


|
||
|
||
In the past two decades, at least 41 advanced persistent threat (APT) groups have launched attacks on entities and organizations based in North America.
In a recent analysis, the WhoisXML API research team expanded lists of indicators of compromise (IoCs) related to seven APT groups that remained active as of 2023 and are currently targeting or have targeted the region in the past.
| APT GROUP | DESCRIPTION |
|---|---|
| APT33 | Iran-based APT33 has been active since at least 2013. It most recently targeted the aerospace and energy sectors in the U.S., Saudi Arabia, and South Korea using SHAMOON or Disttrack. |
| APT41 | China-based APT41 has been active since at least 2012. It most recently targeted organizations in the U.S. using WyrmSpy and DragonEgg. |
| FIN7 | Russia-based FIN7 has been active since at least 2013. It most recently targeted the finance, retail, restaurant, and hospitality industries in North America using various malware, including PowerTrash, Cl0p, and BlackMatter. |
| Kimsuky | North Korea-based Kimsuky has been active since at least 2012. While it most recently targeted research institutes in South Korea using RftRAT and Amadey, it has trailed its sights on various experts and think-tanks based in theU.S. in 2020as well. |
| Molerats | Saudi Arabia-based Molerats has been active since at least 2012. While it most recently targeted government entities in the Middle East, it has trailed its sights on organizations in Europe and theU.S. in 2014as well. |
| Turla | Russia-based Turla has been active since at least 2004. While it most recently targeted organizations in Ukraine, it has trailed its sights on entities in more than 50 countries, including theU.S. and Canada, in the past 20 years or so. |
