register a maximum of 50 domains each. We limited the scope of our investigation on the five public email addresses.
We then scoured the DNS for the domains containing the five public email addresses in their current WHOIS records and found 18 domains after filtering out duplicates and those already identified as IoCs.
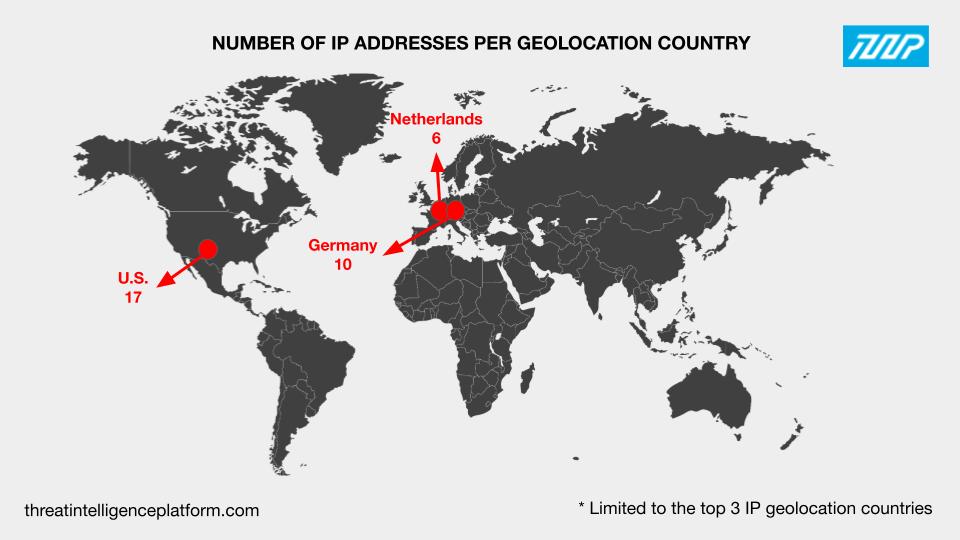
The TIP query results for the 64 original IoCs also showed that they resolved to 47 unique IP addresses spread across 10 geolocation countries led by the U.S., which accounted for 17 of them. Germany (10 IP addresses) and the Netherlands (six IP addresses) rounded out the top 3 geolocation countries. Thirteen IP addresses pointed to seven other countries as their origins. Note, however, that one IP address didn’t have geolocation country information.
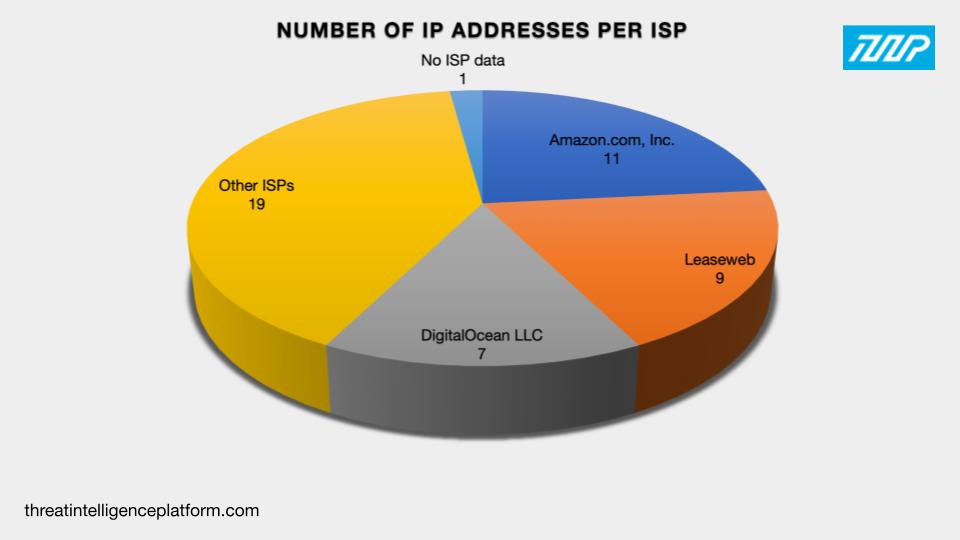
The IP geolocation details also showed that the 47 IP addresses were distributed among 18 Internet service providers (ISPs) topped by Amazon.com, Inc. (11 IP addresses), Leaseweb (nine IP addresses), and DigitalOcean LLC (seven IP addresses). Nineteen IP addresses were administered by 15 other ISPs. Finally, one IP address didn’t have current ISP information.
