


|
||
|
||
The Kimsuky Group, believed to be a North Korea-based advanced persistent threat (APT) group active since 2013, struck again several times this year. They gained notoriety for launching spear-phishing attacks on targets to gain initial access. While that tactic has not changed, the actors have changed their payload delivery means—from infected Hangul Word Processor (HWP) or Microsoft Word documents to compressed files or embedded links that contained or led to the download of a malicious LNK or shortcut file.
ASEC published an in-depth investigation of the latest Kimsuky attack specifically using RftRAT and Amadey and identified six domains and seven IP addresses as indicators of compromise (IoCs), namely:
| KIMSUKY ATTACK IoCs | |
|---|---|
| DOMAINS | IP ADDRESSES |
| brhosting[.]net | 152[.]89[.]247[.]57 |
| prohomepage[.]net | 172[.]93[.]201[.]248 |
| splitbusiness[.]com | 192[.]236[.]154[.]125 |
| techgolfs[.]com | 209[.]127[.]37[.]40 |
| theservicellc[.]com | 23[.]236[.]181[.]108 |
| topspace[.]org | 45[.]76[.]93[.]204 |
| 91[.]202[.]5[.]80 | |
The WhoisXML API research team sought to find other potential entry points the Kimsuky Group could exploit in future attacks by expanding the list of IoCs the AhnLab researchers published. Our DNS deep dive led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
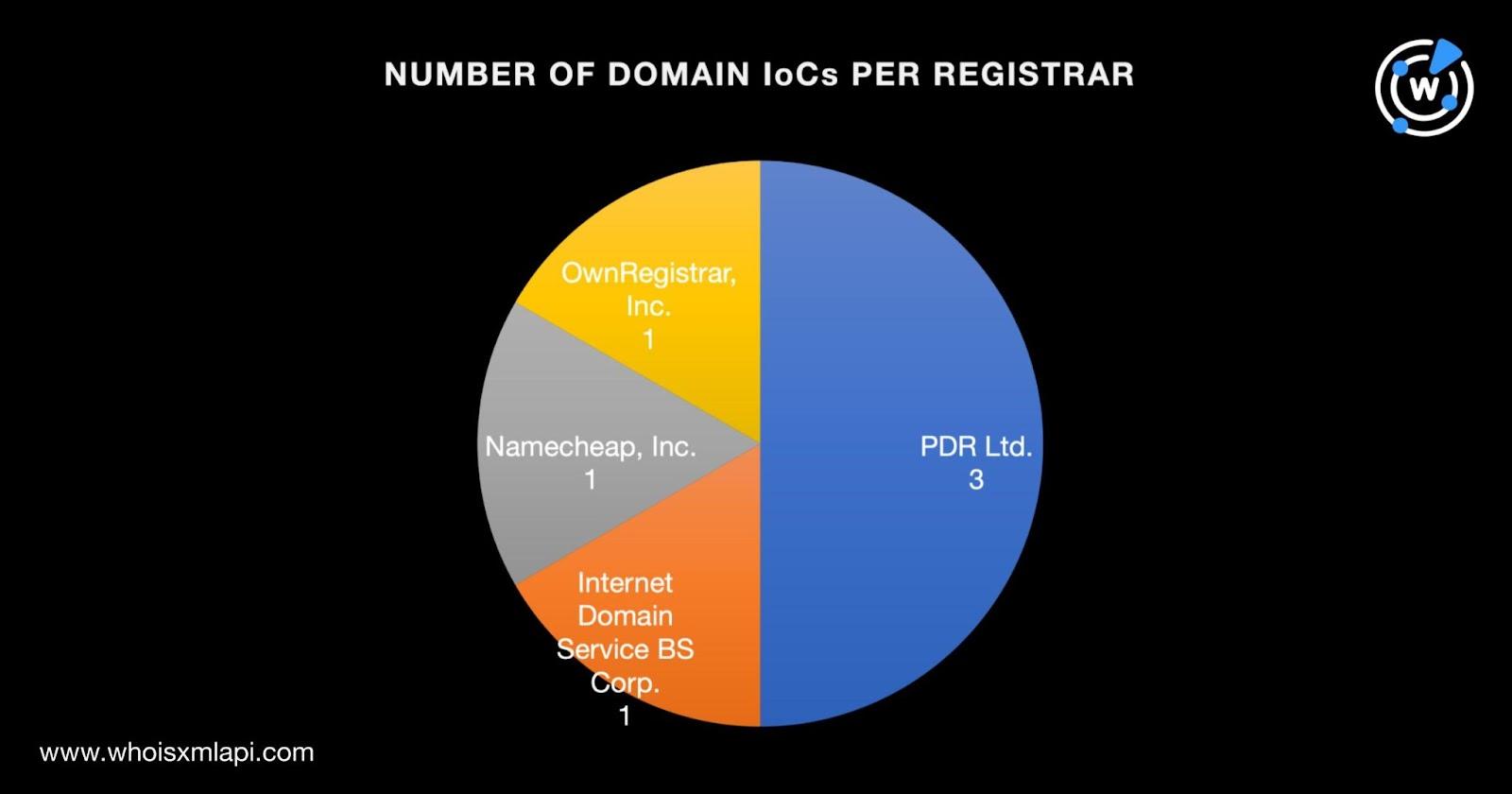
As usual, we started our analysis by taking a closer look at the 13 web properties—six domains and seven IP addresses identified as IoCs.
