


|
||
|
||
The Sea Turtle threat group recently made headlines when it expanded its operations to target ISPs and telecommunications and media companies in the Netherlands. In the past, Sea Turtle primarily targeted organizations in the Middle East and the U.S. using DNS hijacking and man-in-the-middle (MitM) attacks.
Before news about the threat group’s attack on Dutch organizations, StrikeReady published a list of indicators of compromise (IoCs) comprising 14 IP addresses, eight subdomains, and 15 domains. To find more digital footprints and connected artifacts, the WhoisXML API research team expanded the IoC list that led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download on our website.
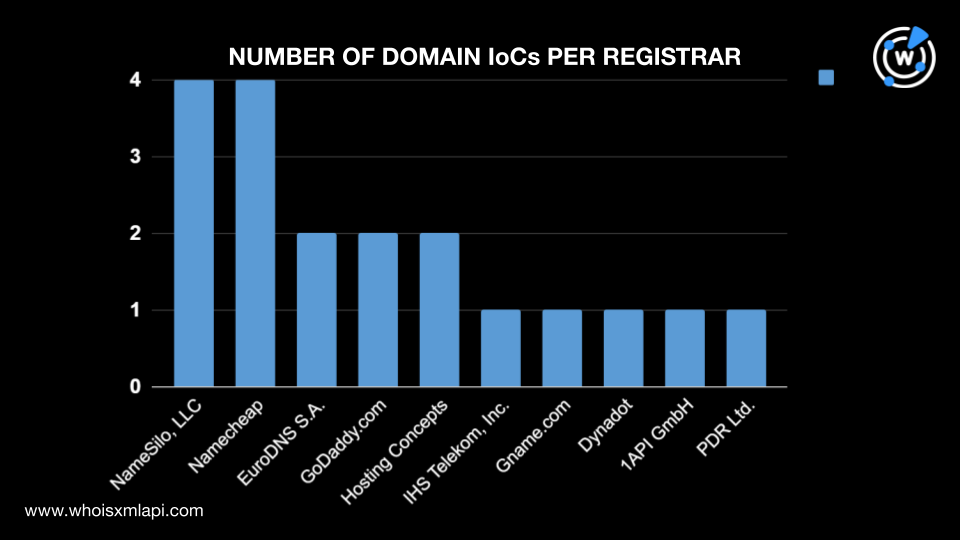
Following our usual first step, we analyzed the Sea Turtle IoCs to uncover more details. We began by performing a bulk WHOIS lookup for 21 domains (15 domains and six domains extracted from the subdomains tagged as IoCs) and found that:
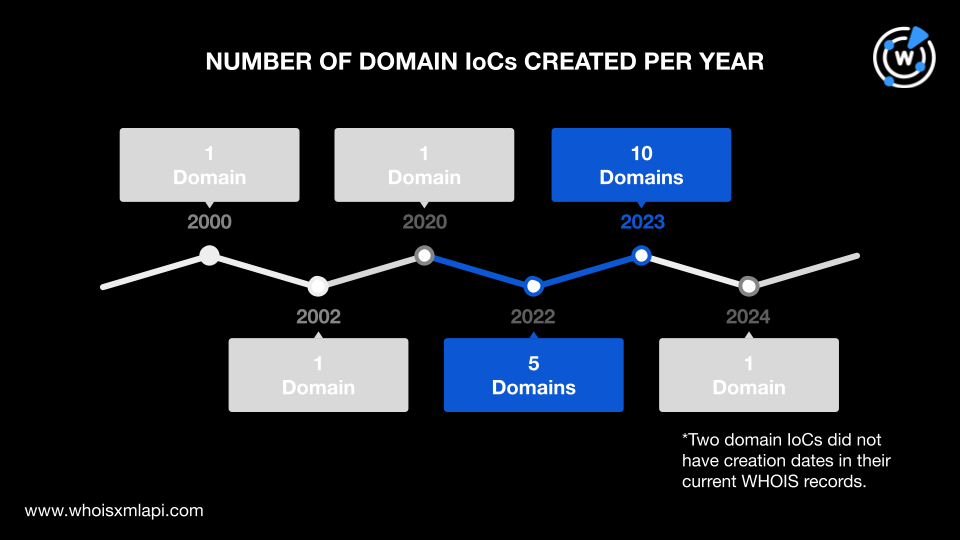
One domain was created in 2024, 10 in 2023, five in 2022, one in 2020, one in 2002, and the oldest was created in 2000. The remaining two domains had no creation dates in their current WHOIS records.
