


|
||
|
||
The Mirai botnet, first discovered way back in 2016, made headlines and gained infamy as the biggest botnet to hit networks the world over. It has resurfaced with multiple ways of infecting Internet of Things (IoT) devices and the ability to launch zero-day exploits.
XLab researchers performed a thorough analysis of what they’ve dubbed “Mirai.TBOT” and identified 112 domains and 22 IP addresses as indicators of compromise (IoCs) in the process. We expanded the published list of IoCs to determine other potential infection avenues and found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our investigation by taking a closer look at the 134 IoCs.
A bulk WHOIS lookup for the 112 domains identified as IoCs revealed that:
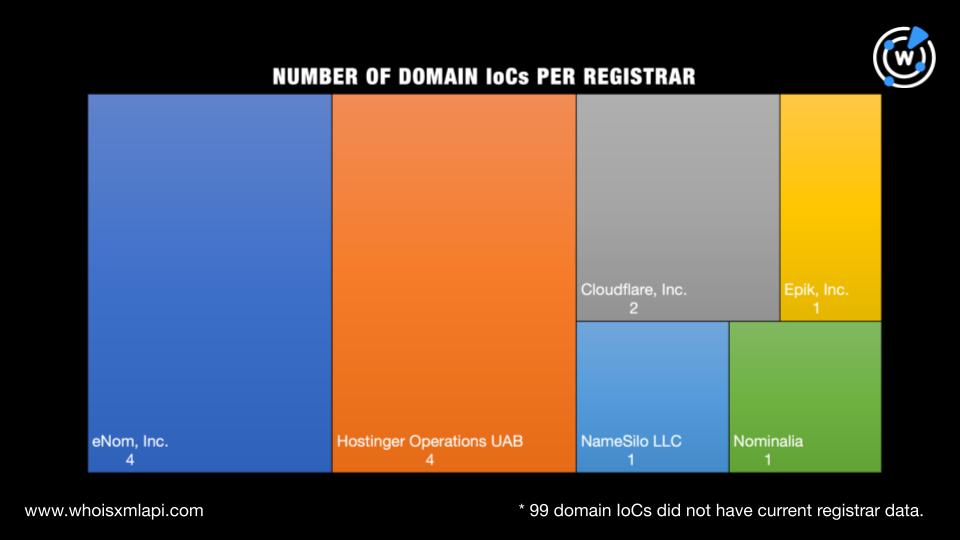
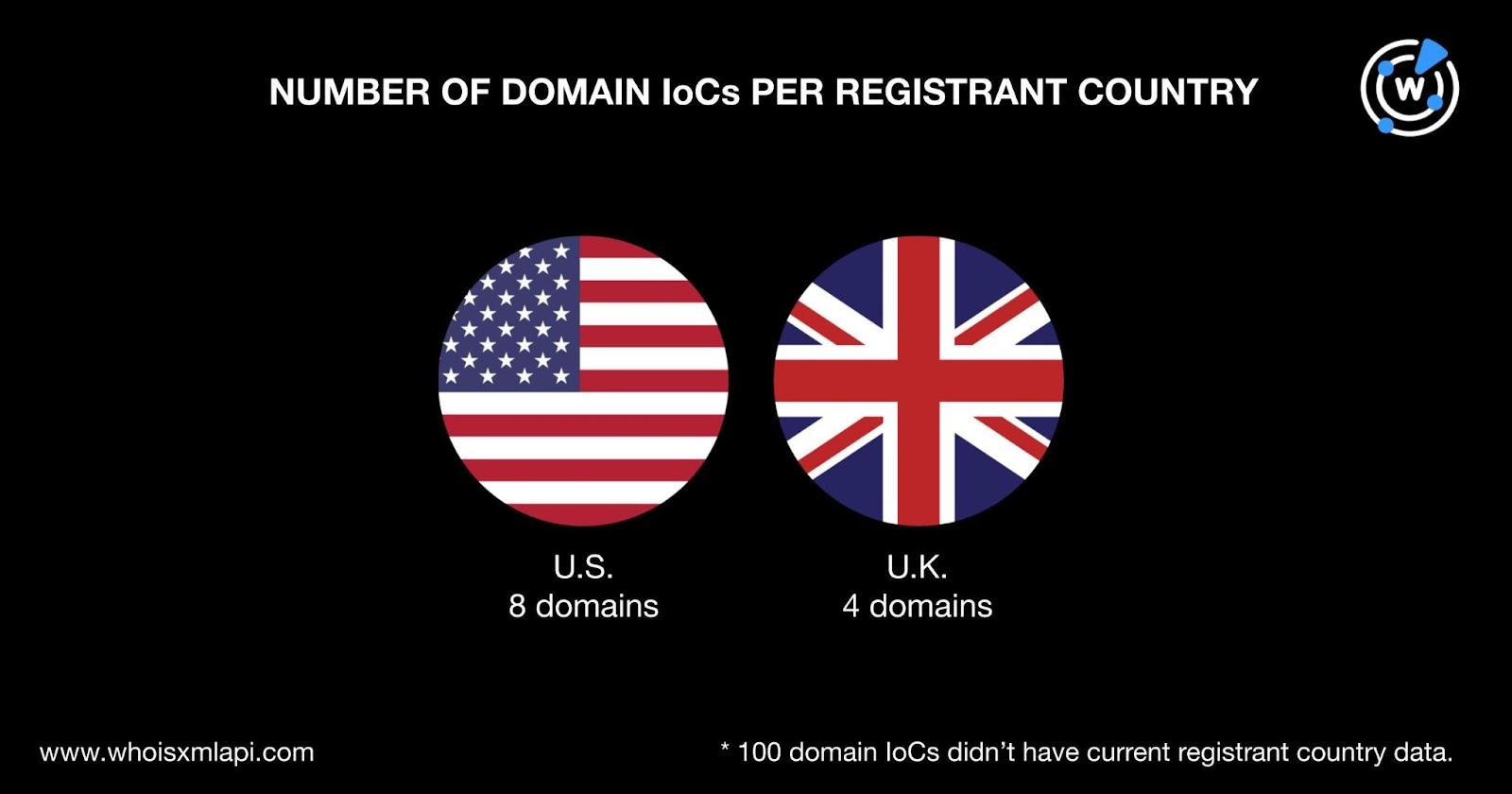
The U.S. was the top registrant country, accounting for eight domains. Four domains were registered in the U.K. while the remaining 100 didn’t have registrant country information in their current WHOIS records.
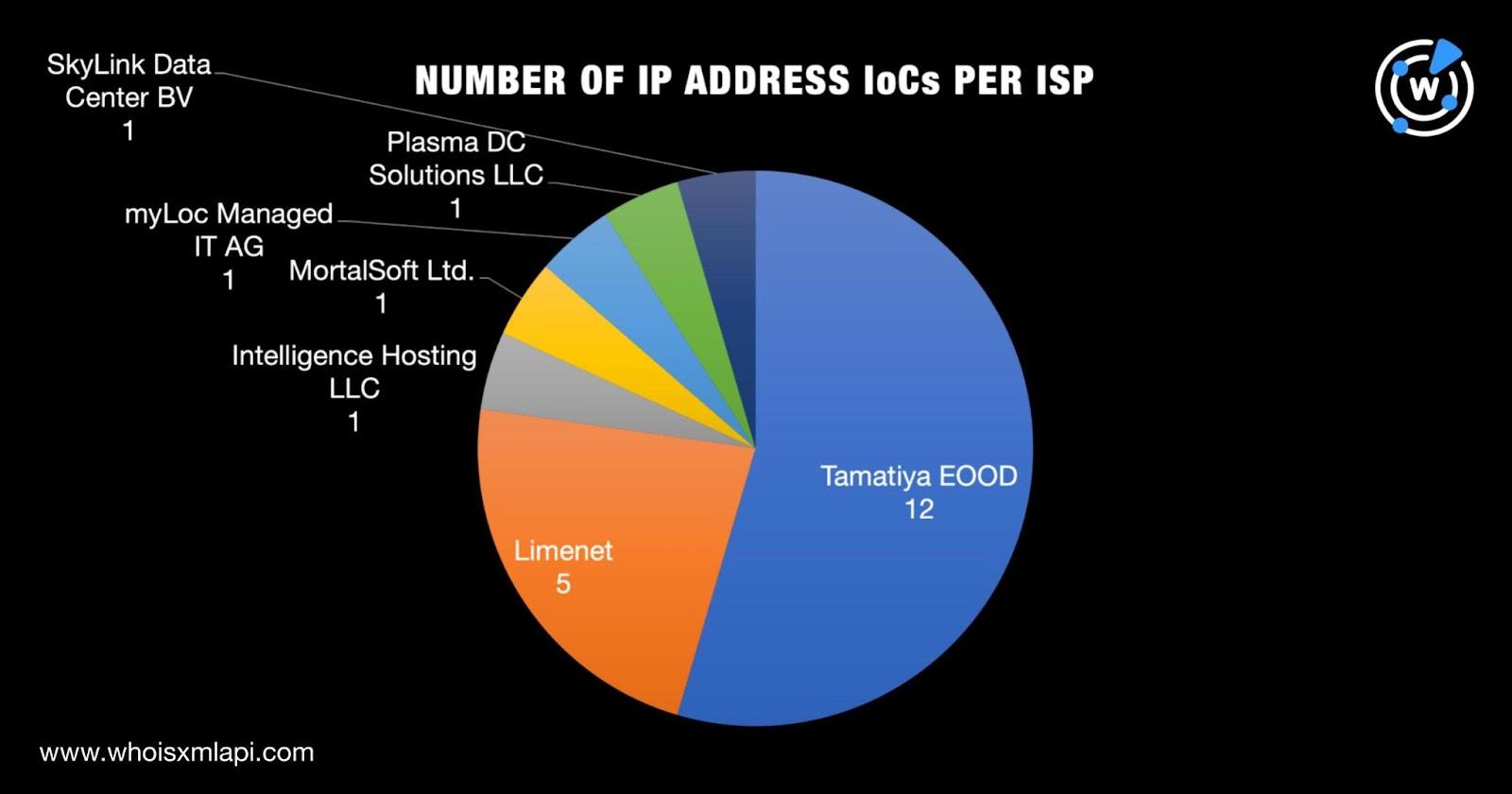
Next, we subjected the 22 IP addresses to a bulk IP geolocation lookup and found that:

They were spread across seven Internet service providers (ISPs) topped by Tamatiya EOOD, which accounted for 12 IP addresses. Limenet placed second with five. The five remaining IP addresses were split among the same number of ISPs, namely, Intelligence Hosting LLC, MortalSoft Ltd., myLoc Managed IT AG, Plasma DC Solutions LLC, and SkyLink Data Center BV.
Now, on to finding more Mirai.TBOT traces in the DNS.
Our search for email-connected domains started with WHOIS History API searches that led to the discovery of nine email addresses in the domain IoCs’ historical WHOIS records, three of which were public.
Reverse WHOIS API searches showed that one public email address appeared in the current WHOIS record of one domain—qqmmqqw[.]cn—after duplicates and those already tagged as IoCs were removed.
Next, we performed DNS lookups on the 112 domain IoCs that enabled us to collate 13 IP addresses after duplicates and those that were already part of the original IoC list were filtered out.
