


|
||
|
||
Computers that get infected with the Epsilon stealer could spell game over for serious gamers, but they are not the only ones at risk. The creators of games like EPSILON, Pokemon, and Roblox that the malware operators are mimicking stand to lose a lot as well. They may lose customers and damage their reputation in the process.
Epsilon steals not only user credentials but also personal data, in-game assets, and other sensitive information using Discord messages and fake game download sites. Sekoia.io security researchers published an in-depth analysis of the data stealer and named 133 domains and subdomains as indicators of compromise (IoCs). We extracted 76 domainsfrom their list for our ex.
The WhoisXML API research team expanded the IoC list to find unpublished connected threat artifacts using our massive DNS intelligence repositories and found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
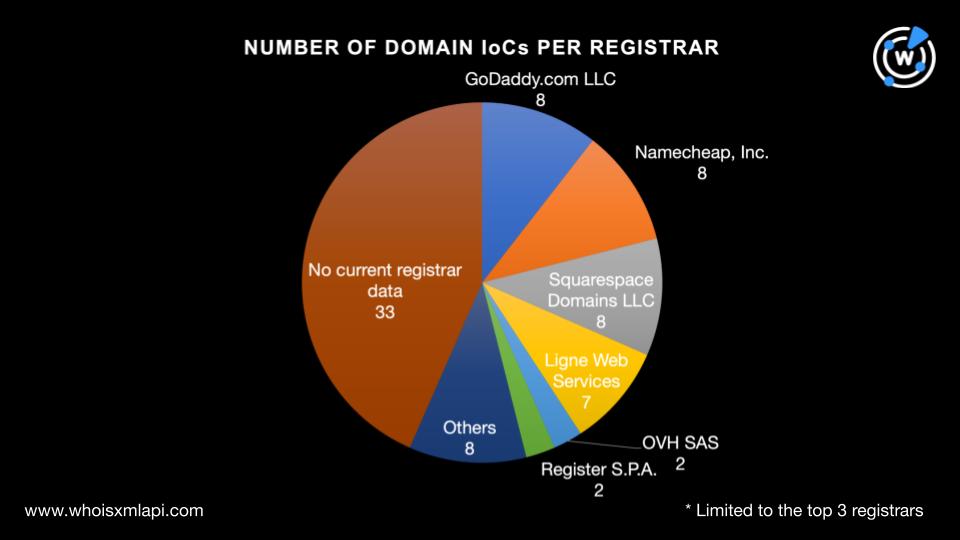
To begin our analysis, we sought to find as much information as possible on the 76 domains tagged as IoCs starting with a bulk WHOIS lookup, which revealed that:
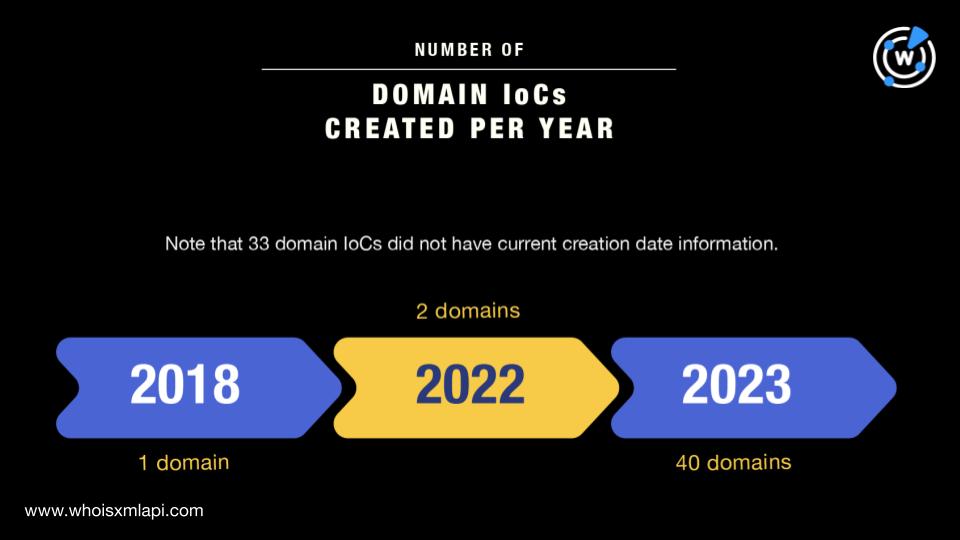
Forty-three of them were created between 2018 and 2023 while the remaining 33 did not have creation date information in their current WHOIS records.