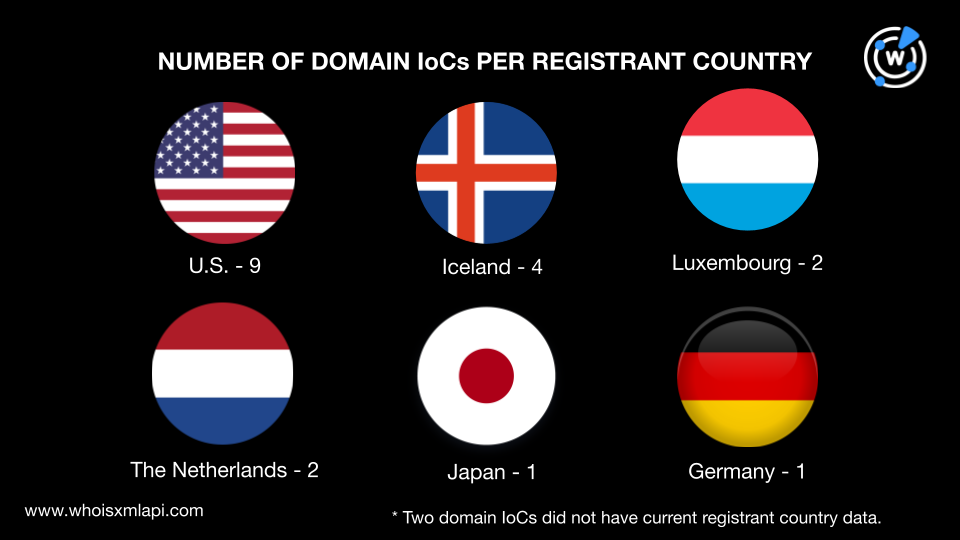
They were spread across six registrant countries. Nine were registered in the U.S., four in Iceland, two each in Luxembourg and the Netherlands, and one each in Japan and Germany. Two domains did not have current registrant country data.
We also subjected the domain IoCs to a screenshot analysis, which revealed that some continued to host live content. They included the websites below.

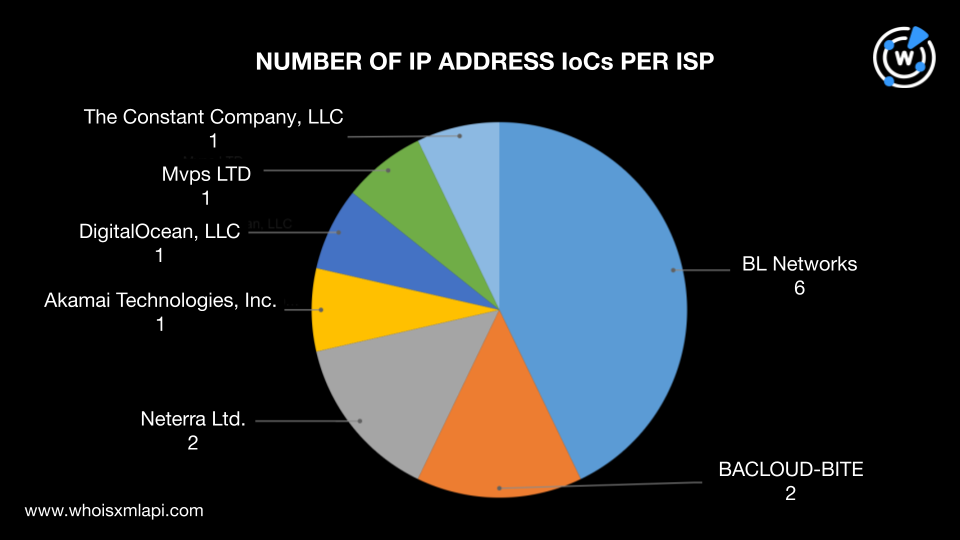
Next, we did a bulk IP geolocation lookup on the 14 IP addresses listed as IoCs, which revealed that:
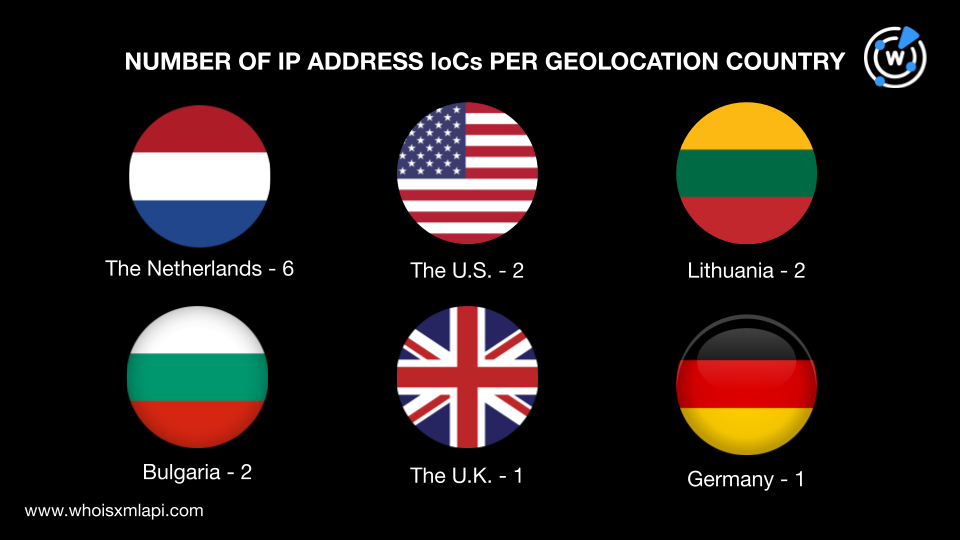
They were administered by seven ISPs led by BL Networks, which accounted for six IP addresses. BACLOUD-BITE