IP geolocation lookups for the 13 additional IP addresses showed that:
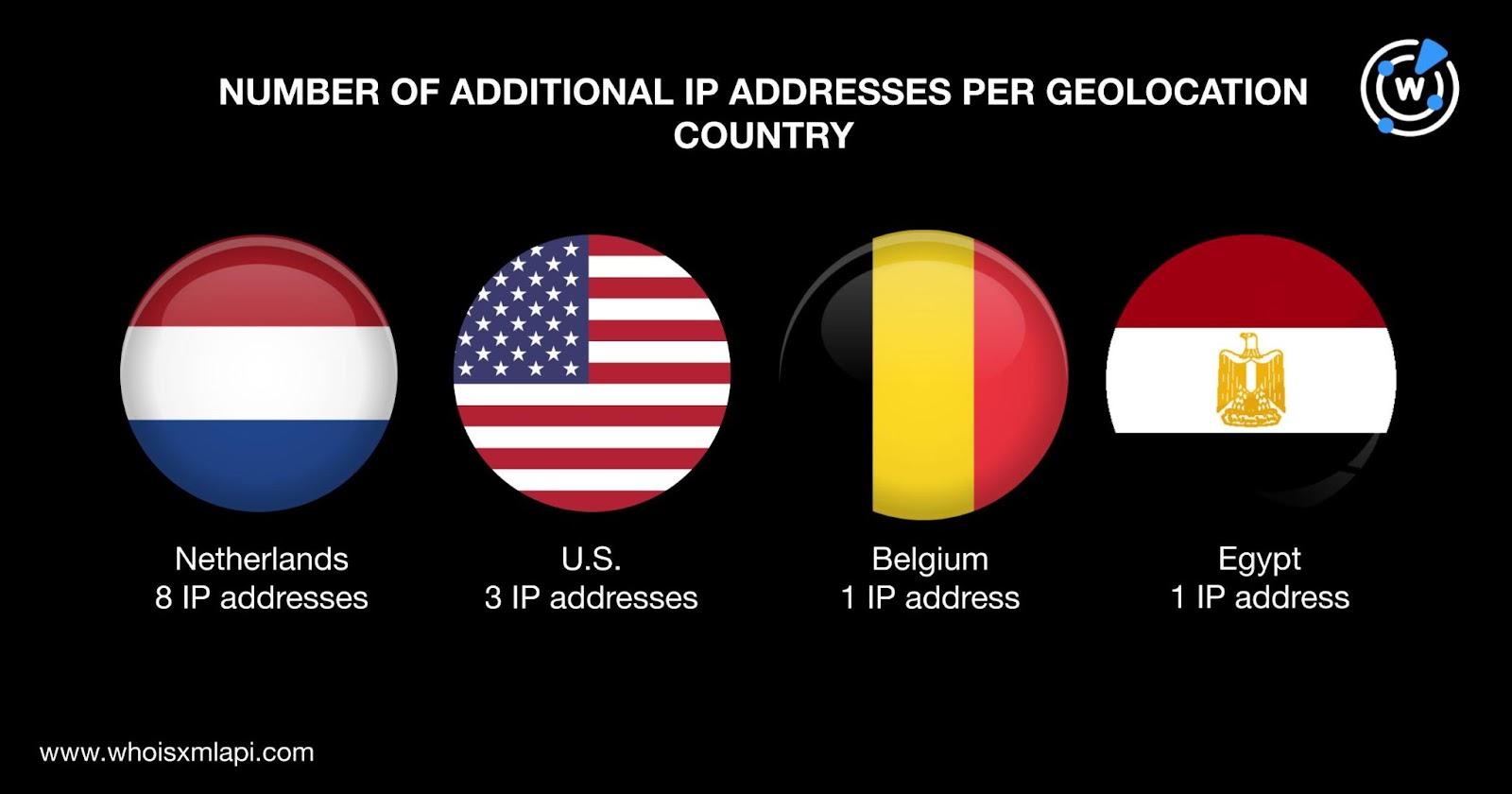
Twelve of the additional IP addresses shared three of the IoCs’ geolocation countries—the Netherlands, the U.S., and Belgium.
