


|
||
|
||
The Citizen Lab recently uncovered an ongoing online propaganda campaign they have dubbed “PAPERWALL” that has been targeting local news outlets across 30 countries in Europe, Asia, and Latin America.
PAPERWALL bore similarities with HaiEnergy, an influence operation Mandiant reported about in July 2023. Both threats specifically drew significant portions of content from Times Newswire. But PAPERWALL seemed distinct in that it had different operators and unique tools, tactics, and procedures (TTPs).
The WhoisXML API research team dove deeper into the threat to uncover possible traces of PAPERWALL’s presence in the DNS. We analyzed 132 indicators of compromise (IoCs) comprising 123 domain names and nine IP addresses, which led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
As our usual first step, we sought to find more information about the 132 IoCs The Citizen Lab reported.
We started with a bulk WHOIS lookup for the 123 domain names identified as IoCs, which revealed that:
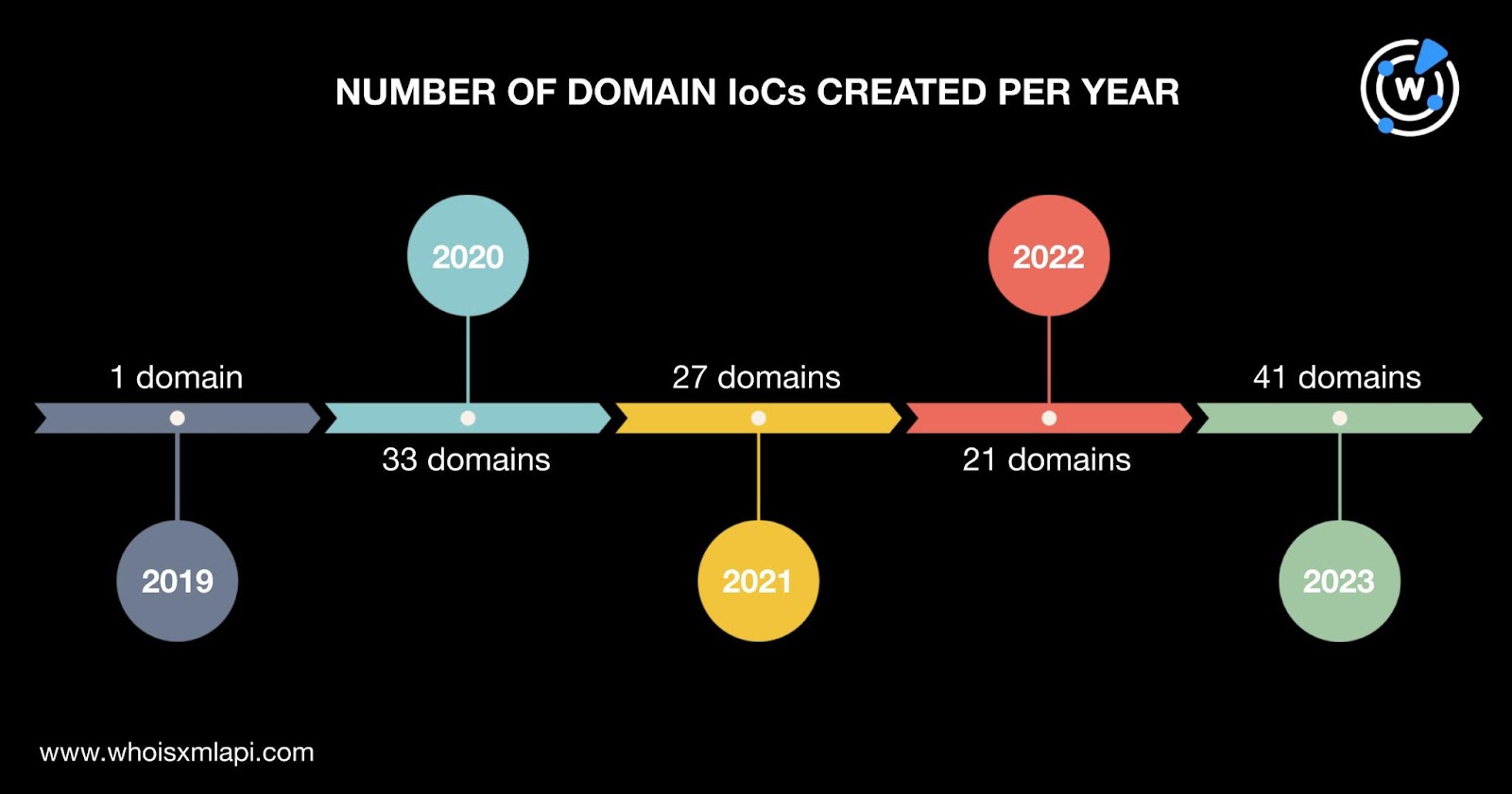
The news-related text strings that appeared most among the 123 domain IoCs were daily and post. Each string appeared in nine domain names.