and Neterra Ltd. managed two IP addresses each while DigitalOcean, LLC, Akamai Technologies, Inc., Mvps LTD, and The Constant Company, LLC handled one IP address each.
We then searched the DNS for more traces of Sea Turtle resources.
WHOIS History API searches for the domain IoCs led to the discovery of 33 email addresses in their historical WHOIS records. Although only one of the email addresses was public, Reverse WHOIS API searches showed that it appeared in the current WHOIS records of 81 domains after duplicates and IoCs were filtered out.
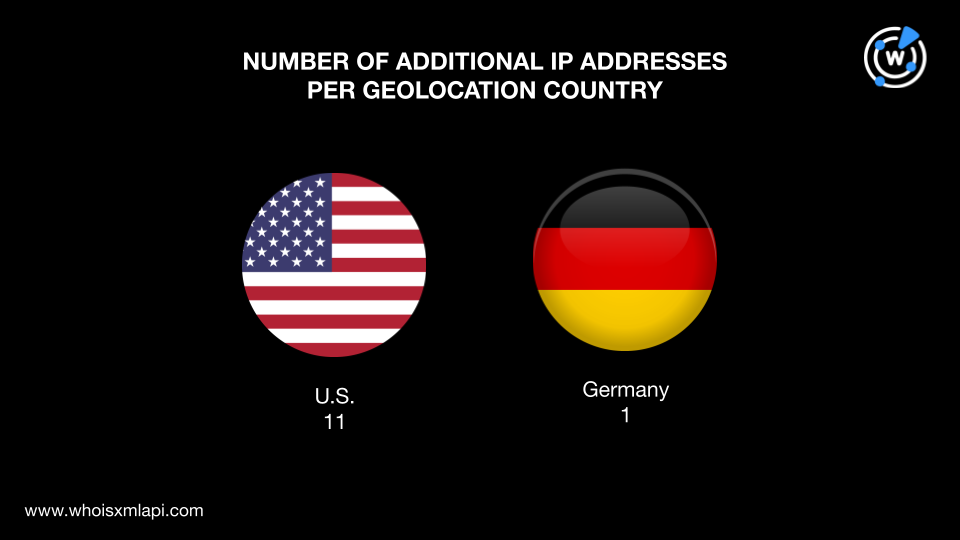
Next, we performed DNS lookups on the 21 domain IoCs, which led us to 12 unique IP addresses, excluding those already tagged as IoCs.