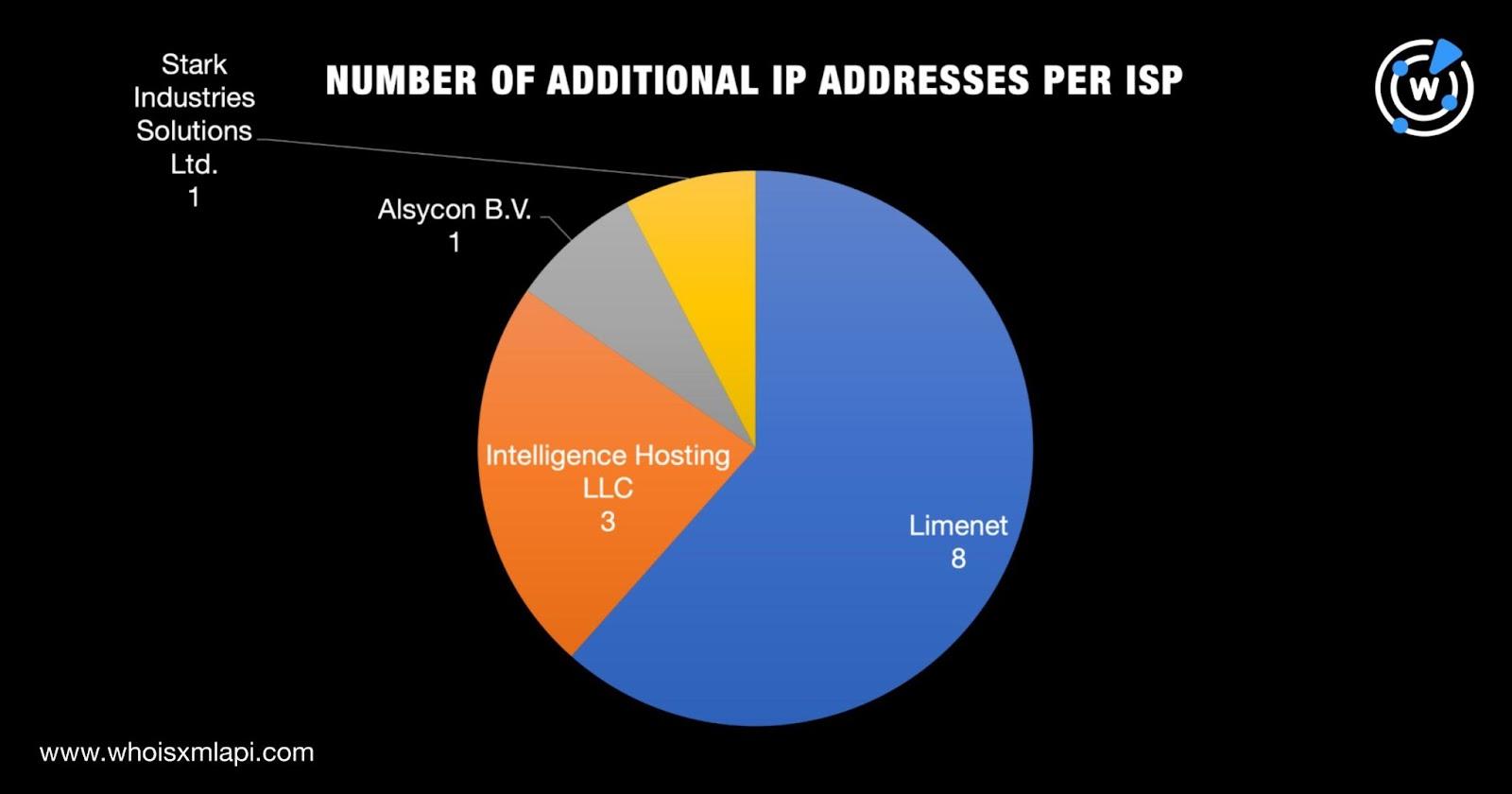
They were administered by four ISPs—Limenet (8 IP addresses), Intelligence Hosting LLC (3 IP addresses), and Alsycon B.V. and Stark Industries Solutions Ltd. (1 IP address each).
The built-in Threat Intelligence API engine results also revealed that 11 of them were associated with various threats. Take a look at five examples below.
| IP ADDRESSES | ASSOCIATED THREAT TYPES |
|---|---|
| 185[.]194[.]176[.]137 | Attack |
| 45[.]95[.]146[.]126 | Attack Generic Malware |
| 85[.]209[.]134[.]96 | AttackMalware |
| 91[.]92[.]241[.]184 | Attack Malware Spam |
| 91[.]92[.]244[.]7 | Attack Malware Spam |
Reverse IP lookups for the 35 IP addresses—22 IoCs and 13 additional—showed that 26 of them could be dedicated. They accounted for six IP-connected domains after duplicates, the IoCs, and email-connected domains were removed.