Next, a closer look at the 47 IP addresses’ DNS records revealed that 30 of them seemed to be dedicated hosts while the remaining 16 were shared. One IP address did not seem to be actively used. We limited our next step to the potentially dedicated IP addresses, which hosted 380 domains in total after duplicates, the IoCs, and the email-connected domains were filtered out.
Two IP-connected domains seemed interesting as they could be typosquatting on legitimate brands—Walmart and Linux. While we couldn’t compare the WHOIS record of IP-connected domain walmart[.]lc to that of Walmart’s official domain walmart[.]com due to the fact that it was privacy-protected, we couldn’t publicly attribute the IP-connected domain linux-sicherheit[.]org to Linux. It didn’t have the same registrant organization in its current WHOIS record as linux[.]org.
During the course of our investigation, we noted the text strings that appeared among the IoCs.
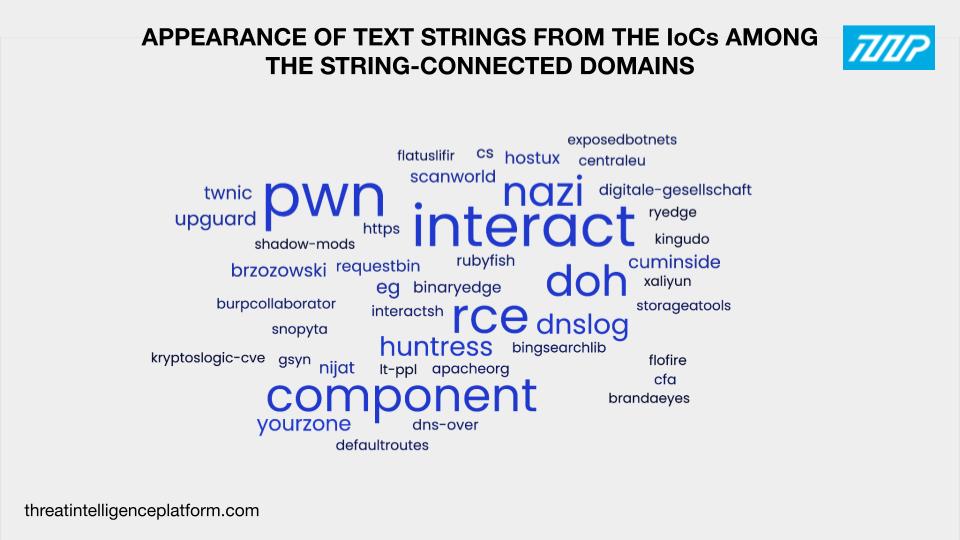
A total of 45 text strings from the domains identified as IoCs listed below appeared in other domains scattered across the DNS.
Altogether, they appeared in 2,456 domains (only sporting different TLD extensions compared to the IoCs) after duplicates, the IoCs, and email- and IP-connected domains were filtered out. Take a look at the word cloud below that depicts the number of times each text string appeared among the string-connected domains.
We also noted the appearance of three text strings from the subdomains identified as IoCs listed below in 54 other subdomains we found in the DNS that aren’t part of the IoC list.
Take a look at how frequent each string appeared among the 54 string-connected subdomains.

Our in-depth analysis of the 64 IoCs related to an ongoing Log4Shell malware campaign led to the discovery of 2,955 potentially connected web properties comprising 18 email-connected domains, 47 IP addresses, 380 IP-connected domains, 2,456 string-connected domains, and 54 string-connected subdomains. These findings can help organizations improve their cybersecurity posture, especially in dealing with this particular attack.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byDNIB.com

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign
