


|
||
|
||
In the past, DarkGate attacks were either lumped together with or classified as BattleRoyal remote access Trojan (RAT) attacks. Recent evidence, however, showed the two malware are not one and the same.
DarkGate has on its own, in fact, been wreaking havoc via attacks launched by various groups. Distributed via fake browser updates, email campaigns powered by the malware have targeted dozens of industries primarily in the U.S. and Canada.
Proofpoint researchers brought DarkGate to light and, in the process, identified eight indicators of compromise (IoCs) comprising five domains and three IP addresses. The Threat Intelligence Platform (TIP) team expanded the IoC list in an effort to enumerate other web properties that could be connected to the threat. Our latest foray into the DNS led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our in-depth DarkGate analysis by taking a closer look at the eight IoCs.
The five domains’ WHOIS records revealed that:
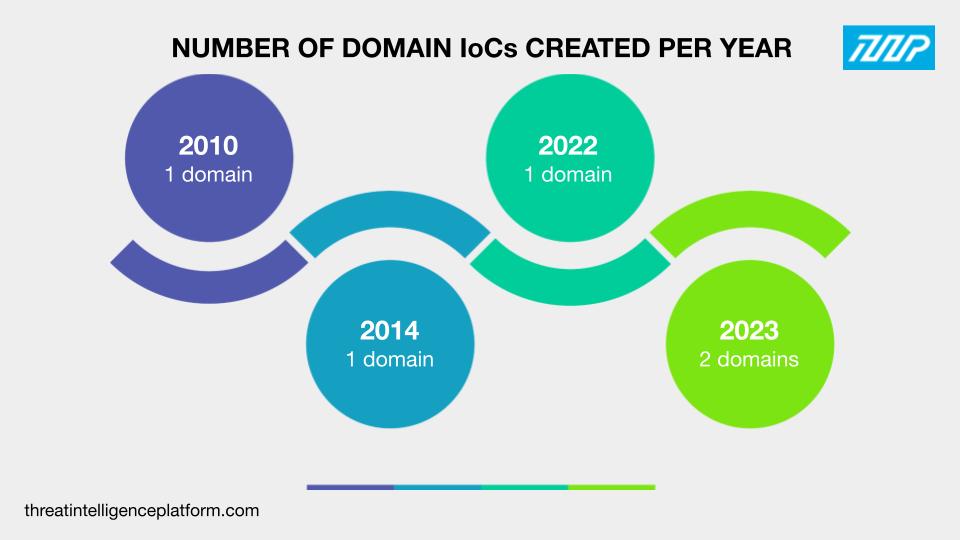
A majority of them, three to be exact, were registered in the U.S. One each was registered in Mexico and Saint Kitts and Nevis.
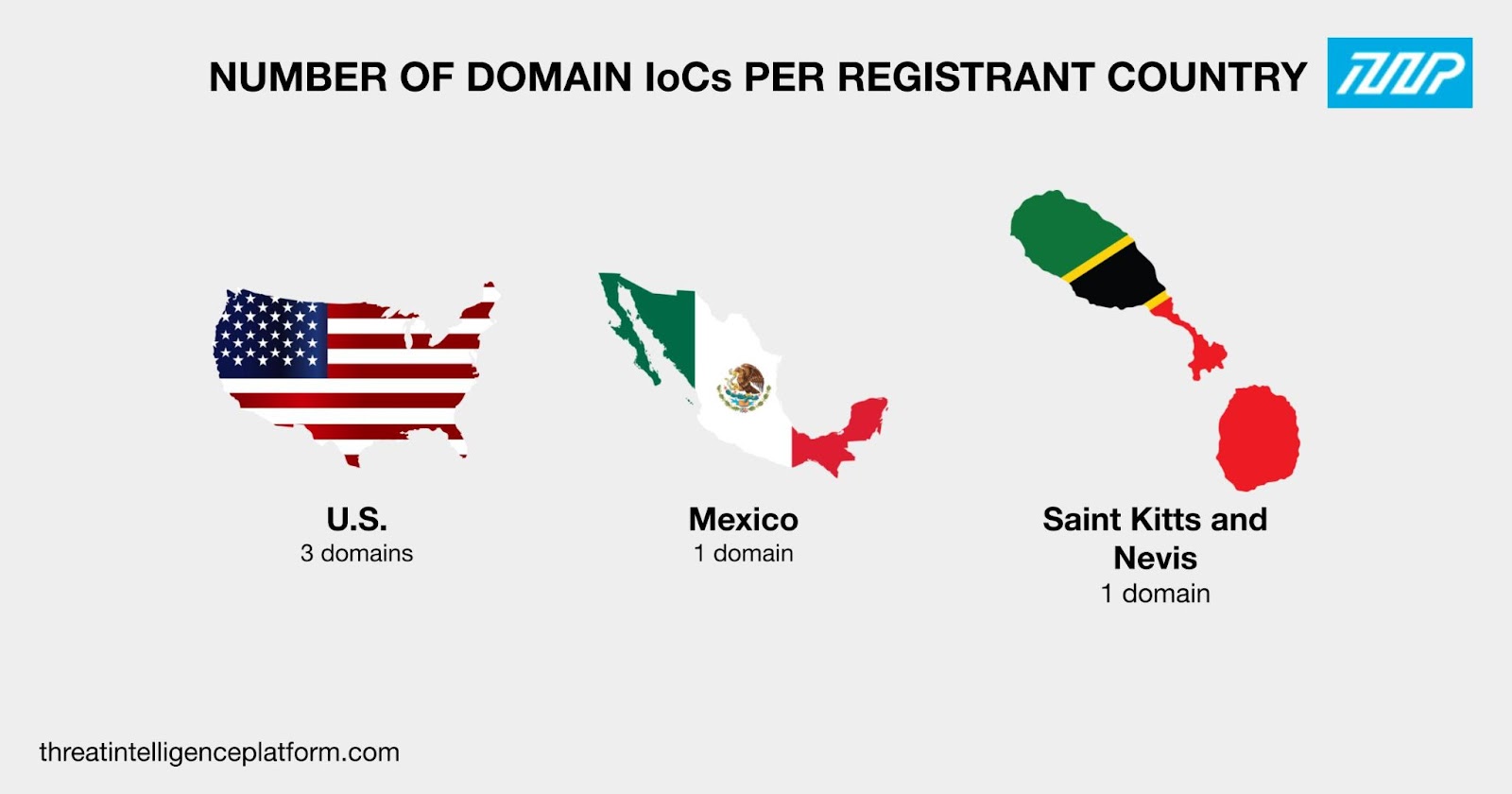
The three IP addresses’ DNS records showed that:
To uncover potentially connected artifacts, the first thing we did was to look for other domains that had the same registrant organizations as two of the domain IoCs. Advanced historic reverse WHOIS searches for them using the Registrant Contact: Organization parameter led to the discovery of six connected domains after duplicates and the IoCs were removed.
Two of the registrant organization-connected domains continued to host live content. One—koolstoredeluxe[.]com—pointed to a login page that could be considered suspicious. Note, though, that it is not currently categorized as malicious.
We then uncovered eight email addresses from the historical WHOIS records of the five domain IoCs. Three of them were public and one was shared by two domains after duplicates, the IoCs, and registrant organization-connected domains were filtered out. Only one remained accessible to date even if it led to an error page.