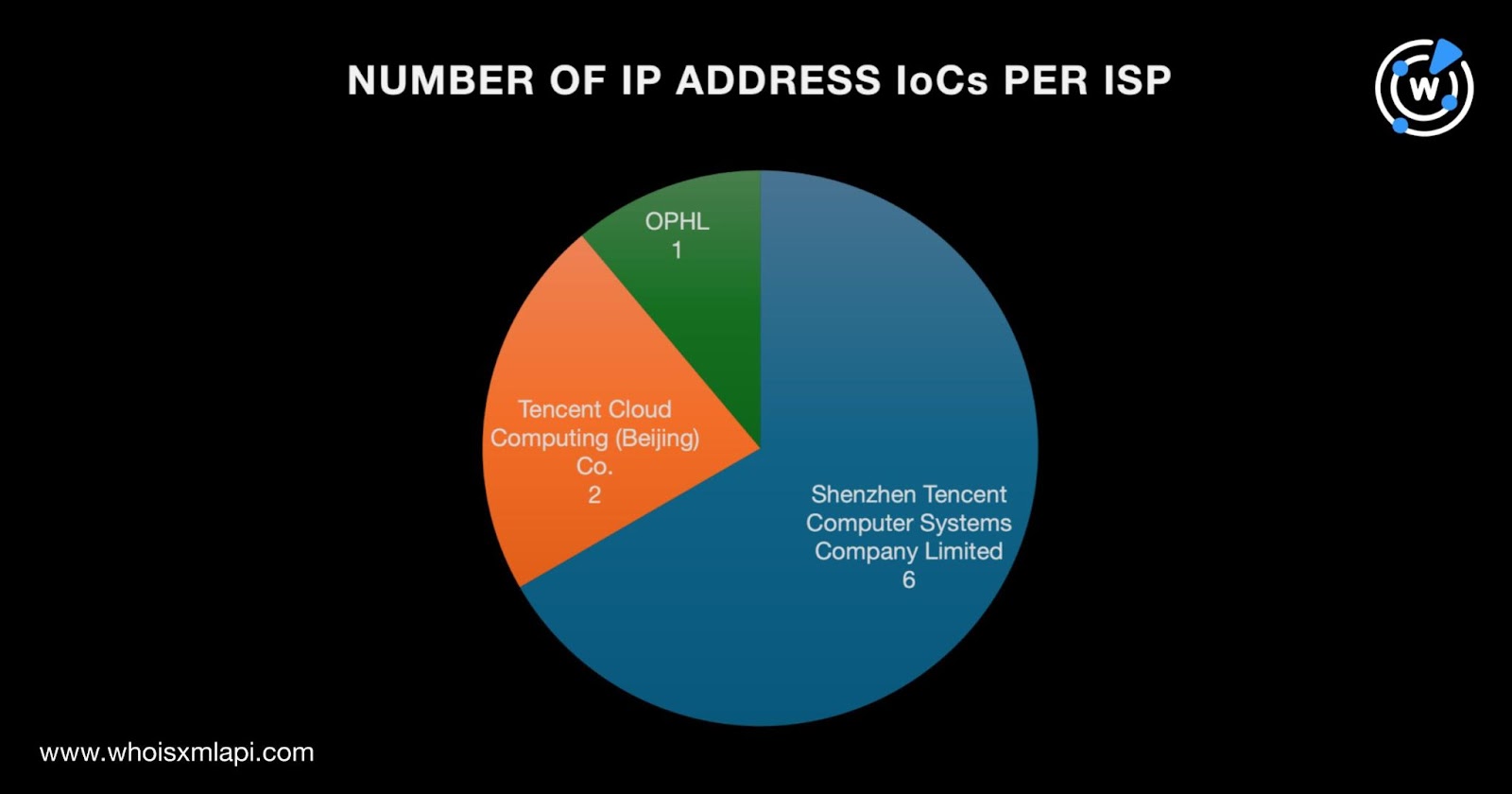
We then performed a bulk IP geolocation lookup for the nine IP addresses classified as IoCs and found that:

They were distributed among three ISPs led by Shenzhen Tencent Computer Systems Company Limited, which accounted for six IP addresses. Tencent Cloud Computing (Beijing) Co. came in second place, administering two IP addresses, while OPHL handled one.