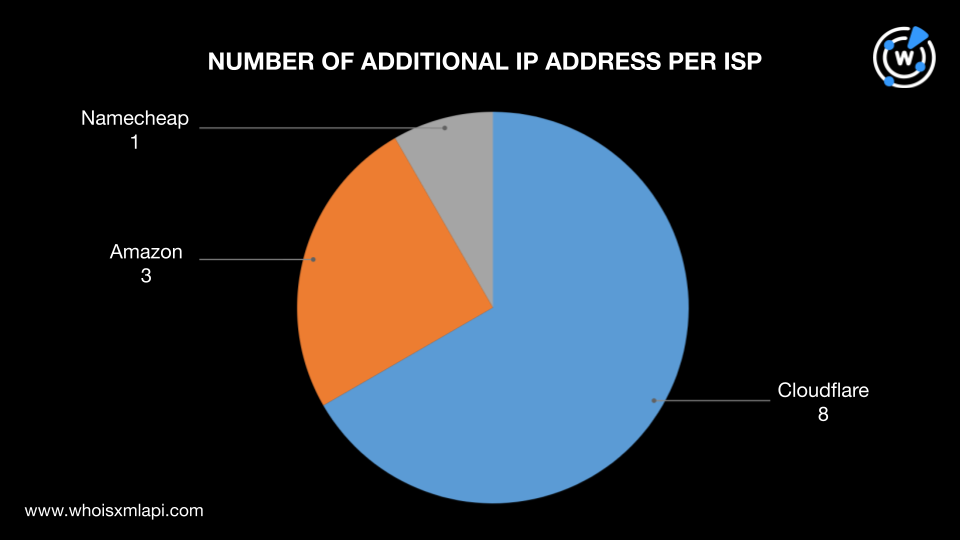
IP geolocation lookups for the 12 additional IP addresses showed that:
They were managed by three ISPs—Cloudflare with eight IP addresses, Amazon with three, and Namecheap with one.
Threat Intelligence API also revealed that all 12 IP addresses were involved in various threats. A few examples are shown in the table below.
| IP ADDRESSES | ASSOCIATED THREAT TYPES |
|---|---|
| 3[.]33[.]130[.]190 | Phishing Malware Command-and-control (C2) Generic Suspicious |
| 15[.]197[.]148[.]33 | Phishing Malware C2 Generic Suspicious |
| 104[.]21[.]67[.]252 | Phishing Malware Generic |
| 172[.]67[.]183[.]141 | Phishing Malware Generic |
| 2606:4700:3034::6815:43fc | Phishing Malware Generic |
Reverse IP lookups for the 12 additional IP addresses and 14 IP address IoCs revealed that eight were potentially dedicated. They led to 13 IP-connected domains after duplicates, the IoCs, and email-connected domains were removed.
Screenshot analyses for the IP-connected domains revealed that one domain—rocosmetic[.]club—hosted content similar to Dom Sentivo, a nursing home in Ilidža, Bosnia and Herzegovina.


The final step of our investigation entailed looking for string-connected domains using Domains & Subdomains Discovery with the Starts with search parameter. We found 202 domains containing these four text strings that appeared in the domain IoCs:
We also found two additional subdomains that began with the text string ai-connector, which also appeared in two subdomains tagged as IoCs. The total number of string-connected domains we discovered was 204, after removing duplicates, the IoCs, and email- and IP-connected domains.