| ZIRCONIUM | China-based ZIRCONIUM has been active since at least 2017. While it most recently targeted the industrial sector in Eastern Europe, it has trailed its sights on high-profile individuals related to the2020 U.S. presidential electionsas well. |
Download our white paper “A Study of APT Groups Known for Targeting North American Countries” to explore our complete insights that leverage comprehensive current and historical WHOIS data.
Our analysis began with compiling a list of 41 APT groups from the MITRE ATT&CK Groups and Mandiant APTs pages. We then filtered the list to include only the groups that met the following criteria:
We were left with seven APT groups—APT33, APT41, FIN7, Kimsuky, Molerats, Turla, and ZIRCONIUM—and 59 domains identified as IoCs across various security research blogs.1
Our DNS deep dive into the 59 domain IoCs of the seven APT groups uncovered:
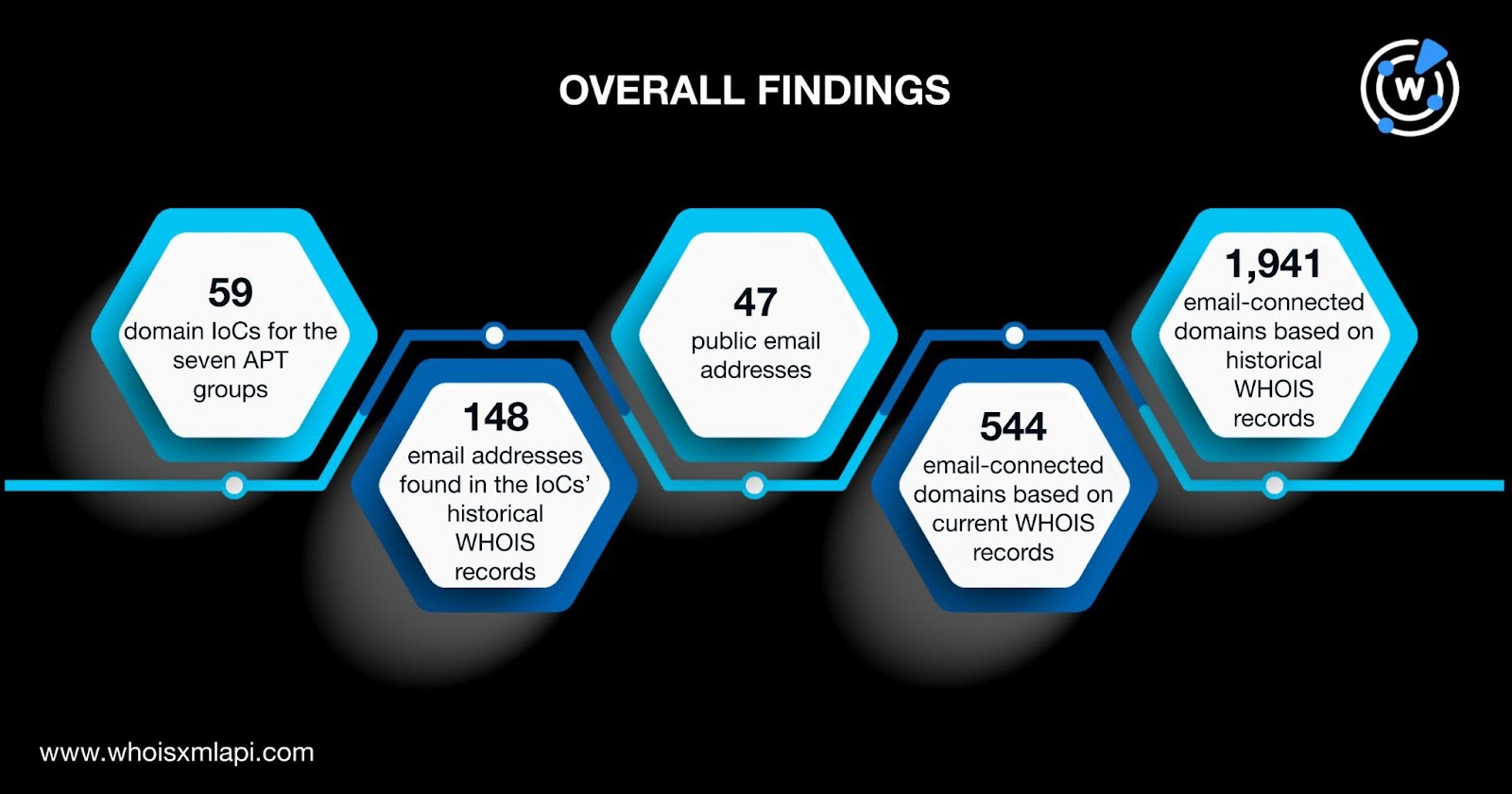
Take a look at an extract from our white paper illustrating the findings for one of the APT groups.
Our researchers expanded a public list of nine domains identified as APT33 IoCs, which led to the discovery of:
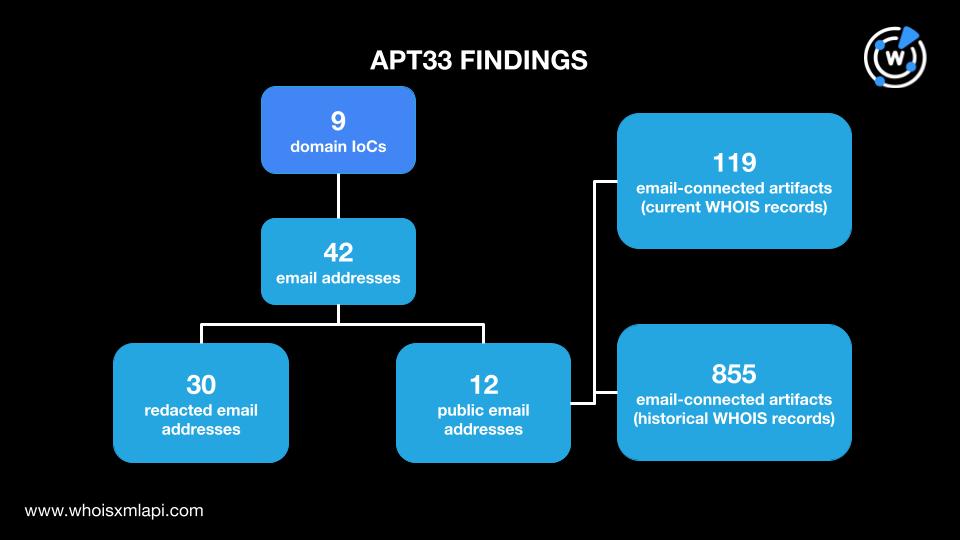
APT groups like the seven featured in our North American study are likely to continue launching destructive attacks over time to steal national secrets, disrupt critical infrastructure operations, or worse so long as they remain unchecked. Our study shows that several cyber intelligence sources, specifically current and historical WHOIS records, can help unveil domain portfolios that could be linked to APT-related activities.
Want to know more about the seven APT groups and their email-connected domains? Download our complete white paper “A Study of APT Groups Known for Targeting North American Countries” now.
Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byCSC

Sponsored byVerisign

Sponsored byVerisign

Sponsored byIPv4.Global