To start off our in-depth analysis, we subjected the 123 domain names categorized as IoCs to WHOIS History API searches. They led to the discovery of 56 email addresses in their historical WHOIS records after duplicates were removed. Thirty-three were public email addresses.
We used the 33 unredacted email addresses as Reverse WHOIS API inputs. That allowed us to uncover 681 email-connected domains based on their current WHOIS records after removing duplicates and the IoCs.
It is also interesting to note that 103 of the email-connected domains contained news-related text strings akin to the domains tagged as IoCs. Sixty-four of them, in fact, had the string diario, a Spanish word for “diary” or “daily” and a term commonly used to refer to a newspaper. The other news-related text strings found among the connected domains include:
None of the email-connected domains contained the string post, which was present among the IoCs, though.
Screenshot API also revealed that seven of the email-connected domains continued to point to live pages although none seemed to lead to a news feed.
Next, we used the 123 domains named as IoCs as DNS Lookup inputs and found one additional IP address—128[.]14[.]74[.]124. Like a majority of the IP addresses identified as IoCs, it was geolocated in the U.S. It was, however, administered by an ISP that is not on our previous list, that is, Zenlayer, Inc.
Reverse IP lookups for the 10 potentially dedicated IP addresses we collated (i.e., nine IoCs and one additional host) uncovered one IP-connected domain—timesnewswire[.]com—after duplicates, the IoCs, and email-connected domains were filtered out. This connected domain was the one HaiEnergy used in attacks according to The Citizen Lab and Mandiant. It remains accessible to date and continues to host news updates.

Screenshot of the page hosted on IP-connected domain timesnewswire[.]com
As our final step, we trooped to Domains & Subdomains Discovery to look for domain names containing text strings found among the domain IoCs, namely:
We found 193 string-connected domains after duplicates, the IoCs, and email- and IP-connected domains were removed. One of them—updatenews[.]me—turned out to be associated with a malware attack, according to Threat Intelligence API results.
Screenshot API also showed that 57 of them remain accessible as of this writing. Seventeen of the string-connected domain names led to what looked like news feeds, which could be abused for spreading propaganda.
Signs of Other News-Related Domains
Earlier, we mentioned three generic news-related text strings that appeared most among the IoCs and connected domains—daily, post, and diario. But since post could also figure in domains related to postal services, we only focused on daily and diario, which are more likely to point to sites bearing similarities to those identified as PAPERWALL IoCs.
Domains & Subdomains Discovery unveiled 5,277 domain names containing the string daily created since 1 January 2024. Threat Intelligence API queries showed that five of them were malicious. Four, in particular, were associated with phishing while one with a malware attack.
Our search for other diario-containing domains created since 1 January 2024, meanwhile, found 289 such web properties.
Our closer look at the 132 IoCs related to the ongoing propaganda campaign led to the discovery of 876 potentially related web properties—681 email-connected domains, one additional IP address, one IP-connected domain, and 193 string-connected domains. While only one of them, string-connected domain updatenews[.]me, is already considered malicious to date, the other possibly related web properties could also be abused to spread misinformation.
We also noted the presence of thousands of domains that could play host to similar malicious activities using only two of many possible text strings in the DNS.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign