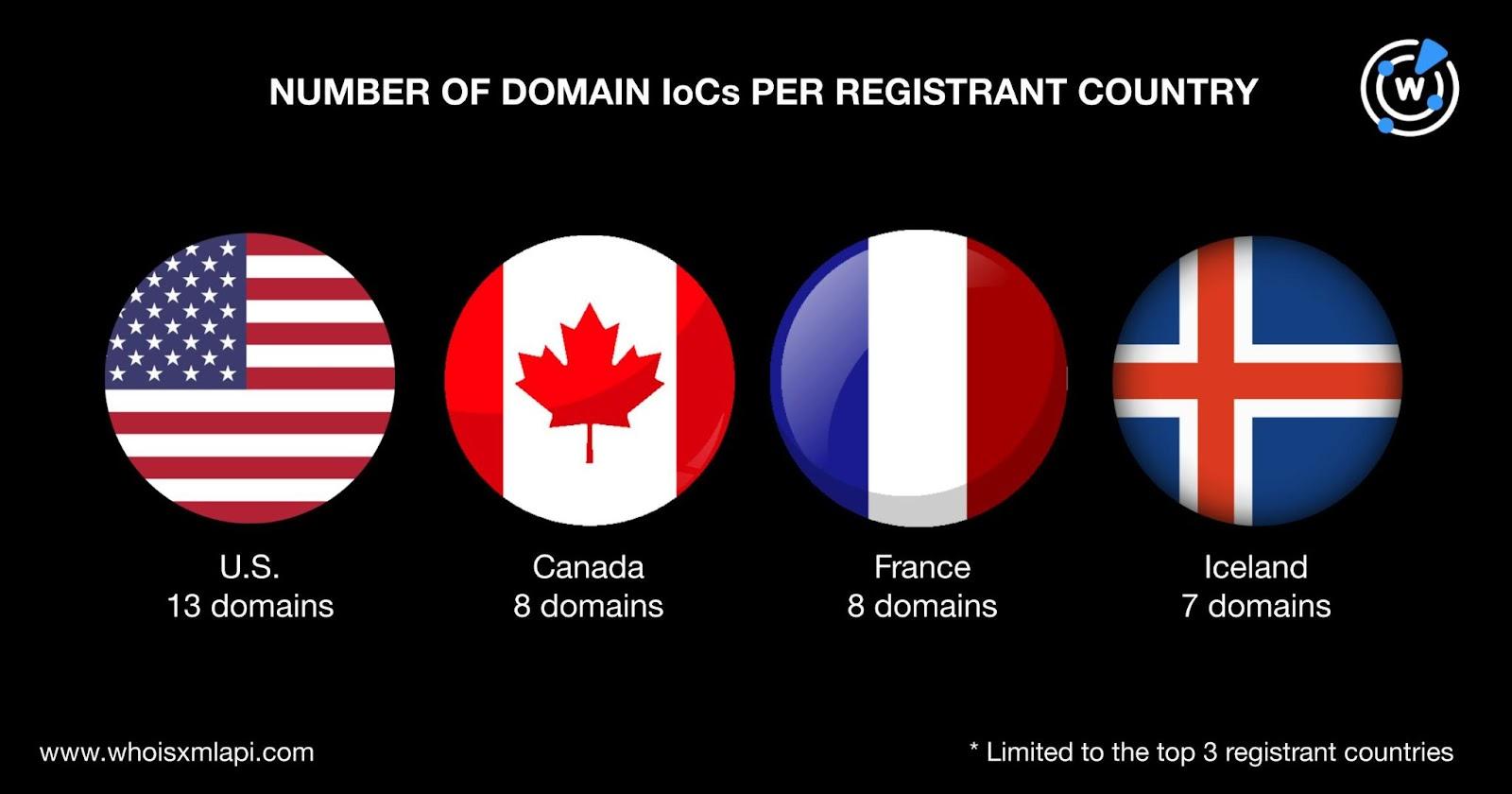
The top 3 registrant countries were the U.S., which accounted for 13 domains; Canada and France with eight domains each; and Iceland with seven domains. One domain each was created in Cyprus, the Netherlands, Romania, and Turkey while 37 did not have current registrant country data.
