


|
||
|
||
Mandiant’s Managed Defense Threat Hunting Team recently published an in-depth study of the malware distributed via what they have dubbed the “UNC2975 malvertising campaign.” Users who have been tricked into clicking poisoned sponsored search engine results and social media posts ended up with computers infected with either the DANABOT or DARKGATE backdoor.
Mandiant’s in-depth analysis of the threat led to the identification of 28 indicators of compromise (IoCs), specifically 19 domains and nine IP addresses. The WhoisXML API research team, in an effort to find more information and possibly connected artifacts that have not been identified to date, expanded the list of IoCs and uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
As is our usual first step, we sought to find more information on the domains and IP addresses that Mandiant identified as IoCs.
We began by performing a bulk WHOIS lookup on the 19 domains and found that:
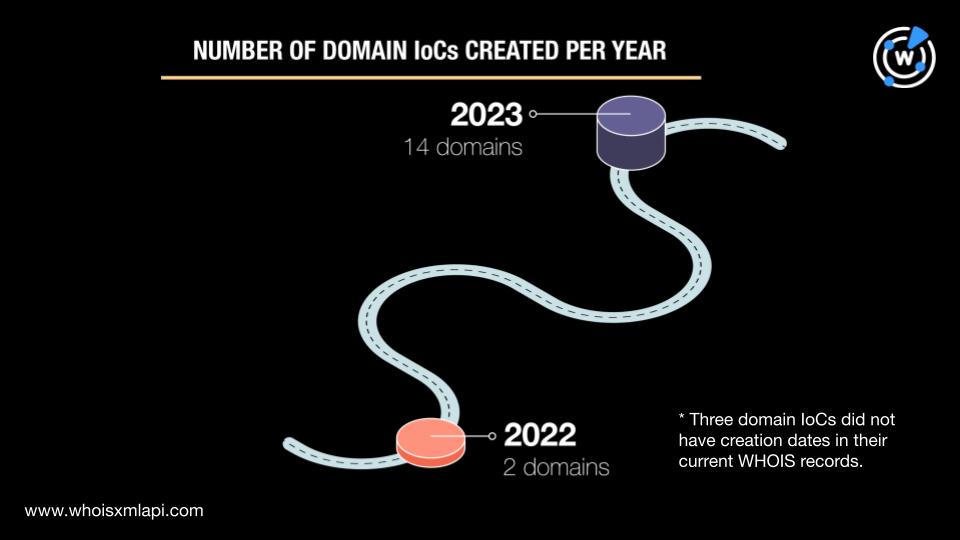
A majority of them were relatively new—14 were created in 2023 and two in 2022. The remaining three domains did not have creation dates retrievable from current WHOIS records.
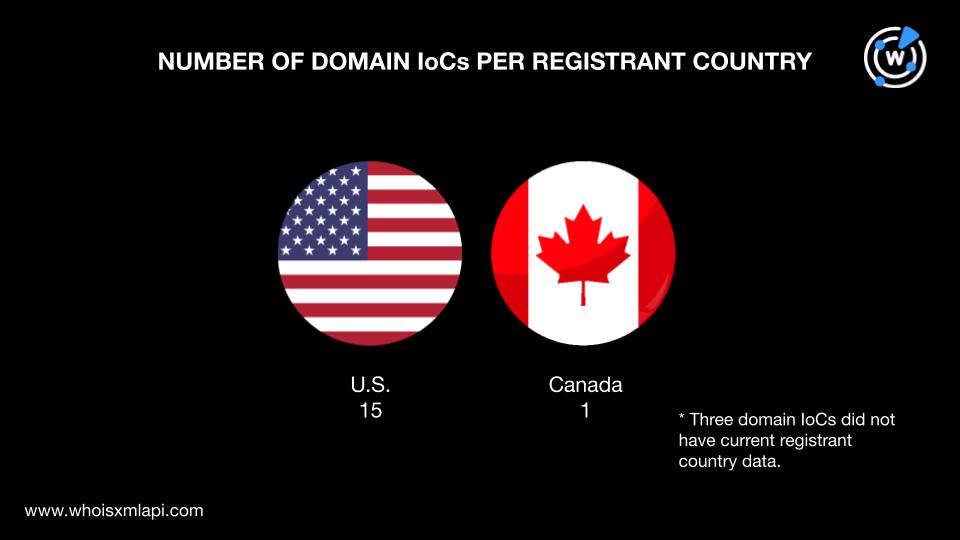
They were spread across two registrant countries—15 domains were supposedly registered in the U.S. and one in Canada. Three domains did not have current registrant country data.