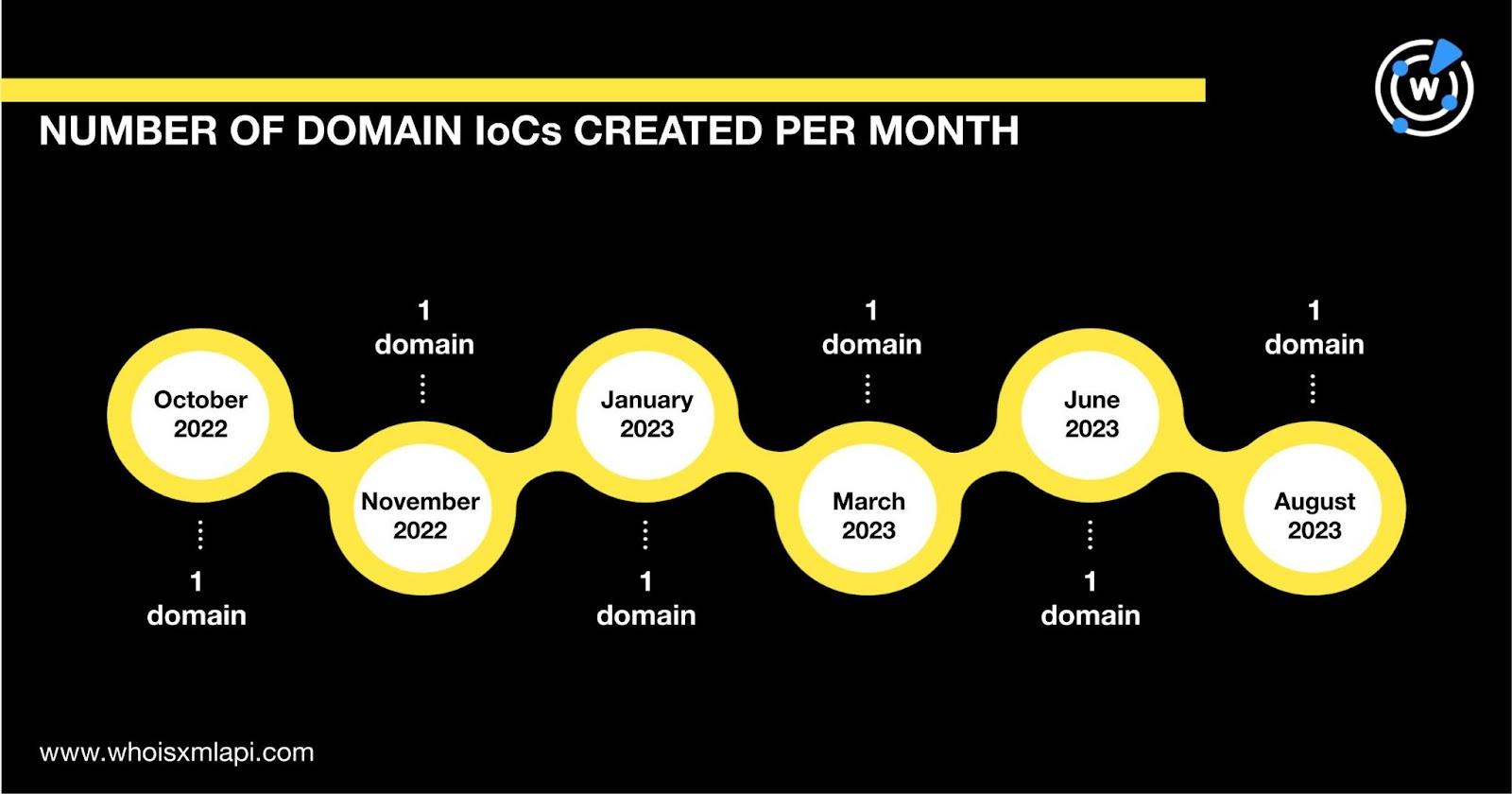
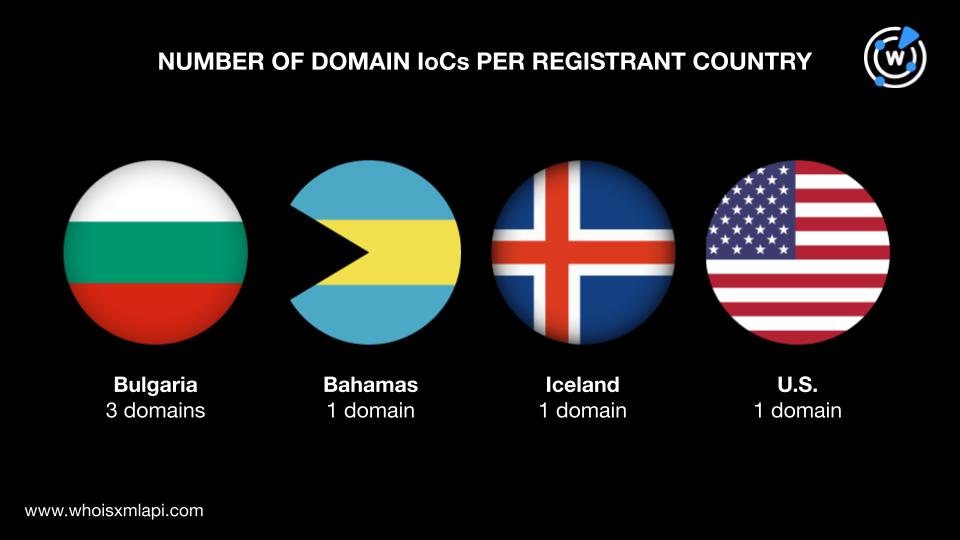
A bulk WHOIS lookup for the six domains revealed that:
They were created recently—two in 2022 and four in 2023.
They were spread across four registrant countries led by Bulgaria, which accounted for three domains. One domain each identified Bahamas, Iceland, and the U.S. as their registrant countries.
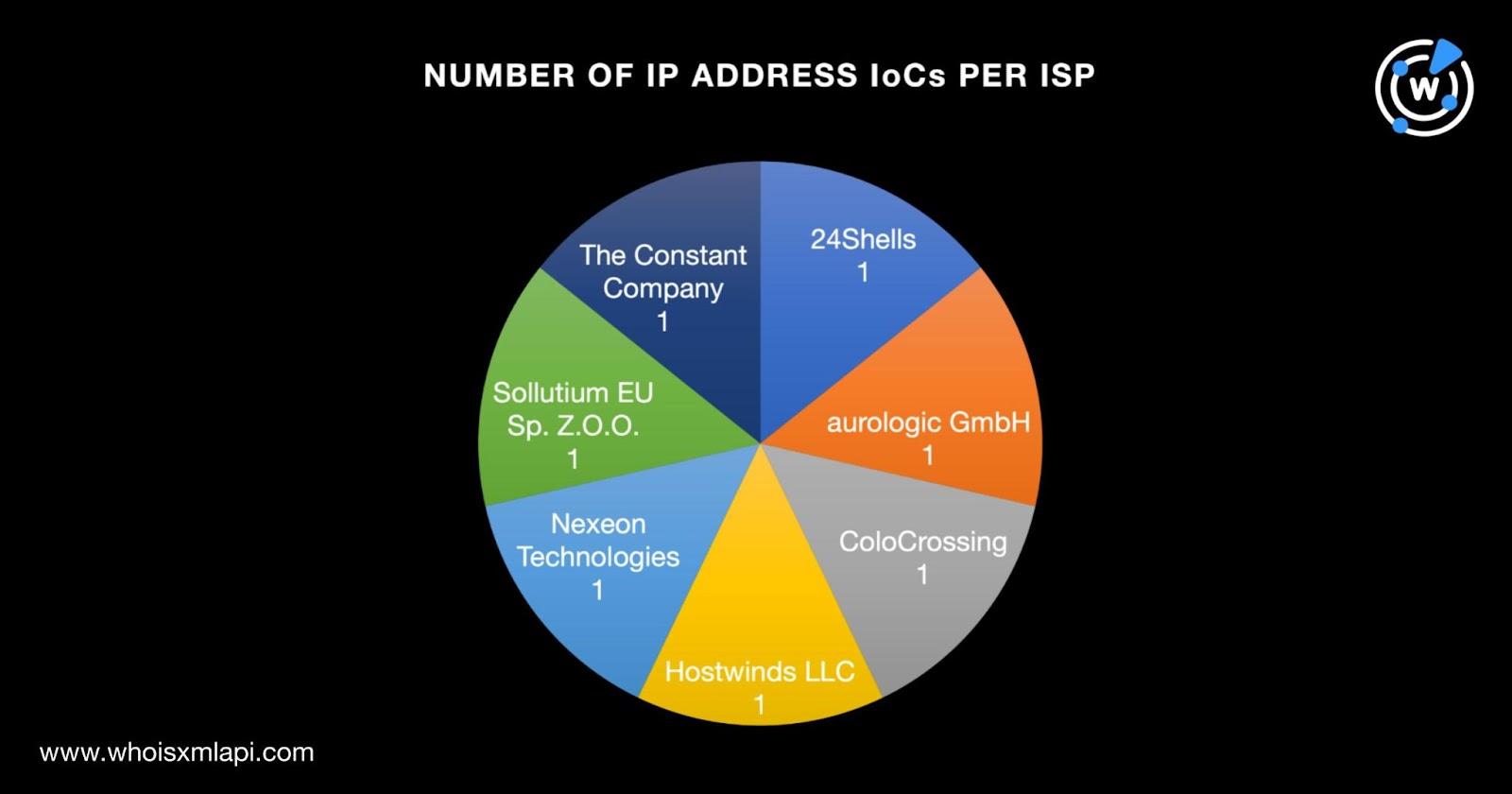
Next, we ran the seven IP addresses through a bulk IP geolocation lookup and found that:

They were spread across seven Internet service providers (ISPs) that accounted for one IP address each—24Shells, aurologic GmbH, ColoCrossing, Hostwinds LLC, Nexeon Technologies, Sollutium EU Sp. Z.O.O., and The Constant Company.