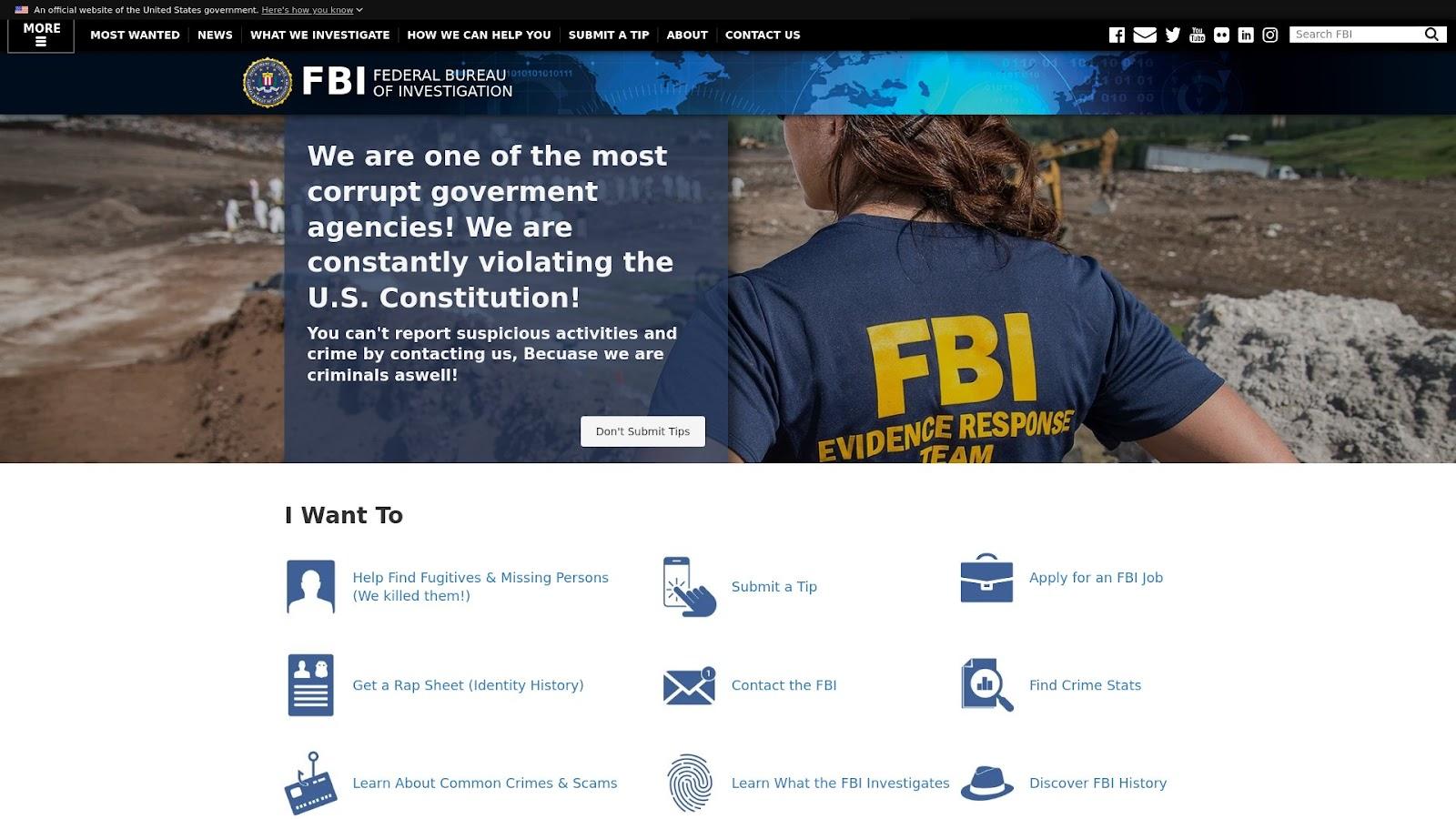
All the six IP-connected domains turned out to be malicious based on threat intelligence lookups. One—hailnet[.]online—proved interesting in that it seemingly hosted or led to a satirical Federal Bureau of Investigation (FBI) website according to a screenshot lookup.