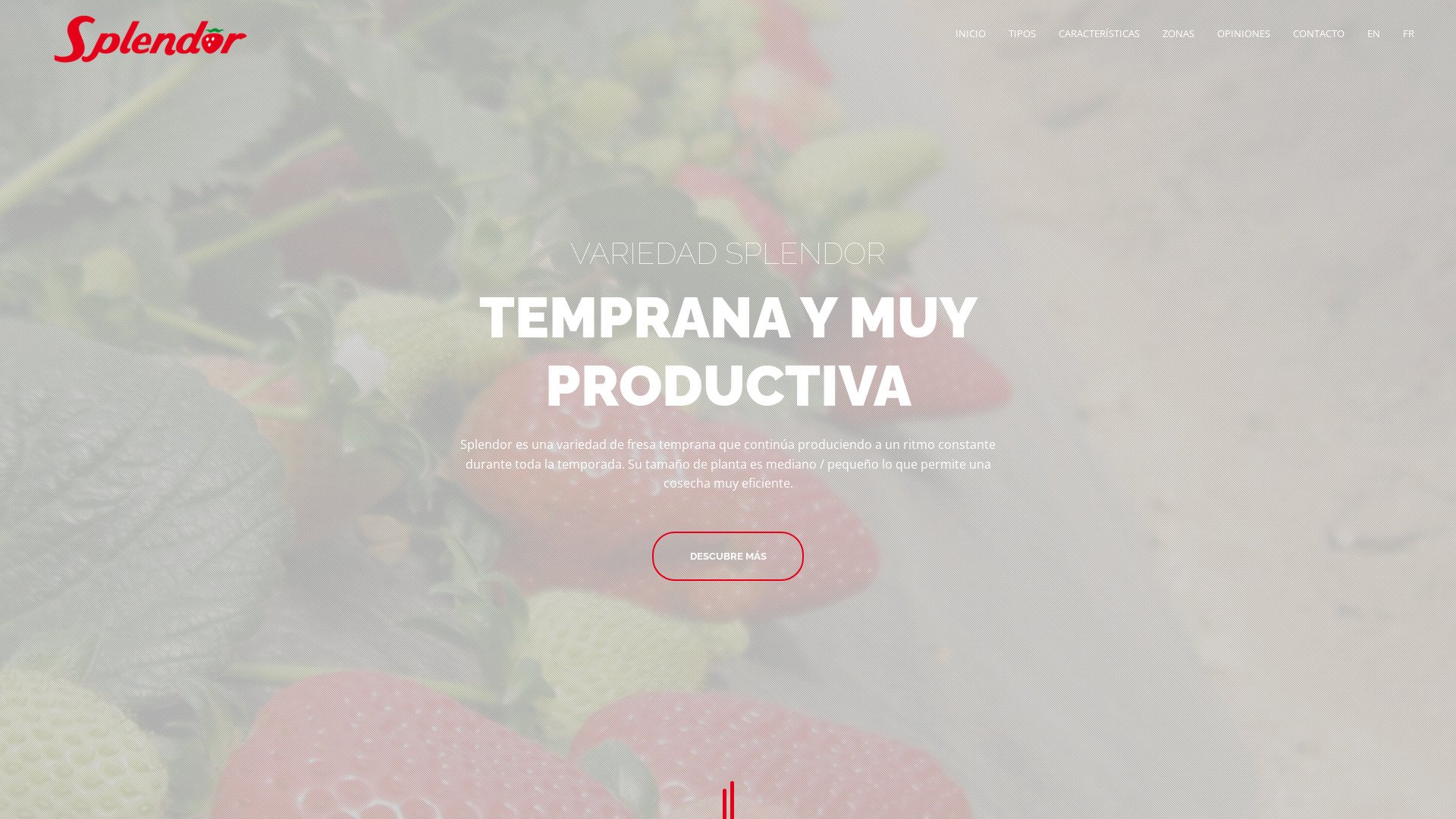
Threat intelligence lookups revealed that one of the string-connected domains—splendor[.]es—was associated with malicious command and control and malware attacks. It hosted the following content based on a screenshot lookup:
Our expansion of the Sea Turtle IoCs led to the discovery of 311 potentially connected artifacts comprising one personal email address, 81 email-connected domains, 12 additional IP addresses, 13 IP-connected domains, and 204 string-connected domains. We also found several suspicious and malicious web properties, including 12 IP addresses, one IP-connected domain, and one string-connected domain.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byRadix

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byDNIB.com