In a bid to obtain as much information about the current Kimsuky Group attack infrastructure, we performed an expansion analysis beginning with WHOIS History API searches for the six domains identified as IoCs. Our queries led to the discovery of 30 email addresses found anywhere in their historical WHOIS records.
Seven of them were public email addresses. We subjected them to reverse WHOIS searches, which revealed that three of them also appeared in the current WHOIS records of 336 domains. None of them had duplicates nor have already been identified as IoCs.
It is interesting to note that 29 of them could figure in cryptocurrency-, blockchain-, or nonfungible token (NFT)-related threats should they get weaponized. The following table shows some examples.
| TEXT STRING | SAMPLE EMAIL-CONNECTED DOMAIN |
|---|---|
| blockchain | ablockchaincompany[.]com |
| bitcoin | bitcoinmover[.]com |
| btc | btclightningnetwork[.]com |
| coin | coinmarket[.]ca |
| crypto | cryptoadept[.]com |
| matrix | matrixcoin[.]net |
| meta | metapayment[.]ca |
| nft | nfttrader[.]ca |
| token | tokenpromoter[.]com |
Screenshot lookups also showed that the websites 37 of the email-connected domains pointed to remained accessible as of this writing. Only eight of them, however, led to functional websites.
Next, we performed DNS lookups on the six domains identified as IoCs and found that they resolved to five unique IP addresses that have not yet been identified as IoCs.