Next, we subjected the nine IP addresses to a bulk IP geolocation lookup, which revealed that:
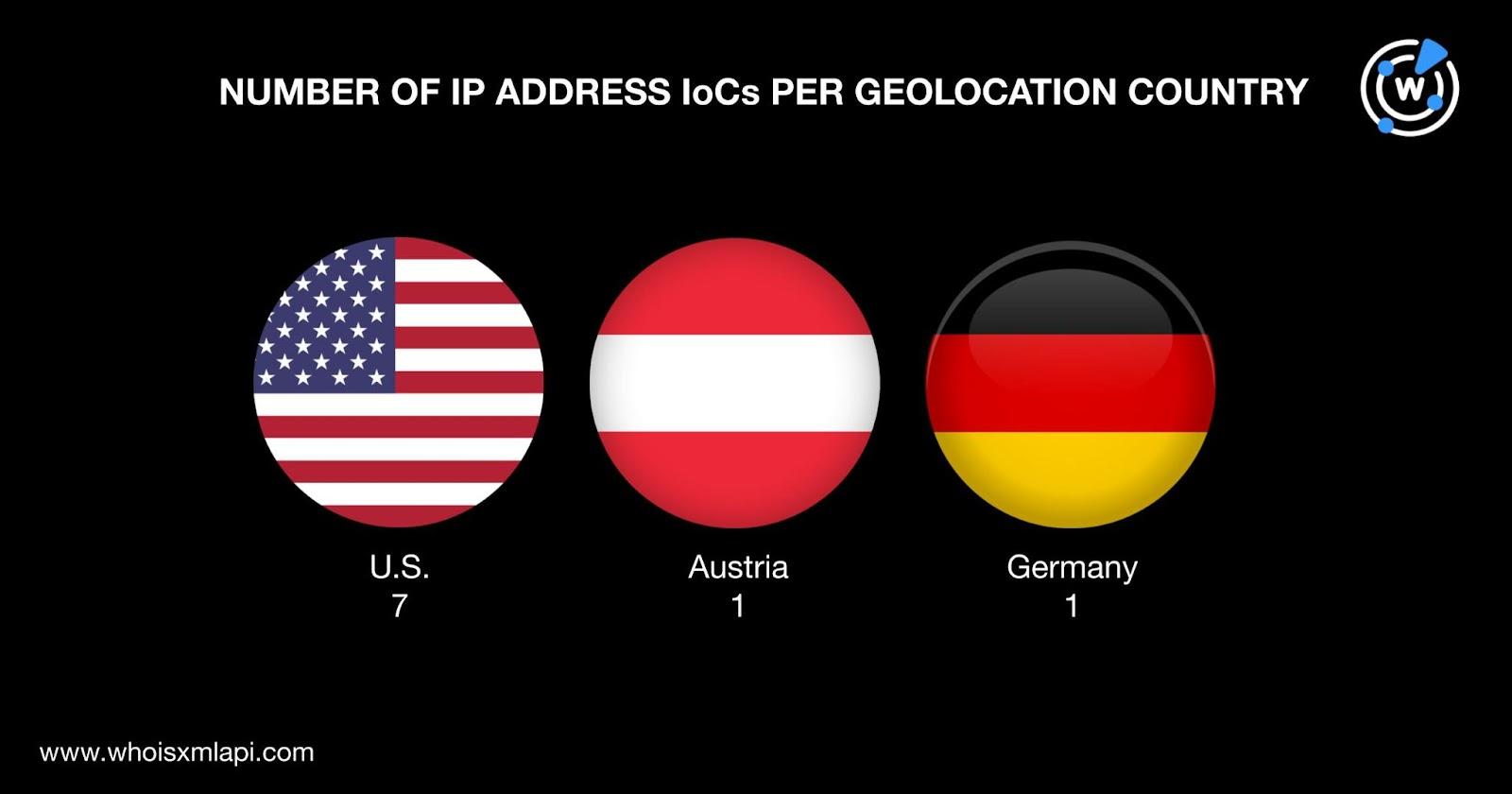
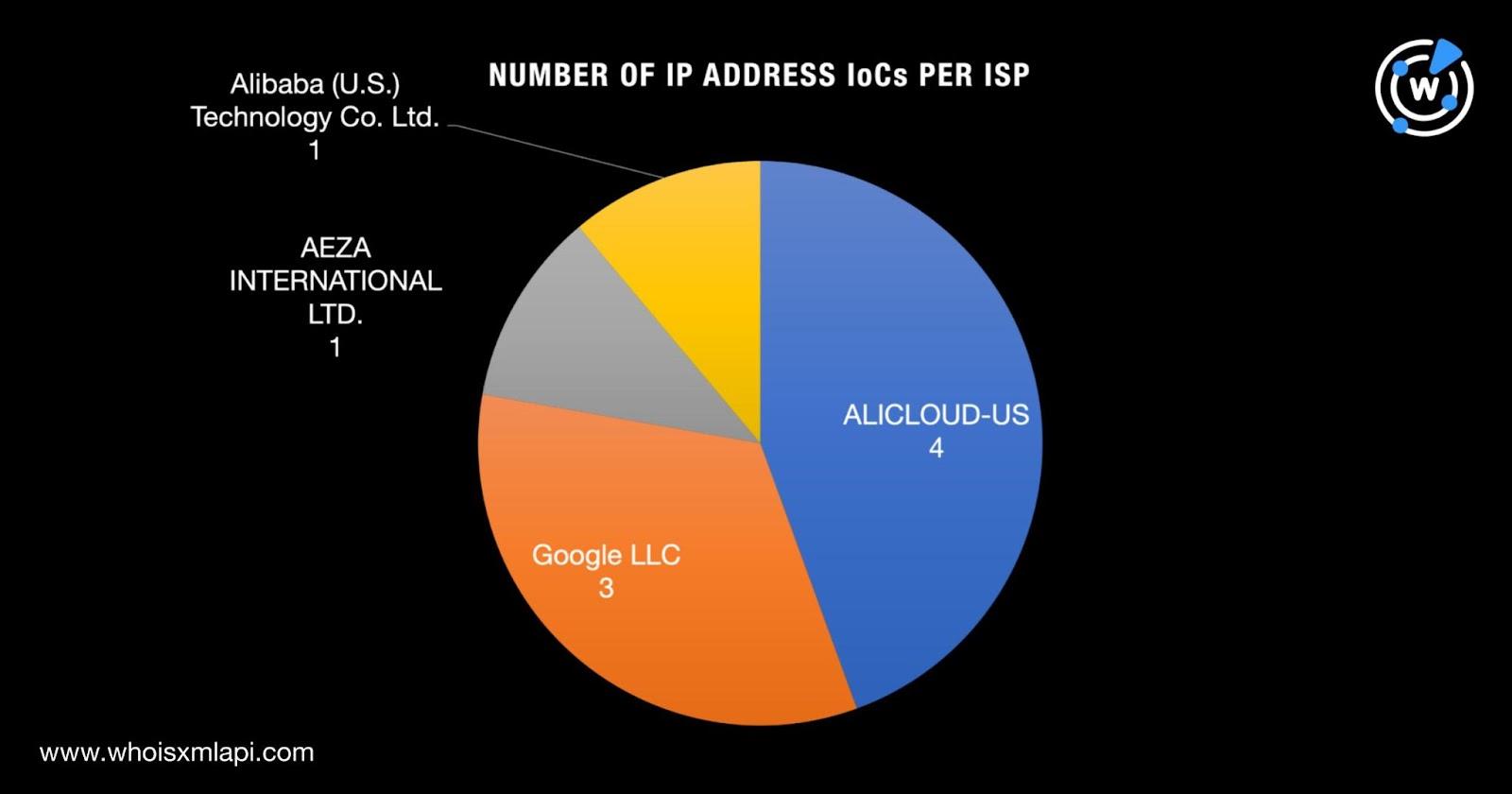
They were administered by four Internet service providers (ISPs) topped by ALICLOUD-US with four IP addresses. Google LLC handled three IP addresses and AEZA INTERNATIONAL LTD. and Alibaba (U.S.) Technology Co. Ltd. managed one IP address each.