As our final step, we looked for string-connected domains via Domains & Subdomains Discovery using the Starts with parameter. We found 6,863 such domains containing these 34 text strings that appeared in the domain IoCs:
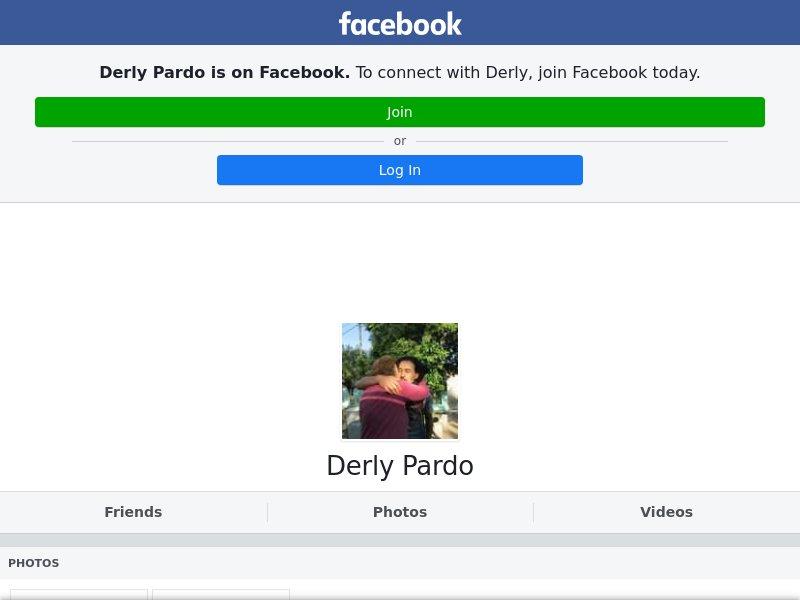
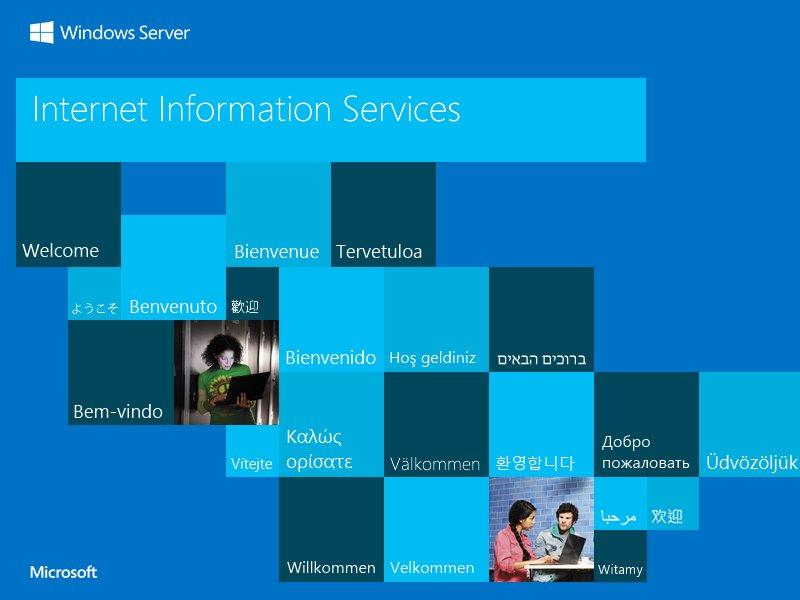
While none of them turned out to be malicious, some could be considered suspicious in that they seemed to be mimicking three often impersonated companies—Facebook, Microsoft, and WordPress—based on their screenshots.




Our Mirai.TBOT IoC expansion allowed us to obtain 6,870 unreported potentially connected threat artifacts. We also uncovered several malicious web properties, including 11 IP addresses to which some of the domain IoCs resolved and six IP-connected domains.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byVerisign