It is also worth noting that one of them—plaguehunter[.]com—had a publicly viewable registrant name.
To expand the current list of Epsilon stealer IoCs, we began by looking into their historical WHOIS records.
WHOIS History API revealed that 31 of the 76 domains classified as IoCs had 32 email addresses in their historical WHOIS records. Nine of them were public email addresses.
Subjecting the nine public email addresses to Reverse WHOIS API queries allowed us to determine they were present in the current WHOIS records of 74 other domains (email-connected) after duplicates and those already part of the current IoC list were filtered out.
DNS lookups for the 76 domains tagged as IoCs revealed that 22 of them had active IP resolutions. They resolved to 33 IP addresses after duplicates were removed.
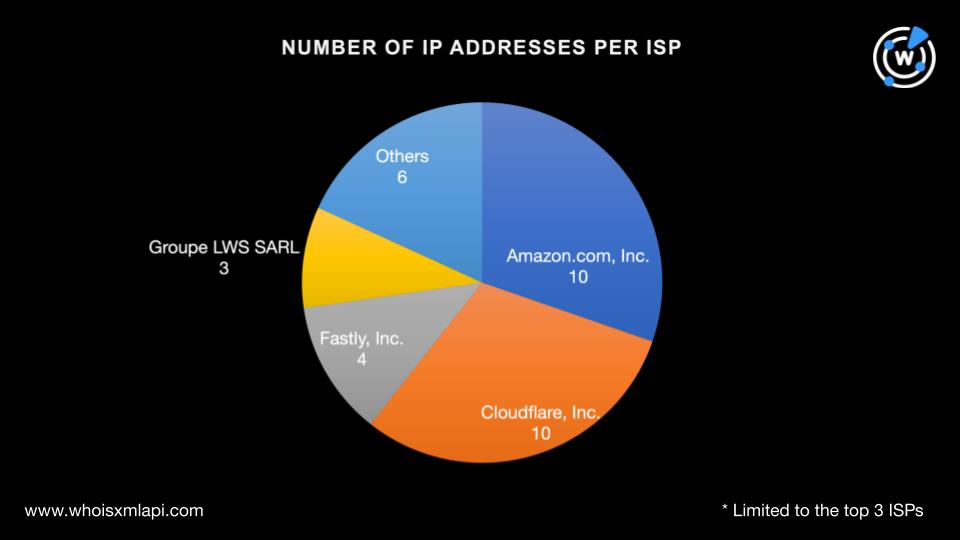
Performing IP geolocation lookups for the 33 IP addresses led to these interesting findings:

They were spread across 10 Internet service providers (ISPs) led by Amazon.com, Inc. and Cloudflare, Inc. with 10 IP addresses each. Fastly, Inc. took the second spot with four IP addresses. Groupe LWS SARL took third place with three IP addresses. Six other ISPs accounted for one IP address each.
Twenty-eight of them were flagged as malicious by the built-in Threat Intelligence API engine. Take a look at the tool’s detailed findings for five of the IP addresses below.
| IP ADDRESS | ASSOCIATED THREAT TYPE | DATE FIRST SEEN |
|---|---|---|
| 104[.]21[.]0[.]216 | Generic Malware Phishing | 29 March 2023 |
| 104[.]21[.]61[.]207 | Malware Suspicious | 5 April 2023 |
| 104[.]21[.]63[.]236 | Generic Malware Phishing | 21 May 2023 |
| 13[.]248[.]169[.]48 | C2Generic Malware Phishing Suspicious | 28 March 2023 |
| 13[.]248[.]213[.]45 | C2Generic Malware Phishing Suspicious | 7 December 2023 |
Finally, to cover all our bases, we used Domains & Subdomains Discovery to look for domains containing 48 text strings that appeared in the IoCs, namely:
We uncovered 1,623 string-connected domains, two of which were flagged as malicious by Threat Intelligence API. See the details in the table below.
| STRING-CONNECTED DOMAIN | ASSOCIATED THREAT TYPE | DATE FIRST SEEN |
|---|---|---|
| dualcorps[.]site | Generic | 2 November 2023 |
| unturnedplayable[.]com | Phishing | 9 March 2023 |
Our deep dive into Epsilon Stealer led to the discovery of 1,730 potentially connected threat artifacts, including 28 malicious IP addresses and two malware-laden string-connected domains.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byVerisign

Sponsored byRadix

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byIPv4.Global