To unveil as many potentially connected UNC2975 artifacts as possible, we looked at the WHOIS records of the 19 domains identified as IoCs first.
WHOIS History API searches showed that seven of them had 15 email addresses in total in their WHOIS records, 13 of which were public.
Next, Reverse WHOIS API searches for the 13 public email addresses revealed that only five were present in the current WHOIS records of 239 other domains after duplicates and the IoCs were filtered out.
Screenshot API searches for the 239 email-connected domains showed that only one continued to host live content as of this writing.

We then subjected the 19 domains identified as IoCs to DNS lookups and found that 10 of them actively resolved to 13 IP addresses after duplicates and those already identified as IoCs were removed.
Threat Intelligence API searches for the 13 additional IP addresses showed that all of them were associated with various threats. Take a look at our specific findings for each below.
| IP ADDRESS | NUMBER OF ASSOCIATED THREATS | ASSOCIATED THREAT TYPES |
|---|---|---|
| 104[.]21[.]29[.]244 | 3 | Generic Phishing Malware |
| 104[.]21[.]4[.]50 | 3 | Malware Phishing Generic |
| 104[.]21[.]43[.]177 | 3 | Malware Phishing Generic |
| 104[.]21[.]62[.]212 | 1 | Malware |
| 104[.]21[.]65[.]69 | 1 | Malware |
| 104[.]21[.]69[.]249 | 3 | Phishing Malware Generic |
| 172[.]67[.]131[.]172 | 3 | Malware Phishing Generic |
| 172[.]67[.]139[.]87 | 1 | Malware |
| 172[.]67[.]150[.]3 | 3 | Generic Phishing Malware |
| 172[.]67[.]182[.]165 | 3 | Malware Phishing Generic |
| 172[.]67[.]189[.]35 | 1 | Malware |
| 172[.]67[.]216[.]21 | 3 | Phishing Malware Generic |
| 91[.]195[.]240[.]12 | 5 | Malware Phishing Generic SuspiciousC2 |
A bulk IP geolocation lookup for the additional 13 IP addresses revealed that:

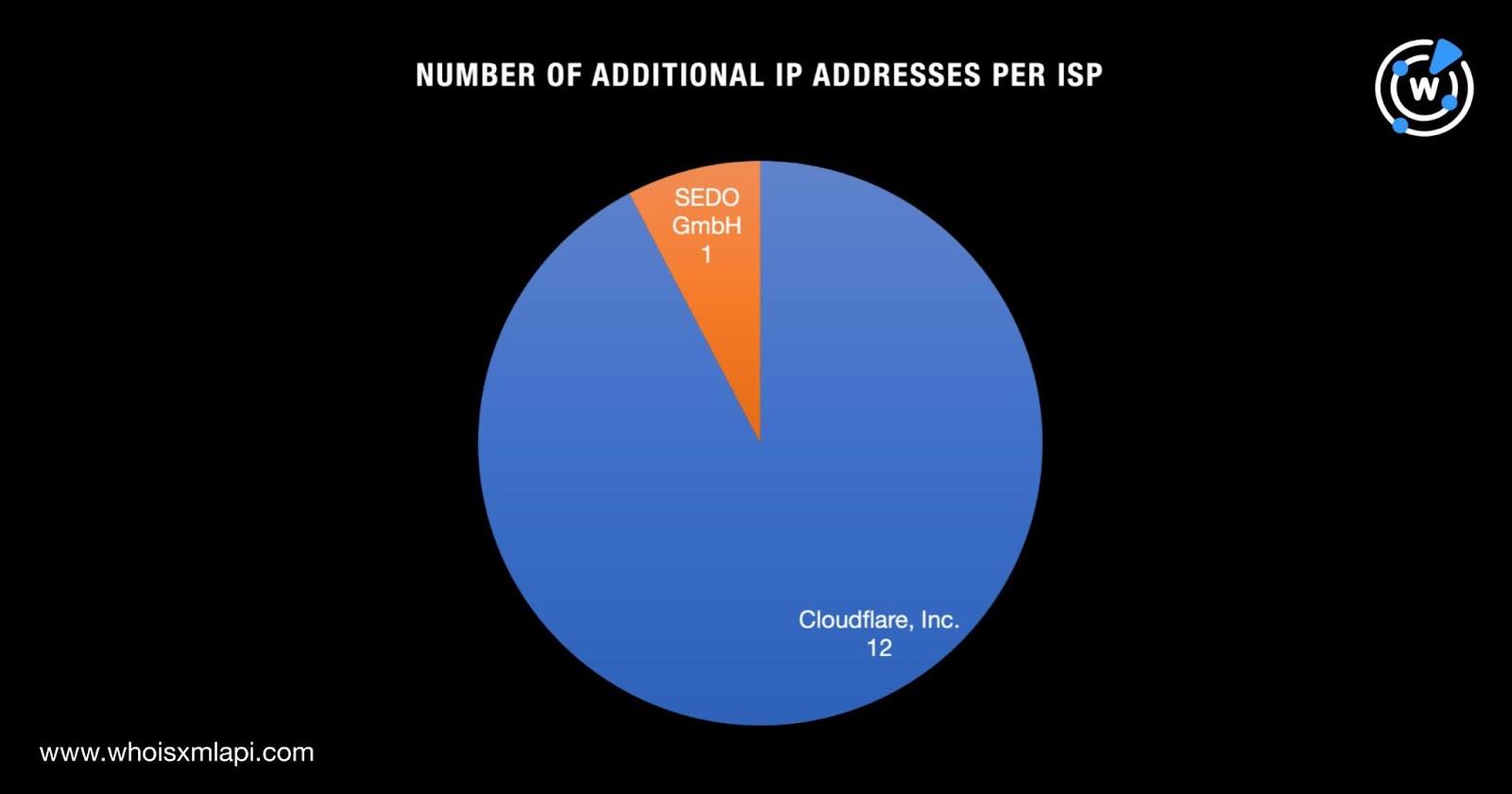
A huge chunk of them, 12 to be exact, were administered by Cloudflare, Inc. One was under the purview of SEDO GmbH. None of them had the same ISP as any of the IP addresses identified as IoCs.
Next, we subjected the 22 IP addresses, the nine identified as IoCs and 13 additional, to reverse IP lookups and found that three of them seemed to be dedicated hosts. Altogether, they hosted three additional domains after the duplicates, IoCs, and email-connected domains were filtered out.
To cover all of our bases, we further scrutinized the 19 domains identified as IoCs and found that they contained text strings that appeared in 2,772 other domains after duplicates, the IoCs, and email- and IP-connected domains were removed. We specifically used the following as search strings on Domains & Subdomains Discovery using the Starts with parameter:
Screenshot lookups for the string-connected domains revealed that 379 continued to host live content to date. String-connected domain whatuptrepstars[.]com, in particular, proved interesting in that it led to what seemed to be a Facebook login page even if it could not be publicly attributed to the social media platform based on its WHOIS record details.

In addition, based on Threat Intelligence API checks, the string-connected domain halibut[.]site was associated with one threat, specifically malware.
Our follow-up investigation on UNC2975 led to the discovery of 3,027 email-, IP-, and string-connected artifacts. It is also worth noting that 14 of them—13 IP addresses and one string-connected domain—were associated with threats or have already been classified as malicious.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byVerisign

Sponsored byRadix