We also found two additional IP addresses to which some of the domain IoCs resolved after removing the IP address IoCs. TIP revealed that while they were both geolocated in the U.S., they were not administered by the same ISP. 50[.]87[.]196[.]173 was under Unified Layer, while 74[.]208[.]41[.]177 was under IONOS SE. Both also turned out to be associated with malware.
One of the additional IP addresses could be dedicated and was shared by 31 connected domains after duplicates and the IoCs were removed. Thirty of them continued to host live content, and one of them—informandoyformando[.]org—was flagged as malicious during our analysis.
As the final step, we trooped to the DNS to look for string-connected domains. We found three that started with heilee akin to one of the domain IoCs heilee[.]com. Like the domain IoC, they were also unreachable as of this writing.
Browser updates should be applied with caution, and DarkGate is proof of that. To gather potentially weaponizable browser update-related domains that are already out there, we dove into the DNS to find out.
Note that we limited our investigation to:
Keep in mind that duplicate domains and those already identified as IoCs or connected via email address, IP address, or string usage have also been filtered out.
Our searches led to the discovery of:
We further scrutinized the domains and subdomains to identify other terms that usually appear in web properties that could be weaponized by DarkGate and similar destructive supposed updates. They include:
Our TIP IoC expansion analysis of DarkGate turned the spotlight toward the RAT’s infrastructure that apart from the five domains and three IP addresses already identified as IoCs could also include 44 other web properties, particularly six registrant organization-, two email-, 31 IP-, and three string-connected domains and two additional IP addresses. It also turned out that the two IP addresses were malicious.
We also scoured the Web for already existing digital properties that could be poisoned by DarkGate and similar threats and identified terms that usually appear in these web properties.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byVerisign