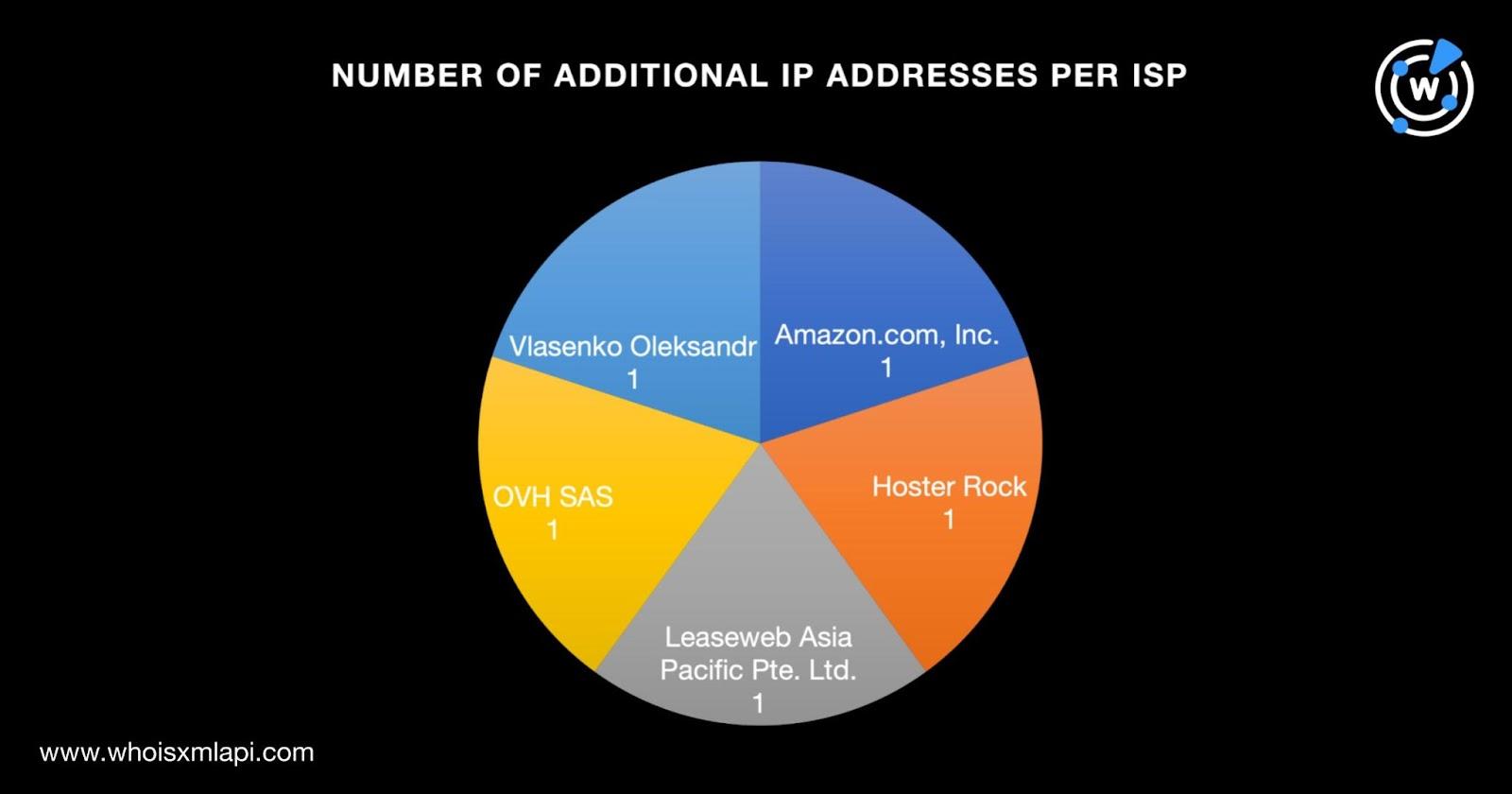
IP geolocation lookups for the five IP addresses showed that:

They were administered by five different ISPs—Amazon.com, Inc.; Hoster Rock; Leaseweb Asia Pacific Pte. Ltd.; OVH SAS; and Vlasenko Oleksandr. None of them shared the ISPs of the IP addresses identified as IoCs.
To further our search for possibly connected artifacts, we ran reverse IP lookups for the 12 IP addresses—seven identified as IoCs and five additional from our DNS lookups. We discovered that five of them could be dedicated and played host to five domains that were not part of the lists of domain IoCs and email-connected domains.
Based on screenshot lookups, only one IP-connected domain continued to host live content—thesisterize[.]gb[.]net.
As a final step, we ran Domains & Subdomains Discovery searches for text strings found among the domains identified as IoCs, namely:
That led to the discovery of 356 string-connected domains after duplicates, the IoCs, and email- and IP-connected domains were filtered out. Note that we used the Contains parameter and included all the domains in our repository (collated over the past decade or so). Screenshot lookups revealed that 34 of them continued to point to live websites.
Our more in-depth investigation into the latest set of Kimsuky Group attack IoCs, specifically those that used the RftRAT and Amadey malware, allowed us to uncover 702 possibly connected artifacts—336 email-connected domains, five IP addresses, five IP-connected domains, and 356 string-connected domains.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byRadix

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byCSC
